Create a network security group (classic) using the Azure classic CLI
You can use an NSG to control traffic to one or more virtual machines (VMs), role instances, network adapters (NICs), or subnets in your virtual network. An NSG contains access control rules that allow or deny traffic based on traffic direction, protocol, source address and port, and destination address and port. The rules of an NSG can be changed at any time, and changes are applied to all associated instances.
For more information about NSGs, visit what is an NSG.
Important
Before you work with Azure resources, it's important to understand that Azure currently has two deployment models: Azure Resource Manager and classic. Make sure you understand deployment models and tools before you work with any Azure resource. You can view the documentation for different tools by clicking the tabs at the top of this article.
This article covers the classic deployment model. You can also create NSGs in the Resource Manager deployment model.
Scenario
To better illustrate how to create NSGs, this document uses the following scenario:
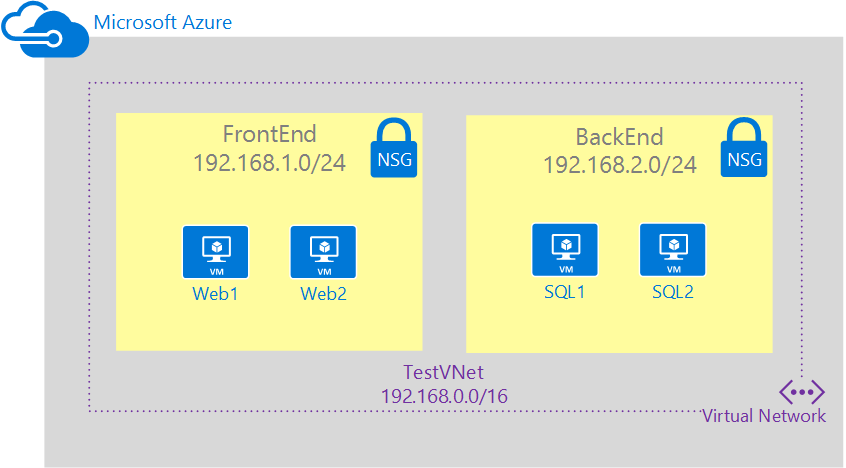
In this scenario, you create an NSG for each subnet in the TestVNet virtual network, as follows:
- NSG-FrontEnd. The front-end NSG is applied to the FrontEnd subnet, and contains two rules:
- rdp-rule. Allows RDP traffic to the FrontEnd subnet.
- web-rule. Allows HTTP traffic to the FrontEnd subnet.
- NSG-BackEnd. The back-end NSG is applied to the BackEnd subnet, and contains two rules:
- sql-rule. Allows SQL traffic only from the FrontEnd subnet.
- web-rule. Denies all internet bound traffic from the BackEnd subnet.
The combination of these rules create a DMZ-like scenario, where the back-end subnet can only receive incoming traffic for SQL from the front-end subnet, and has no access to the Internet, while the front-end subnet can communicate with the Internet, and receive incoming HTTP requests only.
The following sample Azure CLI commands expect a simple environment already created based on the scenario. If you want to run the commands as they are displayed in this document, first build the test environment by creating a VNet.
Create an NSG for the front-end subnet
If you have never used Azure CLI, see Install and Configure the Azure CLI.
Switch to classic mode:
azure config mode asmCreate an NSG::
azure network nsg create -l uswest -n NSG-FrontEndCreate a security rule that allows access to port 3389 (RDP) from the internet:
azure network nsg rule create -a NSG-FrontEnd -n rdp-rule -c Allow -p Tcp -r Inbound -y 100 -f Internet -o * -e * -u 3389Create a rule that allows access to port 80 (HTTP) from the internet:
azure network nsg rule create -a NSG-FrontEnd -n web-rule -c Allow -p Tcp -r Inbound -y 200 -f Internet -o * -e * -u 80Associate the NSG to the front-end subnet:
azure network nsg subnet add -a NSG-FrontEnd --vnet-name TestVNet --subnet-name FrontEnd
Create the NSG for the back-end subnet
Create the NSG:
azure network nsg create -l uswest -n NSG-BackEndCreate a rule that allows access to port 1433 (SQL) from the front-end subnet:
azure network nsg rule create -a NSG-BackEnd -n sql-rule -c Allow -p Tcp -r Inbound -y 100 -f 192.168.1.0/24 -o * -e * -u 1433Create a rule that denies access to the internet:
azure network nsg rule create -a NSG-BackEnd -n web-rule -c Deny -p Tcp -r Outbound -y 200 -f * -o * -e Internet -u 80Associate the NSG to the back-end subnet:
azure network nsg subnet add -a NSG-BackEnd --vnet-name TestVNet --subnet-name BackEnd