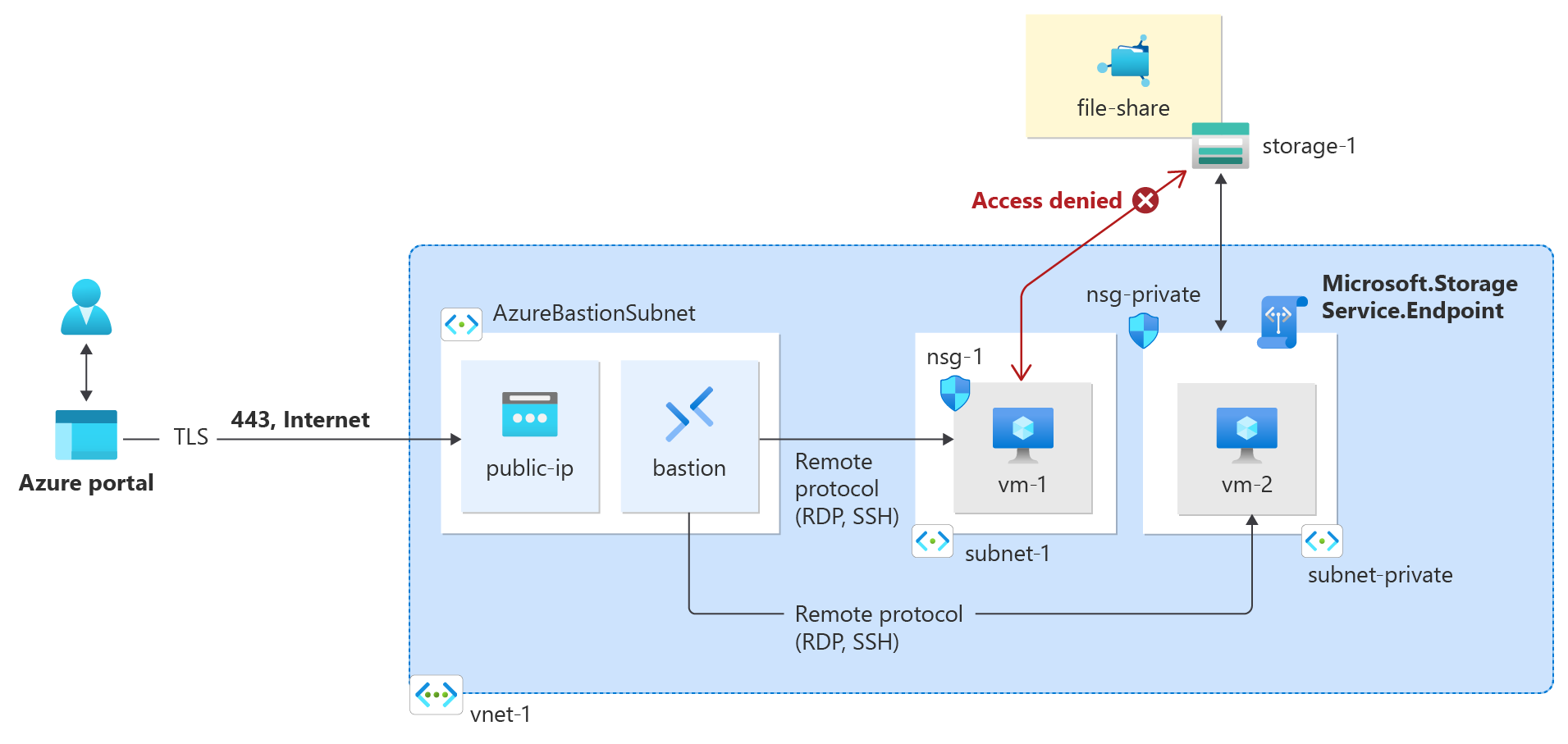
通过虚拟网络服务终结点,可以将某些 Azure 服务资源的网络访问限制在一个虚拟网络的特定子网内。 还可以删除对资源的 Internet 访问。 服务终结点提供从虚拟网络到受支持 Azure 服务的直接连接,使你能够使用虚拟网络的专用地址空间访问 Azure 服务。 通过服务终结点发往 Azure 资源的流量始终保留在 Azure 主干网络上。
本教程介绍如何执行下列操作:
- 创建包含一个子网的虚拟网络
- 添加子网并启用服务终结点
- 创建 Azure 资源并且仅允许从一个子网对其进行网络访问
- 将虚拟机 (VM) 部署到每个子网
- 确认从某个子网对资源的访问
- 确认已拒绝从某个子网和互联网访问某个资源
先决条件
如果没有 Azure 订阅,可在开始前创建一个试用帐户。
如果选择在本地安装和使用 PowerShell,则本文需要 Azure PowerShell 模块 1.0.0 或更高版本。 运行 Get-Module -ListAvailable Az 查找已安装的版本。 如果需要进行升级,请参阅 Install Azure PowerShell module(安装 Azure PowerShell 模块)。 如果在本地运行 PowerShell,则还需运行 Connect-AzAccount -Environment AzureChinaCloud 以创建与 Azure 的连接。
如果没有 Azure 试用版订阅,请在开始前创建一个试用版订阅。
可以使用本地 Azure CLI。
- 本文需要 Azure CLI 2.0.28 或更高版本。
启用服务终结点
创建虚拟网络和 Azure Bastion 主机
以下过程创建包含资源子网、Azure Bastion 子网和 Bastion 主机的虚拟网络:
在门户中,搜索并选择“虚拟网络”。
在“虚拟网络”页面上,选择“+ 创建”。
在创建虚拟网络的基本信息选项卡上输入或选择以下信息:
| 设置 |
值 |
|
项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择“新建”。
输入“test-rg”作为名称。
选择“确定”。 |
|
实例详细信息 |
|
| 名称 |
输入“vnet-1”。 |
| 区域 |
选择“(亚太)中国东部 2”。 |
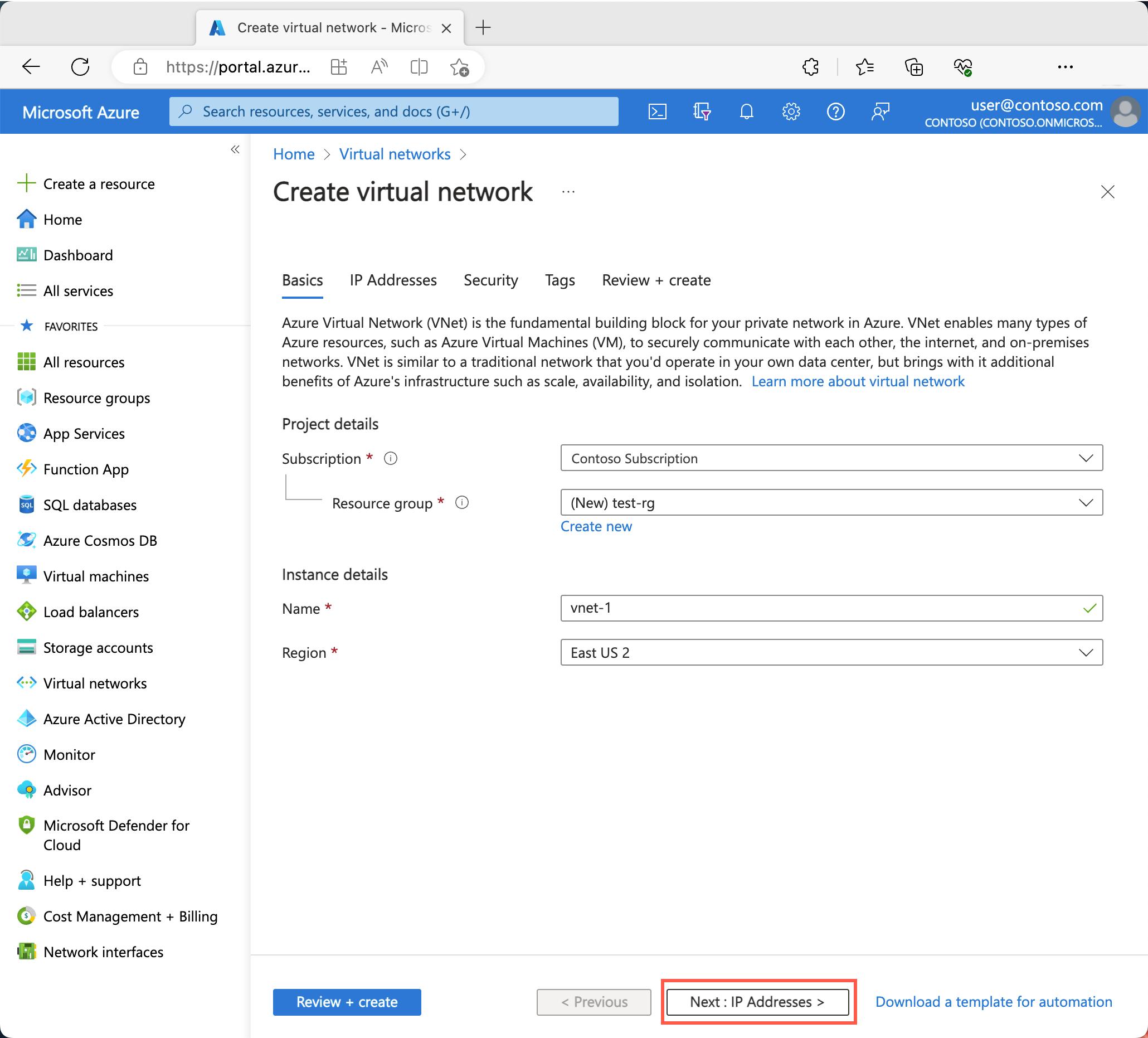
选择“下一步”,转到“安全性”选项卡。
在“Azure Bastion”部分,选择“启用 Bastion”。
Bastion 使用浏览器通过安全外壳 (SSH) 或远程桌面协议 (RDP),通过使用其专用 IP 地址连接虚拟网络中的虚拟机。 虚拟机不需要公共 IP 地址、客户端软件或特殊配置。 有关详细信息,请参阅什么是 Azure Bastion?。
注意事项
每小时定价从部署 Bastion 的时刻开始计算,无论出站数据的使用情况如何。 有关详细信息,请参阅定价和 SKU。 如果要将 Bastion 部署为教程或测试的一部分,建议在使用完此资源后将其删除。
在“Azure Bastion”中,输入或选择以下信息:
| 设置 |
值 |
| Azure Bastion 主机名 |
输入堡垒。 |
| Azure Bastion 公共 IP 地址 |
选择“创建公共 IP 地址”。
在名称中输入 public-ip-bastion。
选择“确定”。 |
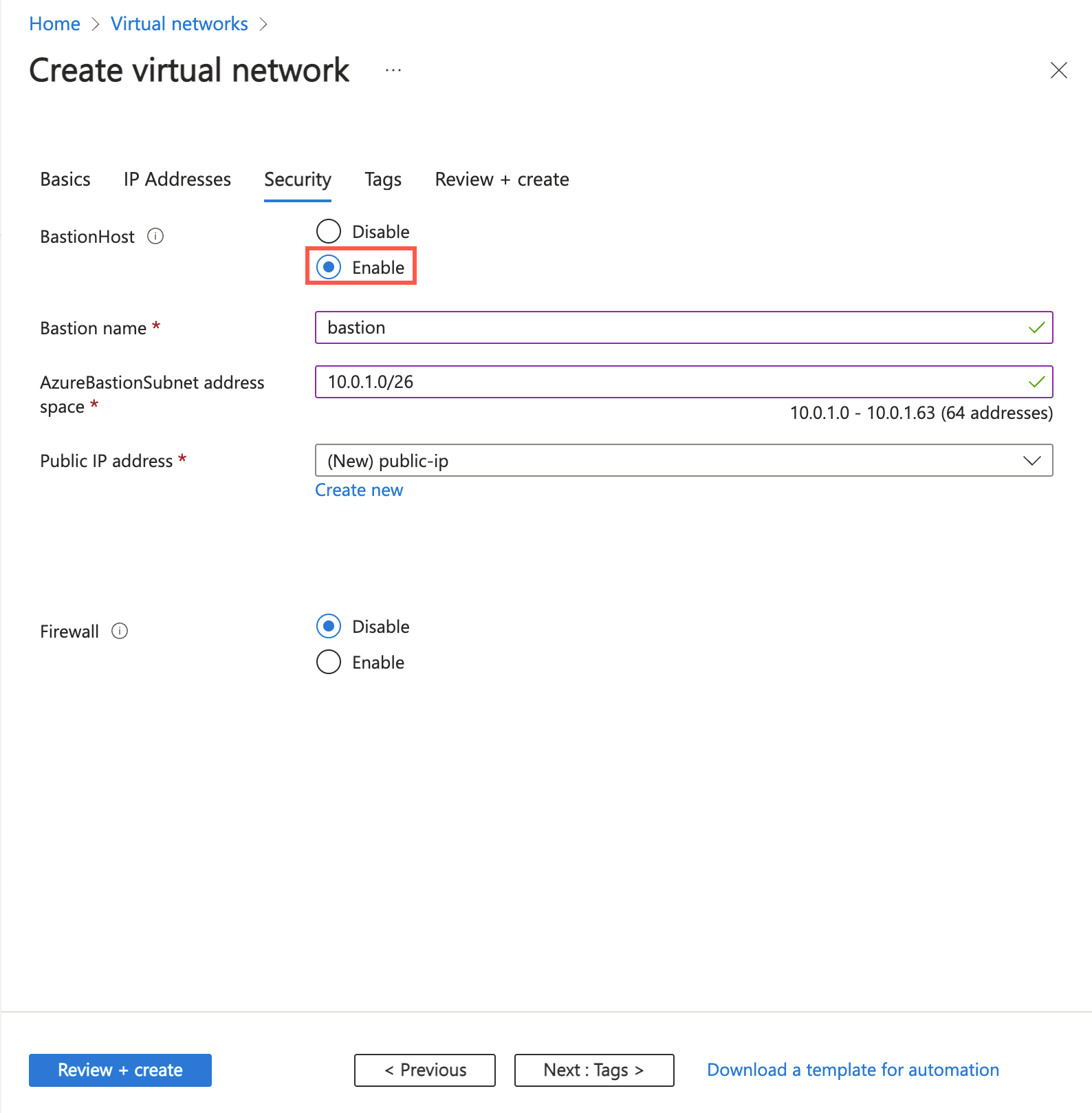
选择下一步,转到IP 地址选项卡。
在“子网”的地址空间框中,选择“默认”子网。
在编辑子网中,输入或选择以下信息:
| 设置 |
值 |
|
子网详细信息 |
|
| 子网模板 |
保留默认值“默认”。 |
| 名称 |
输入“subnet-1”。 |
| 起始地址 |
保留默认值“10.0.0.0”。 |
| 子网大小 |
保留默认值“/24 (256 个地址)”。 |
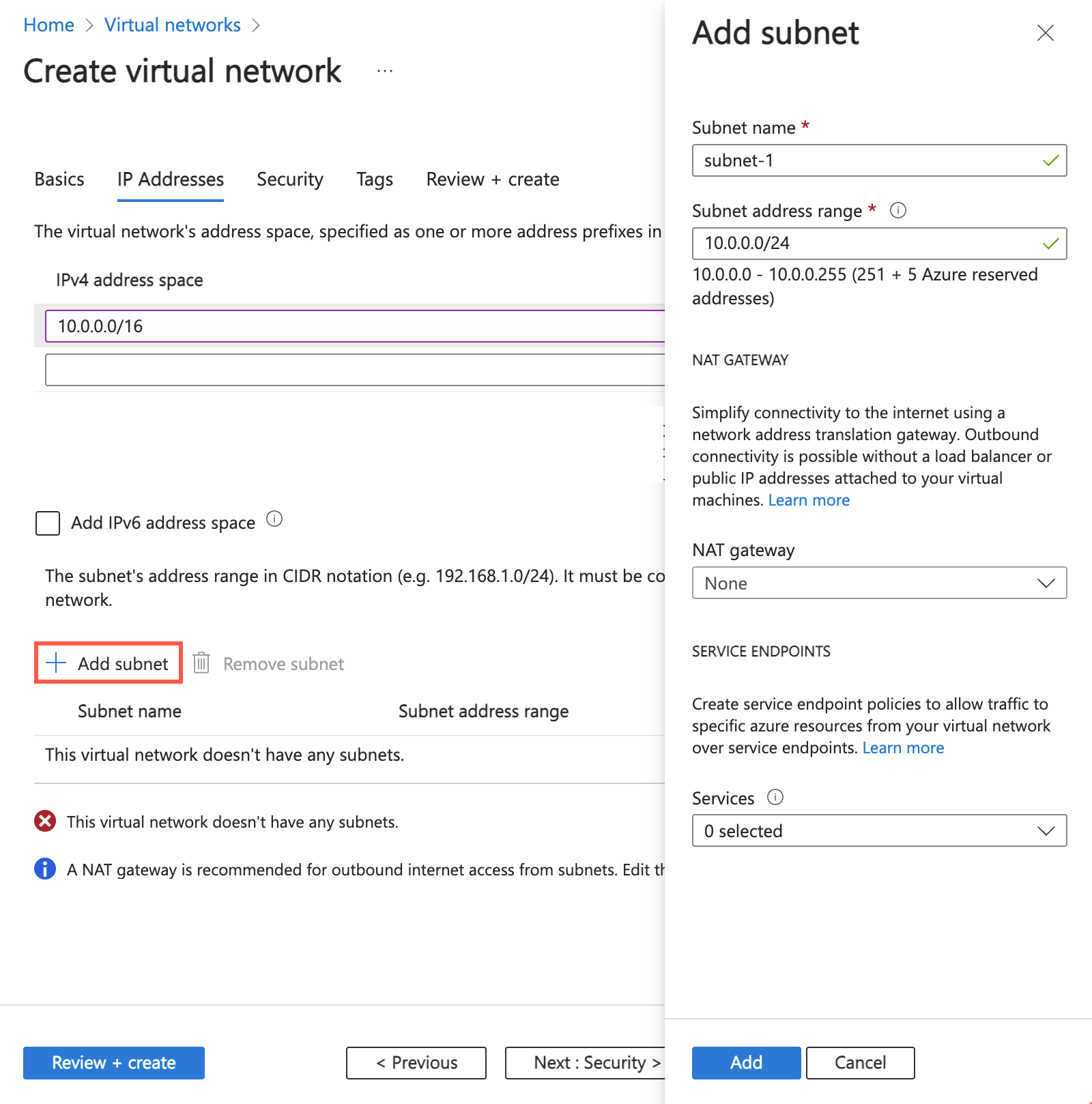
选择“保存”。
在窗口底部选择“查看 + 创建”。 验证通过后,选择“创建”。
每个服务、每个子网均启用服务终结点。
在门户页面顶部的搜索框中,搜索“虚拟网络”。 在搜索结果中,选择“虚拟网络”。
在“虚拟网络”中,选择“vnet-1”。
在vnet-1的“设置”部分,选择“子网”。
选择“+ 子网”。
在“添加子网”页面上,输入或选择以下信息:
| 设置 |
值 |
| 名称 |
子网专用 |
| 子网地址范围 |
保留默认值10.0.2.0/24。 |
|
服务终结点 |
|
| 服务 |
选择“Microsoft.Storage” |
选择“保存”。
注意
在为其中有资源的现有子网启用服务终结点之前,请参阅更改子网设置。
创建虚拟网络
创建虚拟网络之前,必须为虚拟网络创建资源组以及本文中创建的所有其他资源。 使用 New-AzResourceGroup 创建资源组。 以下示例创建名为 test-rg 的资源组:
$rg = @{
ResourceGroupName = "test-rg"
Location = "chinanorth3"
}
New-AzResourceGroup @rg
使用 New-AzVirtualNetwork 创建虚拟网络。 以下示例使用地址前缀“10.0.0.0/16”创建一个名为“vnet-1”的虚拟网络。
$vnet = @{
ResourceGroupName = "test-rg"
Location = "chinanorth3"
Name = "vnet-1"
AddressPrefix = "10.0.0.0/16"
}
$virtualNetwork = New-AzVirtualNetwork @vnet
使用 New-AzVirtualNetworkSubnetConfig 创建子网配置。 以下示例为名为 subnet-public 的子网创建子网配置:
$subpub = @{
Name = "subnet-public"
AddressPrefix = "10.0.0.0/24"
VirtualNetwork = $virtualNetwork
}
$subnetConfigPublic = Add-AzVirtualNetworkSubnetConfig @subpub
通过使用 Set-AzVirtualNetwork 将子网配置写入虚拟网络,在虚拟网络中创建子网:
$virtualNetwork | Set-AzVirtualNetwork
在虚拟网络中创建另一个子网。 在此示例中,将创建一个名为 subnet-private 的子网,该子网具有用于 Microsoft.Storage 的服务终结点。
$subpriv = @{
Name = "subnet-private"
AddressPrefix = "10.0.2.0/24"
VirtualNetwork = $virtualNetwork
ServiceEndpoint = "Microsoft.Storage"
}
$subnetConfigPrivate = Add-AzVirtualNetworkSubnetConfig @subpriv
$virtualNetwork | Set-AzVirtualNetwork
部署 Azure Bastion
Azure Bastion 使用浏览器通过安全外壳 (SSH) 或远程桌面协议 (RDP) 连接到虚拟网络中的 VM(通过使用其专用 IP 地址)。 虚拟机不需要公共 IP 地址、客户端软件或特殊配置。 有关 Bastion 的详细信息,请参阅 什么是 Azure Bastion?
每小时定价从部署 Bastion 的时刻开始计算,无论出站数据的使用情况如何。 有关详细信息,请参阅定价和 SKU。 如果要将 Bastion 部署为教程或测试的一部分,建议在使用完此资源后将其删除。
为虚拟网络配置 Bastion 子网。 此子网专为 Bastion 资源保留,且必须命名为 AzureBastionSubnet。
$subnet = @{
Name = 'AzureBastionSubnet'
VirtualNetwork = $virtualNetwork
AddressPrefix = '10.0.1.0/26'
}
$subnetConfig = Add-AzVirtualNetworkSubnetConfig @subnet
设置配置:
$virtualNetwork | Set-AzVirtualNetwork
为 Bastion 创建一个公共 IP 地址。 Bastion 主机使用公共 IP 通过端口 443 访问 SSH 和 RDP。
$ip = @{
ResourceGroupName = 'test-rg'
Name = 'public-ip'
Location = 'chinanorth3'
AllocationMethod = 'Static'
Sku = 'Standard'
Zone = 1,2,3
}
New-AzPublicIpAddress @ip
使用 New-AzBastion 命令在 AzureBastionSubnet 中创建新的标准 Bastion 主机:
$bastion = @{
Name = 'bastion'
ResourceGroupName = 'test-rg'
PublicIpAddressRgName = 'test-rg'
PublicIpAddressName = 'public-ip'
VirtualNetworkRgName = 'test-rg'
VirtualNetworkName = 'vnet-1'
Sku = 'Basic'
}
New-AzBastion @bastion -AsJob
部署 Bastion 资源大约需要 10 分钟。 当 Bastion 部署到虚拟网络时,可以在下一部分创建 VM。
创建虚拟网络
创建虚拟网络之前,必须为虚拟网络创建资源组以及本文中创建的所有其他资源。 使用 az group create 创建资源组。 以下示例在“chinanorth3”位置创建名为“test-rg”的资源组:
az group create \
--name test-rg \
--location chinanorth3
使用 az network vnet create 创建包含一个子网的虚拟网络。
az network vnet create \
--name vnet-1 \
--resource-group test-rg \
--address-prefix 10.0.0.0/16 \
--subnet-name subnet-public \
--subnet-prefix 10.0.0.0/24
只能为支持服务终结点的服务启用服务终结点。 使用 az network vnet list-endpoint-services 查看某个 Azure 位置中启用服务终结点的可用服务。 以下示例返回 chinanorth3 区域中可用的启用了服务终端节点的服务列表。 随着更多的 Azure 服务启用服务终结点,返回的服务列表将随时间增大。
az network vnet list-endpoint-services \
--location chinanorth3 \
--out table
使用 az network vnet subnet create 在虚拟网络中创建另一个子网。 此示例中,将为子网创建 Microsoft.Storage 的服务终结点。
az network vnet subnet create \
--vnet-name vnet-1 \
--resource-group test-rg \
--name subnet-private \
--address-prefix 10.0.1.0/24 \
--service-endpoints Microsoft.Storage
限制子网的网络访问
默认情况下,子网中的所有虚拟机实例均可与任何资源通信。 可以通过创建网络安全组并将其关联到子网来限制与子网中所有资源的通信。
在门户页面顶部的搜索框中,搜索“网络安全组”。 在搜索结果中选择“网络安全组”。
在“网络安全组”中,选择“+ 创建”。
在“创建网络安全组”的“基本信息”选项卡中,输入或选择以下信息 :
| 设置 |
值 |
|
项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择“test-rg”。 |
|
实例详细信息 |
|
| 名称 |
输入nsg-storage。 |
| 区域 |
选择“中国北部 3”。 |
选择查看 + 创建,然后选择创建。
使用 New-AzNetworkSecurityGroup 创建网络安全组。 以下示例创建一个名为 nsg-private 的网络安全组。
$nsgpriv = @{
ResourceGroupName = 'test-rg'
Location = 'chinanorth3'
Name = 'nsg-private'
}
$nsg = New-AzNetworkSecurityGroup @nsgpriv
使用 az network nsg create 创建网络安全组。 以下示例创建一个名为 nsg-private 的网络安全组。
az network nsg create \
--resource-group test-rg \
--name nsg-private
创建出站网络安全组 (NSG) 规则
在门户页面顶部的搜索框中,搜索“网络安全组”。 在搜索结果中选择“网络安全组”。
选择“nsg-storage”。
在“设置”中,选择“出站安全规则” 。
选择“+ 添加”。
创建一条允许出站通信到 Azure 存储服务的规则。 在“添加出站安全规则”中,输入或选择以下信息:
| 设置 |
值 |
| 源 |
选择“服务标记”。 |
| 源服务标记 |
选择“VirtualNetwork”。 |
| 源端口范围 |
保留默认值 *。 |
| 目标 |
选择 “Service Tag”。 |
| 目标服务标记 |
选择“存储”。 |
| 服务 |
保留默认值“自定义”。 |
| 目标端口范围 |
输入445。 |
| 协议 |
选择“任何”。 |
| 动作 |
选择“允许”。 |
| 优先级 |
保留默认值“100”。 |
| 名称 |
输入allow-storage-all。 |
选择“+ 添加”。
创建另一条出站安全规则,拒绝到 Internet 的通信。 此规则将覆盖所有网络安全组中允许出站 Internet 通信的默认规则。 使用添加出站安全规则中的以下值完成上述步骤:
| 设置 |
值 |
| 源 |
选择“服务标记”。 |
| 源服务标记 |
选择“VirtualNetwork”。 |
| 源端口范围 |
保留默认值 *。 |
| 目标 |
选择“服务标签”。 |
| 目标服务标记 |
选择“Internet”。 |
| 服务 |
保留默认值“自定义”。 |
| 目标端口范围 |
输入 *。 |
| 协议 |
选择“任何”。 |
| 动作 |
选择“拒绝”。 |
| 优先级 |
保留默认值110。 |
| 名称 |
输入deny-internet-all。 |
选择 添加 。
在门户页面顶部的搜索框中,搜索“网络安全组”。 在搜索结果中选择“网络安全组”。
选择“nsg-storage”。
在“设置”中选择“子网”。
选择“+ 关联”。
在“关联子网”中,选择“虚拟网络”中的“vnet-1”。 在“子网”中选择“子网专用“。
选择“确定”。
使用 New-AzNetworkSecurityRuleConfig 创建网络安全组安全规则。 以下规则允许对分配给 Azure 存储服务的公共 IP 地址进行出站访问:
$r1 = @{
Name = "Allow-Storage-All"
Access = "Allow"
DestinationAddressPrefix = "Storage"
DestinationPortRange = "*"
Direction = "Outbound"
Priority = 100
Protocol = "*"
SourceAddressPrefix = "VirtualNetwork"
SourcePortRange = "*"
}
$rule1 = New-AzNetworkSecurityRuleConfig @r1
以下规则拒绝对所有公共 IP 地址的访问。 上一个规则将替代此规则,因为它的优先级更高,上一个规则允许对 Azure 存储的公共 IP 地址进行访问。
$r2 = @{
Name = "Deny-Internet-All"
Access = "Deny"
DestinationAddressPrefix = "Internet"
DestinationPortRange = "*"
Direction = "Outbound"
Priority = 110
Protocol = "*"
SourceAddressPrefix = "VirtualNetwork"
SourcePortRange = "*"
}
$rule2 = New-AzNetworkSecurityRuleConfig @r2
使用 Get-AzNetworkSecurityGroup 将网络安全组对象检索到变量中。 使用 Set-AzNetworkSecurityRuleConfig 将规则添加到网络安全组。
# Retrieve the existing network security group
$nsgpriv = @{
ResourceGroupName = 'test-rg'
Name = 'nsg-private'
}
$nsg = Get-AzNetworkSecurityGroup @nsgpriv
# Add the new rules to the security group
$nsg.SecurityRules += $rule1
$nsg.SecurityRules += $rule2
# Update the network security group with the new rules
Set-AzNetworkSecurityGroup -NetworkSecurityGroup $nsg
使用 Set-AzVirtualNetworkSubnetConfig 将该网络安全组添加到 subnet-private 子网,然后将子网配置写入到虚拟网络。 以下示例将 nsg-private 网络安全组关联到 subnet-private 子网:
$subnet = @{
VirtualNetwork = $VirtualNetwork
Name = "subnet-private"
AddressPrefix = "10.0.2.0/24"
ServiceEndpoint = "Microsoft.Storage"
NetworkSecurityGroup = $nsg
}
Set-AzVirtualNetworkSubnetConfig @subnet
$virtualNetwork | Set-AzVirtualNetwork
使用 az network nsg rule create 创建安全规则。 以下规则允许对分配给 Azure 存储服务的公共 IP 地址进行出站访问:
az network nsg rule create \
--resource-group test-rg \
--nsg-name nsg-private \
--name Allow-Storage-All \
--access Allow \
--protocol "*" \
--direction Outbound \
--priority 100 \
--source-address-prefix "VirtualNetwork" \
--source-port-range "*" \
--destination-address-prefix "Storage" \
--destination-port-range "*"
每个网络安全组包含多个默认安全规则。 以下规则将替代允许对所有公共 IP 地址进行出站访问的默认安全规则。
destination-address-prefix "Internet" 选项拒绝对所有公共 IP 地址进行出站访问。 上一个规则将替代此规则,因为它的优先级更高,上一个规则允许对 Azure 存储的公共 IP 地址进行访问。
az network nsg rule create \
--resource-group test-rg \
--nsg-name nsg-private \
--name Deny-Internet-All \
--access Deny \
--protocol "*" \
--direction Outbound \
--priority 110 \
--source-address-prefix "VirtualNetwork" \
--source-port-range "*" \
--destination-address-prefix "Internet" \
--destination-port-range "*"
以下规则允许 SSH 流量从任何位置进入子网。 该规则将替代拒绝来自 Internet 的所有入站流量的默认安全规则。 允许通过 SSH 访问子网,以便在稍后的步骤中测试连接。
az network nsg rule create \
--resource-group test-rg \
--nsg-name nsg-private \
--name Allow-SSH-All \
--access Allow \
--protocol Tcp \
--direction Inbound \
--priority 120 \
--source-address-prefix "*" \
--source-port-range "*" \
--destination-address-prefix "VirtualNetwork" \
--destination-port-range "22"
使用 az network vnet subnet update 将该网络安全组关联到 subnet-private 子网。 以下示例将网络安全组nsg-private关联到子网subnet-private:
az network vnet subnet update \
--vnet-name vnet-1 \
--name subnet-private \
--resource-group test-rg \
--network-security-group nsg-private
限制对资源的网络访问
对于通过为服务终结点启用的 Azure 服务创建的资源,限制对其的网络访问时所需的步骤因服务而异。 请参阅各个服务的文档来了解适用于每个服务的具体步骤。 本教程的余下内容以示例的形式介绍了限制 Azure 存储帐户进行网络访问的步骤。
创建存储帐户
为本文中的步骤创建 Azure 存储帐户。 如果已有存储帐户,可以改为使用它。
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
选择“+ 新建”。
在“创建存储帐户”的“基本信息”选项卡中,输入或选择以下信息:
| 设置 |
值 |
|
项目详细信息 |
|
| 订阅 |
选择 Azure 订阅。 |
| 资源组 |
选择“test-rg”。 |
|
实例详细信息 |
|
| 存储帐户名称 |
输入 storage1。 如果该名称不可用,请输入一个唯一的名称。 |
| 位置 |
选择“(亚太)中国北部 3”。 |
| 性能 |
保留默认值“标准”。 |
| 冗余 |
选择“本地冗余存储(LRS)”。 |
选择“查看”。
选择创建。
使用 New-AzStorageAccount 创建 Azure 存储帐户。 将 <replace-with-your-unique-storage-account-name> 替换为在所有 Azure 位置中唯一的、长度为 3-24 个字符且仅使用数字和小写字母的名称。
$storageAcctName = '<replace-with-your-unique-storage-account-name>'
$storage = @{
Location = 'chinanorth3'
Name = $storageAcctName
ResourceGroupName = 'test-rg'
SkuName = 'Standard_LRS'
Kind = 'StorageV2'
}
New-AzStorageAccount @storage
创建存储帐户后,使用 Get-AzStorageAccountKey 将存储帐户的密钥检索到一个变量中:
$storagekey = @{
ResourceGroupName = 'test-rg'
AccountName = $storageAcctName
}
$storageAcctKey = (Get-AzStorageAccountKey @storagekey).Value[0]
在后面的步骤中将使用此密钥来创建文件共享。 输入 $storageAcctKey 并记下该值。 在稍后的步骤中,当您将文件共享映射到虚拟机中的驱动器时,请手动输入该值。
对于通过为服务终结点启用的 Azure 服务创建的资源,限制对其的网络访问时所需的步骤因服务而异。 请参阅各个服务的文档来了解适用于每个服务的具体步骤。 作为示例,本文的剩余部分包括了针对 Azure 存储帐户限制网络访问的步骤。
创建存储帐户
使用 az storage account create 创建一个 Azure 存储帐户。 将 <replace-with-your-unique-storage-account-name> 替换为在所有 Azure 位置中唯一的、长度为 3-24 个字符且仅使用数字和小写字母的名称。
storageAcctName="<replace-with-your-unique-storage-account-name>"
az storage account create \
--name $storageAcctName \
--resource-group test-rg \
--sku Standard_LRS \
--kind StorageV2
创建存储帐户后,使用 az storage account show-connection-string 将存储帐户的连接字符串检索到一个变量中。 在后面的步骤中将使用此连接字符串来创建文件共享。
saConnectionString=$(az storage account show-connection-string \
--name $storageAcctName \
--resource-group test-rg \
--query 'connectionString' \
--out tsv)
重要
Microsoft 建议使用最安全的可用身份验证流。 本程序中描述的身份验证流程需要对应用程序有非常高的信任度,并且存在其他流程中不存在的风险。 请仅在无法使用其他更安全的流(例如托管标识)时才使用此流。
有关使用托管标识连接到存储帐户的详细信息,请参阅使用托管标识访问 Azure 存储。
在存储帐户中创建文件共享
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
在“存储帐户”中,选择在前面步骤中创建的存储帐户。
在“数据存储”中,选择“文件共享”。
选择 + 文件共享。
在“新文件共享”中,输入或选择以下信息:
| 设置 |
值 |
| 名称 |
输入文件共享。 |
| 层 |
保留默认值“事务优化”。 |
选择“下一步:备份”。
取消选择“启用备份”。
选择查看 + 创建,然后选择创建。
使用 New-AzStorageContext 为存储帐户和密钥创建上下文。 该上下文封装了存储帐户名称和帐户密钥:
$storagecontext = @{
StorageAccountName = $storageAcctName
StorageAccountKey = $storageAcctKey
}
$storageContext = New-AzStorageContext @storagecontext
使用 New-AzStorageShare 创建一个文件共享:
$fs = @{
Name = "file-share"
Context = $storageContext
}
$share = New-AzStorageShare @fs
使用 az storage share create 在存储帐户中创建一个文件共享。 在后续步骤中,将挂载该文件共享以确认可以通过网络访问它。
az storage share create \
--name file-share \
--quota 2048 \
--connection-string $saConnectionString > /dev/null
限制对子网的网络访问
默认情况下,存储帐户接受来自任何网络(包括 Internet)中的客户端的网络连接。 可限制来自 Internet 以及所有虚拟网络中的所有其他子网的网络访问(除vnet-1虚拟网络中的子网专用子网外)。
限制对子网的网络访问:
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
选择存储帐户。
在“安全性 + 网络”中,选择“网络”。
在“防火墙和虚拟网络”选项卡中,在“公共网络访问”下选择“已从所选虚拟网络和 IP 地址启用”。
在“虚拟网络”中,选择“+ 添加现有虚拟网络”。
在“添加网络”中,输入或选择以下信息:
| 设置 |
值 |
| 订阅 |
选择订阅。 |
| 虚拟网络 |
选择“vnet-1”。 |
| 子网 |
选择“subnet-private”。 |
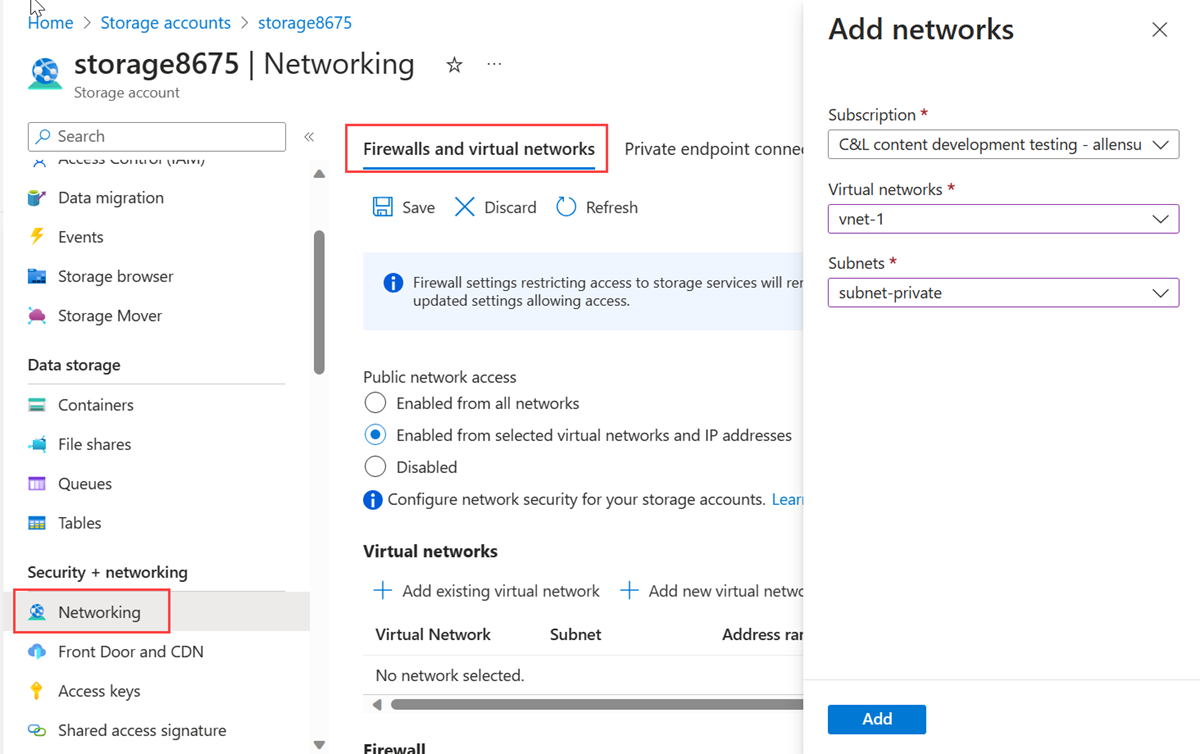
选择 添加 。
选择“保存”按钮保存虚拟网络配置。
默认情况下,存储帐户接受来自任何网络中的客户端的网络连接。 若要仅允许所选的网络进行访问,请使用 Update-AzStorageAccountNetworkRuleSet 将默认操作更改为 Deny。 在拒绝网络访问后,将无法从任何网络访问存储帐户。
$storagerule = @{
ResourceGroupName = "test-rg"
Name = $storageAcctName
DefaultAction = "Deny"
}
Update-AzStorageAccountNetworkRuleSet @storagerule
使用 Get-AzVirtualNetwork 检索所创建的虚拟网络,然后使用 Get-AzVirtualNetworkSubnetConfig 将专用子网对象检索到一个变量中:
$subnetpriv = @{
ResourceGroupName = "test-rg"
Name = "vnet-1"
}
$privateSubnet = Get-AzVirtualNetwork @subnetpriv | Get-AzVirtualNetworkSubnetConfig -Name "subnet-private"
使用 Add-AzStorageAccountNetworkRule 允许从 subnet-private 子网对存储帐户进行网络访问。
$storagenetrule = @{
ResourceGroupName = "test-rg"
Name = $storageAcctName
VirtualNetworkResourceId = $privateSubnet.Id
}
Add-AzStorageAccountNetworkRule @storagenetrule
默认情况下,存储帐户接受来自任何网络中的客户端的网络连接。 若要仅允许所选的网络进行访问,请使用 az storage account update 将默认操作更改为 Deny。 在拒绝网络访问后,将无法从任何网络访问存储帐户。
az storage account update \
--name $storageAcctName \
--resource-group test-rg \
--default-action Deny
使用 az storage account network-rule add 命令允许从“subnet-private”子网对存储帐户进行网络访问。
az storage account network-rule add \
--resource-group test-rg \
--account-name $storageAcctName \
--vnet-name vnet-1 \
--subnet subnet-private
将虚拟机部署到子网
要测试对存储帐户的网络访问,请向每个子网部署虚拟机。
创建测试虚拟机
以下过程会在虚拟网络中创建一个名为 vm-1 的测试虚拟机 (VM)。
在门户中,搜索并选择“虚拟机”。
在“虚拟机”中,选择“+ 创建”。
在“创建虚拟机”的“基本信息”选项卡上,输入或选择以下信息:
| 设置 |
值 |
|
项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择“test-rg”。 |
|
实例详细信息 |
|
| 虚拟机名称 |
输入“vm-1”。 |
| 区域 |
选择“中国东部 2”。 |
| 可用性选项 |
选择“无需基础结构冗余”。 |
| 安全类型 |
保留默认值标准。 |
| 图像 |
选择Windows Server 2022 Datacenter - x64 Gen2。 |
| VM 架构 |
保留默认值“x64”。 |
| 大小 |
选择一个大小。 |
|
管理员帐户 |
|
| 身份验证类型 |
选择密码。 |
| 用户名 |
输入“azureuser”。 |
| 密码 |
输入密码。 |
| 确认密码 |
重新输入密码。 |
|
入站端口规则 |
|
| 公共入站端口 |
选择“无”。 |
选择页面顶部的“网络”选项卡。
在“网络”选项卡中,输入或选择以下信息:
| 设置 |
值 |
|
网络接口 |
|
| 虚拟网络 |
选择“vnet-1”。 |
| 子网 |
选择“subnet-1 (10.0.0.0/24)”。 |
| 公共 IP |
选择“无”。 |
| NIC 网络安全组 |
选择“高级”。 |
| 配置网络安全组 |
选择“新建”。
在“名称”中输入“nsg-1”。
将其余字段保留默认设置,然后选择“确定”。 |
将其余设置保留为默认值,然后选择“查看 + 创建”。
检查设置,然后选择“创建”。
注意事项
虚拟网络中具有堡垒主机的虚拟机不需要公共 IP 地址。 Bastion 提供公共 IP,虚拟机使用专用 IP 在网络中进行通信。 可以从堡垒托管的虚拟网络的任何虚拟机中删除公共 IP。 有关详细信息,请参阅 将公共 IP 地址与 Azure VM 取消关联。
注意事项
Azure 会为未分配公共 IP 地址的 VM 或位于内部基本 Azure 负载均衡器的后端池中的 VM 提供默认出站访问 IP。 默认出站访问 IP 机制会提供不可配置的出站 IP 地址。
发生以下事件之一时,将禁用默认出站访问 IP:
在灵活业务流程模式下通过使用虚拟机规模集创建的 VM 没有默认的出站访问权限。
有关 Azure 中的出站连接的详细信息,请参阅 Azure 中的默认出站访问,使用源网络地址转换(SNAT)进行出站连接。
创建第二个虚拟机
创建第二个虚拟机,重复上一部分中的步骤。 替换“创建虚拟机”中的以下值:
| 设置 |
值 |
| 虚拟机名称 |
输入vm-private。 |
| 子网 |
选择“subnet-private”。 |
| 公共 IP |
选择“无”。 |
| NIC 网络安全组 |
选择“无”。 |
创建第一个虚拟机
使用 New-AzVM 在 subnet-public 子网中创建虚拟机。 运行以下命令时,会提示输入凭据。 输入的值将配置为用于 VM 的用户名和密码。
$vm1 = @{
ResourceGroupName = "test-rg"
Location = "chinanorth3"
VirtualNetworkName = "vnet-1"
SubnetName = "subnet-public"
Name = "vm-public"
PublicIpAddressName = $null
}
New-AzVm @vm1
创建第二个虚拟机
在 subnet-private 子网中创建一台虚拟机:
$vm2 = @{
ResourceGroupName = "test-rg"
Location = "chinanorth3"
VirtualNetworkName = "vnet-1"
SubnetName = "subnet-private"
Name = "vm-private"
PublicIpAddressName = $null
}
New-AzVm @vm2
Azure 需要花费几分钟时间来创建 VM。 在 Azure 完成创建 VM 并将输出返回到 PowerShell 之前,请不要继续执行下一步骤。
若要测试对存储帐户的网络访问,请向每个子网部署 VM。
创建第一个虚拟机
使用 az vm create 在 subnet-public 子网中创建一个 VM。 如果默认密钥位置中尚不存在 SSH 密钥,该命令会创建它们。 若要使用特定的一组密钥,请使用 --ssh-key-value 选项。
az vm create \
--resource-group test-rg \
--name vm-public \
--image Ubuntu2204 \
--vnet-name vnet-1 \
--subnet subnet-public \
--admin-username azureuser \
--generate-ssh-keys
创建 VM 需要几分钟时间。 创建 VM 之后,Azure CLI 将显示类似于以下示例的信息:
{
"fqdns": "",
"id": "/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/test-rg/providers/Microsoft.Compute/virtualMachines/vm-public",
"location": "westus2",
"macAddress": "00-0D-3A-23-9A-49",
"powerState": "VM running",
"privateIpAddress": "10.0.0.4",
"publicIpAddress": "203.0.113.24",
"resourceGroup": "test-rg"
}
创建第二个虚拟机
az vm create \
--resource-group test-rg \
--name vm-private \
--image Ubuntu2204 \
--vnet-name vnet-1 \
--subnet subnet-private \
--admin-username azureuser \
--generate-ssh-keys
创建 VM 需要几分钟时间。
确认对存储帐户的访问
之前创建的分配给子网专用子网的虚拟机用于确认对存储帐户的访问。 您在上一部分中创建的分配给子网 1的虚拟机将用于确认存储帐户访问已被阻止。
获取存储帐户访问密钥
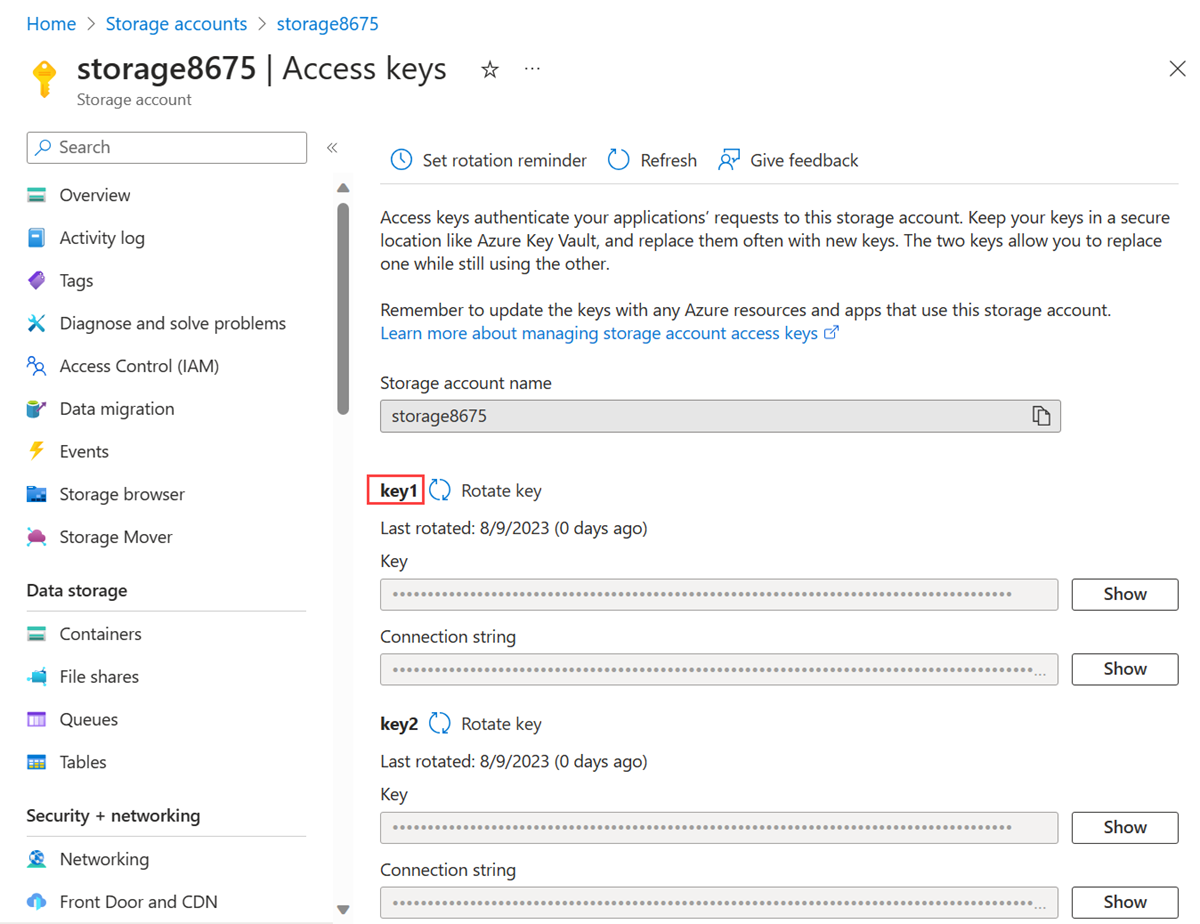
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
在“存储帐户”中,选择存储帐户。
在“安全性 + 网络”中,选择“访问密钥”。
复制key1值。 可能需要选择“显示”按钮以显示密钥。
在门户顶部的搜索框中,输入虚拟机。 在搜索结果中,选择“虚拟机”。
选择“vm-private”。
在操作中选择Bastion。
输入在创建虚拟机时指定的用户名和密码。 选择“连接” 。
打开 Windows PowerShell。 使用以下脚本将 Azure 文件共享映射到驱动器 Z。
$key = @{
String = "<storage-account-key>"
}
$acctKey = ConvertTo-SecureString @key -AsPlainText -Force
$cred = @{
ArgumentList = "Azure\<storage-account-name>", $acctKey
}
$credential = New-Object System.Management.Automation.PSCredential @cred
$map = @{
Name = "Z"
PSProvider = "FileSystem"
Root = "\\<storage-account-name>.file.core.chinacloudapi.cn\file-share"
Credential = $credential
}
New-PSDrive @map
PowerShell 将返回类似于以下示例的输出:
Name Used (GB) Free (GB) Provider Root
---- --------- --------- -------- ----
Z FileSystem \\storage8675.file.core.chinacloudapi.cn\f...
Azure 文件共享已成功映射到驱动器 Z。
关闭与vm-private的 Bastion 连接。
之前创建的分配给子网专用子网的虚拟机用于确认对存储帐户的访问。 您在上一部分中创建的分配给子网 1的虚拟机将用于确认存储帐户访问已被阻止。
获取存储帐户访问密钥
登录到 Azure 门户。
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
在“存储帐户”中,选择存储帐户。
在“安全性 + 网络”中,选择“访问密钥”。
复制key1值。 可能需要选择“显示”按钮以显示密钥。

在门户顶部的搜索框中,输入虚拟机。 在搜索结果中,选择“虚拟机”。
选择“vm-private”。
在概述中,选择连接,然后选择通过 Bastion 连接。
输入在创建虚拟机时指定的用户名和密码。 选择“连接” 。
打开 Windows PowerShell。 使用以下脚本将 Azure 文件共享映射到驱动器 Z。
$key = @{
String = "<storage-account-key>"
}
$acctKey = ConvertTo-SecureString @key -AsPlainText -Force
$cred = @{
ArgumentList = "Azure\<storage-account-name>", $acctKey
}
$credential = New-Object System.Management.Automation.PSCredential @cred
$map = @{
Name = "Z"
PSProvider = "FileSystem"
Root = "\\<storage-account-name>.file.core.chinacloudapi.cn\file-share"
Credential = $credential
}
New-PSDrive @map
PowerShell 将返回类似于以下示例的输出:
Name Used (GB) Free (GB) Provider Root
---- --------- --------- -------- ----
Z FileSystem \\storage8675.file.core.chinacloudapi.cn\f...
Azure 文件共享已成功映射到驱动器 Z。
确认 VM 没有与其他任何公网 IP 地址的出站连接。
ping bing.com
你不会收到回复,因为除了分配给 Azure 存储服务的地址之外,关联到 Private 子网的网络安全组不允许对其他公共 IP 地址的出站访问。
关闭与vm-private的 Bastion 连接。
通过 SSH 连接到 vm-private VM。
运行以下命令以将 VM 的 IP 地址存储为环境变量:
export IP_ADDRESS=$(az vm show --show-details --resource-group test-rg --name vm-private --query publicIps --output tsv)
ssh -o StrictHostKeyChecking=no azureuser@$IP_ADDRESS
为装入点创建一个文件夹:
sudo mkdir /mnt/file-share
将 Azure 文件共享装载到你创建的目录中。 在运行以下命令之前,将 <storage-account-name> 替换为帐户名称,将 <storage-account-key> 替换为在创建存储帐户中检索到的密钥。
sudo mount --types cifs //<storage-account-name>.file.core.chinacloudapi.cn/my-file-share /mnt/file-share --options vers=3.0,username=<storage-account-name>,password=<storage-account-key>,dir_mode=0777,file_mode=0777,serverino
你将收到 user@vm-private:~$ 提示。 Azure 文件共享已成功装载到 /mnt/file-share。
确认 VM 没有与其他任何公网 IP 地址的出站连接。
ping bing.com -c 4
你不会收到回复,因为除了分配给 Azure 存储服务的地址之外,关联到 subnet-private 子网的网络安全组不允许对其他公共 IP 地址进行出站访问。
退出与 vm-private VM 的 SSH 会话。
确认已拒绝对存储帐户的访问
从 vm-1
在门户顶部的搜索框中,输入虚拟机。 在搜索结果中,选择“虚拟机”。
选择 vm-1。
在操作中选择Bastion。
输入在创建虚拟机时指定的用户名和密码。 选择“连接” 。
重复上述命令,尝试将驱动器映射到存储帐户中的文件共享。 对于此过程,可能需要再次复制存储帐户访问密钥:
$key = @{
String = "<storage-account-key>"
}
$acctKey = ConvertTo-SecureString @key -AsPlainText -Force
$cred = @{
ArgumentList = "Azure\<storage-account-name>", $acctKey
}
$credential = New-Object System.Management.Automation.PSCredential @cred
$map = @{
Name = "Z"
PSProvider = "FileSystem"
Root = "\\<storage-account-name>.file.core.chinacloudapi.cn\file-share"
Credential = $credential
}
New-PSDrive @map
会收到以下错误信息:
New-PSDrive : Access is denied
At line:1 char:5
+ New-PSDrive @map
+ ~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (Z:PSDriveInfo) [New-PSDrive], Win32Exception
+ FullyQualifiedErrorId : CouldNotMapNetworkDrive,Microsoft.PowerShell.Commands.NewPSDriveCommand
关闭与vm-1的 Bastion 连接。
从本地计算机上
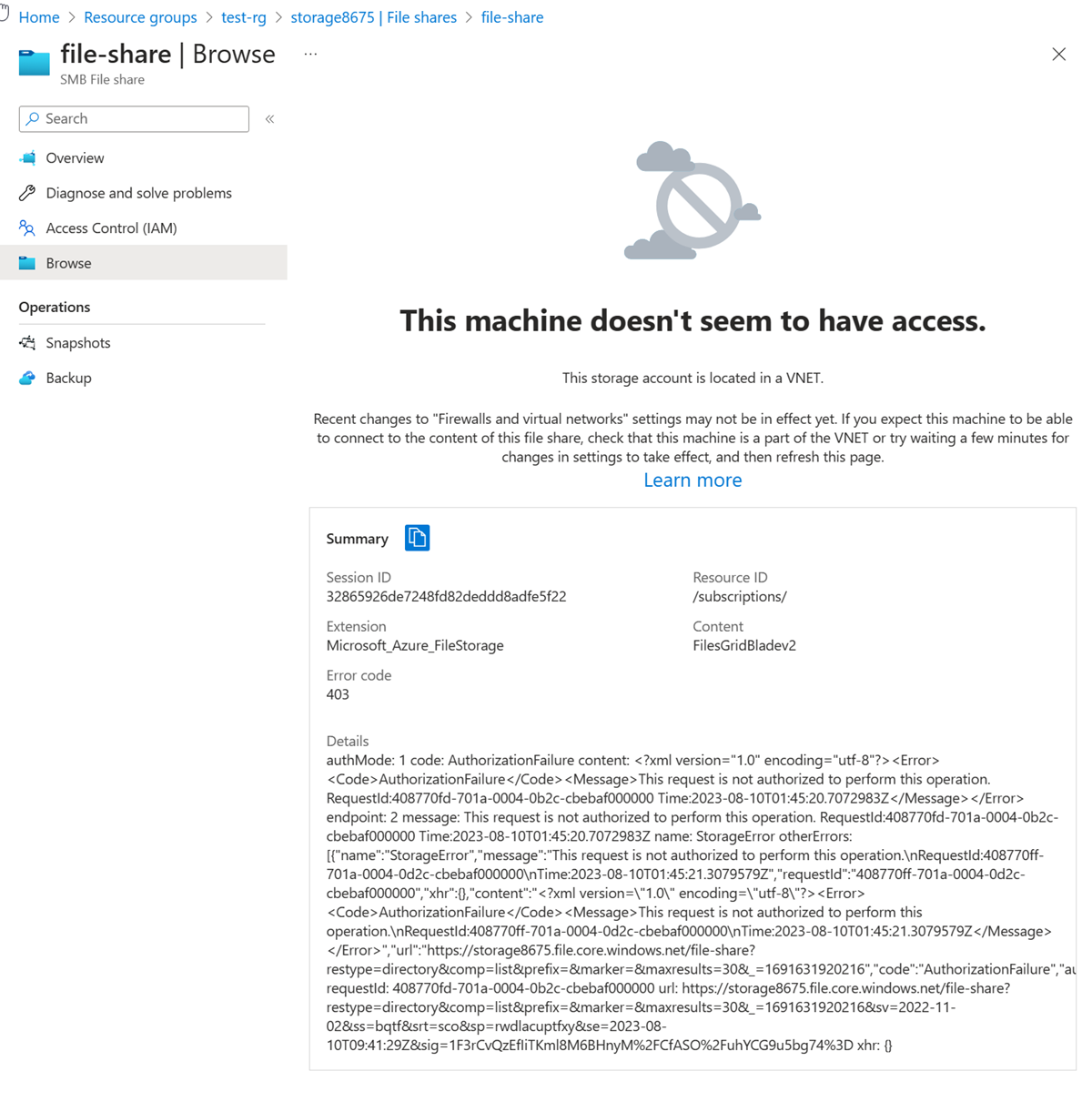
在门户顶部的搜索框中,输入“存储帐户”。 在搜索结果中选择“存储帐户”。
在“存储帐户”中,选择存储帐户。
在“数据存储”中,选择“文件共享”。
选择“文件共享”。
在左侧菜单中,选择“浏览”。
会收到以下错误信息:
注意事项
访问被拒绝,因为计算机不在vnet-1虚拟网络的子网专用子网中。
从 vm-1
在门户顶部的搜索框中,输入虚拟机。 在搜索结果中,选择“虚拟机”。
选择 vm-1。
在操作中选择Bastion。
输入在创建虚拟机时指定的用户名和密码。 选择“连接” 。
重复上述命令,尝试将驱动器映射到存储帐户中的文件共享。 对于此过程,可能需要再次复制存储帐户访问密钥:
$key = @{
String = "<storage-account-key>"
}
$acctKey = ConvertTo-SecureString @key -AsPlainText -Force
$cred = @{
ArgumentList = "Azure\<storage-account-name>", $acctKey
}
$credential = New-Object System.Management.Automation.PSCredential @cred
$map = @{
Name = "Z"
PSProvider = "FileSystem"
Root = "\\<storage-account-name>.file.core.chinacloudapi.cn\file-share"
Credential = $credential
}
New-PSDrive @map
会收到以下错误信息:
New-PSDrive : Access is denied
At line:1 char:5
+ New-PSDrive @map
+ ~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (Z:PSDriveInfo) [New-PSDrive], Win32Exception
+ FullyQualifiedErrorId : CouldNotMapNetworkDrive,Microsoft.PowerShell.Commands.NewPSDriveCommand
关闭与vm-1的 Bastion 连接。
从计算机中,尝试使用以下命令查看存储帐户中的文件共享:
$storage = @{
ShareName = "file-share"
Context = $storageContext
}
Get-AzStorageFile @storage
拒绝访问。 将会收到类似于以下示例的输出。
Get-AzStorageFile : The remote server returned an error: (403) Forbidden. HTTP Status Code: 403 - HTTP Error Message: This request isn't authorized to perform this operation
计算机不在 subnet-private 子网的 vnet-1 虚拟网络中。
通过 SSH 连接到 vm-public VM。
运行以下命令以将 VM 的 IP 地址存储为环境变量:
export IP_ADDRESS=$(az vm show --show-details --resource-group test-rg --name vm-public --query publicIps --output tsv)
ssh -o StrictHostKeyChecking=no azureuser@$IP_ADDRESS
为装入点创建一个目录:
sudo mkdir /mnt/file-share
尝试将 Azure 文件共享装载到你创建的目录中。 本文假定你已部署了 Ubuntu 的最新版本。 如果使用的是早期版本的 Ubuntu,请参阅在 Linux 上装载来了解有关装载文件共享的更多说明。 在运行以下命令之前,将 <storage-account-name> 替换为帐户名称,将 <storage-account-key> 替换为在创建存储帐户时检索到的密钥:
sudo mount --types cifs //storage-account-name>.file.core.chinacloudapi.cn/file-share /mnt/file-share --options vers=3.0,username=<storage-account-name>,password=<storage-account-key>,dir_mode=0777,file_mode=0777,serverino
访问被拒绝,并且你将收到 mount error(13): Permission denied 错误,因为 vm-public VM 部署在 subnet-public 子网中。 subnet-public 子网没有为 Azure 存储启用服务终结点,并且存储帐户仅允许来自 subnet-private 子网(而不是 subnet-public 子网)的网络访问。
退出与 vm-public VM 的 SSH 会话。
从计算机中,尝试使用 az storage share list 查看存储帐户中的共享。 将 <account-name> 和 <account-key> 替换为在创建存储帐户中获得的存储帐户名称和密钥:
az storage share list \
--account-name <account-name> \
--account-key <account-key>
访问被拒绝,并且你将收到“此请求无权执行此操作”错误,因为你的计算机不在 vnet-1 虚拟网络的 subnet-private 子网中。
清理资源
使用创建的资源之后,可以删除资源组及其所有资源:
在 Azure 门户中,搜索并选择“资源组”。
在“资源组”页上,选择“test-rg”资源组。
在“test-rg”页上,选择“删除资源组”。
在“输入资源组名称以确认删除”中输入“test-rg”,然后选择“删除”。
如果不再需要资源组及其包含的所有资源,请使用 Remove-AzResourceGroup 将其删除:
$cleanup = @{
Name = "test-rg"
}
Remove-AzResourceGroup @cleanup -Force
清理资源
如果不再需要资源组及其包含的所有资源,可以使用 az group delete 将其删除。
az group delete \
--name test-rg \
--yes \
--no-wait
后续步骤
本教程的内容:
若要详细了解服务终结点,请参阅服务终结点概述和管理子网。
如果你的帐户中有多个虚拟网络,你可能需要在这些虚拟网络之间建立连接,使资源能够相互通信。 若要了解如何连接虚拟网络,请继续学习下一教程。






