本文有助于你了解如何为跨界连接和 VNet 到 VNet 连接设计高可用网关连接。
关于 VPN 网关冗余
默认情况下,每个 Azure VPN 网关由两个采用主动-等待配置的实例组成。 当主动实例发生任何计划内维护或计划外中断时,待机实例会自动接管(故障转移)并恢复 S2S VPN 或 VNet 到 VNet 连接。 这种交接会造成短暂的中断。 发生计划内维护时,10 到 15 秒内应可恢复连接。 发生计划外的问题时,恢复连接所需的时间会更长,在最糟的情况下大约需要 1 到 3 分钟。 对于 P2S VPN 客户端到网关的连接,会断开 P2S 连接,并且用户需要从客户端计算机重新连接。
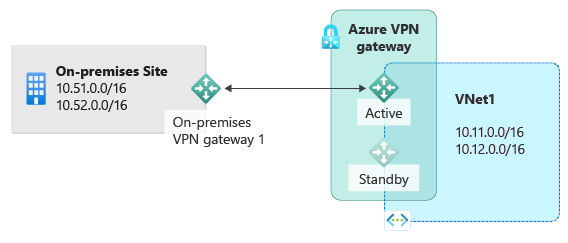
高可用性跨界
若要为跨界连接提供更高的可用性,可以使用以下选项:
- 多个本地 VPN 设备
- 主动-主动 Azure VPN 网关
- 两者的组合
多个本地 VPN 设备
可以使用本地网络中的多个 VPN 设备连接到 Azure VPN 网关,如下图所示:
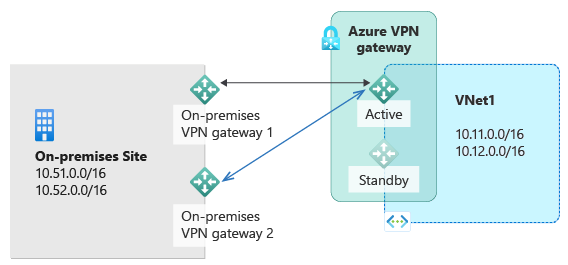
此配置提供多个活动隧道用于从同一个 Azure VPN 网关连接到同一位置中的本地设备。 在此配置中,Azure VPN 网关仍处于主动-等待模式,因此仍会发生相同的故障转移行为和短暂中断。 但是,此设置可针对本地网络和 VPN 设备故障或中断提供保护。
此配置有一些要求和限制:
- 需要创建从 VPN 设备到 Azure 的多个 S2S VPN 连接。 将多个 VPN 设备从同一本地网络连接到 Azure 时,请为每个 VPN 设备创建一个本地网关,以及一个从 Azure VPN 网关到每个本地网关的连接。
- 对应于 VPN 设备的本地网络网关在“GatewayIpAddress”属性中必须有唯一的公共 IP 地址。
- 此配置需要 BGP。 必须在“BgpPeerIpAddress”属性中为代表 VPN 设备的每个本地网络网关指定唯一的 BGP 对等 IP 地址。
- 使用 BGP 将相同本地网络前缀的相同前缀播发到 Azure VPN 网关。 流量会同时通过这些隧道转发。
- 必须使用等价多路径路由 (ECMP)。
- 每个连接将计入 Azure VPN 网关的隧道数目上限。 有关隧道、连接和吞吐量的最新信息,请参阅 VPN 网关设置页。
主动-主动 VPN 网关
可以采用主动-主动模式配置创建 Azure VPN 网关。 在主动-主动模式中,两个网关 VM 的实例与本地 VPN 设备建立 S2S VPN 隧道,如下图所示:
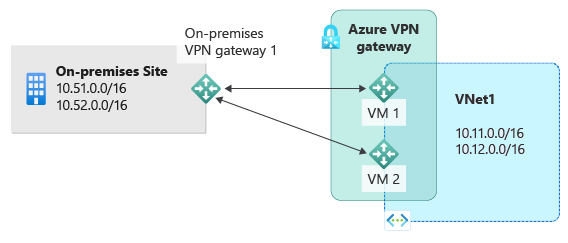
在此配置中,每个 Azure 网关实例都有唯一公共 IP 地址,每个实例会与本地网络网关和连接中指定的本地 VPN 设备建立 IPsec/IKE S2S VPN 隧道。 这两个 VPN 隧道实际上都是同一连接的一部分。 仍然需要配置本地 VPN 设备,以便与这两个 Azure VPN 网关公共 IP 地址建立两条 S2S VPN 隧道,或者接受这种通道。
由于 Azure 网关实例采用主动-主动配置,因此即使本地 VPN 设备可能倾向于其中一个隧道,从 Azure 虚拟网络到本地网络的流量会同时通过两个隧道进行路由。 对于单个 TCP 或 UDP 流,Azure 在将数据包发送到本地网络时会尝试使用同一隧道。 但是,本地网络可以使用其他隧道将数据包发送到 Azure。
当一个网关实例发生计划内维护或计划外事件时,从该实例到本地 VPN 设备的 IPsec 隧道会断开。 VPN 设备上的对应路由应会自动移除或撤消,以便将流量切换到其他主动 IPsec 隧道。 在 Azure 端,会自动从受影响的实例切换到主动实例。
双重冗余:Azure 和本地网络的主动-主动 VPN 网关
最可靠的选项是结合网络和 Azure 上的主动-主动网关,如下图所示。
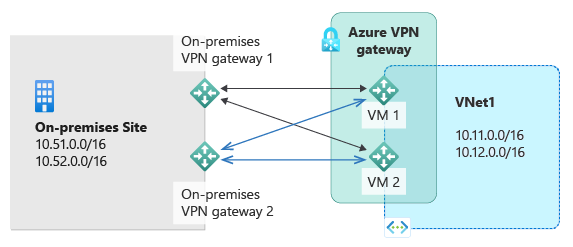
在这种类型的配置中,请采用主动-主动配置设置 Azure VPN 网关。 为两个本地 VPN 设备创建两个本地网络网关和两个连接。 结果是在 Azure 虚拟网络与本地网络之间建立了包含 4 个 IPsec 隧道的全面网格连接。
所有网关和隧道从 Azure 端激活,因此流量同时分配在 4 个隧道之间,每个 TCP 或 UDP 流量沿着源自 Azure 端的相同隧道或路径传送。 通过分配流量,你可能会在 IPsec 隧道中看到稍好吞吐量。 然而,此配置的主要目标是高可用性。 由于流量分配的统计性质,难以通过某种测量方式来确定不同的应用程序流量状况可能如何影响聚合吞吐量。
此拓扑需要使用两个本地网络网关和两个连接来支持本地 VPN 设备对,需要使用 BGP 来同时连接到同一本地网络的两个连接。 这些要求与多个本地 VPN 设备应用场景相同。
高可用性 VNet 到 VNet
上述主动-主动配置同样适用于 Azure VNet 到 VNet 连接。 可为每个虚拟网络创建主动-主动 VPN 网关,然后将它们连接到一起,从而在两个 VNet 之间构成包含 4 个隧道的相同全面网格连接。 下图显示了此特点:
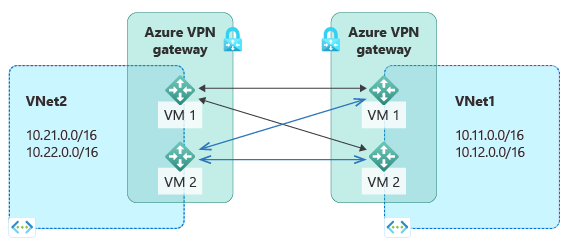
这种类型的配置确保用于任何计划内维护事件的两个虚拟网络之间始终有一对隧道,进一步提高可用性。 尽管用于跨界连接的相同拓扑需要两个连接,但此示例中的 VNet 到 VNet 拓扑只需要为每个网关建立一个连接。 除非基于 VNet 到 VNet 连接的传输路由是必需的,否则 BGP 是可选的。
后续步骤
使用 Azure 门户或 PowerShell 来配置主动-主动 VPN 网关。