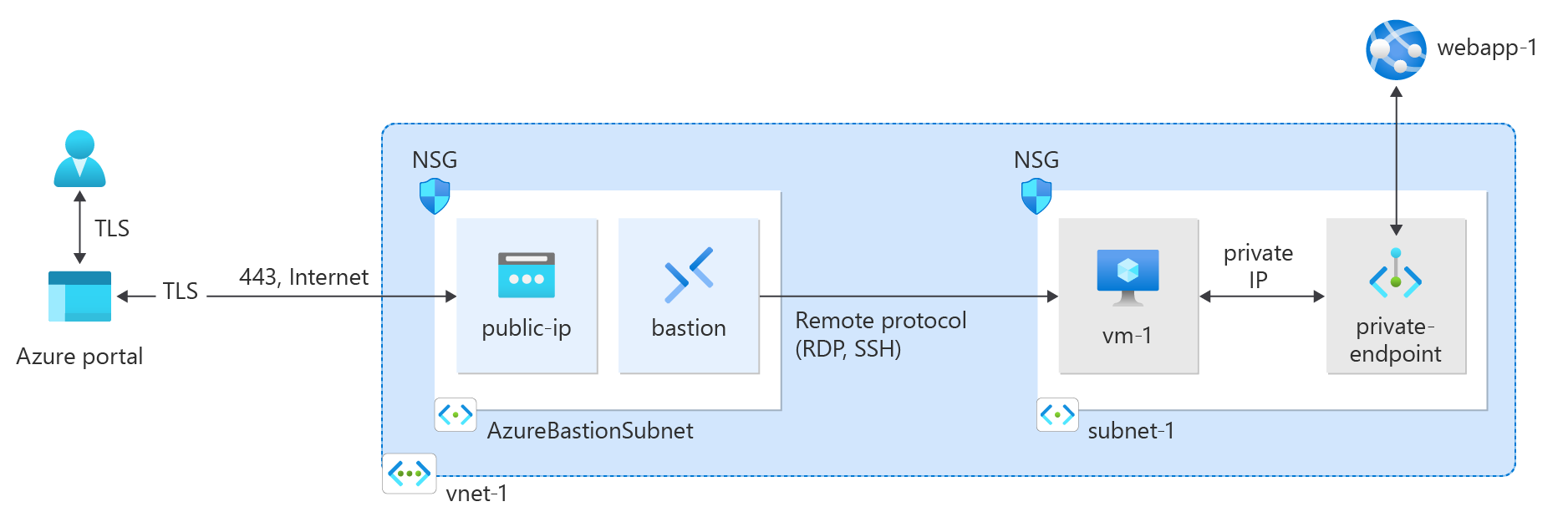
创建并使用专用终结点安全连接到 Azure 应用服务以开始使用 Azure 专用链接。
在本快速入门中,创建 Azure 应用服务 Web 应用的专用终结点,然后部署虚拟机 (VM) 以测试专用连接。
你可以为各种 Azure 服务(例如 Azure SQL 和 Azure 存储)创建专用终结点。
先决条件
具有活动订阅的 Azure 帐户。 如果还没有 Azure 帐户,请创建一个试用订阅。
部署在 Azure 订阅中且支持 PremiumV2 层或更高版本应用服务计划的 Azure Web 应用。
有关详细信息及示例,请参阅快速入门:在 Azure 中创建 ASP.NET Core Web 应用。
本文中的示例 Web 应用名为 webapp-1。 请将示例名称替换为你自己的 Web 应用名称。
Azure PowerShell。
可在本地安装 Azure PowerShell 来运行 cmdlet。 本文中的示例需要版本 5.4.1 或更高版本的 Azure PowerShell 模块。 运行
Get-Module -ListAvailable Az来查找已安装的版本。 如果需要升级,请参阅更新 Azure PowerShell 模块。如要在本地运行 PowerShell,请运行
Connect-AzAccount -Environment AzureChinaCloud以连接到 Azure。
创建资源组
Azure 资源组是在其中部署和管理 Azure 资源的逻辑容器。
使用 New-AzResourceGroup 创建资源组:
$rg = @{
Name = 'test-rg'
Location = 'chinaeast2'
}
New-AzResourceGroup @rg
创建虚拟网络
使用 New-AzVirtualNetwork 在 test-rg 资源组和 chinaeast2 位置创建 IP 地址前缀为 10.0.0.0/16、名为“vnet-1”的虚拟网络。
$vnet = @{ Name = 'vnet-1' ResourceGroupName = 'test-rg' Location = 'chinaeast2' AddressPrefix = '10.0.0.0/16' } $virtualNetwork = New-AzVirtualNetwork @vnetAzure 将资源部署到虚拟网络中的子网。 使用 Add-AzVirtualNetworkSubnetConfig 创建名为“subnet-1”、地址前缀为 10.0.0.0/24 的子网配置。
$subnet = @{ Name = 'subnet-1' VirtualNetwork = $virtualNetwork AddressPrefix = '10.0.0.0/24' } $subnetConfig = Add-AzVirtualNetworkSubnetConfig @subnet然后,使用 Set-AzVirtualNetwork 将子网配置关联到虚拟网络。
$virtualNetwork | Set-AzVirtualNetwork
部署 Azure Bastion
Azure Bastion 使用浏览器通过安全外壳 (SSH) 或远程桌面协议 (RDP),通过使用其专用 IP 地址连接虚拟网络中的虚拟机。 虚拟机不需要公共 IP 地址、客户端软件或特殊配置。 有关 Azure Bastion 的详细信息,请参阅 Azure Bastion。
注意
每小时定价从部署 Bastion 的时刻开始计算,无论出站数据的使用情况如何。 有关详细信息,请参阅定价和 SKU。 如果要将 Bastion 部署为教程或测试的一部分,建议在此资源使用完成后将其删除。
为虚拟网络配置 Azure Bastion 子网。 此子网专为 Azure Bastion 资源保留,且必须命名为 AzureBastionSubnet。
$subnet = @{ Name = 'AzureBastionSubnet' VirtualNetwork = $virtualNetwork AddressPrefix = '10.0.1.0/26' } $subnetConfig = Add-AzVirtualNetworkSubnetConfig @subnet设置配置。
$virtualNetwork | Set-AzVirtualNetwork为 Azure Bastion 创建一个公共 IP 地址。 堡垒主机使用公共 IP 通过端口 443 访问安全外壳 (SSH) 和远程桌面协议 (RDP)。
$ip = @{ ResourceGroupName = 'test-rg' Name = 'public-ip' Location = 'chinaeast2' AllocationMethod = 'Static' Sku = 'Standard' Zone = 1,2,3 } New-AzPublicIpAddress @ip使用 New-AzBastion 命令在 AzureBastionSubnet 中创建新的标准 SKU Azure Bastion 主机。
$bastion = @{ Name = 'bastion' ResourceGroupName = 'test-rg' PublicIpAddressRgName = 'test-rg' PublicIpAddressName = 'public-ip' VirtualNetworkRgName = 'test-rg' VirtualNetworkName = 'vnet-1' Sku = 'Basic' } New-AzBastion @bastion
部署 Bastion 资源大约需要几分钟。
创建专用终结点
需要使用一个支持专用终结点的 Azure 服务来设置专用终结点和连接到虚拟网络。 对于本文中的示例,我们将使用先决条件中提到的 Azure 应用服务 Web 应用。 有关支持专用终结点的 Azure 服务的详细信息,请参阅 Azure 专用链接可用性。
专用终结点可以有静态或动态分配的 IP 地址。
重要
必须事先部署 Azure 应用服务 Web 应用才能继续执行本文中的步骤。 有关详细信息,请参阅先决条件。
在本部分,你将:
使用 New-AzPrivateLinkServiceConnection 创建专用链接服务连接。
使用 New-AzPrivateEndpoint 创建专用终结点。
(可选)使用 New-AzPrivateEndpointIpConfiguration 创建专用终结点静态 IP 配置。
## Place the previously created webapp into a variable. ##
$webapp = Get-AzWebApp -ResourceGroupName test-rg -Name webapp-1
## Create the private endpoint connection. ##
$pec = @{
Name = 'connection-1'
PrivateLinkServiceId = $webapp.ID
GroupID = 'sites'
}
$privateEndpointConnection = New-AzPrivateLinkServiceConnection @pec
## Place the virtual network you created previously into a variable. ##
$vnet = Get-AzVirtualNetwork -ResourceGroupName 'test-rg' -Name 'vnet-1'
## Create the private endpoint. ##
$pe = @{
ResourceGroupName = 'test-rg'
Name = 'private-endpoint'
Location = 'chinaeast2'
Subnet = $vnet.Subnets[0]
PrivateLinkServiceConnection = $privateEndpointConnection
}
New-AzPrivateEndpoint @pe
