通过使用 Azure 网络观察程序的数据包捕获功能,可以在 Azure 虚拟机(VM)和虚拟机规模集上启动和管理捕获会话:
- 通过 Azure 门户、PowerShell 和 Azure CLI。
- 通过 SDK 和 REST API 以编程方式进行。
使用数据包捕获,可以通过以易用格式提供信息来解决需要数据包级数据的方案。 通过使用免费可用的工具来检查数据,您可以检查传入和传出您 VM 或规模集的通信,以便深入了解网络流量。 数据包捕获数据的示例用法包括调查网络或应用程序问题、检测网络滥用和入侵尝试以及维护法规合规性。
本文介绍如何使用常用的开源工具打开网络观察程序提供的数据包捕获文件。 你还将了解如何计算连接延迟、识别异常流量以及检查网络统计信息。
先决条件
通过网络观察程序创建了数据包捕获文件。 有关详细信息,请参阅 使用 Azure 网络观察程序启动、停止、下载和删除数据包捕获。
Wireshark。 有关详细信息,请参阅 Wireshark 网站。
计算网络延迟
在此示例中,你将了解如何查看两个终结点之间的传输控制协议(TCP)对话的初始往返时间(RTT)。
建立 TCP 连接后,在连接中发送的前三个数据包遵循称为三向握手的模式。 通过检查在此握手中发送的前两个数据包(来自客户端的初始请求和服务器的响应),可以计算延迟。 此延迟是 RTT。 有关 TCP 协议和三向握手的详细信息,请参阅 TCP/IP 的三向握手的说明。
启动 Wireshark。
从数据包捕获会话加载 .cap 文件。
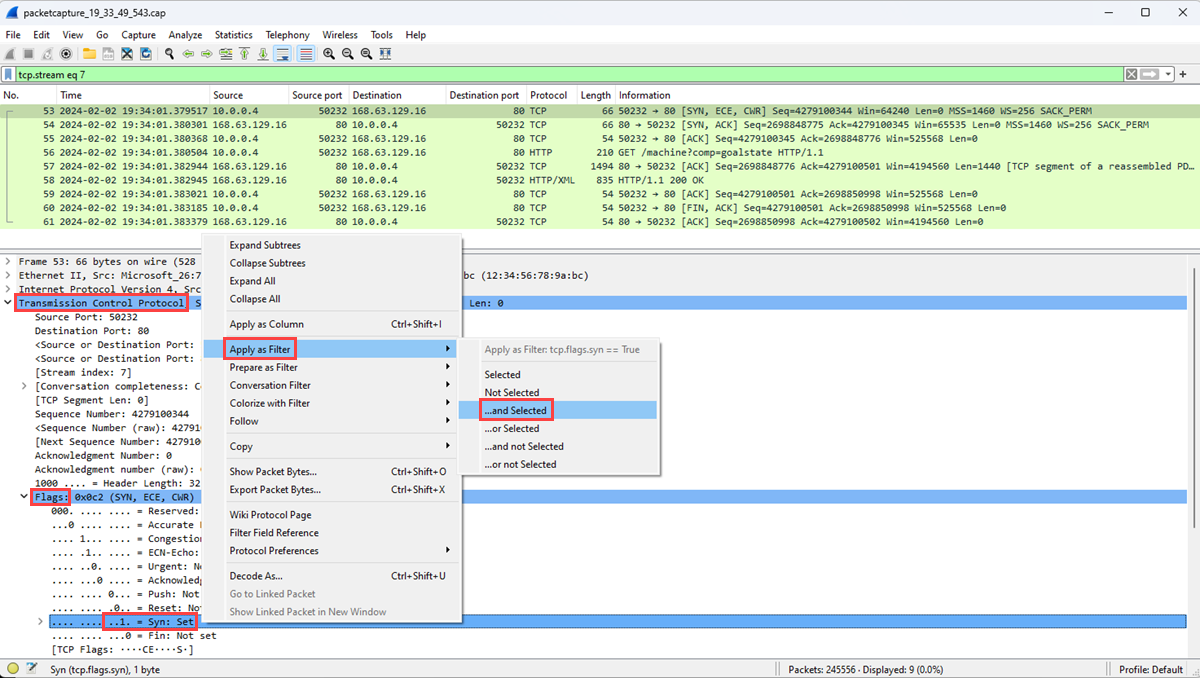
在捕获中选择 [SYN] 数据包。 此数据包是客户端发送的第一个数据包,用于启动 TCP 连接。
右键单击数据包,选择 “跟踪”,然后选择 “TCP 流”。
展开 [SYN] 数据包的 传输控制协议 部分,然后展开 “标志 ”部分。
确认 Syn bit 设置为 1,然后右键单击它。
选择“应用为筛选器”,然后选择“…和已选”以显示在 TCP 流中将 Syn 位设置为 1 的数据包。
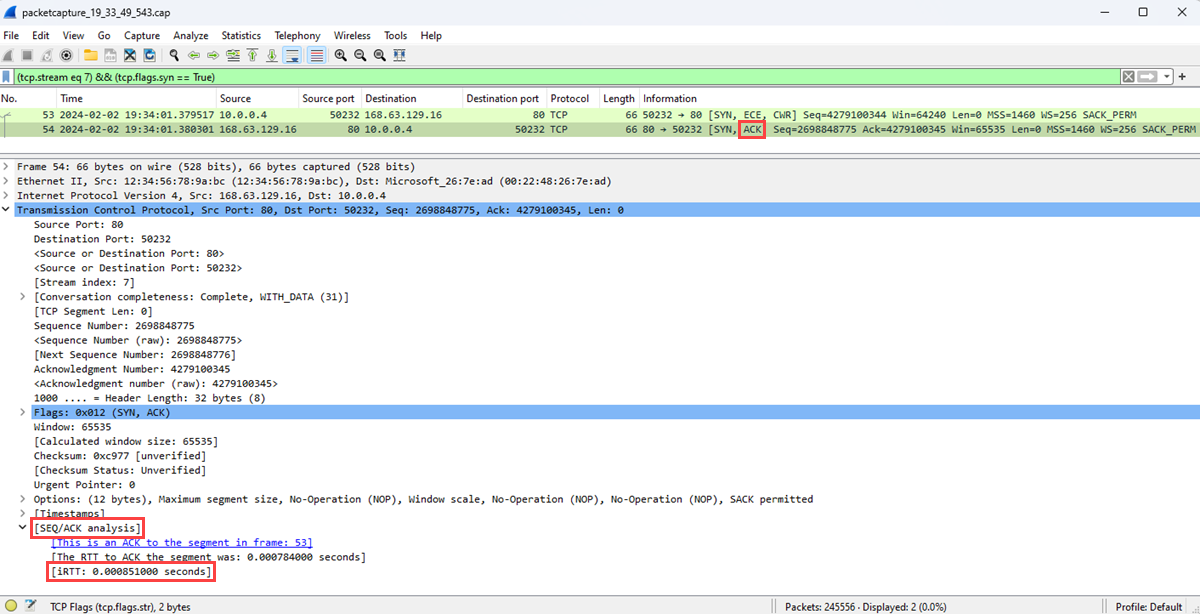
TCP 握手中涉及的前两个数据包是 [SYN] 和 [SYN, ACK] 数据包。 握手过程中不需要最后一个数据包,即 [ACK] 数据包。 客户端发送 [SYN] 数据包。 服务器收到 [SYN] 数据包后,它会发送 [ACK] 数据包作为从客户端接收 [SYN] 数据包的确认。
选择 [SCK] 数据包。
展开 SEQ/ACK 分析 部分以显示初始 RTT(以秒为单位)。
查找不需要的协议
可以在 Azure 虚拟机上运行许多应用程序。 其中许多应用程序通过网络通信,有时未经你的明确许可。 通过使用数据包捕获来记录网络通信,可以调查应用程序如何通过网络进行通信。 调查有助于识别和解决任何潜在问题。
在此示例中,您将学习如何分析数据包捕获,以查找可能指示来自虚拟机上运行的应用程序未经授权通信的不必要协议。
打开 Wireshark。
从数据包捕获会话加载 .cap 文件。
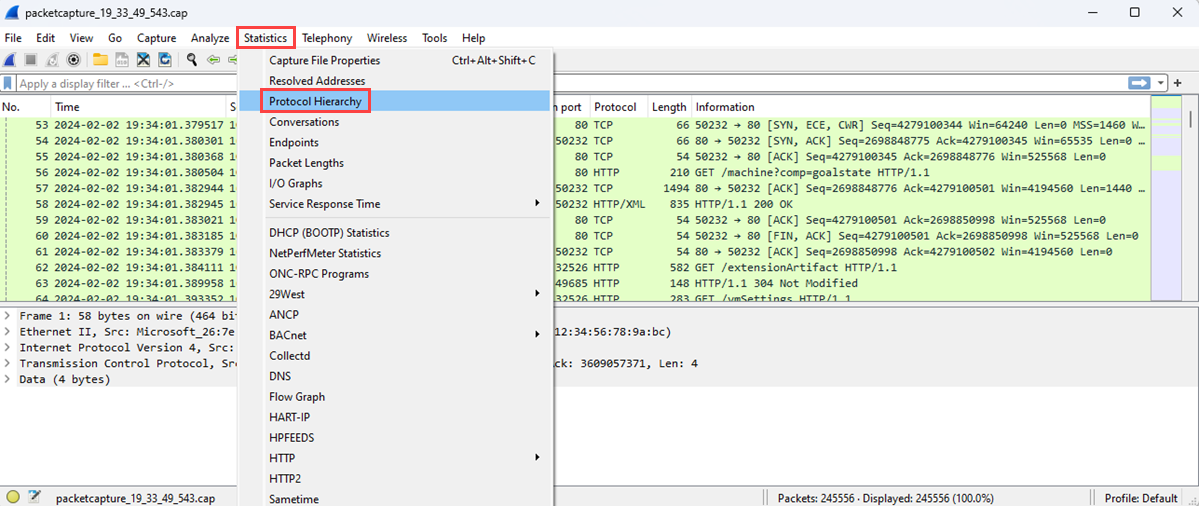
在“ 统计信息 ”菜单上,选择“ 协议层次结构”。
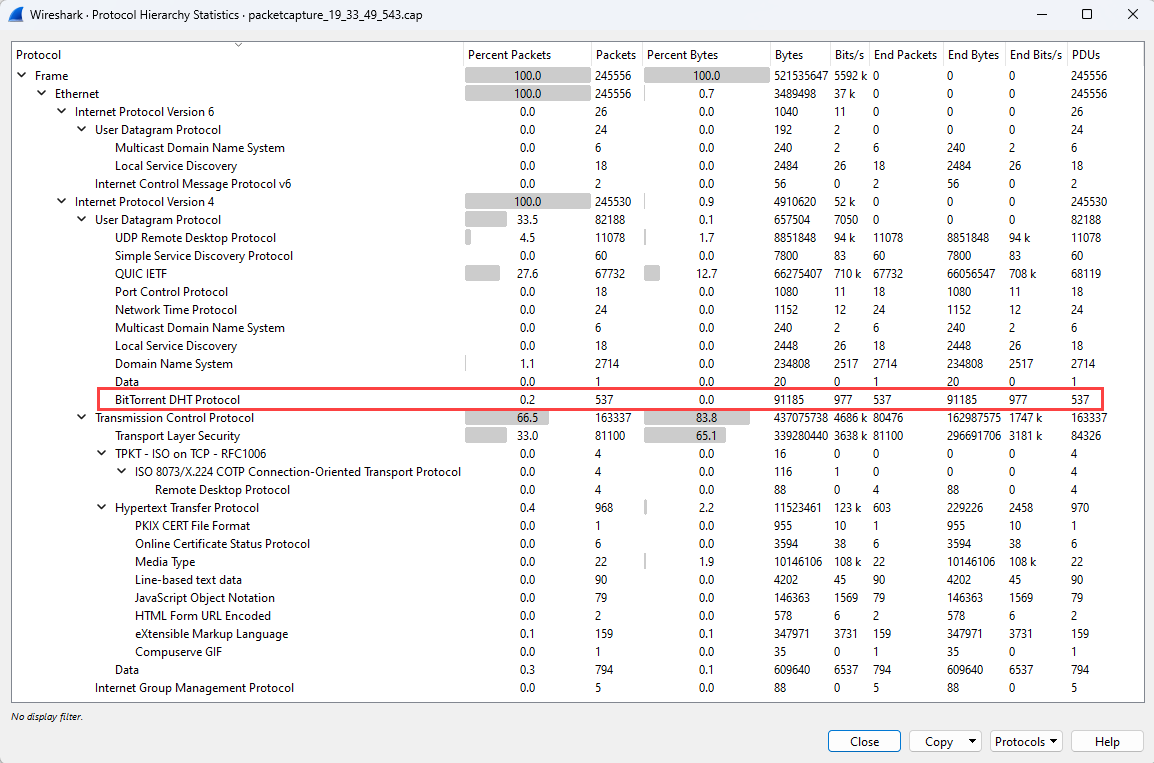
“ 协议层次结构统计信息 ”窗口列出捕获会话期间使用的所有协议,以及为每个协议传输和接收的数据包数。 此视图可用于查找虚拟机或网络上不需要的网络流量。
此示例显示了 BitTorrent 协议的流量,该协议用于对等文件共享。 作为管理员,如果不希望在此虚拟机上看到 BitTorrent 流量,可以采取以下措施:
- 删除此虚拟机上安装的点对点软件。
- 使用网络安全组或防火墙阻止流量。
查找目标和端口
监视或排查网络中的应用程序和资源问题时,了解通信的流量类型、终结点和端口非常重要。 通过分析数据包捕获文件,可以了解虚拟机与之通信的顶级目标以及它们使用的端口。
启动 Wireshark。
从数据包捕获会话加载 .cap 文件。
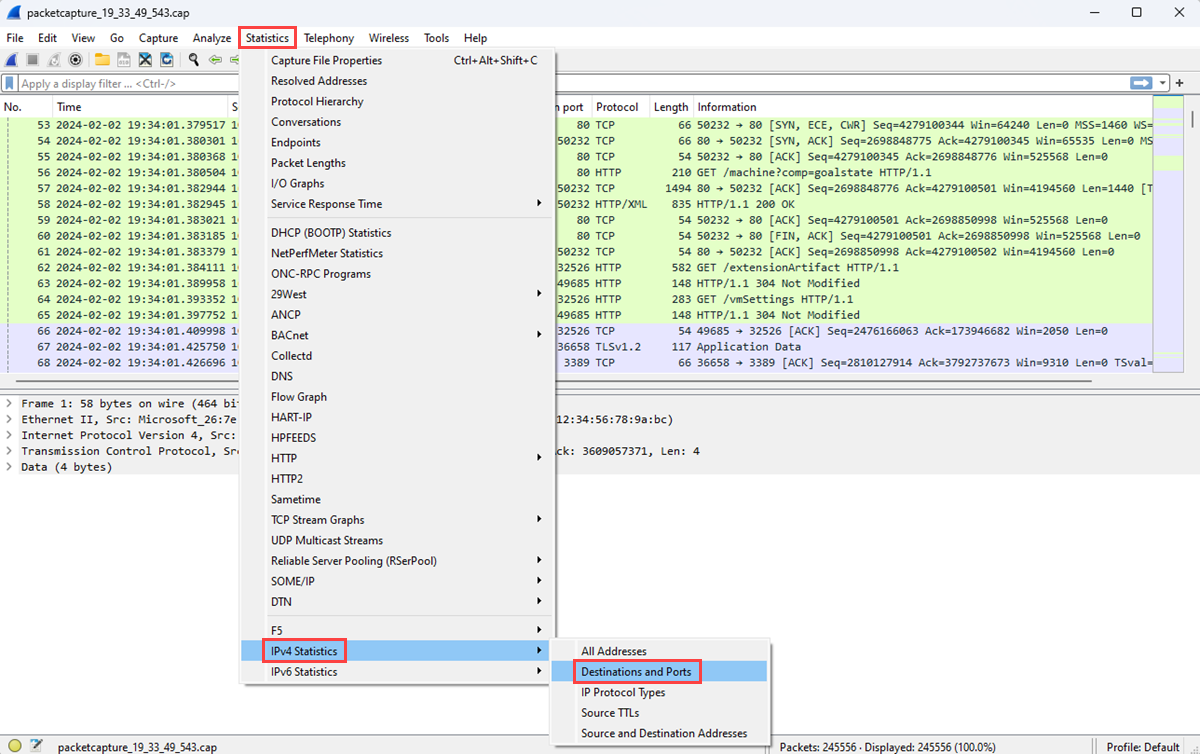
在“ 统计信息 ”菜单上,选择 “IPv4 统计信息 ”,然后选择“ 目标”和“端口”。
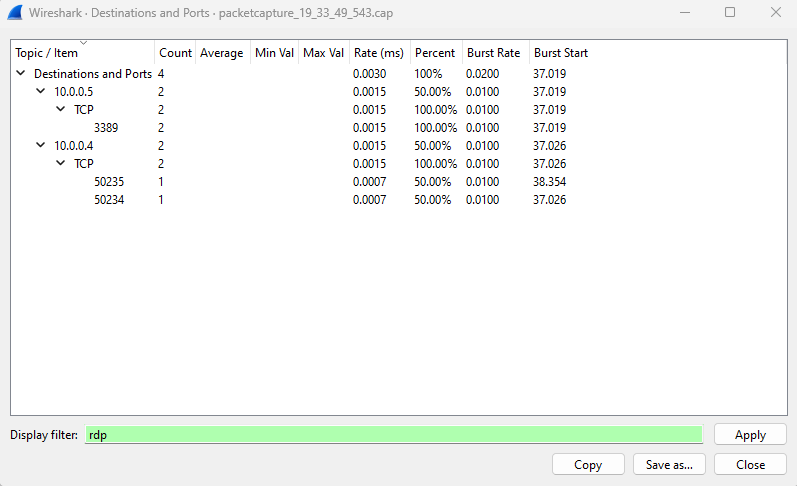
“ 目标和端口 ”窗口列出了 VM 在捕获会话期间与之通信的首要目标和端口。 通过筛选器仅显示特定协议的通信。 例如,可以通过在“显示筛选器”框中输入 rdp 来查看是否使用了任何通信的远程桌面协议(RDP)。
同样,可以筛选你感兴趣的其他协议。
后续步骤
若要了解网络观察程序的其他网络诊断工具,请参阅: