适用于: ✔️ SMB Azure 文件共享
Azure 文件是 Microsoft 推出的易用云文件系统。 本文介绍如何在 Windows 和 Windows Server 上装载 SMB Azure 文件共享。
Azure 文件仅支持 SSD 文件共享上的 SMB 多通道 。
| Windows 版本 | SMB 版本 | Azure 文件存储 SMB 多通道 | 最大 SMB 通道加密 |
|---|---|---|---|
| Windows Server 2025 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 11,版本 24H2 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 11 版本 23H2 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 11 版本 22H2 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 10 版本 22H2 | SMB 3.1.1 | 是 | AES-128-GCM |
| Windows Server 2022 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 11 版本 21H2 | SMB 3.1.1 | 是 | AES-256-GCM |
| Windows 10 版本 21H2 | SMB 3.1.1 | 是 | AES-128-GCM |
| Windows 10,版本 21H1 | SMB 3.1.1 | 是,具有 KB5003690 或更新的版本 | AES-128-GCM |
| Windows Server,版本 20H2 | SMB 3.1.1 | 是,具有 KB5003690 或更新的版本 | AES-128-GCM |
| Windows 10 版本 20H2 | SMB 3.1.1 | 是,具有 KB5003690 或更新的版本 | AES-128-GCM |
| Windows Server 版本 2004 | SMB 3.1.1 | 是,具有 KB5003690 或更新的版本 | AES-128-GCM |
| Windows 10 版本 2004 | SMB 3.1.1 | 是,具有 KB5003690 或更新的版本 | AES-128-GCM |
| Windows Server 2019 | SMB 3.1.1 | 是,具有 KB5003703 或更新的版本 | AES-128-GCM |
| Windows 10 版本 1809 | SMB 3.1.1 | 是,具有 KB5003703 或更新的版本 | AES-128-GCM |
| Windows Server 2016 | SMB 3.1.1 | 是,具有 KB5004238 或更高版本并且应用了注册表项 | AES-128-GCM |
| Windows 10 版本 1607 | SMB 3.1.1 | 是,具有 KB5004238 或更高版本并且应用了注册表项 | AES-128-GCM |
| Windows 10 版本 1507 | SMB 3.1.1 | 是,具有 KB5004249 或更高版本并且应用了注册表项 | AES-128-GCM |
| Windows Server 2012 R21 | SMB 3.0 | 否 | AES-128-CCM |