配置专用 DNS 区域
专用 DNS 区域用于解析虚拟网络中专用终结点的 DNS 名称。 对于此示例,我们将使用 Azure 应用服务 Web 应用的 DNS 信息。有关专用终结点的 DNS 配置的详细信息,请参阅 Azure 专用终结点 DNS 配置。
在本部分,你将:
使用 New-AzPrivateDnsZone 创建新的专用 Azure DNS 区域
使用 New-AzPrivateDnsVirtualNetworkLink 将 DNS 区域链接到先前创建的虚拟网络
使用 New-AzPrivateDnsZoneConfig 创建 DNS 区域配置
使用 New-AzPrivateDnsZoneGroup 创建 DNS 区域组
## Place the virtual network into a variable. ##
$vnet = Get-AzVirtualNetwork -ResourceGroupName 'test-rg' -Name 'vnet-1'
## Create the private DNS zone. ##
$zn = @{
ResourceGroupName = 'test-rg'
Name = 'privatelink.chinacloudsites.cn'
}
$zone = New-AzPrivateDnsZone @zn
## Create a DNS network link. ##
$lk = @{
ResourceGroupName = 'test-rg'
ZoneName = 'privatelink.chinacloudsites.cn'
Name = 'dns-link'
VirtualNetworkId = $vnet.Id
}
$link = New-AzPrivateDnsVirtualNetworkLink @lk
## Configure the DNS zone. ##
$cg = @{
Name = 'privatelink.chinacloudsites.cn'
PrivateDnsZoneId = $zone.ResourceId
}
$config = New-AzPrivateDnsZoneConfig @cg
## Create the DNS zone group. ##
$zg = @{
ResourceGroupName = 'test-rg'
PrivateEndpointName = 'private-endpoint'
Name = 'zone-group'
PrivateDnsZoneConfig = $config
}
New-AzPrivateDnsZoneGroup @zg
创建测试虚拟机
若要验证静态 IP 地址和专用终结点的功能,需要将一个测试虚拟机连接到虚拟网络。
在本部分,你将:
使用 Get-Credential 为虚拟机创建登录凭据
使用 New-AzNetworkInterface 为虚拟机创建网络接口
使用 New-AzVMConfig、Set-AzVMOperatingSystem、Set-AzVMSourceImage 和 Add-AzVMNetworkInterface 创建虚拟机配置
使用 New-AzVM 创建虚拟机
## Create the credential for the virtual machine. Enter a username and password at the prompt. ##
$cred = Get-Credential
## Place the virtual network into a variable. ##
$vnet = Get-AzVirtualNetwork -Name vnet-1 -ResourceGroupName test-rg
## Create a network interface for the virtual machine. ##
$nic = @{
Name = 'nic-1'
ResourceGroupName = 'test-rg'
Location = 'chinaeast2'
Subnet = $vnet.Subnets[0]
