Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
This page answers frequently asked questions about the Azure Active Directory B2C (Azure AD B2C). Keep checking back for updates.
Azure AD B2C end of sale
Effective May 1, 2025 Azure AD B2C will no longer be available to purchase for new customers, but current Azure AD B2C customers can continue using the product. The product experience, including creating new tenants or user flows, will remain unchanged; however, new tenants can only be created with Azure AD B2C P1. Azure AD B2C P2 will be discontinued on March 15, 2026, for all customers. The operational commitments, including service level agreements (SLAs), security updates, and compliance, will also remain unchanged. We'll continue supporting Azure AD B2C until at least May 2030. More information, including migration plans will be made available. Contact your account representative for more information and to learn more about Microsoft Entra External ID.
What is Microsoft Entra External ID?
We have released our next generation Microsoft Entra External ID product which combines powerful solutions for working with people outside of your organization. With External ID capabilities, you can allow external identities to securely access your apps and resources. Whether you’re working with external partners, consumers, or business customers, users can bring their own identities. These identities can range from corporate or government-issued accounts to social identity providers. For more information, see Introduction to Microsoft Entra External ID
Why can't I access the Azure AD B2C extension in the Azure portal?
There are two common reasons for why the Microsoft Entra extension isn't working for you. Azure AD B2C requires your user role in the directory to be a Global administrator. Contact your administrator if you think you should have access. If you have Global administrator privileges, make sure that you are in an Azure AD B2C directory and not a Microsoft Entra directory. You can see instructions for creating an Azure AD B2C tenant.
Can I use Azure AD B2C features in my existing, employee-based Microsoft Entra tenant?
Microsoft Entra ID and Azure AD B2C are separate product offerings. To use Azure AD B2C features, create a separate Azure AD B2C tenant from your existing employee-based Microsoft Entra tenant. A Microsoft Entra tenant represents an organization. An Azure AD B2C tenant represents a collection of identities to be used with relying party applications. By adding New OpenID Connect provider under Azure AD B2C > Identity providers or with custom policies, Azure AD B2C can federate to Microsoft Entra ID allowing authentication of employees in an organization.
What are local accounts in Azure AD B2C? How are they different from work or school accounts in Microsoft Entra ID?
In a Microsoft Entra tenant, users that belong to the tenant sign in with an email address of the form <xyz>@<tenant domain>. The <tenant domain> is one of the verified domains in the tenant or the initial <...>.partner.onmschina.cn domain. This type of account is a work or school account.
In an Azure AD B2C tenant, most apps want the user to sign in with any arbitrary email address (for example, joe@comcast.net, bob@gmail.com, sarah@contoso.com, or jim@live.com). This type of account is a local account. We also support arbitrary user names as local accounts (for example, joe, bob, sarah, or jim). You can choose one of these two local account types when configuring identity providers for Azure AD B2C in the Azure portal. In your Azure AD B2C tenant, select Identity providers, select Local account, and then select Username.
User accounts for applications can be created through a sign-up user flow, sign-up or sign-in user flow, the Microsoft Graph API, or the Azure portal.
How many users can an Azure AD B2C tenant accommodate?
By default, each tenant can accommodate a total of 1.25 million objects (user accounts and applications), but you can increase this limit to 5.25 million objects when you add and verify a custom domain. If you want to increase this limit, please contact Microsoft Support. However, if you created your tenant before September 2022, this limit doesn't affect you, and your tenant will retain the size allocated to it at creation, that's, 50 million objects.
Which social identity providers do you support now? Which ones do you plan to support in the future?
We currently support several social identity providers including GitHub (preview), QQ (preview), WeChat (preview), and Weibo (preview). We evaluate adding support for other popular social identity providers based on customer demand.
Azure AD B2C also supports custom policies. Custom policies allow you to create your own policy for any identity provider that supports OpenID Connect or SAML. Get started with custom policies by checking out our custom policy starter pack.
I'm using ADFS as an identity provider in Azure AD B2C. When I try to initiate a sign-out request from Azure AD B2C, ADFS shows the error *MSIS7084: SAML logout request and logout response messages must be signed when using SAML HTTP Redirect or HTTP POST binding*. How do I resolve this issue?
On the ADFS server, run: Set-AdfsProperties -SignedSamlRequestsRequired $true. This will force Azure AD B2C to sign all requests to ADFS.
Does my application have to be run on Azure for it to work with Azure AD B2C?
No, you can host your application anywhere (in the cloud or on-premises). All it needs to interact with Azure AD B2C is the ability to send and receive HTTP requests on publicly accessible endpoints.
I have multiple Azure AD B2C tenants. How can I manage them on the Azure portal?
Before opening Azure AD B2C service in the Azure portal, you must switch to the directory you want to manage. Select the Settings icon in the top menu to switch to the directory you want to manage from the Directories + subscriptions menu.
Why am I unable to create an Azure AD B2C tenant?
You might not have permission to create an Azure AD B2C tenant. Only users with at least Tenant Creator roles can create the tenant.
How do I customize verification emails (the content and the "From:" field) sent by Azure AD B2C?
You can use the company branding feature to customize the content of verification emails. Specifically, these two elements of the email can be customized:
Banner logo: Shown at the bottom-right.
Background color: Shown at the top.
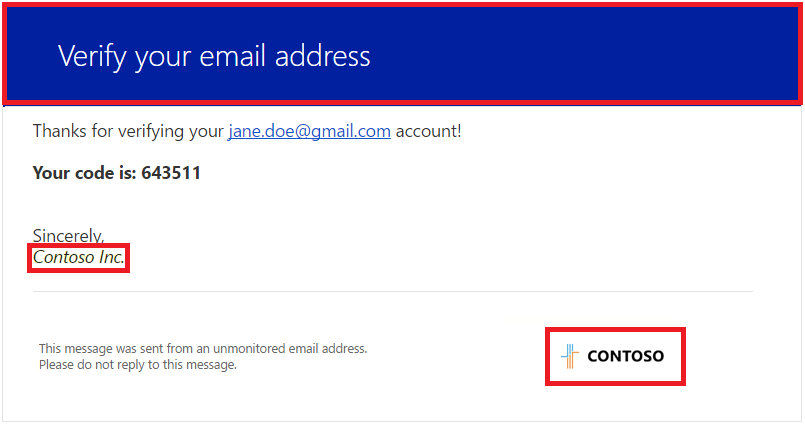
The email signature contains the Azure AD B2C tenant's name that you provided when you first created the Azure AD B2C tenant. You can change the name using these instructions:
- Sign in to the Azure portal as the Global Administrator.
- Open the Microsoft Entra ID blade.
- Select the Properties tab.
- Change the Name field.
- Select Save at the top of the page.
Currently, you can’t change the "From:" field on the email.
Tip
With Azure AD B2C custom policy, you can customize the email Azure AD B2C sends to users, including the "From:" field on the email. The custom email verification requires the use of a third-party email provider like Mailjet or SendGrid.
How can I migrate my existing user names, passwords, and profiles from my database to Azure AD B2C?
You can use the Microsoft Graph API to write your migration tool. See the User migration guide for details.
What password user flow is used for local accounts in Azure AD B2C?
The Azure AD B2C password user flow for local accounts is based on the policy for Microsoft Entra ID. Azure AD B2C's sign-up, sign-up or sign-in and password reset user flows use the "strong" password strength and don't expire any passwords. For more information, see Password policies and restrictions in Microsoft Entra ID.
Can I use Microsoft Entra Connect to migrate consumer identities that are stored on my on-premises Active Directory to Azure AD B2C?
No, Microsoft Entra Connect isn't designed to work with Azure AD B2C. Consider using the Microsoft Graph API for user migration. See the User migration guide for details.
Does Azure AD B2C work with CRM systems such as Microsoft Dynamics?
Integration with Microsoft Dynamics 365 Portal is available. See Configuring Dynamics 365 Portal to use Azure AD B2C for authentication.
Does Azure AD B2C work with SharePoint on-premises 2016 or earlier?
Azure AD B2C isn't meant for the SharePoint external partner-sharing scenario; see Microsoft Entra B2B instead.
Should I use Azure AD B2C or B2B to manage external identities?
Read Compare solutions for External Identities to learn more about applying the appropriate features to your external identity scenarios.
What reporting and auditing features does Azure AD B2C provide? Are they the same as in Microsoft Entra ID P1 or P2?
No, Azure AD B2C doesn't support the same set of reports as Microsoft Entra ID P1 or P2. However, there are many commonalities:
- Sign-in reports provide a record of each sign-in with reduced details.
- Audit reports include both admin activity and application activity.
- Usage reports include the number of users, number of logins, and volume of MFA.
Why does my Azure AD B2C bill show phone charges named "Microsoft Entra External ID?"
Following the new billing model for Azure AD External Identities SMS Phone Authentication, you may notice a new name on your bill. Previously, Phone MFA was billed as "Azure Active Directory B2C - Basic 1 Multi-Factor Authentication." Now you’ll see the following names based on your country or region pricing tier:
- Microsoft Entra External ID - Phone Authentication Low Cost 1 Transaction
- Microsoft Entra External ID - Phone Authentication Mid Low Cost 1 Transaction
- Microsoft Entra External ID - Phone Authentication Mid High Cost 1 Transaction
- Microsoft Entra External ID - Phone Authentication High Cost 1 Transaction
Although the new bill mentions Microsoft Entra External ID, you’re still billed for Azure AD B2C based on your core MAU count.
Can I localize the UI of pages served by Azure AD B2C? What languages are supported?
Yes, see language customization. We provide translations for 36 languages, and you can override any string to suit your needs.
How do I delete my Azure AD B2C tenant?
Follow these steps to delete your Azure AD B2C tenant.
You can use our new unified App registrations experience or our legacy Applications (Legacy) experience. Learn more about the new experience.
- Sign in to the Azure portal as the Subscription Administrator. Use the same work or school account or the same Microsoft account that you used to sign up for Azure.
- Make sure you're using the directory that contains your Azure AD B2C tenant. Select the Settings icon in the portal toolbar.
- On the Portal settings | Directories + subscriptions page, find your Azure AD B2C directory in the Directory name list, and then select Switch.
- In the left menu, select Azure AD B2C. Or, select All services and search for and select Azure AD B2C.
- Delete all User flows (policies) in your Azure AD B2C tenant.
- Delete all Identity Providers in your Azure AD B2C tenant.
- Select App registrations, then select the All applications tab.
- Delete all applications that you registered.
- Delete the b2c-extensions-app.
- Under Manage, select Users.
- Select each user in turn (exclude the Subscription Administrator user you're currently signed in as). Select Delete at the bottom of the page and select Yes when prompted.
- Select Microsoft Entra ID on the left-hand menu.
- Under Manage, select Properties
- Under Access management for Azure resources, select Yes, and then select Save.
- Sign out of the Azure portal and then sign back in to refresh your access.
- Select Microsoft Entra ID on the left-hand menu.
- On the Overview page, select Delete tenant. Follow the on-screen instructions to complete the process.
Can I get Azure AD B2C as part of the Enterprise Mobility Suite?
No, Azure AD B2C is a pay-as-you-go Azure service and isn't part of Enterprise Mobility Suite.
Can I purchase Microsoft Entra ID P1 and Microsoft Entra ID P2 licensing for my Azure AD B2C tenant?
No, Azure AD B2C tenants don't use Microsoft Entra ID P1 or Microsoft Entra ID P2 licensing. Azure AD B2C uses Premium P1 or P2 licenses, which are no longer available for purchase as of May 1, 2025. They are different from Microsoft Entra ID P1 or P2 licenses for a Standard Microsoft Entra tenant. Azure AD B2C tenants natively support some features that are similar to Microsoft Entra ID P1 or P2 features, as explained in Supported Microsoft Entra ID features.
Can I use a group-based assignment for Microsoft Entra Enterprise Applications in my Azure AD B2C tenant?
No, Azure AD B2C tenants don't support group-based assignment to Microsoft Entra Enterprise Applications.
I am using rolling refresh tokens for my application and I am getting an invalid_grant error on redeeming newly acquired refresh tokens well within their set validity period. Why does this happen?
While determining validity for rolling refresh tokens, B2C will consider the initial login time of the user in the application also to calculate the token validity skew. If the user hasn't logged out of the application for a very long time, this skew value will exceed the validity period of the token and hence for security reasons the tokens will be considered as invalid. Hence the error. Inform the user to perform a proper logout and login back into the application and this should reset the skew. This scenario is not applicable if refresh token rolling is set as infinite rolling.
I've revoked the refresh token using Microsoft Graph invalidateAllRefreshTokens, or Microsoft Graph PowerShell, Revoke-MgUserSignInSession. Why is Azure AD B2C still accepting the old refresh token?
In Azure AD B2C, if the time difference between refreshTokensValidFromDateTime and refreshTokenIssuedTime is less than or equal to 5 minutes, the refresh token is still considered valid. However, if the refreshTokenIssuedTime is greater than the refreshTokensValidFromDateTime, then the refresh token is revoked.
Follow the following steps to check if the refresh token is valid or revoked:
Retrieve the
RefreshTokenand theAccessTokenby redeemingauthorization_code.Wait for 7 minutes.
Use Microsoft Graph PowerShell cmdlet Revoke-MgUserSignInSession or Microsoft Graph API invalidateAllRefreshTokens to run the
RevokeAllRefreshTokencommand.Wait for 10 minutes.
Retrieve the
RefreshTokenagain.
Tip
With Azure AD B2C custom policy, you can reduce the above mentioned skew time of 5 minutes (300000 milliseconds) by adjusting the value for InputParameter "TreatAsEqualIfWithinMillseconds" under claim transformation Id "AssertRefreshTokenIssuedLaterThanValidFromDate". This claim transformation can be found in the TrustFrameworkBase.xml file under latest custom policy stater-pack.
I use multiple tabs in a web browser to sign in to multiple applications that I registered in the same Azure AD B2C tenant. When I try to perform a single sign-out, not all of the applications are signed out. Why does this happen?
Currently, Azure AD B2C doesn't support single sign-out for this specific scenario. It's caused by cookie contention as all the applications operate on the same cookie simultaneously.