建议先了解 Service Fabric 使用 X.509 证书的方式,并熟悉群集安全性应用场景。 在继续下一步之前,必须先了解群集证书的定义和用途。
Azure Service Fabrics SDK 的默认证书加载行为是部署和使用过期日期最远的已定义证书,而不管其主要或次要配置定义如何。 回退到经典行为是不推荐使用的高级操作,需要在 Fabric.Code 配置内将“UseSecondaryIfNever”设置参数的值设置为 false。
在创建群集期间配置证书安全性时,Service Fabric 允许指定两个群集证书(主要证书和辅助证书)以及客户端证书。 请参阅通过门户创建 Azure 群集或通过 Azure 资源管理器创建 Azure 群集,了解在创建时进行相关设置的详细信息。 如果创建时只指定了一个群集证书,将使用该证书作为主要证书。 在创建群集后,可以添加一个新证书作为辅助证书。
注意
对于安全群集,始终需要至少部署一个有效的(未吊销或过期)群集证书(主要或辅助),否则,群集无法正常运行。 在所有有效证书过期前的 90 天,系统会针对节点生成警告跟踪和警告运行状况事件。 目前,Service Fabric 仅发送了这些有关证书过期的通知。
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
使用门户添加辅助群集证书
无法通过 Azure 门户添加辅助群集证书;请使用 Azure 资源管理器。
使用门户删除群集证书
对安全群集,始终需要至少一个有效(未撤销且未过期)证书。 将使用具有最远过期日期的已部署证书,并且删除该证书会导致群集停止运行;请确保仅删除过期的证书或最快过期的未使用证书。
若要删除未使用的群集安全证书,请导航到“安全性”部分,然后在该未使用证书的上下文菜单中选择“删除”选项。
若要删除标记为“主要”的证书,则需部署一个过期日期比该主要证书更远的辅助证书,从而启用自动变换行为;并在自动变换完成后该删除主要证书。
使用 Azure 资源管理器添加辅助证书
执行这些步骤的前提是,熟悉资源管理器的工作原理,并已使用资源管理器模板至少部署了一个 Service Fabric 群集,同时已准备好在设置此群集时使用的模板。 此外,还假定可以熟练使用 JSON。
注意
如需可参考或入手的示例模板和参数,请从此 git-repo 下载。
编辑 资源管理器模板
为了便于参考,示例 5-VM-1-NodeTypes-Secure_Step2.JSON 包含我们作出的所有编辑。 该示例位于 git-repo。
请确保执行所有步骤
打开用于部署群集的资源管理器模板。 (如果已从上述存储库下载此示例,则使用 5-VM-1-NodeTypes-Secure_Step1.JSON 部署安全群集,并打开该模板)。
向模板的参数部分添加两个新参数“secCertificateThumbprint”和“secCertificateUrlValue”,类型为“string”。 可复制以下代码片段,并将其添加到该模板。 根据具体的模板源,可能已经存在这些定义,如果是这样,请转至下一步。
"secCertificateThumbprint": { "type": "string", "metadata": { "description": "Certificate Thumbprint" } }, "secCertificateUrlValue": { "type": "string", "metadata": { "description": "Refers to the location URL in your key vault where the certificate was uploaded, it is should be in the format of https://<name of the vault>.vault.azure.cn:443/secrets/<exact location>" } },对 Microsoft.ServiceFabric/clusters 资源进行更改 - 在模板中找到“Microsoft.ServiceFabric/clusters”资源定义。 在该定义的属性下,找到“Certificate”JSON 标记,如以下 JSON 代码片段所示:
"properties": { "certificate": { "thumbprint": "[parameters('certificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" }添加新标记“thumbprintSecondary”并为其指定值“[parameters('secCertificateThumbprint')]”。
资源定义现在应如下所示(根据具体的模板源,有时与下面的代码片段不完全相同)。
"properties": { "certificate": { "thumbprint": "[parameters('certificateThumbprint')]", "thumbprintSecondary": "[parameters('secCertificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" }如果要滚动更新证书,请将新证书指定为主要证书,并将当前的主要证书移为辅助证书。 这样就可以通过一个部署步骤,将当前主要证书滚动更新为新证书。
"properties": { "certificate": { "thumbprint": "[parameters('secCertificateThumbprint')]", "thumbprintSecondary": "[parameters('certificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" }对所有Microsoft.Compute/virtualMachineScaleSets 资源定义进行更改 - 查找 Microsoft.Compute/virtualMachineScaleSets 资源定义。 滚动到 "publisher":"Microsoft.Azure.ServiceFabric",位于 "virtualMachineProfile" 下。
在 Service Fabric 发布服务器设置中,应看到类似如下的内容。
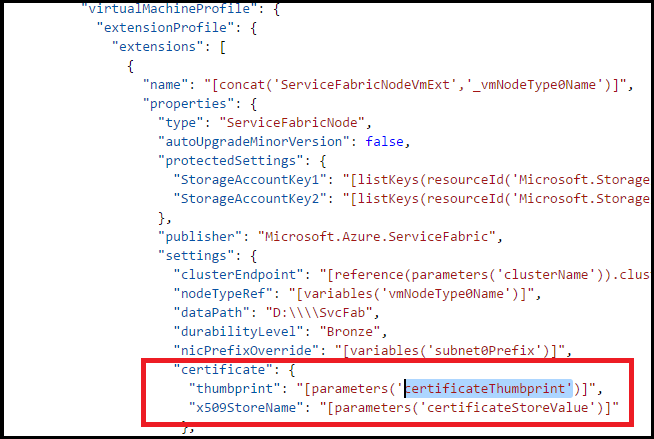
向其中添加新的证书项
"certificateSecondary": { "thumbprint": "[parameters('secCertificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" } },属性现在应如下所示
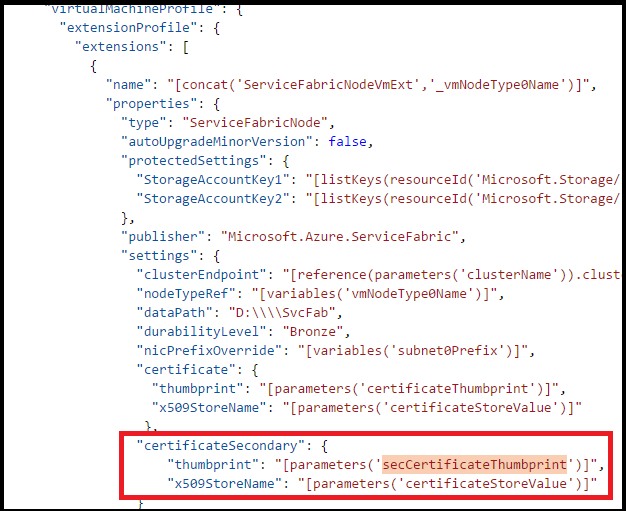
如果要滚动更新证书,请将新证书指定为主要证书,并将当前的主要证书移为辅助证书。 这样就可以通过一个部署步骤,将当前证书滚动更新为新证书。
"certificate": { "thumbprint": "[parameters('secCertificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" }, "certificateSecondary": { "thumbprint": "[parameters('certificateThumbprint')]", "x509StoreName": "[parameters('certificateStoreValue')]" } },属性现在应如下所示
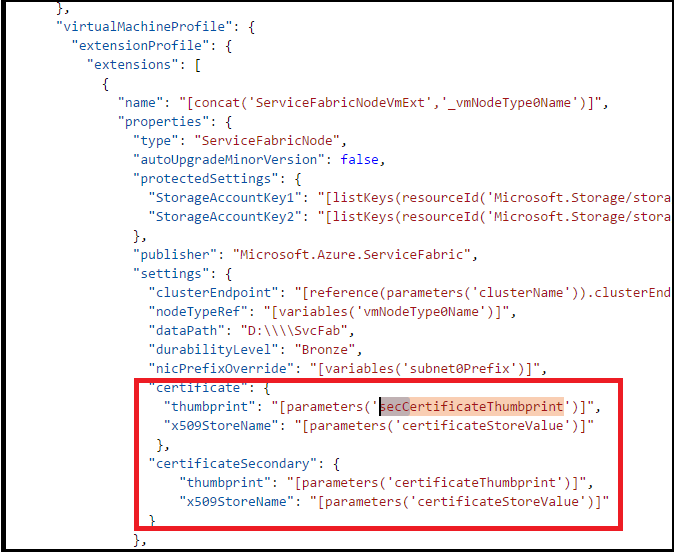
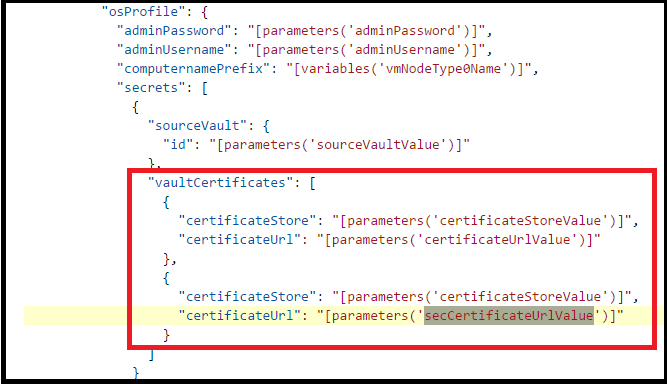
对所有Microsoft.Compute/virtualMachineScaleSets 资源定义进行更改 - 查找 Microsoft.Compute/virtualMachineScaleSets 资源定义。 滚动到 "vaultCertificates":,位于 "OSProfile" 下。 应该会看到类似下面的屏幕。
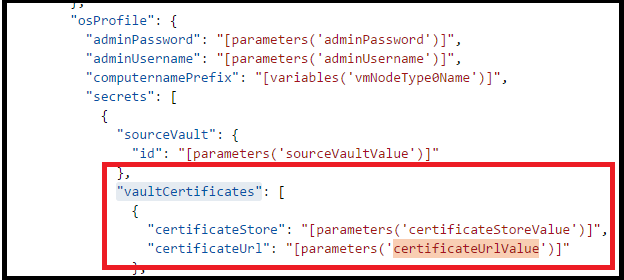
将 secCertificateUrlValue 添加到它。使用以下代码片段:
{ "certificateStore": "[parameters('certificateStoreValue')]", "certificateUrl": "[parameters('secCertificateUrlValue')]" }现在,生成的 Json 应如下所示。
注意
请确保已对模板中的 Nodetypes/Microsoft.Compute/virtualMachineScaleSets 资源定义重复执行了步骤 4 和 5。 如果缺少其中一个,证书将无法安装在该虚拟机规模集上,并且在群集(包括停止运行的群集)上产生不可预知的结果(如果最终没有群集可用于安全性的有效证书)。 因此在继续之前,请仔细检查。
编辑模板文件,反映前面添加的新参数
如果参考了 git-repo 中的示例,便可开始更改示例 5-VM-1-NodeTypes-Secure.parameters_Step2.JSON
编辑 Resource Manager 模板参数文件,添加 secCertificateThumbprint 和 secCertificateUrlValue 的两个新参数。
"secCertificateThumbprint": {
"value": "thumbprint value"
},
"secCertificateUrlValue": {
"value": "Refers to the location URL in your key vault where the certificate was uploaded, it is should be in the format of https://<name of the vault>.vault.azure.cn:443/secrets/<exact location>"
},
将模板部署到 Azure
- 现在可以将模板部署到 Azure。 打开 Azure PowerShell 版本 1(或更高版本)的命令提示符。
- 登录到 Azure 帐户,选择具体 Azure 订阅。 对于有权访问多个 Azure 订阅的用户而言,这是一个重要步骤。
Connect-AzAccount -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId <Subscription ID>
部署模板之前先进行测试。 使用群集当前部署到的同一个资源组。
Test-AzResourceGroupDeployment -ResourceGroupName <Resource Group that your cluster is currently deployed to> -TemplateFile <PathToTemplate>
将模板部署到该资源组。 使用群集当前部署到的同一个资源组。 运行 New-AzResourceGroupDeployment 命令。 无需指定模式,因为默认值为增量。
注意
如果将 Mode 设置为 Complete,可能会无意中删除不在模板中的资源。 因此请不要在此方案中使用该模式。
New-AzResourceGroupDeployment -Name ExampleDeployment -ResourceGroupName <Resource Group that your cluster is currently deployed to> -TemplateFile <PathToTemplate>
下面是已填充数据的同一个 PowerShell 命令示例。
$ResourceGroup2 = "chackosecure5"
$TemplateFile = "C:\GitHub\Service-Fabric\ARM Templates\Cert Rollover Sample\5-VM-1-NodeTypes-Secure_Step2.json"
$TemplateParmFile = "C:\GitHub\Service-Fabric\ARM Templates\Cert Rollover Sample\5-VM-1-NodeTypes-Secure.parameters_Step2.json"
New-AzResourceGroupDeployment -ResourceGroupName $ResourceGroup2 -TemplateParameterFile $TemplateParmFile -TemplateUri $TemplateFile -clusterName $ResourceGroup2
部署完成后,使用新证书连接到群集,并执行一些查询。 如果能够做到。 然后便可删除旧证书。
如果使用自签名证书,请务必将它们导入本地 TrustedPeople 证书存储。
######## Set up the certs on your local box
Import-PfxCertificate -Exportable -CertStoreLocation Cert:\CurrentUser\TrustedPeople -FilePath c:\Mycertificates\chackdanTestCertificate9.pfx -Password (ConvertTo-SecureString -String abcd123 -AsPlainText -Force)
Import-PfxCertificate -Exportable -CertStoreLocation Cert:\CurrentUser\My -FilePath c:\Mycertificates\chackdanTestCertificate9.pfx -Password (ConvertTo-SecureString -String abcd123 -AsPlainText -Force)
以下快速参考提供了用于连接到安全群集的命令
$ClusterName= "chackosecure5.chinanorth.cloudapp.chinacloudapi.cn:19000"
$CertThumbprint= "AA11BB22CC33DD44EE55FF66AA77BB88CC99DD00"
Connect-serviceFabricCluster -ConnectionEndpoint $ClusterName -KeepAliveIntervalInSec 10 `
-X509Credential `
-ServerCertThumbprint $CertThumbprint `
-FindType FindByThumbprint `
-FindValue $CertThumbprint `
-StoreLocation CurrentUser `
-StoreName My
以下快速参考提供了用于获取群集运行状况的命令
Get-ServiceFabricClusterHealth
将客户端证书部署到群集。
可以使用与上述步骤 5 相同的步骤,将证书从 keyvault 部署到节点。 只需定义并使用不同的参数。
添加或删除客户端证书
除群集证书外,还可添加客户端证书来执行 Service Fabric 群集上的管理操作。
可以添加两种客户端证书 - 管理员或只读。 这些证书稍后可用于在群集上控制对管理员操作和查询操作的访问。 默认情况下,群集证书将添加到允许的管理员证书列表中。
可以指定任意数量的客户端证书。 每次执行添加/删除操作都会更新 Service Fabric 群集的配置。
通过门户添加客户端证书 - 管理员或只读
- 导航到“安全性”部分,并选择“安全性”部分顶部的“+ 身份验证”按钮。
- 在“添加身份验证”部分中,选择“身份验证类型”-“只读客户端”或“管理员客户端”
- 现在选择授权方法。 向 Service Fabric 指出是要使用使用者名称还是指纹来查找此证书。 通常情况下,采用使用者名称的授权方法并不是很好的安全做法。
使用门户删除客户端证书 - 管理员或只读
若要删除辅助证书,以防将其用于群集安全,请导航到“安全性”部分,并从特定证书的上下文菜单中选择“删除”选项。
向虚拟机规模集添加应用程序证书
若要将用于应用程序的证书部署到群集,请参阅此示例 PowerShell 脚本。
后续步骤
有关群集管理的详细信息,请阅读以下文章: