Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
If your monitored application or infrastructure is behind a firewall, you need to configure network access to allow communication with Azure Monitor services.
Azure Monitor uses service tags, which provide a dynamic way to manage network access, especially if you're using Azure network security groups, Azure Firewall, or next generation firewalls (NGFW) that can implement service tags. For hybrid or on-premises resources, or network perimeter controls that don't support service tags, retrieve the equivalent IP address lists programmatically or download them as JSON files. For more information, see Service tags on-premises.
To cover all necessary exceptions, use the service tags ActionGroup, ApplicationInsightsAvailability, and AzureMonitor. Service tags don't replace validation and authentication checks required for cross-tenant communications between a customer's Azure resource and other service tag resources.
Outbound traffic
Each of the following Azure Monitor service sections require outbound traffic rules (destination) unless indicated otherwise. For example, availability monitoring and action group webhooks require inbound firewall rules (source).
Application Insights ingestion
You need to open the following outbound ports in your firewall to allow the Application Insights SDK or Application Insights agent to send data to the portal.
Note
IPv6 support is limited to specific endpoints:
{region].in.applicationinsights.azure.cnsupports both IPv4 and IPv6.{region}.livediagnostics.monitor.azure.cncurrently supports IPv4 only; IPv6 support is planned.- Global ingestion endpoints do not support IPv6 and are deprecated. For details, see Retirement announcement
| Purpose | Hostname | Type | Ports |
|---|---|---|---|
| Telemetry | dc.applicationinsights.azure.cndc.applicationinsights.microsoft.comdc.services.visualstudio.com{region}.in.applicationinsights.azure.cn |
Global Global Global Regional |
443 |
| Live Metrics | live.applicationinsights.azure.cnrt.applicationinsights.microsoft.comrt.services.visualstudio.com{region}.livediagnostics.monitor.azure.cnAn example {region} is chinanorth2 |
Global Global Global Regional |
443 |
Application Insights agent configuration
Application Insights agent configuration is needed only when you're making changes.
| Purpose | Hostname | Ports |
|---|---|---|
| Configuration | management.core.chinacloudapi.cn |
443 |
| Configuration | management.chinacloudapi.cn |
443 |
| Configuration | login.chinacloudapi.cn |
443 |
| Configuration | login.partner.microsoftonline.cn |
443 |
| Configuration | secure.aadcdn.partner.microsoftonline-p.cn |
443 |
| Configuration | auth.gfx.ms |
443 |
| Configuration | login.live.com |
443 |
| Installation | globalcdn.nuget.org, packages.nuget.org ,api.nuget.org/v3/index.json nuget.org, api.nuget.org, dc.services.vsallin.net |
443 |
Availability tests
Availability tests require inbound firewall access and are best configured with service tags and custom headers. For more information, see Availability testing behind a firewall.
Logs Query API endpoints
Starting July 1, 2025, Log Analytics enforces TLS 1.2 or higher for secure communication. For more information, see Secure Logs data in transit.
| Purpose | Hostname | Ports |
|---|---|---|
| Application Insights | api.applicationinsights.ioapi1.applicationinsights.ioapi2.applicationinsights.ioapi3.applicationinsights.ioapi4.applicationinsights.ioapi5.applicationinsights.ioapi.applicationinsights.azure.cn*.api.applicationinsights.azure.cn |
443 |
| Log Analytics | api.loganalytics.io*.api.loganalytics.ioapi.loganalytics.azure.cnapi.monitor.azure.cn*.api.monitor.azure.cn |
443 |
| Azure Data Explorer | ade.loganalytics.ioade.applicationinsights.ioadx.monitor.azure.cn*.adx.monitor.azure.cn*.adx.applicationinsights.azure.cnadx.applicationinsights.azure.cnadx.loganalytics.azure.com*.adx.loganalytics.azure.com |
443 |
Logs Ingestion API endpoints
Starting March 1, 2026, Logs Ingestion enforces TLS 1.2 or higher for secure communication. For more information, see Secure Logs data in transit.
