在较大的 Azure 客户中,一种常见情况是需要向 Internet 公开某个双层应用程序,同时允许从本地数据中心访问后端层。 本文会指导你使用路由表、VPN 网关和网络虚拟设备来部署双层环境,该方案可满足以下要求:
- 只能从公共 Internet 访问 Web 应用程序。
- 托管应用程序的 Web 服务器必须能够访问后端应用程序服务器。
- 从 Internet 到 Web 应用程序的所有流量必须流经防火墙虚拟设备。 此虚拟设备只用于 Internet 流量。
- 发往应用程序服务器的所有流量必须流经防火墙虚拟设备。 此虚拟设备用于访问后端服务器,并用于通过 VPN 网关从本地网络传入的访问。
- 管理员必须能够使用第三个防火墙虚拟设备(专门用于管理目的)从其本地计算机管理防火墙虚拟设备。
此示例是一个标准的外围网络(也称为 DMZ)方案,其中包含一个 DMZ 和一个受保护网络。 可以在 Azure 中使用网络安全组 (NSG) 和/或防火墙虚拟设备来构建此方案。
下表显示了 NSG 与防火墙虚拟设备的一些优缺点。
| 条目 | 优点 | 缺点 |
|---|---|---|
| 核供应国集团 (NSG) | 无需付费。 已集成到 Azure 基于角色的访问中。 能够在 Azure 资源管理器模板中创建规则。 |
在大型环境中复杂性各不相同。 |
| 防火墙 | 完全控制数据平面。 通过防火墙控制台进行集中管理。 |
防火墙设备的费用。 未与 Azure 基于角色的访问集成。 |
以下解决方案使用防火墙虚拟设备来实施外围网络 (DMZ)/受保护网络方案。
注意事项
可以使用目前提供的功能在 Azure 中部署上述环境:
- 虚拟网络:Azure 虚拟网络在形式上与本地网络类似。 可以将它分段为一个或多个子网,以提供流量隔离和关注点分离。
- 虚拟设备:有多个合作伙伴在 Azure 市场中提供了虚拟设备,可用于前述三种防火墙。
-
路由表:Azure 网络使用路由表来控制数据包在虚拟网络中的流动。 可以将这些路由表应用到子网。 可以将路由表应用到
GatewaySubnet,该路由表会将从混合连接进入 Azure 虚拟网络的所有流量转发到虚拟设备。 - IP 转发:默认情况下,仅当数据包目标 IP 地址与 NIC IP 地址匹配时,Azure 网络引擎才将数据包转发到虚拟网络接口卡 (NIC)。 如果路由表的定义表明必须将数据包发送到特定的虚拟设备,则 Azure 网络引擎会丢弃该数据包。 为了确保将数据包传送到并非数据包实际目标的 VM(在本例中为虚拟设备),请为虚拟设备启用 IP 转发。
- 网络安全组:以下示例不使用 NSG,但可以在此解决方案中使用应用于子网或 NIC 的 NSG。 NSG 会进一步筛选进出这些子网和 NIC 的流量。
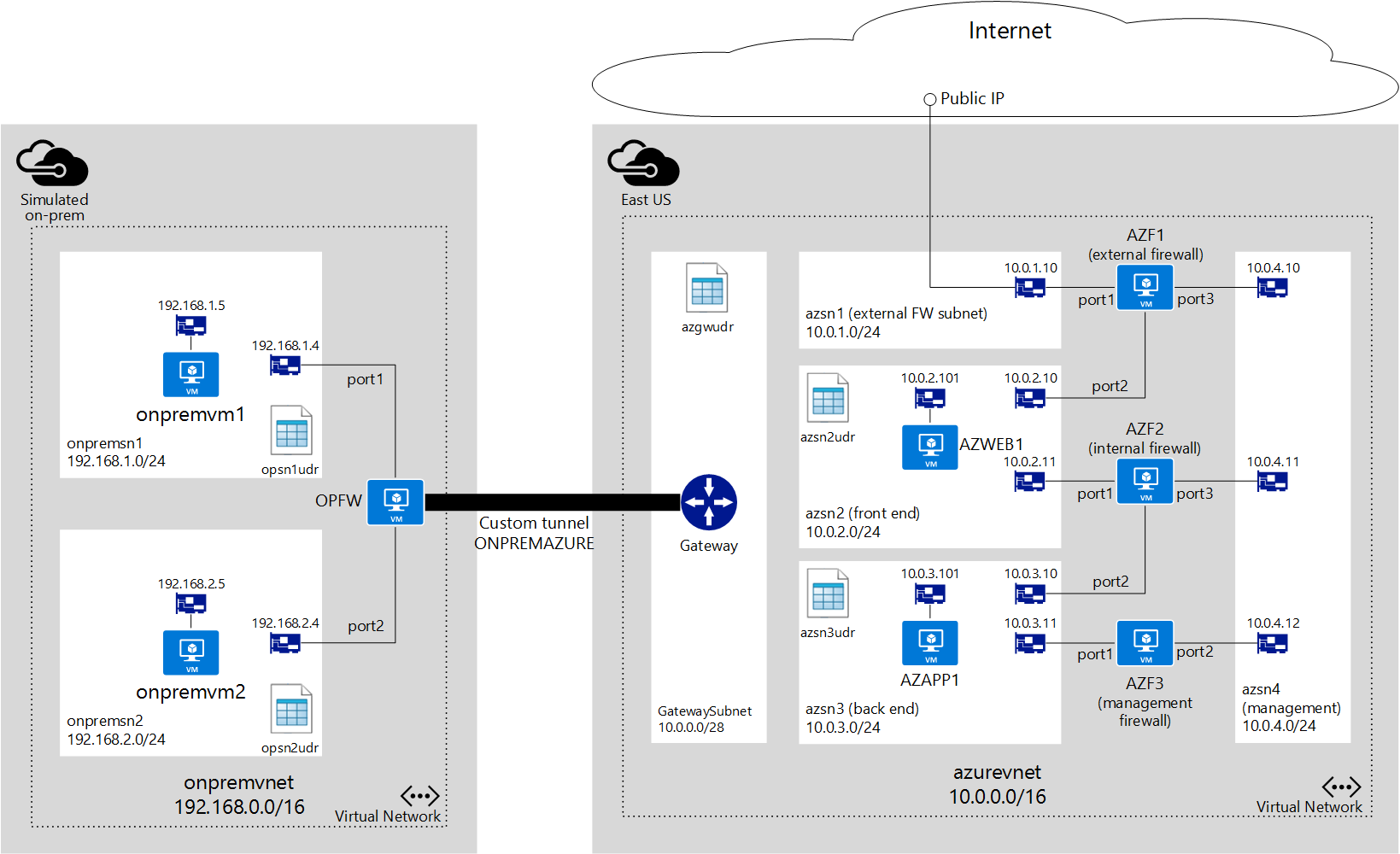
在本示例中,订阅包含以下项:
两个资源组(未在示意图中显示):
-
ONPREMRG:包含模拟本地网络所需的所有资源。 -
AZURERG:包含 Azure 虚拟网络环境所需的所有资源。
-
名为
onpremvnet的虚拟网络进行了分段,并用于模拟本地数据中心:-
onpremsn1:包含运行 Linux 发行版的虚拟机 (VM) 的子网,用于模拟本地服务器。 -
onpremsn2:包含运行 Linux 发行版的 VM 的子网,用于模拟管理员使用的计算机。
-
一个名为
OPFW的防火墙虚拟设备位于onpremvnet上。 它用于维护到azurevnet的隧道。名为
azurevnet的虚拟网络分段如下:-
azsn1:专门用于外部防火墙的外部防火墙子网。 所有 Internet 流量都通过此子网传入。 此子网仅包含一个链接到外部防火墙的 NIC。 -
azsn2:前端子网,托管作为 Web 服务器运行的、从 Internet 访问的 VM。 -
azsn3:后端子网,托管运行后端应用程序服务器的、由前端 Web 服务器访问的 VM。 -
azsn4:管理子网,专门用于提供对所有防火墙虚拟设备的管理访问权限。 此子网仅包含解决方案中使用的每个防火墙虚拟设备的 NIC。 -
GatewaySubnet:Azure ExpressRoute 和 Azure VPN 网关在 Azure 虚拟网络与其他网络之间提供连接所需的 Azure 混合连接子网。
-
azurevnet网络中有三个防火墙虚拟设备:-
AZF1:在 Azure 中使用公共 IP 地址资源向公共 Internet 公开的外部防火墙。 需要确保从 Azure 市场或者直接从设备供应商那里获取一个模板,用于部署具有三个 NIC 的虚拟设备。 -
AZF2:用于控制azsn2与azsn3之间流量的内部防火墙。 此防火墙也是一个具有三个 NIC 的虚拟设备。 -
AZF3:管理员可从本地数据中心访问的管理防火墙,它已连接到用于管理所有防火墙设备的管理子网。 可以在 Azure 市场中查找具有两个 NIC 的虚拟设备模板。 也可以直接向设备供应商请求一个。
-
路由表
将 Azure 中的每个子网链接到路由表,以定义该子网中发起的流量的路由方式。 如果未定义用户定义的路由 (UDR),Azure 会使用默认路由来允许流量从一个子网流向另一个子网。 若要更好地了解路由表和流量路由,请参阅 Azure 虚拟网络流量路由。
为了确保根据前述最后一项要求通过适当的防火墙设备进行通信,必须在 azurevnet 中创建以下路由表。
azgwudr
在此方案中,只会通过连接到 AZF3,使用从本地流往 Azure 的流量来管理防火墙,并且这些流量必须通过内部防火墙 AZF2。
GatewaySubnet 中只需要一个路由,如下所示:
| 目的地 | 下一跳 | 说明 |
|---|---|---|
| 10.0.4.0/24 | 10.0.3.11 | 允许本地流量到达管理防火墙 AZF3。 |
azsn2udr
| 目的地 | 下一跳 | 说明 |
|---|---|---|
| 10.0.3.0/24 | 10.0.2.11 | 允许流量通过 AZF2 到达托管应用程序服务器的后端子网。 |
| 0.0.0.0/0 | 10.0.2.10 | 允许通过 AZF1 路由所有其他流量。 |
azsn3udr
| 目的地 | 下一跳 | 说明 |
|---|---|---|
| 10.0.2.0/24 | 10.0.3.10 | 允许通过 azsn2 将发往 AZF2 的流量从应用服务器传送到 Web 服务器。 |
还需要为 onpremvnet 中的子网创建路由表用于模拟本地数据中心。
onpremsn1udr
| 目的地 | 下一跳 | 说明 |
|---|---|---|
| 192.168.2.0/24 | 192.168.1.4 | 允许通过 onpremsn2 将流量传送到 OPFW。 |
onpremsn2udr
| 目的地 | 下一跳 | 说明 |
|---|---|---|
| 10.0.3.0/24 | 192.168.2.4 | 允许通过 OPFW 将流量传送到 Azure 中的后端子网。 |
| 192.168.1.0/24 | 192.168.2.4 | 允许通过 onpremsn1 将流量传送到 OPFW。 |
IP 转发
可以结合使用路由表和 IP 转发功能,以允许虚拟设备控制 Azure 虚拟网络中的流量流。 虚拟设备只是一个 VM,该 VM 所运行的应用程序用于通过某种方式(例如防火墙或网络地址转换设备)处理网络流量。
此虚拟设备 VM 必须能够接收不发送给自身的传入流量。 若要允许 VM 接收发送到其他目标的流量,必须为该 VM 启用 IP 转发。 此设置是 Azure 设置,不是来宾操作系统中的设置。 虚拟设备仍需要运行某种类型的应用程序来处理传入流量并相应地路由这些流量。
若要详细了解 IP 转发,请参阅 Azure 虚拟网络流量路由。
例如,假设在 Azure 虚拟网络中具有以下设置:
- 子网
onpremsn1包含一个名为onpremvm1的 VM。 - 子网
onpremsn2包含一个名为onpremvm2的 VM。 - 名为
OPFW的虚拟设备已连接到onpremsn1和onpremsn2。 - 链接到
onpremsn1的 UDR 指定必须将所有到达onpremsn2的流量发送到OPFW。
此时,如果 onpremvm1 尝试与 onpremvm2 建立连接,则会使用 UDR,并将流量发送到 OPFW 作为下一跃点。 实际数据包目标不会更改。 它仍然显示 onpremvm2 是目的地。
如果没有为 OPFW 启用 IP 转发,Azure 虚拟网络逻辑会丢弃数据包,因为仅当 VM 的 IP 地址是数据包的目标时,它才允许将数据包发送到 VM。
如果启用了 IP 转发,Azure 虚拟网络逻辑会将数据包转发到 OPFW,且不会更改其原始目标地址。
OPFW 必须处理数据包并决定如何处理它们。
要正常运行前面的方案,必须在用于路由的 OPFW、AZF1、AZF2 和 AZF3 的 NIC(除链接到管理子网以外的所有 NIC)上启用 IP 转发。
防火墙规则
如前文所述,IP 转发仅确保将数据包发送到虚拟设备。 设备仍需要确定如何处理这些数据包。 在之前的方案中,需要在设备中创建以下规则。
OPFW
OPFW 代表包含以下规则的本地设备:
-
路由:所有发往 10.0.0.0/16 (
azurevnet) 的流量都必须通过隧道ONPREMAZURE发送。 -
策略:允许
port2与ONPREMAZURE之间的所有双向流量。
AZF1
AZF1 表示包含以下规则的 Azure 虚拟设备:
策略:允许 port1 与 port2 之间的所有双向流量。
AZF2
AZF2 表示包含以下规则的 Azure 虚拟设备:
策略:允许 port1 与 port2 之间的所有双向流量。
AZF3
AZF3 表示包含以下规则的 Azure 虚拟设备:
路由:发往 192.168.0.0/16 (onpremvnet) 的所有流量都必须通过 port1 发送到 Azure 网关 IP 地址(即 10.0.0.1)。
网络安全组
此方案中未使用 NSG。 但是,可以向每个子网应用 NSG,以限制传入和传出的流量。 例如,可将以下 NSG 规则应用到外部防火墙子网。
传入
- 允许所有 TCP 流量从 Internet 发往子网中任何 VM 上的端口 80。
- 拒绝来自 Internet 的所有其他流量。
传出
拒绝发往 Internet 的所有流量。
高级步骤
要部署此方案,请执行以下步骤:
登录到 Azure 订阅。
如果要部署虚拟网络来模拟本地网络,请部署属于
ONPREMRG的资源。部署属于
AZURERG的资源。部署从
onpremvnet到azurevnet的隧道。预配所有资源后,请登录到
onpremvm2并 ping 10.0.3.101,以测试onpremsn2与azsn3之间的连接。