Azure AI 搜索支持基于标识的身份验证和基于密钥的身份验证(默认值),以便连接到搜索服务。
如果请求和 API 密钥都有效,并且搜索服务配置为允许请求上的 API 密钥,则接受对搜索服务终结点发出的请求。
重要
创建搜索服务时,基于密钥的身份验证是默认设置,但它不是最安全的选项。 建议将其替换为基于角色的访问。
默认启用
在 Azure 门户中,身份验证是在“设置>”页上指定的。 设置为 API 密钥(默认值)或 两者皆可时,允许请求使用 API 密钥的选项。
密钥类型
API 密钥是由 52 个随机生成的数字和字母组成的唯一字符串。 在表面上,管理密钥与查询密钥之间没有区别。 如果无法跟踪应用程序中指定了哪种类型的密钥,可以在 Azure 门户中检查密钥值。
有两种类型的密钥用于对请求进行身份验证:
| 类型 |
权限级别 |
创建方式 |
最大值 |
| 管理员 |
所有数据平面(内容)操作的完整访问权限(读写) |
创建服务时会生成两个管理密钥( 主 密钥和 辅助密钥),并且可以按需单独重新生成。 使用两个密钥可以让您在继续使用第二个密钥访问服务的同时,切换另一个密钥。 |
2 |
| 查询 |
只读访问权限,范围限定为搜索索引的文档集合 |
在服务中生成一个查询密钥。 搜索服务管理员可按需创建更多密钥。 |
50 |
查找现有密钥
可以使用 Azure 门户、 PowerShell、 Azure CLI 或 REST API 查看和管理 API 密钥。
运行以下命令,分别返回管理员和查询 API 密钥。 有关 REST 的帮助,请参阅 使用 REST API 管理 Azure AI 搜索服务。
返回管理密钥:
POST https://management.chinacloudapi.cn/subscriptions/{{subscriptionId}}/resourceGroups/{{resource-group}}/providers//Microsoft.Search/searchServices/{{search-service-name}}/listAdminKeys?api-version=2025-05-01
返回查询密钥:
POST https://management.chinacloudapi.cn/subscriptions/{{subscriptionId}}/resourceGroups/{{resource-group}}/providers//Microsoft.Search/searchServices/{{search-service-name}}/listAdminKeys?api-version=2025-05-01
参考:管理密钥 - 获取、 查询密钥 - 按搜索服务列出
使用用于 Python 的 Azure SDK 以编程方式检索 API 密钥。 安装管理 SDK:
pip install azure-mgmt-search azure-identity
运行以下代码以返回管理员和查询 API 密钥:
import os
from azure.identity import DefaultAzureCredential
from azure.mgmt.search import SearchManagementClient
# Set up variables
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
resource_group = "your-resource-group"
search_service_name = "your-search-service"
# Create the management client
credential = DefaultAzureCredential()
client = SearchManagementClient(credential, subscription_id)
# Get admin keys
admin_keys = client.admin_keys.get(resource_group, search_service_name)
print(f"Primary admin key: {admin_keys.primary_key}")
print(f"Secondary admin key: {admin_keys.secondary_key}")
# Get query keys
query_keys = client.query_keys.list_by_search_service(resource_group, search_service_name)
for key in query_keys:
print(f"Query key '{key.name}': {key.key}")
Reference:SearchManagementClient | AdminKeys | QueryKeys
运行以下命令,分别返回管理员和查询 API 密钥。 有关 PowerShell 的帮助,请参阅 使用 PowerShell 管理 Azure AI 搜索服务。
安装 Az.Search 模块:
Install-Module Az.Search
返回管理密钥:
Get-AzSearchAdminKeyPair -ResourceGroupName <resource-group-name> -ServiceName <search-service-name>
返回查询密钥:
Get-AzSearchQueryKey -ResourceGroupName <resource-group-name> -ServiceName <search-service-name>
运行以下命令,分别返回管理员和查询 API 密钥。 有关 Azure CLI 的帮助,请参阅 使用 Azure CLI 管理 Azure AI 搜索服务。
返回管理密钥:
az search admin-key show --resource-group <myresourcegroup> --service-name <myservice>
返回查询密钥:
az search query-key list --resource-group <myresourcegroup> --service-name <myservice>
在连接上使用密钥
基于密钥的身份验证仅用于数据平面(内容)请求,例如创建或查询索引以及使用 搜索服务 REST API 执行的任何其他作。
在源代码中,可以直接在请求标头中指定 API 密钥。 或者,可以将它存储为项目中的 环境变量 或应用设置,然后在请求中引用该变量。
- 管理密钥用于创建、修改或删除对象。
- 管理密钥还用于 GET 对象定义和系统信息,例如 LIST 索引 或 GET 服务统计信息。
- 查询密钥通常会分发到发出查询的客户端应用程序。
回想一下,密钥身份验证默认已启用,并支持数据平面作,例如索引和查询。
但是,如果你禁用 API 密钥并设置角色分配,则 Azure 门户会改用角色分配。
在请求头中设置管理密钥。 不能在 URI 或请求正文中传递管理密钥。
下面是对“创建索引”请求使用管理 API 密钥的示例:
@baseUrl=https://my-demo-search-service.search.azure.cn
@adminApiKey=aaaabbbb-0000-cccc-1111-dddd2222eeee
### Create an index
POST {{baseUrl}}/indexes?api-version=2025-09-01 HTTP/1.1
Content-Type: application/json
api-key: {{adminApiKey}}
{
"name": "my-new-index",
"fields": [
{"name": "docId", "type": "Edm.String", "key": true, "filterable": true},
{"name": "Name", "type": "Edm.String", "searchable": true }
]
}
在 POST 的请求标头或 GET 的 URI 上设置查询密钥。 查询键用于针对 index/docs 集合的操作:搜索文档、自动完成、建议或通过 GET 获取文档。
下面是对搜索文档 (GET) 请求的查询 API 密钥用法示例:
### Query an index
GET /indexes/my-new-index/docs?search=*&api-version=2025-09-01&api-key={{queryApiKey}}
注意
在请求 URI 中传递敏感数据(例如 api-key)的做法很不安全。 出于此原因, Azure AI 搜索仅接受使用查询密钥作为查询字符串中的 api-key。 作为经验法则,我们建议以请求标头的形式传递 api-key。
最佳做法是将 API 密钥设置为环境变量,但为简单起见,此示例将其显示为字符串。 该示例使用查询 API 密钥来进行查询操作。
# Import libraries
from azure.search.documents import SearchClient
from azure.core.credentials import AzureKeyCredential
from azure.identity import DefaultAzureCredential, AzureAuthorityHosts
# Variables for endpoint, keys, index
search_endpoint: str = "https://<Put your search service NAME here>.search.azure.cn/"
credential = AzureKeyCredential("Your search service query key")
index_name: str = "hotels-quickstart-python"
# Set up the client
search_client = SearchClient(endpoint=search_endpoint,
index_name=index_name,
credential=credential)
# Run the query
results = search_client.search(query_type='simple',
search_text="*" ,
select='HotelName,Description,Tags',
include_total_count=True)
print ('Total Documents Matching Query:', results.get_count())
for result in results:
print(result["@search.score"])
print(result["HotelName"])
print(result["Tags"])
print(f"Description: {result['Description']}")
使用以下语法在请求头中设置 API 密钥:
$headers = @{
'api-key' = '<YOUR-ADMIN-OR-QUERY-API-KEY>'
'Content-Type' = 'application/json'
'Accept' = 'application/json' }
使用变量存储完全限定的查询。
$url = '<YOUR-SEARCH-SERVICE>/indexes/hotels-quickstart/docs?api-version=2025-09-01&search=attached restaurant&searchFields=Description,Tags&$select=HotelId,HotelName,Tags,Description&$count=true'
将请求发送到搜索服务:
Invoke-RestMethod -Uri $url -Headers $headers | ConvertTo-Json
有关其他作的更多脚本示例,请参阅 快速入门:使用 REST API 在 PowerShell 中创建 Azure AI 搜索索引。
创建查询密钥
查询密钥用于对面向文档集合的操作索引中的文档进行只读访问。 搜索、筛选和建议查询都是采用查询密钥的操作。 返回系统数据或对象定义(例如索引定义或索引器状态)的所有只读操作需要管理密钥。
限制客户端应用中的访问和操作对于保护服务中的搜索资产至关重要。 对于源自客户端应用的任何查询,请始终使用查询密钥而不是管理密钥。
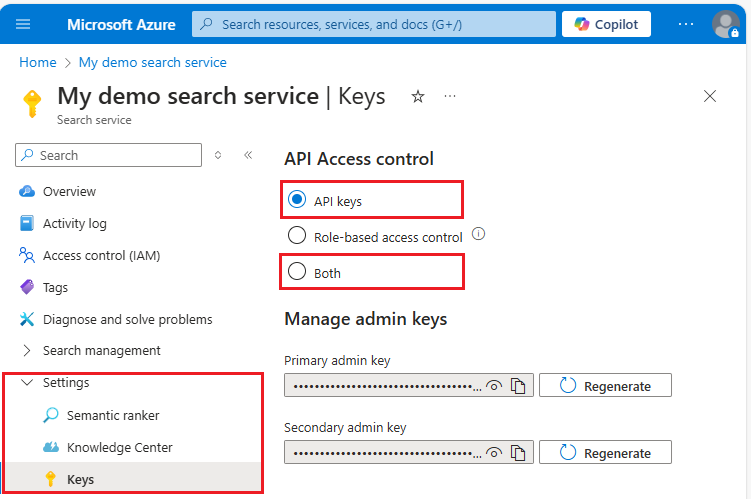
登录到 Azure 门户并查找你的搜索服务。
在左窗格中,选择“设置>”以查看 API 密钥。
在“管理查询密钥”下,使用已为服务生成的查询密钥,或创建新的查询密钥。 默认查询密钥未命名,但生成的其他查询密钥可命名以便于管理。
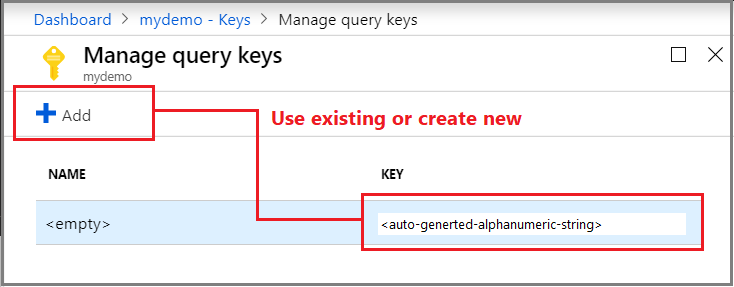
在管理 REST API 中使用创建查询密钥。
必须具有有效的角色分配才能创建或管理 API 密钥。 有关使用 REST API 满足角色要求的指导,请参阅使用 REST API 管理 Azure AI 搜索服务。
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Search/searchServices/{searchServiceName}/createQueryKey/{name}?api-version=2025-05-01
重新生成管理员密钥
系统将为每个服务生成两个管理密钥,以便在轮换主密钥时可以使用辅助密钥,从而实现业务连续性。
登录到 Azure 门户并查找你的搜索服务。
在左窗格中,选择“设置”“密钥”。>
复制辅助密钥。
对于所有应用程序,更新 API 密钥设置以使用辅助密钥。
重新生成主密钥。
更新所有应用程序以使用新的主密钥。
如果无意中同时重新生成了这两个密钥,则使用这些密钥的所有客户端请求将会失败并出现“HTTP 403 禁止访问”。 但是,内容不会删除,并且不会将你永久性地锁定在系统之外。
仍然可以通过 Azure 门户或通过编程方式访问该服务。 管理功能是通过订阅 ID 而不是服务 API 密钥运行的,因此,即使 API 密钥不可用,这些功能也仍可用。
通过门户或管理层创建新的密钥后,只要在请求中提供这些新密钥,就会恢复对内容(索引、索引器、数据源、同义词映射)的访问权限。
从密钥迁移到角色
若要过渡到基于角色的访问,了解密钥如何映射到 Azure AI 搜索中的内置角色会很有帮助:
- 管理员密钥对应于 搜索服务参与者 和 搜索索引数据参与者 角色。
- 查询键对应于 搜索索引数据读取者 角色。
保护密钥
使用角色分配来限制对 API 密钥的访问。
无法使用客户管理的密钥加密来加密 API 密钥。 只能对搜索服务本身中的敏感数据(例如,索引内容或数据源对象定义中的连接字符串)进行 CMK 加密。
登录到 Azure 门户并查找你的搜索服务。
在左窗格中,选择 “访问控制”(IAM),然后选择“ 角色分配 ”选项卡。
在“角色”筛选器中,选择有权查看或管理密钥的角色(所有者、参与者、搜索服务参与者)。 最终分配给这些角色的安全主体对搜索服务拥有密钥权限。
作为预防措施,另请检查“经典管理员”选项卡,以确定管理员和共同管理员是否拥有访问权限。
最佳做法
相关内容