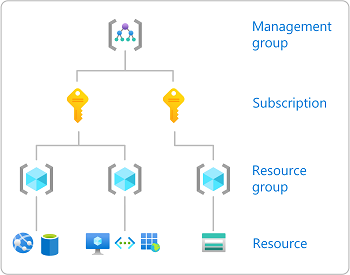
范围 是访问权限应用于的资源集。 分配角色时,请务必了解范围,以便你可以仅授予安全主体真正需要的访问权限。 通过限制范围,可以减少安全权限主体遭到入侵时面临风险的资源。
范围级别
在 Azure 中,可以在以下四个级别指定范围:管理组、订阅、资源组和资源。 范围采用父子关系结构。 层次结构的每个级别都会使范围更具针对性。 可以在其中任何一个范围级别分配角色。 所选级别决定了角色的应用广泛程度。 较低级别继承较高级别的角色权限。
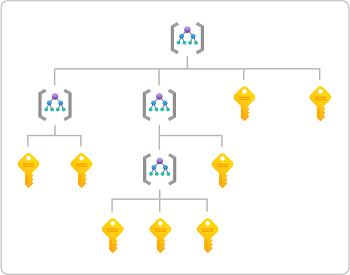
管理组是比订阅更高的范围级别,同时支持更复杂的层次结构。 下图显示了可以定义的管理组和订阅层次结构的示例。 有关管理组的详细信息,请参阅 什么是 Azure 管理组?
范围格式
如果使用命令行分配角色,则需要指定范围。 对于命令行工具,范围是一个潜在的长字符串,用于标识角色分配的确切范围。 在 Azure 门户中,此范围通常列为 资源 ID。
范围由由斜杠(/)字符分隔的一系列标识符组成。 可以将此字符串视为表示以下层次结构,其中没有占位符({})的文本是固定标识符:
/subscriptions
/{subscriptionId}
/resourcegroups
/{resourceGroupName}
/providers
/{providerName}
/{resourceType}
/{resourceSubType1}
/{resourceSubType2}
/{resourceName}
-
{subscriptionId}是要使用的订阅的 ID(GUID)。 -
{resourceGroupName}是包含资源组的名称。 -
{providerName}是处理资源的资源提供程序的名称,然后{resourceType}{resourceSubType*}标识该资源提供程序中的进一步级别。 -
{resourceName}是标识特定资源的字符串的最后一部分。
管理组高于订阅级别,具有最广泛的(最不具体的)范围。 此级别的角色分配适用于管理组中的订阅。 管理组的范围采用以下格式:
/providers
/Microsoft.Management
/managementGroups
/{managementGroupName}
范围示例
| Scope | 示例: |
|---|---|
| 管理组 | /providers/Microsoft.Management/managementGroups/marketing-group |
| 订阅 | /subscriptions/00000000-0000-0000-0000-000000000000 |
| 资源组 | /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/Example-Storage-rg |
/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/pharma-sales |
|
| 资源 | /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/Example-Storage-rg/providers/Microsoft.Storage/storageAccounts/azurestorage12345/blobServices/default/containers/blob-container-01 |
/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/MyVirtualNetworkResourceGroup/providers/Microsoft.Network/virtualNetworks/MyVirtualNetwork12345 |
如何确定资源的范围
确定管理组、订阅或资源组的范围相当简单。 只需知道名称和订阅 ID。 但是,确定资源的范围需要更多工作。 可通过以下几种方法来确定资源的范围。
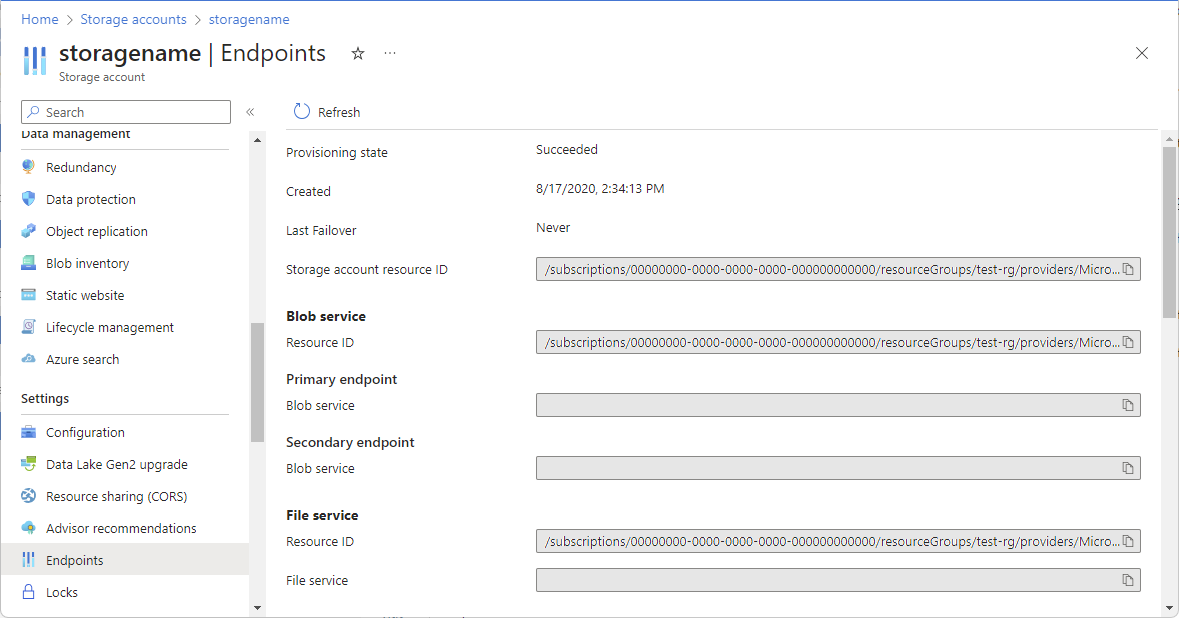
在 Azure 门户中,打开资源,然后查看属性。 资源应列出资源 ID ,可在其中确定范围。 例如,下面是存储帐户的资源 ID。
另一种方法是使用 Azure 门户暂时在资源范围内分配角色,然后使用 Azure PowerShell 或 Azure CLI 列出角色分配。 在输出中,范围将列为属性。
