使用证书身份验证(经典)配置点到站点连接
本文介绍如何使用经典(旧的)部署模型通过点到站点连接来创建 VNet。 此配置使用证书(不管是自签名的还是 CA 颁发的)来验证正在进行连接的客户端。 这些说明适用于经典部署模型。 你无法再使用经典部署模型创建网关。 请改为参阅此文的资源管理器版本。
重要
你无法再为经典部署模型(服务管理)虚拟网络创建新的虚拟网络网关。 只能为资源管理器虚拟网络创建新的虚拟网络网关。
使用点到站点链接 (P2S) VPN 网关创建从单个客户端计算机到虚拟网络的安全连接。 要从远程位置连接到 VNet,可使用点到站点 VPN 连接。 如果只有一些客户端需要连接到 VNet,则可使用 P2S VPN 这种解决方案来代替站点到站点 VPN。 可通过从客户端计算机启动连接来建立 P2S VPN 连接。
重要
经典部署模型仅支持 Windows VPN 客户端,并使用安全套接字隧道协议 (SSTP),一种基于 SSL 的 VPN 协议。 为了支持非 Windows VPN 客户端,必须使用资源管理器部署模型创建 VNet。 除了 SSTP,资源管理器部署模型还支持 IKEv2 VPN。 有关详细信息,请参阅关于 P2S 连接。
注意
本文为经典(旧的)部署模型而写。 建议你改用最新的 Azure 部署模型。 资源管理器部署模型是最新的部署模型,提供比经典部署模型更多的选项和更强的功能兼容性。 请参阅了解部署模型和资源状态,了解这两种部署模型之间的差异。
如果要使用本文提到的其他版本,请使用左侧窗格中的目录。
设置和要求
要求
点到站点证书身份验证连接需要以下项。 本文中提供了可帮助你创建它们的步骤。
- 动态 VPN 网关。
- 适用于根证书的公钥(.cer 文件),已上传到 Azure。 此公钥被视为可信证书,用于身份验证。
- 从根证书生成的客户端证书,安装在每个要连接的客户端计算机上。 此证书用于客户端身份验证。
- 必须生成 VPN 客户端配置包,并将其安装在每个进行连接的客户端计算机上。 客户端配置包配置本机 VPN 客户端,该客户端已经位于操作系统中,且具有连接到 VNet 所需的信息。
点到站点连接不需要 VPN 设备或面向公众的本地 IP 地址。 VPN 连接基于 SSTP(安全套接字隧道协议)创建。 在服务器端,我们支持 SSTP 1.0、1.1 和 1.2 版。 客户端决定要使用的版本。 对于 Windows 8.1 及更高版本,SSTP 默认使用 1.2。
示例设置
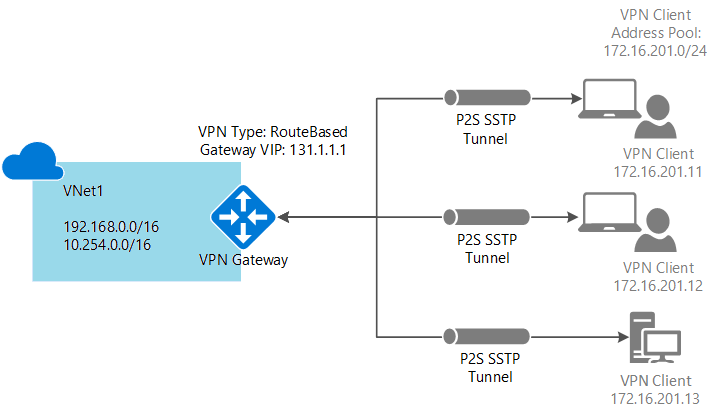
使用以下值创建测试环境,或参考这些值以更好地理解本文中的示例:
- 资源组: TestRG
- VNet 名称: VNet1
- 地址空间:192.168.0.0/16
对于此示例,我们只使用一个地址空间。 VNet 可以有多个地址空间。 - 子网名称: FrontEnd
- 子网地址范围: 192.168.1.0/24
- GatewaySubnet:192.168.200.0/24
- 区域: 中国北部
- 客户端地址空间:172.16.201.0/24
使用此点到站点连接连接到 VNet 的 VPN 客户端接收来自指定池的 IP 地址。 - 连接类型:选择“点到站点”。
开始之前,请确保拥有 Azure 订阅。 如果还没有 Azure 订阅,可以注册一个试用帐户。
创建虚拟网络
如果已有一个 VNet,请验证这些设置是否与 VPN 网关设计兼容。 请特别注意任何可能与其他网络重叠的子网。
- 从浏览器导航到 Azure 门户,并在必要时用 Azure 帐户登录。
- 选择“+创建资源”。 在“在市场中搜索”字段中,键入“虚拟网络”。 从返回的列表中找到“虚拟网络”,选择它以打开“虚拟网络”页。
- 在“虚拟网络”页的“创建”按钮下,可以看到“使用资源管理器部署(更改为经典)”。 “资源管理器”是创建 VNet 的默认设置。 不需要创建资源管理器 VNet。 选择“(更改为经典)”以创建经典 VNet。 然后,选择“概述”选项卡并选择“创建”。
- 在“创建虚拟网络(经典)”页的“基本信息”选项卡上,使用示例值配置 VNet 设置。
- 选择“查看 + 创建”以验证自己的 VNet。
- 此时验证将运行。 验证 VNet 后,选择“创建”。
在此配置过程中不需进行 DNS 设置,但如果希望在 VM 之间进行名称解析,则 DNS 是必需的。 指定一个值不会创建新的 DNS 服务器。 指定的 DNS 服务器 IP 地址应该是可以解析所连接的资源名称的 DNS 服务器。
创建虚拟网络后,可以添加 DNS 服务器的 IP 地址来处理名称解析。 打开虚拟网络的设置,选择“DNS 服务器”,并添加要用于名称解析的 DNS 服务器的 IP 地址。
- 在门户中找到虚拟网络。
- 在虚拟网络页的“设置”部分,选择“DNS 服务器”。
- 添加 DNS 服务器。
- 若要保存设置,请选择页面顶部的“保存”。
创建 VPN 网关
导航到你创建的 VNet。
在 VNet 页面的“设置”下选择“网关”。 在“网关”页面上,你可以查看虚拟网络的网关。 此虚拟网络尚无网关。 单击注释“单击此处以添加连接和网关”。
在“配置 VPN 连接和网关”页上,选择以下设置:
- 连接类型:点到站点
- 客户端地址空间:添加 VPN 客户端在连接时要从中接收 IP 地址的 IP 地址范围。 使用专用 IP 地址范围时,该范围不得与要通过其进行连接的本地位置重叠,也不得与连接到其中的 VNet 重叠。
让“此时不配置网关”复选框保留未选中状态。 我们将创建一个网关。
在页面底部选择“下一步: 网关 >”。
在“网关”选项卡上,选择以下值:
- Size: 大小为虚拟网关的网关 SKU。 在 Azure 门户中,默认 SKU 为“默认”。 有关网关 SKU 的详细信息,请参阅关于 VPN 网关设置。
- 路由类型: 对于点到站点配置,必须选择“动态”。 静态路由不起作用。
- 网关子网: 此字段已自动填充。 无法更改该名称。 如果你尝试使用 PowerShell 或任何其他方式更改名称,则网关将无法正常工作。
- 地址范围(CIDR 块):尽管创建的网关子网最小可为 /29,但建议至少选择 /28 或 /27,创建包含更多地址的更大子网。 这样便可以留出足够多的地址,满足将来可能需要使用的其他配置。 处理网关子网时,请避免将网络安全组 (NSG) 关联到网关子网。 将网络安全组与此子网关联可能会导致 VPN 网关不再按预期方式工作。
选择“查看 + 创建”以验证自己的设置 。
通过验证后,选择“创建”。 VPN 网关可能需要长达 45 分钟的时间才能完成,具体取决于所选网关 SKU。
创建证书
Azure 使用证书对点到站点 VPN 的 VPN 客户端进行身份验证。 请将根证书的公钥信息上传到 Azure, 然后即可将该公钥视为“可信”公钥。 必须根据可信根证书生成客户端证书,并将其安装在每个客户端计算机的 Certificates-Current User\Personal\Certificates 证书存储中。 客户端连接到 VNet 时,使用证书进行身份验证。
如果使用自签名证书,这些证书必须使用特定的参数创建。 可以按照适用于 PowerShell 和 Windows 10 或更高版本或 MakeCert 的说明,创建自签名证书。 在使用自签名根证书以及从自签名根证书生成客户端证书时,必须按这些说明中的步骤操作,这一点很重要。 否则,创建的证书将与 P2S 连接不兼容,你将收到“连接错误”。
获取根证书的公钥 (.cer)
获取根证书的 .cer 文件。 你可以使用通过企业解决方案生成的根证书(推荐),或者生成自签名证书。 创建根证书后,将公共证书数据(不是私钥)作为 Base64 编码的 X.509 .cer 文件导出。 稍后,请将此文件上传到 Azure。
企业证书: 如果使用的是企业级解决方案,可以使用现有的证书链。 获取要使用的根证书的 .cer 文件。
自签名根证书: 如果使用的不是企业证书解决方案,请创建自签名根证书。 否则,创建的证书将不兼容 P2S 连接,客户端会在尝试进行连接时收到连接错误。 可以使用 Azure PowerShell、MakeCert 或 OpenSSL。 以下文章中的步骤介绍了如何生成兼容的自签名根证书:
- 适用于 Windows 10 或更高版本的 PowerShell 说明:这些说明要求运行 Windows 10 或更高版本的计算机上具有 PowerShell。 从根证书生成的客户端证书可以安装在任何受支持的 P2S 客户端上。
- MakeCert 说明:如果无法访问运行 Windows 10 或更高版本的计算机,则可使用 MakeCert 生成证书。 虽然 MakeCert 已弃用,但仍可使用它来生成证书。 从根证书生成的客户端证书可以安装在任何受支持的 P2S 客户端上。
- Linux - OpenSSL 说明
- Linux - strongSwan 说明
生成客户端证书
在使用点到站点连接连接到 VNet 的每台客户端计算机上,必须安装客户端证书。 请从根证书生成它,然后将它安装在每个客户端计算机上。 如果未安装有效的客户端证书,则当客户端尝试连接到 VNet 时,身份验证会失败。
可以为每个客户端生成唯一证书,也可以对多个客户端使用同一证书。 生成唯一客户端证书的优势是能够吊销单个证书。 否则,如果多个客户端使用相同的客户端证书进行身份验证而你将其撤销,则需为所有使用该证书的客户端生成并安装新证书。
可以通过以下方法生成客户端证书:
企业证书:
如果使用的是企业证书解决方案,请使用通用名称值格式 name@yourdomain.com 生成客户端证书, 而不要使用“域名\用户名”格式。
请确保客户端证书基于“用户”证书模板,该模板将“客户端身份验证”列为用户列表中的第一项。 检查证书的方式是:双击证书,然后在“详细信息”选项卡中查看“增强型密钥用法” 。
自签名根证书: 按照下述某篇 P2S 证书文章中的步骤操作,使创建的客户端证书兼容 P2S 连接。
从自签名根证书生成客户端证书时,该证书会自动安装在用于生成该证书的计算机上。 如果想要在另一台客户端计算机上安装客户端证书,请以 .pfx 文件格式导出该证书以及整个证书链。 这样做会创建一个 .pfx 文件,其中包含的根证书信息是客户端进行身份验证所必需的。
这些文章中的步骤可生成兼容的客户端证书,然后你可以导出和分发该证书。
适用于 Windows 10 或更高版本 PowerShell 的说明:按照这些说明进行操作时,需要使用 Windows 10(或更高版本)和 PowerShell 来生成证书。 生成的证书可以安装在任何受支持的 P2S 客户端上。
适用于 MakeCert 的说明:如果无权访问用于生成证书的 Windows 10 或更高版本计算机,则可使用 MakeCert。 虽然 MakeCert 已弃用,但仍可使用它来生成证书。 可以将生成的证书安装在任何受支持的 P2S 客户端上。
Linux:请参阅 strongSwan 或 OpenSSL 指令。
上传根证书 .cer 文件
创建网关之后,将可信根证书的 .cer 文件(包含公钥信息)上传到 Azure 服务器。 请勿上传根证书私钥。 上传证书后,Azure 使用该证书对已安装客户端证书(根据可信根证书生成)的客户端进行身份验证。 之后可根据需要上传更多可信根证书文件(最多 20 个)。
- 导航到你创建的虚拟网络。
- 在“设置”下,选择“点到站点连接”。
- 选择“管理证书”。
- 选择“上传”。
- 在“上传证书”窗格中,选择文件夹图标,然后导航到要上传的证书。
- 选择“上传”。
- 成功上传证书后,可以在“管理证书”页上查看该证书。 你可能需要选择“刷新”才能查看刚才上传的证书。
配置客户端
要通过点到站点 VPN 连接到 VNet,每个客户端都必须安装一个用于配置本机 Windows VPN 客户端的包。 配置包使用连接到虚拟网络所需的设置配置本机 Windows VPN 客户端。
只要版本与客户端的体系结构匹配,就可以在每台客户端计算机上使用相同的 VPN 客户端配置包。 有关支持的客户端操作系统的列表,请参阅关于点到站点连接和常见问题解答。
生成和安装 VPN 客户端配置包
导航到你的 VNet 的“点到站点连接”设置。
在页面顶部,选择与要在其中进行安装的客户端操作系统对应的下载包:
- 对于 64 位客户端,请选择“VPN 客户端(64 位)”。
- 对于 32 位客户端,请选择“VPN 客户端(32 位)”。
Azure 会使用客户端需要的特定设置来生成包。 每次对 VNet 或网关进行更改时,你都需要下载新的客户端配置包,并将其安装在客户端计算机上。
包生成后,选择“下载”。
在客户端计算机上安装客户端配置包。 在安装时,如果看到一个 SmartScreen 弹出窗口,指出 Windows 保护了你的电脑,请选择“详细信息”,然后选择“仍要运行”。 也可将要安装的包保存在其他客户端计算机上。
安装客户端证书
在此练习中,它已在你生成客户端证书时自动安装在你的计算机上。 若要从另一台客户端计算机(而不是用于生成客户端证书的计算机)创建 P2S 连接,必须将生成的客户端证书安装在该计算机上。
安装客户端证书时,需要使用导出客户端证书时创建的密码。 通常,只需双击证书即可安装。 有关详细信息,请参阅安装已导出的客户端证书。
连接到 VNet
注意
在要从其进行连接的客户端计算机上,你必须拥有管理员权限。
- 在客户端计算机上,转到 VPN 设置。
- 选择你创建的 VPN。 如果你使用了示例设置,则连接会被标记为“Group TestRG VNet1”。
- 选择“连接”。
- 在“Windows Azure 虚拟网络”框中,选择“连接”。 如果显示了关于证书的弹出消息,请选择“继续”以使用提升的权限,并选择“是”以接受配置更改 。
- 当连接成功时,你会看到“已连接”通知。
如果在连接时遇到问题,请检查以下项:
如果你已通过证书导出向导导出客户端证书,请确保已将其导出为 .pfx 文件并选中了“包括证书路径中的所有证书(如果可能)”。 使用此值将其导出时,也会导出根证书信息。 在客户端计算机上安装证书后,还会安装 .pfx 文件中的根证书。 若要验证是否安装了根证书,请打开“管理用户证书”,然后选择“受信任的根证书颁发机构\证书”。 验证是否列出了根证书,必须存在根证书才能进行身份验证。
如果使用的是由企业 CA 解决方案颁发的证书,并且无法进行身份验证,请在客户端证书上验证身份验证顺序。 通过双击客户端证书,选择“详细信息”选项卡并选择“增强型密钥用法”来检查身份验证列表顺序。 确保此列表中的第一项是“客户端身份验证”。 如果不是,请基于将“客户端身份验证”作为列表中第一项的用户模板颁发客户端证书。
如需更多的 P2S 故障排除信息,请参阅排查 P2S 连接问题。
验证 VPN 连接
验证 VPN 连接是否激活。 在客户端计算机上打开提升的命令提示符,并运行 ipconfig/all。
查看结果。 请注意,收到的 IP 地址是点到站点连接地址范围中的一个地址,该范围是你在创建 VNet 时指定的。 结果应类似于以下示例:
PPP adapter VNet1: Connection-specific DNS Suffix .: Description.....................: VNet1 Physical Address................: DHCP Enabled....................: No Autoconfiguration Enabled.......: Yes IPv4 Address....................: 172.16.201.11 (Preferred) Subnet Mask.....................: 255.255.255.255 Default Gateway.................: NetBIOS over Tcpip..............: Enabled
连接到虚拟机
创建远程桌面连接来连接到部署到 VNet 的 VM。 若要验证是否能够连接到 VM,最好的方式是使用其专用 IP 地址而不是计算机名称进行连接。 这种方式测试的是能否进行连接,而不是测试名称解析是否已正确配置。
- 定位 VM 的专用 IP 地址。 若要查找 VM 的专用 IP 地址,可以在 Azure 门户中或使用 PowerShell 查看 VM 的属性。
- 验证你是否已使用点到站点 VPN 连接连接到 VNet。
- 若要打开远程桌面连接,请在任务栏上的搜索框中键入 RDP 或远程桌面连接,然后选择“远程桌面连接”。 也可以在 PowerShell 中使用 mstsc 命令打开远程桌面连接。
- 在“远程桌面连接”中,输入 VM 的专用 IP 地址。 如果需要,选择“显示选项”来调整其他设置,然后进行连接。
排查到 VM 的 RDP 连接的问题
如果无法通过 VPN 连接连接到虚拟机,可以查看一些项目。
- 验证 VPN 连接是否成功。
- 验证是否已连接到 VM 的专用 IP 地址。
- 输入 ipconfig 来检查分配给以太网适配器的 IPv4 地址,该适配器所在的计算机正是你要从其进行连接的计算机。 如果该 IP 地址位于要连接到的 VNet 的地址范围内,或者位于 VPNClientAddressPool 的地址范围内,则会出现重叠的地址空间。 当地址空间以这种方式重叠时,网络流量不会抵达 Azure,而是呆在本地网络中。
- 如果可以使用专用 IP 地址连接到 VM,但不能使用计算机名称进行连接,则请验证是否已正确配置 DNS。 若要详细了解如何对 VM 进行名称解析,请参阅针对 VM 的名称解析。
- 为 VNet 指定 DNS 服务器 IP 地址之后,验证是否生成了 VPN 客户端配置包。 如果更新了 DNS 服务器 IP 地址,请生成并安装新的 VPN 客户端配置包。
如需更多故障排除信息,请参阅排查到 VM 的远程桌面连接问题。
添加或删除受信任的根证书
可以在 Azure 中添加和删除受信任的根证书。 删除根证书时,具有从该根生成的证书的客户端不能再进行身份验证和连接。 为了让这些客户端再次进行身份验证并连接,必须安装新的客户端证书,该证书由 Azure 信任的根证书生成。
添加受信任的根证书
你可以使用添加第一个受信任的根证书时所用的过程,将最多 20 个受信任的根证书 .cer 文件添加到 Azure。
删除受信任的根证书
- 在 VNet 页的“点到站点连接”部分中,选择“管理证书”。
- 选择要删除的证书旁边的省略号,然后选择“删除”。
吊销客户端证书
如有必要,可以吊销客户端证书。 证书吊销列表用于选择性地拒绝基于单个客户端证书的点到站点连接。 此方法不同于删除可信根证书。 如果从 Azure 中删除受信任的根证书 .cer,它会吊销由吊销的根证书生成/签名的所有客户端证书的访问权限。 如果吊销客户端证书而非根证书,则可继续使用从根证书生成的其他证书,以便进行点到站点连接所需的身份验证。
常见的做法是使用根证书管理团队或组织级别的访问权限,并使用吊销的客户端证书针对单个用户进行精细的访问控制。
可以通过将指纹添加到吊销列表来吊销客户端证书。
- 检索客户端证书指纹。 有关详细信息,请参阅如何:检索证书的指纹。
- 将信息复制到文本编辑器,删除其中的空格,使之成为连续的字符串。
- 导航到“点到站点 VPN 连接”,然后选择“管理证书”。
- 选择“吊销列表”,打开“吊销列表”页。
- 在“指纹”页中,将证书指纹以连续文本行的形式进行粘贴,不留空格。
- 选择“+ 添加到列表”,将指纹添加到证书吊销列表 (CRL)。
更新完成后,不再可以使用证书来进行连接。 客户端在尝试使用此证书进行连接时,会收到一条消息,指出证书不再有效。
FAQ
此常见问题解答适用于使用经典部署模型的 P2S 连接。
点到站点连接可用于哪些客户端操作系统?
支持以下客户端操作系统:
- Windows 7(32 位和 64 位)
- Windows Server 2008 R2(仅 64 位)
- Windows 8(32 位和 64 位)
- Windows 8.1(32 位和 64 位)
- Windows Server 2012(仅 64 位)
- Windows Server 2012 R2(仅 64 位)
- Windows 10
- Windows 11
是否可以使用支持将 SSTP 用于点到站点连接的任何软件 VPN 客户端?
否。 仅支持所列出的 Windows 操作系统版本。
在我的点到站点配置中,可以存在多少 VPN 客户端终结点?
VPN 客户端终结点的数量取决于网关 SKU 和协议。
| VPN 网关 代系 |
SKU | S2S/VNet 到 VNet 隧道 |
P2S SSTP 连接 |
P2S IKEv2/OpenVPN 连接 |
聚合 吞吐量基准 |
BGP | 区域冗余 | 虚拟网络中支持的 VM 数 |
|---|---|---|---|---|---|---|---|---|
| 第 1 代 | 基本 | 最大 10 | 最大 128 | 不支持 | 100 Mbps | 不支持 | 否 | 200 |
| 第 1 代 | VpnGw1 | 最大 30 | 最大 128 | 最大 250 | 650 Mbps | 支持 | 否 | 450 |
| 第 1 代 | VpnGw2 | 最大 30 | 最大 128 | 最大 500 | 1 Gbps | 支持 | 否 | 1300 |
| 第 1 代 | VpnGw3 | 最大 30 | 最大 128 | 最大 1000 | 1.25 Gbps | 支持 | 否 | 4000 |
| 第 1 代 | VpnGw1AZ | 最大 30 | 最大 128 | 最大 250 | 650 Mbps | 支持 | 是 | 1000 |
| 第 1 代 | VpnGw2AZ | 最大 30 | 最大 128 | 最大 500 | 1 Gbps | 支持 | 是 | 2000 |
| 第 1 代 | VpnGw3AZ | 最大 30 | 最大 128 | 最大 1000 | 1.25 Gbps | 支持 | 是 | 5000 |
| 第 2 代 | VpnGw2 | 最大 30 | 最大 128 | 最大 500 | 1.25 Gbps | 支持 | 否 | 685 |
| 第 2 代 | VpnGw3 | 最大 30 | 最大 128 | 最大 1000 | 2.5 Gbps | 支持 | 否 | 2240 |
| 第 2 代 | VpnGw4 | 最大 100* | 最大 128 | 最大 5000 | 5 Gbps | 支持 | 否 | 5300 |
| 第 2 代 | VpnGw5 | 最大 100* | 最大 128 | 最大 10000 | 10 Gbps | 支持 | 否 | 6700 |
| 第 2 代 | VpnGw2AZ | 最大 30 | 最大 128 | 最大 500 | 1.25 Gbps | 支持 | 是 | 2000 |
| 第 2 代 | VpnGw3AZ | 最大 30 | 最大 128 | 最大 1000 | 2.5 Gbps | 支持 | 是 | 3300 |
| 第 2 代 | VpnGw4AZ | 最大 100* | 最大 128 | 最大 5000 | 5 Gbps | 支持 | 是 | 4400 |
| 第 2 代 | VpnGw5AZ | 最大 100* | 最大 128 | 最大 10000 | 10 Gbps | 支持 | 是 | 9000 |
能否将我自己的 PKI 根 CA 用于点到站点连接?
是的。 以前只可使用自签名根证书。 现在还可以上传最多 20 个根证书。
是否可以使用点到站点连接穿越代理和防火墙?
是的。 我们使用安全套接字隧道协议 (SSTP) 作为隧道来穿越防火墙。 此隧道显示为 HTTPS 连接。
如果重新启动进行过点到站点配置的客户端计算机,是否会自动重新连接 VPN?
默认情况下,客户端计算机将不会自动重新建立 VPN 连接。
点到站点 VPN 客户端上是否支持自动重新连接和 DDNS?
否。 点到站点 VPN 中当前不支持自动重新连接和 DDNS。
同一虚拟网络中是否可以同时存在站点到站点和点到站点配置?
是的。 如果网关使用 RouteBased VPN 类型,这两种解决方案都可行。 对于经典部署模型,需要一个动态网关。 我们不支持将点到站点连接用于静态路由 VPN 网关,也不支持将其用于使用 -VpnType PolicyBased cmdlet 的网关。
能否配置点到站点客户端,使其同时连接到多个虚拟网络?
是的。 但是,虚拟网络的 IP 前缀不得重叠,并且点到站点地址空间在虚拟网络之间不得重叠。
使用站点到站点连接或点到站点连接时,预计吞吐量为多少?
很难维持 VPN 隧道的准确吞吐量。 IPsec 和 SSTP 是重重加密的 VPN 协议。 本地网络与 Internet 之间的延迟和带宽也限制了吞吐量。
后续步骤
连接完成后,即可将虚拟机添加到虚拟网络。 有关详细信息,请参阅虚拟机。
要详细了解网络和 Linux 虚拟机,请参阅 Azure 和 Linux VM 网络概述。
有关 P2S 故障排除信息,请参阅排查 Azure 点到站点连接问题。