}
$nicVM = New-AzNetworkInterface @nic
## Create the configuration for the virtual machine. ##
$vm1 = @{
VMName = 'vm-1'
VMSize = 'Standard_DS1_v2'
}
$vm2 = @{
ComputerName = 'vm-1'
Credential = $cred
}
$vm3 = @{
PublisherName = 'MicrosoftWindowsServer'
Offer = 'WindowsServer'
Skus = '2022-Datacenter'
Version = 'latest'
}
$vmConfig =
New-AzVMConfig @vm1 | Set-AzVMOperatingSystem -Windows @vm2 | Set-AzVMSourceImage @vm3 | Add-AzVMNetworkInterface -Id $nicVM.Id
## Create the virtual machine. ##
New-AzVM -ResourceGroupName 'test-rg' -Location 'chinaeast2' -VM $vmConfig
注意
虚拟网络中具有堡垒主机的虚拟机不需要公共 IP 地址。 Bastion 提供公共 IP,虚拟机使用专用 IP 在网络中进行通信。 可以从堡垒托管的虚拟网络的任何虚拟机中删除公共 IP。 有关详细信息,请参阅 将公共 IP 地址与 Azure VM 取消关联。
注意
Azure 会为未分配公共 IP 地址的 VM 或位于内部基本 Azure 负载均衡器的后端池中的 VM 提供默认出站访问 IP。 默认出站访问 IP 机制会提供不可配置的出站 IP 地址。
发生以下事件之一时,将禁用默认出站访问 IP:
- 将公共 IP 地址分配给 VM。
- 虚拟机被放置在标准负载平衡器的后端池中,有无出站规则均可。
- 向 VM 的子网分配了 Azure NAT 网关资源。
在灵活业务流程模式下通过使用虚拟机规模集创建的 VM 没有默认的出站访问权限。
有关 Azure 中的出站连接的详细信息,请参阅 Azure 中的默认出站访问权限和使用用于出站连接的源网络地址转换 (SNAT)。
测试到专用终结点的连接
使用之前创建的虚拟机,通过专用终结点连接到 Web 应用。
在门户顶部的搜索框中,输入“虚拟机”。 选择“虚拟机”。
选择 vm-1。
在 vm-1 的“概述”页中,选择“连接”,然后选择“堡垒”选项卡。
选择“使用 Bastion”。
输入创建 VM 时使用的用户名和密码。
选择“连接”。
连接后,在服务器上打开 PowerShell。
输入
nslookup webapp-1.chinacloudsites.cn。 你会收到类似于以下示例的消息:Server: UnKnown Address: 168.63.129.16 Non-authoritative answer: Name: webapp-1.privatelink.chinacloudsites.cn Address: 10.0.0.10 Aliases: webapp-1.chinacloudsites.cn如果在前面的步骤中选择了静态 IP 地址,则会为 Web 应用程序名称返回专用 IP 地址 10.0.0.10。 此地址位于你之前创建的虚拟网络的子网中。
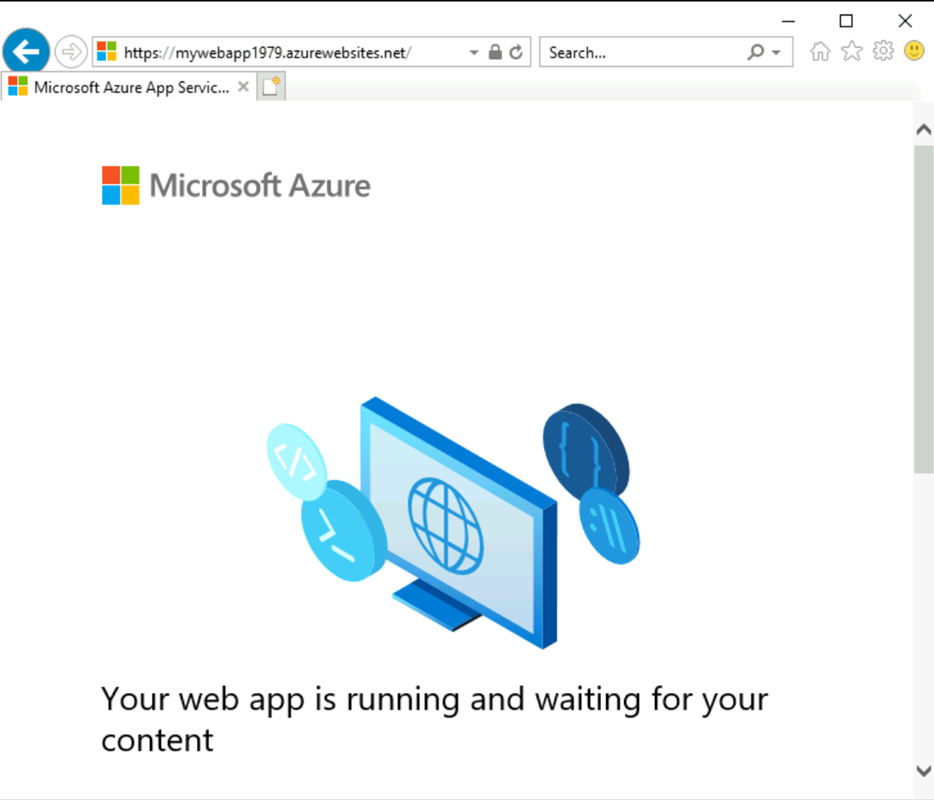
在与 vm-1 的堡垒连接中,打开 Web 浏览器。
输入 Web 应用的 URL,即
https://webapp-1.chinacloudsites.cn。如果你的 Web 应用尚未部署,你会看到以下默认 Web 应用页:
清理资源
如果不再需要资源组、虚拟网络和剩余资源,可以使用 Remove-AzResourceGroup 命令将其删除。
Remove-AzResourceGroup -Name 'test-rg'
后续步骤
要详细了解支持专用终结点的服务,请参阅: