Azure NAT 网关资源
本文介绍 NAT 网关资源的关键组件,这些组件使其能够提供高度安全、可缩放和可复原的出站连接。 可以在订阅中通过 Azure 门户、Azure CLI、Azure PowerShell、资源管理器模板或适当的替代项配置其中某些组件。
NAT 网关体系结构
NAT 网关使用软件定义的网络作为分布式和完全管理的服务运行。 由于 NAT 网关有多个容错域,因此它能够承受多次故障,而不会对服务造成任何影响。
NAT 网关为 Azure 虚拟网络子网中的专用实例提供源网络地址转换 (SNAT)。 在子网上配置后,子网中的专用 IP 会 SNAT 为 NAT 网关的静态公共 IP 地址,以出站方式连接到 Internet。 NAT 网关还仅为出站始发连接的响应数据包提供目标网络地址转换 (DNAT)。
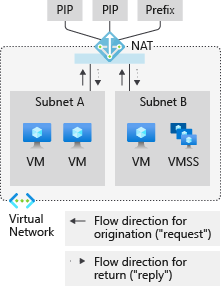
图:用于出站到 Internet 的 NAT 网关
当 NAT 网关附加到虚拟网络中的子网时,NAT 网关会针对定向到 Internet 的所有出站流量采用子网的默认下一跃点类型。 无需额外的路由配置。 NAT 网关不提供来自 Internet 的未经请求的入站连接。 DNAT 仅针对作为对出站数据包的响应而到达的数据包执行。
子网
NAT 网关可以附加到虚拟网络中的多个子网,以提供与 Internet 的出站连接。 当 NAT 网关附加到一个子网时,它采用默认的 Internet 路由。 然后,NAT 网关将是发往 Internet 的所有出站流量的下一跃点类型。
以下子网配置不能与 NAT 网关一起使用:
子网不能附加到多个 NAT 网关。 NAT 网关将成为子网的默认 Internet 路由,只有一个 NAT 网关可以充当默认路由。
NAT 网关不能从不同的虚拟网络附加到子网。
NAT 网关不能与网关子网一起使用。 网关子网是 VPN 网关在 Azure 虚拟网络和本地位置之间发送加密流量的指定子网。 有关网关子网的详细信息,请参阅网关子网。
静态公共 IP 地址
NAT 网关可以与静态公共 IP 地址或公共 IP 前缀相关联,以提供出站连接。 NAT 网关支持 IPv4 地址。 NAT 网关可以使用公共 IP 地址或前缀的任何组合,总共可以使用 16 个 IP 地址。 如果分配公共 IP 前缀,则会使用整个公共 IP 前缀。 可以直接使用公共 IP 前缀,或者在多个 NAT 网关资源之间分配前缀的公共 IP 地址。 NAT 网关会将所有流量梳理到前缀的 IP 地址范围。
NAT 网关不能与 IPv6 公共 IP 地址或前缀一起使用。
NAT 网关不能与基本 SKU 公共 IP 地址一起使用。
SNAT 端口
SNAT 端口清单由附加到 NAT 网关的公共 IP 地址和/或公共 IP 前缀提供。 SNAT 端口清单按需提供给附加到 NAT 网关的子网中的所有实例。 无需为每个实例预分配 SNAT 端口。
有关 SNAT 端口和 Azure NAT 网关的详细信息,请参阅使用 Azure NAT 网关进行源网络地址转换 (SNAT)。
在将虚拟网络中的多个子网附加到同一 NAT 网关资源时,NAT 网关提供的 SNAT 端口清单将会跨所有子网共享。
SNAT 端口充当唯一标识符,用于区分不同的连接流。 可以使用同一 SNAT 端口同时连接到不同的目标终结点。
不同的 SNAT 端口用于建立与同一目标终结点的连接,以便区分不同的连接流。 重复使用以连接到同一目标的 SNAT 端口将放在 重用冷却计时器上,然后才能重复使用。
单个 NAT 网关最多可扩展为 16 个 IP 地址。 每个 NAT 网关公共 IP 地址提供 64,512 个 SNAT 端口以建立出站连接。 NAT 网关可以纵向扩展到超过 100 万个 SNAT 端口。 TCP 和 UDP 是独立的 SNAT 端口清单,与 NAT 网关无关。
可用性区域
NAT 网关可以在特定的可用性区域中创建,也可以放置在禁止区域中。 当 NAT 网关放置在禁止区域中时,Azure 会为 NAT 网关选择要驻留的区域。
区域冗余公共 IP 地址可用于区域或非区域 NAT 网关资源。
建议将 NAT 网关配置为各个可用性区域。 此外,它应附加到具有来自同一区域的私有实例的子网。 有关可用性区域和 Azure NAT 网关的详细信息,请参阅可用性区域设计注意事项。

部署 NAT 网关后,无法更改区域选择。
协议
NAT 网关与 UDP 和 TCP 流的 IP 和 IP 传输标头进行交互。 NAT 网关对应用层有效负载不可知。 不支持其他 IP 协议。
TCP 重置
当 NAT 网关检测到不存在的连接流上的流量时,将发送 TCP 重置数据包。 TCP 重置数据包向接收终结点指示连接流发布已发生,并且此同一 TCP 连接上未来的任何通信都将失败。 TCP 重置对于 NAT 网关是单向的。
如果出现以下情况,则连接流可能不存在:
在连接流上处于非活动状态一段时间后,达到空闲超时,并以无提示方式中断了连接。
来自 Azure 网络端或公共 Internet 端的发送方在连接中断后发送了流量。
TCP 重置数据包仅在检测到中断的连接流上的流量时发送。 此操作意味着在连接流中断后,TCP 重置数据包可能不会立即发送。
无论流量来自 Azure 网络端还是公共 Internet 端,系统都会发送 TCP 重置数据包,以响应检测不存在的连接流上的流量。
TCP 空闲超时
NAT 网关为 TCP 协议提供 4 分钟到 120 分钟的可配置空闲超时范围。 UDP 协议的不可配置的空闲超时为 4 分钟。
当连接空闲时,NAT 网关会一直占用 SNAT 端口,直到连接空闲超时。当由于长时间空闲超时计时器可能会不必要地增加 SNAT 端口耗尽的可能性,因此建议不要将 TCP 空闲超时持续时间增加到超过默认的 4 分钟。 空闲计时器不会影响从不处于空闲状态的流。
TCP keepalive 可用于提供刷新长时间空闲连接和终结点活动状态检测的模式。 有关详细信息,请参阅 .NET 示例。 TCP Keepalive 以重复 ACK 的形式显示给终结点,其开销较低,对应用层不可见。
UDP 空闲超时计时器不可配置,应使用 UDP keepalive 来确保未达到空闲超时值,从而保持连接。 与 TCP 连接不同,在连接的一端启用 UDP keepalive 功能仅适用于一个方向的流量流。 必须在流量流的两端均启用 UDP keepalive,从而保持流量流活动状态。
计时器
端口重用计时器
端口重用计时器确定在连接关闭后,NAT 网关可以在源端口保持占用状态多长时间之后重用该端口来连接到同一目标终结点。
下表提供了有关 TCP 端口何时可供 NAT 网关重复用来连接到同一目标终结点的信息。
| 计时器 | 描述 | 值 |
|---|---|---|
| TCP FIN | TCP FIN 数据包关闭连接后,将激活一个占用 SNAT 端口的 65 秒计时器。 该计时器结束后,该 SNAT 端口可供重用。 | 65 秒 |
| TCP RST | TCP RST 数据包(重置)关闭连接后,将激活一个占用 SNAT 端口的 16 秒计时器。 该计时器结束时,该端口可供重用。 | 16 秒 |
| TCP 半开 | 在建立连接期间,当一个连接终结点正在等待另一终结点的确认时,将激活 30 秒计时器。 如果未检测到任何流量,则连接将会关闭。 连接关闭后,可以重用源端口连接到同一目标终结点。 | 30 秒 |
对于 UDP 流量,连接关闭后,端口将保持占用状态 65 秒,然后可供重用。
空闲超时计时器
| 计时器 | 描述 | 值 |
|---|---|---|
| TCP 空闲超时 | 如果在任一终结点之间长时间未传输任何数据,则 TCP 连接可能处于空闲状态。 计时器可配置为 4分钟(默认)到 120 分钟(2 小时),使进入空闲状态的连接超时。 流中的流量会重置空闲超时计时器。 | 可配置;4分钟(默认)- 120 分钟 |
| UDP 空闲超时 | 如果在任一终结点之间长时间未传输任何数据,则 UDP 连接可能处于空闲状态。 UDP 空闲超时计时器为 4 分钟,且不可配置。 流中的流量会重置空闲超时计时器。 | 不可配置;4 分钟 |
注意
这些计时器设置随时可能更改。 提供这些值是为了帮助进行故障排除,暂时请不要依赖于特定的计时器。
带宽
每个 NAT 网关最多可提供 50 Gbps 的吞吐量。 此数据吞吐量包括通过 NAT 网关资源处理的出站和入站数据(响应)。 可以将部署拆分成多个子网,为每个子网或子网组分配一个 NAT 网关,以便进行横向扩展。
性能
对于 TCP 和 UDP,NAT 网关最多可以支持每个公共 IP 地址通过 Internet 到同一目的地终结点的 50,000 个并发连接。 NAT 网关每秒可处理 1M 数据包,并可纵向扩展到每秒 5M 数据包。
NAT 网关随时可以支持的连接总数最多为 200 万。 虽然 NAT 网关可能超过 200 万个连接,但连接失败的风险会增加。
限制
基本负载均衡器和基本公共 IP 地址与 NAT 网关不兼容。 请改用标准 SKU 负载均衡器和公共 IP。
若要将负载均衡器从基本升级到标准,请参阅升级 Azure 公共负载均衡器
若要将公共 IP 地址从基本升级到标准,请参阅升级公共 IP 地址
NAT 网关不支持 ICMP
IP 分段不适用于 NAT 网关。
后续步骤
查看 Azure NAT 网关。
了解 NAT 网关的指标和警报。
了解如何对 NAT 网关进行故障排除。