本文介绍如何使用 Azure 网络观察程序 VPN 故障排除功能来诊断和排查 VPN 网关及其与本地 VPN 设备的连接问题。
通过 VPN 故障排除,可以快速诊断网关和连接的问题。 它会检查常见问题,并返回可用于进一步排查问题的诊断日志列表。 日志存储在指定的存储帐户中。
先决条件
具有活动订阅的 Azure 帐户。 创建试用版订阅。
本地网络中的 VPN 设备由 Azure 中的本地网关表示。 有关本地网关的详细信息,请参阅 创建本地网关。 有关已验证的 VPN 设备的列表,请参阅已验证的 VPN 设备。
Azure 中具有站点到站点连接的 VPN 虚拟网关。 有关虚拟网关的详细信息,请参阅创建 VPN 网关和默认 IPsec/IKE 参数。
使用网络观察程序 VPN 故障排除进行故障排除
使用网络观察程序的 VPN 故障排除功能来诊断和排查 VPN 网关及其与本地网络的连接问题。
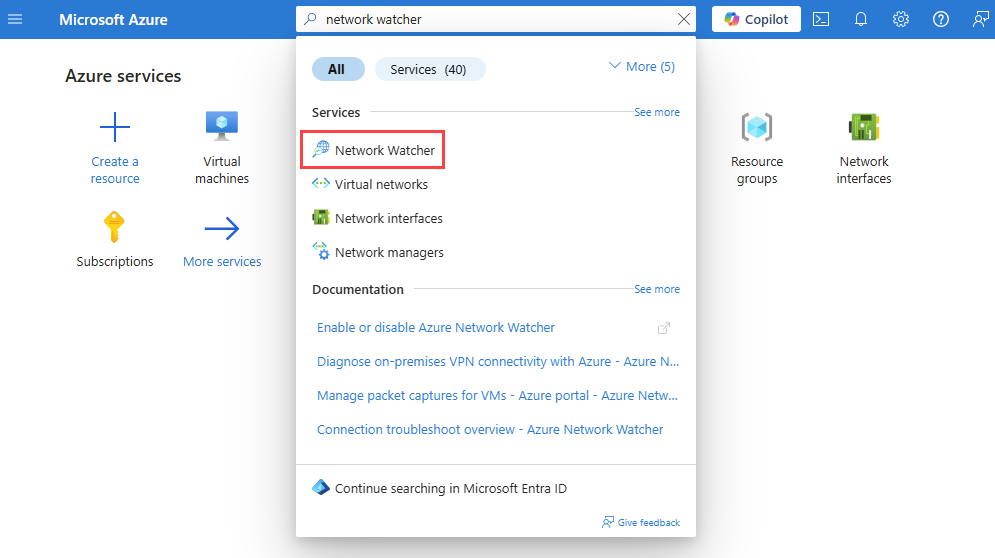
在门户顶部的搜索框中,输入“网络观察程序”。 在搜索结果中,选择“网络观察程序”。
在“网络诊断工具”下,选择“VPN 故障排除”。
在“VPN 故障排除”中,选择“选择存储帐户”选择或创建用于保存诊断文件的标准存储帐户。
选择要进行故障排除的虚拟网关和连接。
选择“开始故障排除”。
检查完成后,会显示网关和连接的故障排除状态。 “运行不正常”状态指示资源出现问题。
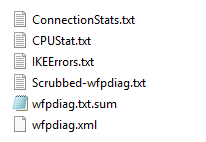
转到之前指定的存储帐户中的 vpn 容器,并下载 VPN 故障排除检查会话期间生成的 zip 文件。 网络观察程序创建包含以下诊断日志文件的 zip 文件夹:
注意
- 在某些情况下,仅生成部分日志文件。
- 较新的网关版本使用 IkeLogs.txt 文件,而不是 IKEErrors.txt、Scrubbed-wfpdiag.txt 和 wfpdiag.txt.sum。 IkeLogs.txt 包含整个 IKE 活动,包括任何错误。
常见的错误配置错误是由于使用了不正确的共享密钥,可以检查 IKEErrors.txt 找到以下错误消息:
Error: Authentication failed. Check shared key.
另一个常见错误是由于 IPsec 参数配置错误,可以在 IKEErrors.txt 文件中找到以下错误消息:
Error: On-premises device rejected Quick Mode settings. Check values.
based on log : Peer sent NO_PROPOSAL_CHOSEN notify
有关网络观察程序可以诊断的故障类型及其日志的详细列表,请参阅网关故障和连接故障。