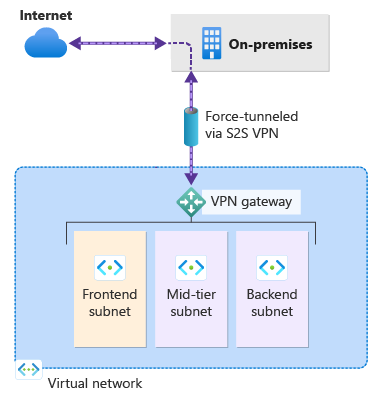
本文可帮助你了解强制隧道如何适用于站点到站点 (S2S) IPsec 连接。 默认情况下,来自虚拟网络中工作负载和 VM 的 Internet 绑定流量将直接发送到 Internet。
强制隧道可让你通过 S2S VPN 隧道将所有 Internet 绑定流量重定向或“强制”返回到本地位置来进行检查和审核。 这是很多企业 IT 策略的关键安全要求。 未经授权的 Internet 访问可能会导致信息泄漏或其他类型的安全漏洞。
以下示例显示所有 Internet 流量都强制通过 VPN 网关返回到本地位置进行检查和审核。
强制隧道的配置方法
可通过几种不同的方法来配置强制隧道。
使用 BGP 进行配置
可通过 BGP 为 VPN 网关配置强制隧道。 需要通过 BGP 将默认路由 0.0.0.0/0 从本地位置播发到 Azure,以便通过 VPN 网关 S2S 隧道发送所有 Azure 流量。
使用默认站点进行配置
可通过为基于路由的 VPN 网关设置默认站点来配置强制隧道。 相关步骤,请参阅通过默认站点进行强制隧道。
- 使用 PowerShell 为虚拟网络网关配置默认站点。
- 必须使用 0.0.0.0/0 作为流量选择器配置本地 VPN 设备。
路由特定子网的 Internet 绑定流量
默认情况下,如果未配置强制隧道,所有 Internet 绑定流量将直接发送到 Internet。 配置强制隧道后,所有 Internet 绑定流量都发送到本地位置。
在某些情况下,你可能只希望来自某些子网(但并非所有子网)的 Internet 绑定流量直接从 Azure 网络基础结构遍历到 Internet,而不是传输到本地位置。 可使用强制隧道和虚拟网络自定义用户定义的路由 (UDR) 的组合来配置此方案。 相关步骤,请参阅路由特定子网的 Internet 绑定流量。
后续步骤
有关虚拟网络流量路由的详细信息,请参阅 VNet 流量路由。