Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
Before you begin, use the Choose a policy type selector at the top of this page to choose the type of policy you’re setting up. Azure Active Directory B2C offers two methods to define how users interact with your applications: through predefined user flows or through fully configurable custom policies. The steps required in this article are different for each method.
When you set up sign-in for your application using Azure Active Directory B2C (Azure AD B2C), you can prepopulate the sign-in name or directly sign in to a specific social identity provider.
Prepopulate the sign in name
During a sign-in user journey, a relying party application may target a specific user or domain name. When targeting a user, an application can specify, in the authorization request, the login_hint query parameter with the user sign-in name. Azure AD B2C automatically populates the sign-in name, while the user only needs to provide the password.
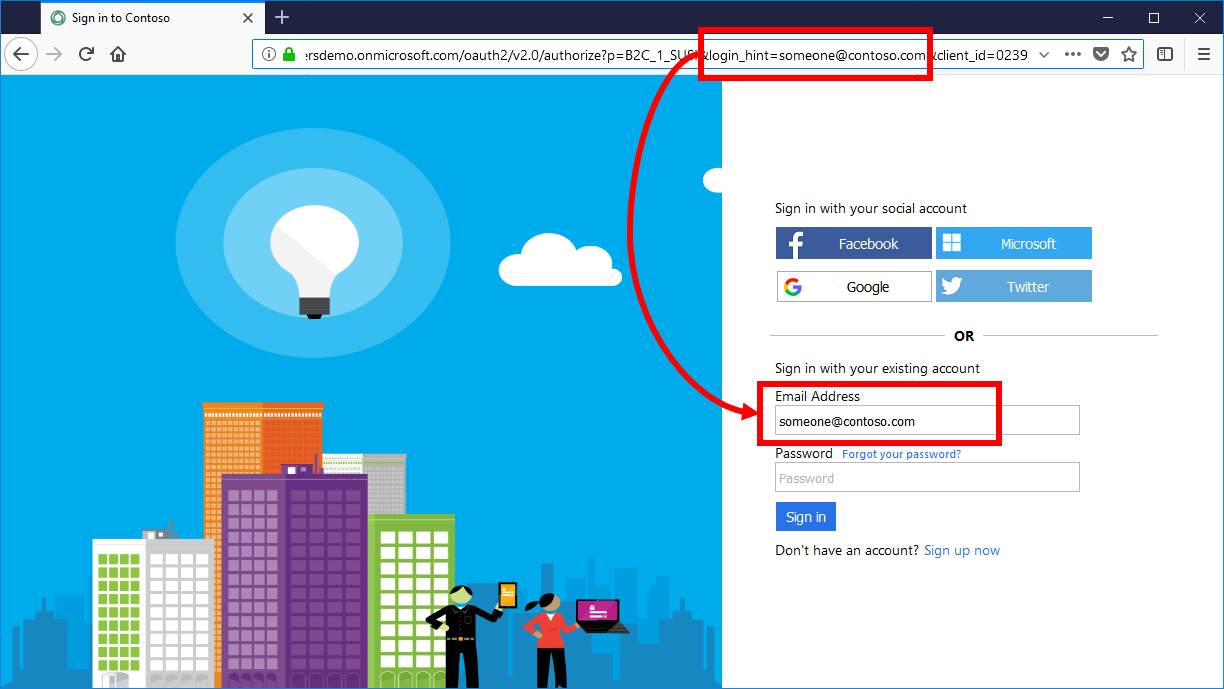
The user is able to change the value in the sign-in textbox.
To support sign in hint parameter, override the SelfAsserted-LocalAccountSignin-Email technical profile. In the <InputClaims> section, set the DefaultValue of the signInName claim to {OIDC:LoginHint}. The {OIDC:LoginHint} variable contains the value of the login_hint parameter. Azure AD B2C reads the value of the signInName claim and pre-populates the signInName textbox.