| Purpose | Hostname | Ports |
|---|---|---|
| Logs Ingestion API | *.ingest.monitor.azure.cnprod.la.ingest.monitor.core.windows.NET*.prod.la.ingestion.msftcloudes.comprod.la.ingestion.msftcloudes.com*.prod.la.ingest.monitor.core.windows.NET |
443 |
Application Insights analytics
| Purpose | Hostname | Ports |
|---|---|---|
| CDN (Content Delivery Network) | applicationanalytics.azureedge.net |
80,443 |
| Media CDN | applicationanalyticsmedia.azureedge.net |
80,443 |
Log Analytics portal
| Purpose | Hostname | Ports |
|---|---|---|
| Portal | portal.loganalytics.io |
443 |
Application Insights Azure portal extension
| Purpose | Hostname | Ports |
|---|---|---|
| Application Insights extension | stamp2.app.insightsportal.visualstudio.com |
80,443 |
| Application Insights extension CDN | insightsportal-prod2-cdn.aisvc.visualstudio.cominsightsportal-prod2-asiae-cdn.aisvc.visualstudio.cominsightsportal-cdn-aimon.applicationinsights.io |
80,443 |
Application Insights SDKs (Software Development Kits)
| Purpose | Hostname | Ports |
|---|---|---|
| Application Insights JS SDK CDN | az416426.vo.msecnd.netjs.monitor.azure.com |
80,443 |
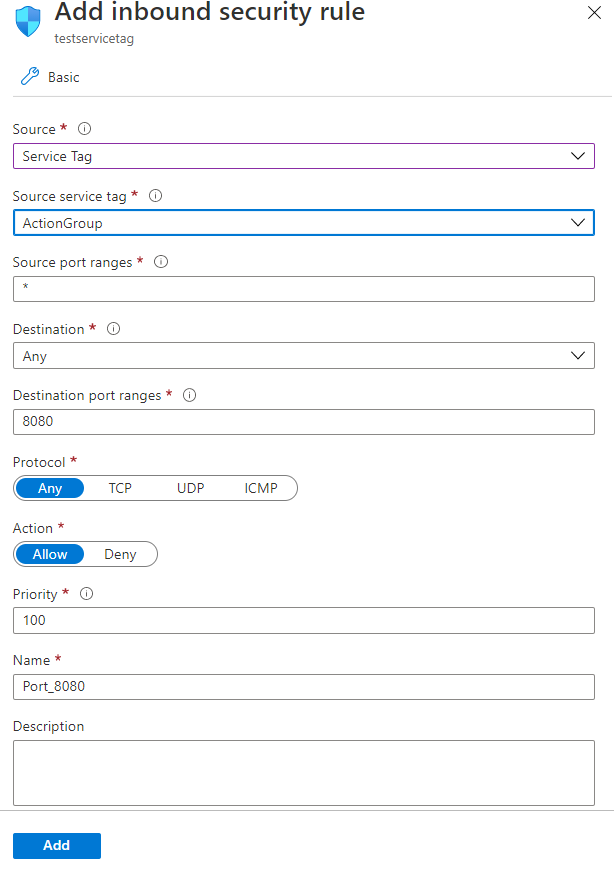
Action group webhooks
Webhooks require inbound network access. Eliminate the need to update firewall and network configurations by using the ActionGroup service tag. Alternatively, you can query the current list of IP addresses used by action groups with the Get-AzNetworkServiceTag PowerShell command or the other Service tags on-premises methods.
Here's an example of an inbound security rule with an ActionGroup service tag:
Application Insights Profiler
| Purpose | Hostname | Ports |
|---|---|---|
| Agent | agent.azureserviceprofiler.net*.agent.azureserviceprofiler.netprofiler.monitor.azure.cn |
443 |
| Portal | gateway.azureserviceprofiler.netdataplane.diagnosticservices.azure.com |
443 |
| Storage | *.core.chinacloudapi.cn |
443 |
Snapshot Debugger
Note
Application Insights Profiler for .NET and Snapshot Debugger share the same set of IP addresses.
| Purpose | Hostname | Ports |
|---|---|---|
| Agent | agent.azureserviceprofiler.net*.agent.azureserviceprofiler.netsnapshot.monitor.azure.cn |
443 |
| Portal | gateway.azureserviceprofiler.netdataplane.diagnosticservices.azure.com |
443 |
| Storage | *.core.chinacloudapi.cn |
443 |
Frequently asked questions
This section provides answers to common questions.
Can I monitor an intranet web server?
Yes, but you need to allow traffic to our services by either firewall exceptions or proxy redirects.
See IP addresses used by Azure Monitor to review our full list of services and IP addresses.
How do I reroute traffic from my server to a gateway on my intranet?
Route traffic from your server to a gateway on your intranet by overwriting endpoints in your configuration. If the Endpoint properties aren't present in your config, these classes use the default values which are documented in IP addresses used by Azure Monitor.
Your gateway should route traffic to our endpoint's base address. In your configuration, replace the default values with http://<your.gateway.address>/<relative path>.