RoleAssignmentId : /subscriptions/<subscriptionId>/resourceGroups/test-rg/providers/Microsoft.Storage/storageAccounts/azurestorage12345/blobServices/default/containers/blob-container-01/pro viders/Microsoft.Authorization/roleAssignments/<roleAssignmentId> Scope : /subscriptions/<subscriptionId>/resourceGroups/test-rg/providers/Microsoft.Storage/storageAccounts/azurestorage12345/blobServices/default/containers/blob-container-01 DisplayName : User SignInName : user@contoso.com RoleDefinitionName : Storage Blob Data Reader RoleDefinitionId : 2a2b9908-6ea1-4ae2-8e65-a410df84e7d1 ObjectId : <principalId> ObjectType : User CanDelegate : False Description : ConditionVersion : Condition :{ "canDelegate": null, "condition": null, "conditionVersion": null, "description": null, "id": "/subscriptions/{subscriptionId}/resourceGroups/Example-Storage-rg/providers/Microsoft.Storage/storageAccounts/azurestorage12345/blobServices/default/containers/blob-container-01/providers/Microsoft.Authorization/roleAssignments/{roleAssignmentId}", "name": "{roleAssignmentId}", "principalId": "{principalId}", "principalName": "user@contoso.com", "principalType": "User", "resourceGroup": "test-rg", "roleDefinitionId": "/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/2a2b9908-6ea1-4ae2-8e65-a410df84e7d1", "roleDefinitionName": "Storage Blob Data Reader", "scope": "/subscriptions/{subscriptionId}/resourceGroups/Example-Storage-rg/providers/Microsoft.Storage/storageAccounts/azurestorage12345/blobServices/default/containers/blob-container-01", "type": "Microsoft.Authorization/roleAssignments" }
范围和 ARM 模板
角色分配是 Azure 资源管理器中称为 扩展资源的特殊类型。 扩展资源是扩展另一资源的功能的资源。 它们总是作为其他资源的一个扩展(类似于子项)存在。 例如,在订阅范围内的角色分配是订阅的扩展资源。 角色分配的名称始终是您要扩展的资源的名称加上/Microsoft.Authorization/roleAssignments/{roleAssignmentId}。 使用 Azure 资源管理器模板(ARM 模板)分配角色时,通常不需要提供范围。 原因是范围字段最终总是成为您正在扩展的资源的 ID。 可以从角色分配本身的 ID 确定范围。 下表显示了角色分配 ID 和相应范围的示例:
| 角色分配标识 | Scope |
|---|---|
/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleAssignments/{roleAssignmentId} |
/subscriptions/{subscriptionId} |
/subscriptions/{subscriptionId}/resourceGroups/Example-Storage-rg/providers/Microsoft.Authorization/roleAssignments/{roleAssignmentId} |
/subscriptions/{subscriptionId}/resourceGroups/Example-Storage-rg |
有关范围和 ARM 模板的详细信息,请参阅 使用 Azure 资源管理器模板分配 Azure 角色。 有关扩展资源类型的完整列表,请参阅用于扩展其他资源的功能的资源类型。