<ClaimsProvider>
<DisplayName>Local Account</DisplayName>
<TechnicalProfiles>
<TechnicalProfile Id="SelfAsserted-LocalAccountSignin-Email">
<InputClaims>
<!-- Add the login hint value to the sign-in names claim type -->
<InputClaim ClaimTypeReferenceId="signInName" DefaultValue="{OIDC:LoginHint}" />
</InputClaims>
</TechnicalProfile>
</TechnicalProfiles>
</ClaimsProvider>
Redirect sign in to a social provider
If you configured the sign-in journey for your application to include social accounts, you can specify the domain_hint parameter. This query parameter provides a hint to Azure AD B2C about the social identity provider that should be used for sign-in.
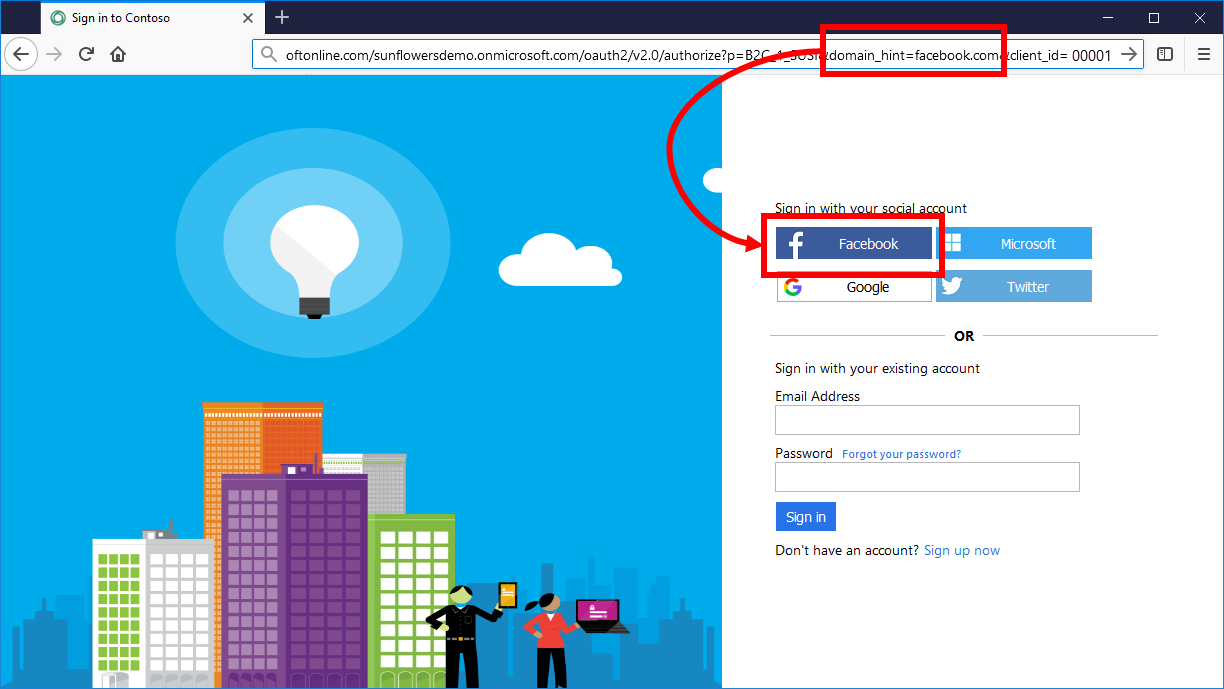
The domain hint query string parameter can set to one of the following domains:
- github.com
- microsoft.com
- qq.com
- wechat.com
- weibo.com
- For Generic OpenID Connect, see Domain hint.
To support domain hint parameter, you can configure the domain name using the <Domain>domain name</Domain> XML element of any <ClaimsProvider>.
<ClaimsProvider>
<!-- Add the domain hint value to the claims provider -->
<Domain>wechat.com</Domain>
<DisplayName>Wechat</DisplayName>
<TechnicalProfiles>
...