| Windows Server 20121 | SMB 3.0 | 否 | AES-128-CCM |
| Windows 8.12 | SMB 3.0 | 否 | AES-128-CCM |
| Windows Server 2008 R22 | SMB 2.1 | 否 | 不支持 |
| Windows 72 | SMB 2.1 | 否 | 不支持 |
1Microsoft 对 Windows Server 2012 和 Windows Server 2012 R2 的常规支持已结束。 仅可以通过扩展安全更新 (ESU) 计划购买针对安全更新的额外支持。
2对 Windows 7、Windows 8 和 Windows Server 2008 R2 的 Microsoft 支持已结束。 我们强烈建议从这些操作系统中迁移。
注意
我们建议使用相对于 Windows 版本来说最新的 KB。
确保端口 445 已打开
SMB 协议要求打开 TCP 端口 445。 如果端口 445 被阻止,连接将失败。 可以使用 Test-NetConnection PowerShell cmdlet 检查防火墙或 ISP 是否正在阻止端口 445。 有关详细信息,请参阅端口 445 被阻止。
如果要从 Azure 外部通过 SMB 装载 Azure 文件共享,而无需打开端口 445,可以使用 点到站点 VPN。
要在托管 Azure 文件共享的 Azure 区域(例如本地或其他 Azure 区域)外部通过公共终结点使用该文件共享,OS 必须支持 SMB 3.x。 仅支持 SMB 2.1 的旧版 Windows 无法通过公共终结点装载 Azure 文件共享。
使用基于标识的身份验证
若要提高安全性和访问控制,可以配置 基于标识的身份验证 并将客户端加入域中。 这允许使用 Active Directory 或 Microsoft Entra 标识来访问文件共享,而不是使用存储帐户密钥。
要使用基于标识的身份验证挂载 Azure 文件共享,必须先完成以下操作:
- 分配共享级别权限 并 配置目录和文件级权限。 请记住,共享级角色分配可能需要一些时间才能生效。
- 如果要从以前使用存储帐户密钥连接到文件共享的客户端装载文件共享,请确保首先卸载共享并删除存储帐户密钥的持久性凭据。 在初始化使用 Active Directory 域服务(AD DS)或 Microsoft Entra 凭据的新连接之前,关于如何删除缓存的凭据和现有的 SMB 连接,请参照 常见问题解答 中的两个步骤。
- 如果 AD 源为 AD DS 或 Microsoft Entra Kerberos,则客户端必须具备与 AD DS 的畅通网络连接。 如果计算机或 VM 不在 AD DS 托管的网络之外,则需要启用 VPN 才能访问 AD DS 进行身份验证。
- 使用你向其授予权限的 AD DS 或Microsoft Entra 标识的凭据登录到客户端。
如果遇到问题,请参阅 无法使用 AD 凭据装载 Azure 文件共享。
将 Azure 文件共享与 Windows 结合使用
若要在 Windows 中使用某个 Azure 文件共享,必须装载该文件共享(为其分配驱动器号或装载点路径),或通过其 UNC 路径来访问它。 目前不支持使用共享访问签名 (SAS) 令牌来装载 Azure 文件共享。
注意
若要将预期使用 SMB 文件共享的业务线 (LOB) 应用程序直接迁移到 Azure,通常的模式是使用 Azure 文件共享,而不是在 Azure 虚拟机 (VM) 中运行专用的 Windows 文件服务器。 成功迁移 LOB 应用程序以使用 Azure 文件共享的一个重要注意事项是,许多应用程序在具有有限系统权限的专用服务帐户的上下文中运行,而不是在 VM 的管理帐户下运行。 因此,必须确保装载/保存服务帐户上下文(而不是管理帐户)中 Azure 文件共享的凭据。
装载 Azure 文件共享
可以使用 Azure 门户或 Azure PowerShell 在 Windows 上装载 SMB Azure 文件共享。
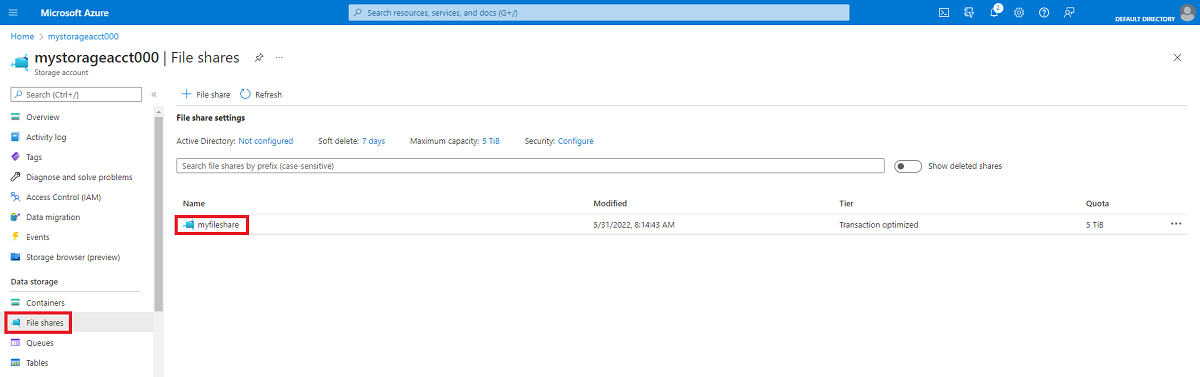
若要使用 Azure 门户装载 Azure 文件共享,请执行以下步骤:
登录到 Azure 门户。
导航到包含要装载的文件共享的存储帐户。
选择“文件共享”。
选择要装载的文件共享。
选择“连接” 。

选择要将共享装载到的驱动器号。
在 “身份验证”方法下,选择 “Active Directory”或“Microsoft Entra”。 如果看到未为存储帐户配置基于标识的身份验证的消息,请根据 基于标识的身份验证概述中所述的方法之一对其进行配置,然后再次尝试装载共享。
选择“ 显示脚本 ”,然后复制提供的脚本。
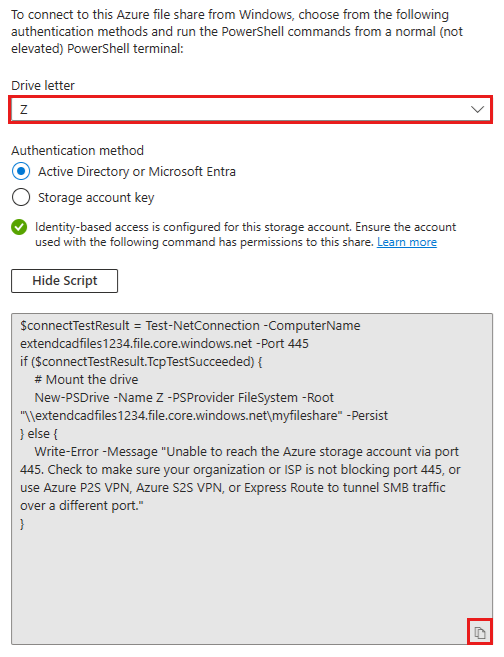
将脚本粘贴到你要将文件共享装载到的主机上的 shell 中,然后运行该脚本。
现已装载 Azure 文件共享。
使用 Windows 命令行装载 Azure 文件共享
还可以使用 net use Windows 提示符中的命令装载文件共享。
从已加入域的 VM 装载文件共享
若要从已加入域的 VM 装载文件共享,请从 Windows 命令提示符运行以下命令。 请记得将<YourStorageAccountName> 和 <FileShareName> 替换为自己的值。
net use Z: \\<YourStorageAccountName>.file.core.chinacloudapi.cn\<FileShareName>
将文件共享装载到未加入域的 VM 或已加入其他 AD 域的 VM
如果 AD 源是本地部署的 AD DS,那么未加入域的 VM 或加入与存储帐户不同 AD 域的 VM 只要具有不受阻碍的网络连接到 AD 域控制器,以及提供显式凭据,也可以访问 Azure 文件共享。 访问文件共享的用户必须在加入存储帐户的 AD 域中具有标识和凭据。
如果您的 AD 源是 Microsoft Entra 域服务,客户端必须确保对 Microsoft Entra 域服务的域控制器的网络连接未受阻,这需要设置站点到站点或点到站点 VPN。 访问文件共享的用户必须在 Microsoft Entra 域服务管理的域中拥有一个标识,该标识是从 Microsoft Entra ID 同步到 Microsoft Entra 域服务的。
若要从未加入域的 VM 挂载文件共享,请使用表示法 username@domainFQDN(其中 domainFQDN 是完全限定的域名),使客户端能够联系域控制器以请求和获取 Kerberos 票证。 可以通过在 Active Directory PowerShell 中运行(Get-ADDomain).Dnsroot 的值。
例如:
net use Z: \\<YourStorageAccountName>.file.core.chinacloudapi.cn\<FileShareName> /user:<username@domainFQDN>
如果 AD 源是 Microsoft Entra 域服务,则还可以提供凭据,例如 DOMAINNAME\username 其中 DOMAINNAME 是 Microsoft Entra 域服务中的域,username 是标识在 Microsoft Entra 域服务中的用户名。
net use Z: \\<YourStorageAccountName>.file.core.chinacloudapi.cn\<FileShareName> /user:<DOMAINNAME\username>
使用存储帐户密钥装载 Azure 文件共享(不建议)
Azure 门户提供了一个 PowerShell 脚本,通过该脚本可以使用存储帐户密钥将文件共享直接装载到主机。 但是,出于安全原因,我们建议使用基于标识的身份验证,而不是存储帐户密钥。 如果必须使用存储帐户密钥,请按照 装载说明进行作,但在 “身份验证”方法下,选择 “存储帐户密钥”。
存储帐户密钥是用于存储帐户的管理员密钥,包括对你要访问的文件共享中所有文件和文件夹的管理员权限,以及对所有文件共享和其他包含在存储帐户中的存储资源(Blob、队列、表等)的权限。 可以通过导航到存储帐户并选择“安全性 + 网络>”,或使用 PowerShell cmdlet,在 Get-AzStorageAccountKey找到存储帐户密钥。
使用文件资源管理器装载 Azure 文件共享
若要打开文件资源管理器,请从“开始”菜单打开,或者按 Win+E 快捷方式。
导航到窗口左侧的“此电脑”。 这样会更改功能区中的可用菜单。 在“计算机”菜单中,选择“映射网络驱动器”。
选择驱动器号并输入 Azure 文件共享的 UNC 路径。 UNC 路径格式为
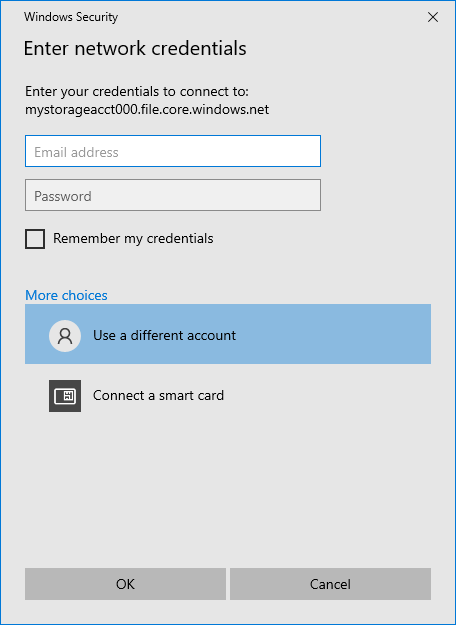
\\<storageAccountName>.file.core.chinacloudapi.cn\<fileShareName>。 例如:\\anexampleaccountname.file.core.chinacloudapi.cn\file-share-name。 选中“使用不同凭据进行连接”复选框。 选择“完成”。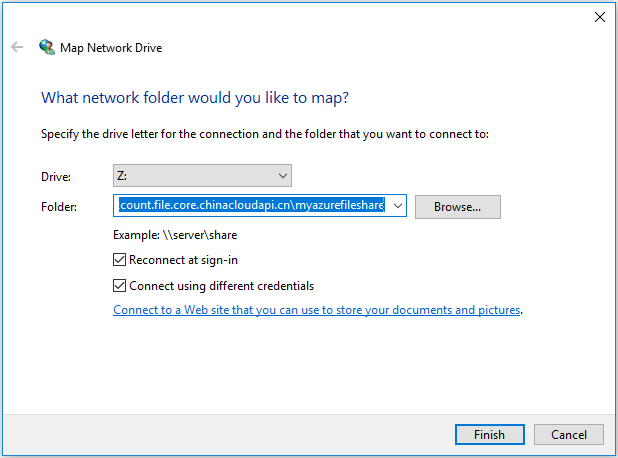
选择“更多选项>使用其他帐户”。 在“电子邮件地址”下,使用存储帐户名称,并使用存储帐户密钥作为密码。 选择“确定”。
根据需要使用 Azure 文件共享。
做好卸载 Azure 文件共享的准备以后,即可在文件资源管理器中右键单击“网络位置”下对应于共享的条目,然后选择“断开连接”。
注意
Azure 文件存储不支持从未加入域的 VM 或通过 Windows 文件资源管理器连接到不同域的 VM 的用户和组的 SID 到 UPN 转换。 如果要通过 Windows 文件资源管理器查看文件/目录所有者或查看/修改 NTFS 权限,则只能从已加入域的 VM 执行此作。
通过其 UNC 路径访问 Azure 文件共享
无需将 Azure 文件共享装载到驱动器号即可使用它。 通过在文件资源管理器中输入以下内容,可以使用 UNC 路径直接访问 Azure 文件共享。 请务必将 storageaccountname 替换为存储帐户名称,并将 myfileshare 替换为文件共享名称:
\\storageaccountname.file.core.chinacloudapi.cn\myfileshare
系统会要求你使用网络凭据登录。 使用在其中创建了存储帐户和文件共享的 Azure 订阅登录。 如果未提示输入凭据,可以使用以下命令添加凭据:
cmdkey /add:StorageAccountName.file.core.chinacloudapi.cn /user:localhost\StorageAccountName /pass:StorageAccountKey
使用自定义域名挂载文件共享
如果不想使用后缀 file.core.chinacloudapi.cn装载 Azure 文件共享,可以修改与 Azure 文件共享关联的存储帐户名称的后缀,然后添加规范名称 (CNAME) 记录以将新后缀路由到存储帐户的终结点。 以下说明仅适用于单林环境。 若要了解如何配置具有两个或多个林的环境,请参阅 将 Azure 文件与多个 Active Directory 林配合使用。
注意
Azure 文件仅支持使用存储帐户名称作为域前缀配置 CNAMES。 如果不想将存储帐户名称用作前缀,请考虑使用 DFS 命名空间。
在此示例中,我们有 Active Directory 域 onpremad1.com,并且有一个名为 mystorageaccount 的存储帐户,其中包含 SMB Azure 文件共享。 首先,我们需要修改存储帐户的 SPN 后缀,以将 mystorageaccount.onpremad1.com 映射到 mystorageaccount.file.core.chinacloudapi.cn。
可以挂载 net use \\mystorageaccount.onpremad1.com 文件共享,因为 onpremad1 中的客户端会自动搜索 onpremad1.com 来查找该存储帐户的适当资源。
若要使用此方法,请完成以下步骤:
请确保设置基于标识的身份验证。 如果 AD 源为 AD DS 或 Microsoft Entra Kerberos,请确保将 AD 用户帐户同步到 Microsoft Entra ID。
使用
setspn该工具修改存储帐户的 SPN。 可以通过运行以下 Active Directory PowerShell 命令找到<DomainDnsRoot>:(Get-AdDomain).DnsRootsetspn -s cifs/<storage-account-name>.<DomainDnsRoot> <storage-account-name>使用 Active Directory DNS 管理器添加 CNAME 条目。 如果使用专用终结点,请添加 CNAME 条目以映射到专用终结点名称。
- 打开 Active Directory DNS 管理器。
- 转到您的域(例如 onpremad1.com)。
- 转到“正向查找区域”。
- 选择与你的域同名的节点(例如 onpremad1.com)并右键单击“新建别名(CNAME)”。
- 对于别名,请输入存储帐户名称。
- 对于完全限定的域名(FQDN),请输入
<storage-account-name>.<domain-name>,例如 mystorageaccount.onpremad1.com。 FQDN 的主机名部分必须与存储帐户名称匹配。 如果主机名与存储帐户名称不匹配,装载将失败,并出现访问被拒绝错误。 - 对于目标主机 FQDN,请输入
<storage-account-name>.file.core.chinacloudapi.cn - 选择“确定”。
现在应该能够使用 storageaccount.domainname.com 装载文件共享。
后续步骤
请参阅以下链接,获取有关 Azure 文件的更多信息: