Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This quickstart provides an introduction to working with Azure Managed Applications. You create and publish a managed application definition that's stored in your service catalog and is intended for members of your organization.
To publish a managed application to your service catalog, do the following tasks:
- Create an Azure Resource Manager template (ARM template) that defines the resources that deploy with the managed application.
- Define the user interface elements for the portal when deploying the managed application.
- Create a .zip package that contains the required JSON files. The .zip package file has a 120-MB limit for a service catalog's managed application definition.
- Publish the managed application definition so it's available in your service catalog.
If your managed application definition is more than 120 MB or if you want to use your own storage account for your organization's compliance reasons, go to Quickstart: Bring your own storage to create and publish an Azure Managed Application definition.
You can use Bicep to develop a managed application definition but it must be converted to ARM template JSON before you can publish the definition in Azure. For more information, go to Quickstart: Use Bicep to create and publish an Azure Managed Application definition.
You can also use Bicep deploy a managed application definition from your service catalog. For more information, go to Quickstart: Use Bicep to deploy an Azure Managed Application definition.
Prerequisites
To complete this quickstart, you need the following items:
- An Azure account with an active subscription and permissions to Microsoft Entra resources like users, groups, or service principals. If you don't have an account, create a Trial before you begin.
- Visual Studio Code with the latest Azure Resource Manager Tools extension. For Bicep files, install the Bicep extension for Visual Studio Code.
- Install the latest version of Azure PowerShell or Azure CLI.
Create the ARM template
Note
Azure Managed Applications only supports ARM templates using languageVersion 1.0 and does not support languageVersion 2.0. Refer to the ARM Template documentation to see what features will automatically enable version 2.0.
Every managed application definition includes a file named mainTemplate.json. The template defines the Azure resources to deploy and is no different than a regular ARM template.
Open Visual Studio Code, create a file with the case-sensitive name mainTemplate.json and save it.
Add the following JSON and save the file. It defines the resources to deploy an App Service, App Service plan, and storage account for the application. This storage account isn't used to store the managed application definition.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]"
},
"appServicePlanName": {
"type": "string",
"maxLength": 40,
"metadata": {
"description": "App Service plan name."
}
},
"appServiceNamePrefix": {
"type": "string",
"maxLength": 47,
"metadata": {
"description": "App Service name prefix."
}
}
},
"variables": {
"appServicePlanSku": "B1",
"appServicePlanCapacity": 1,
"appServiceName": "[format('{0}{1}', parameters('appServiceNamePrefix'), uniqueString(resourceGroup().id))]",
"linuxFxVersion": "DOTNETCORE|8.0"
},
"resources": [
{
"type": "Microsoft.Web/serverfarms",
"apiVersion": "2023-01-01",
"name": "[parameters('appServicePlanName')]",
"location": "[parameters('location')]",
"sku": {
"name": "[variables('appServicePlanSku')]",
"capacity": "[variables('appServicePlanCapacity')]"
},
"kind": "linux",
"properties": {
"zoneRedundant": false,
"reserved": true
}
},
{
"type": "Microsoft.Web/sites",
"apiVersion": "2023-01-01",
"name": "[variables('appServiceName')]",
"location": "[parameters('location')]",
"properties": {
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', parameters('appServicePlanName'))]",
"httpsOnly": true,
"redundancyMode": "None",
"siteConfig": {
"linuxFxVersion": "[variables('linuxFxVersion')]",
"minTlsVersion": "1.2",
"ftpsState": "Disabled"
}
},
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', parameters('appServicePlanName'))]"
]
}
],
"outputs": {
"appServicePlan": {
"type": "string",
"value": "[parameters('appServicePlanName')]"
},
"appServiceApp": {
"type": "string",
"value": "[reference(resourceId('Microsoft.Web/sites', variables('appServiceName')), '2023-01-01').defaultHostName]"
}
}
}
Define your portal experience
As a publisher, you define the portal experience to create the managed application. The createUiDefinition.json file generates the portal's user interface. You define how users provide input for each parameter using control elements like drop-downs and text boxes.
In this example, the user interface prompts you to input the App Service name prefix and App Service plan's name. During deployment of mainTemplate.json the appServiceName variables uses the uniqueString function to append a 13-character string to the name prefix so the name is globally unique across Azure.
Open Visual Studio Code, create a file with the case-sensitive name createUiDefinition.json and save it.
Add the following JSON code to the file and save it.
{
"$schema": "https://schema.management.azure.com/schemas/0.1.2-preview/CreateUIDefinition.MultiVm.json#",
"handler": "Microsoft.Azure.CreateUIDef",
"version": "0.1.2-preview",
"parameters": {
"basics": [
{}
],
"steps": [
{
"name": "webAppSettings",
"label": "Web App settings",
"subLabel": {
"preValidation": "Configure the web app settings",
"postValidation": "Completed"
},
"elements": [
{
"name": "appServicePlanName",
"type": "Microsoft.Common.TextBox",
"label": "App Service plan name",
"placeholder": "App Service plan name",
"defaultValue": "",
"toolTip": "Use alphanumeric characters or hyphens with a maximum of 40 characters.",
"constraints": {
"required": true,
"regex": "^[a-z0-9A-Z-]{1,40}$",
"validationMessage": "Only alphanumeric characters or hyphens are allowed, with a maximum of 40 characters."
},
"visible": true
},
{
"name": "appServiceName",
"type": "Microsoft.Common.TextBox",
"label": "App Service name prefix",
"placeholder": "App Service name prefix",
"defaultValue": "",
"toolTip": "Use alphanumeric characters or hyphens with minimum of 2 characters and maximum of 47 characters.",
"constraints": {
"required": true,
"regex": "^[a-z0-9A-Z-]{2,47}$",
"validationMessage": "Only alphanumeric characters or hyphens are allowed, with a minimum of 2 characters and maximum of 47 characters."
},
"visible": true
}
]
}
],
"outputs": {
"location": "[location()]",
"appServicePlanName": "[steps('webAppSettings').appServicePlanName]",
"appServiceNamePrefix": "[steps('webAppSettings').appServiceName]"
}
}
}
To learn more, see Get started with CreateUiDefinition.
Package the files
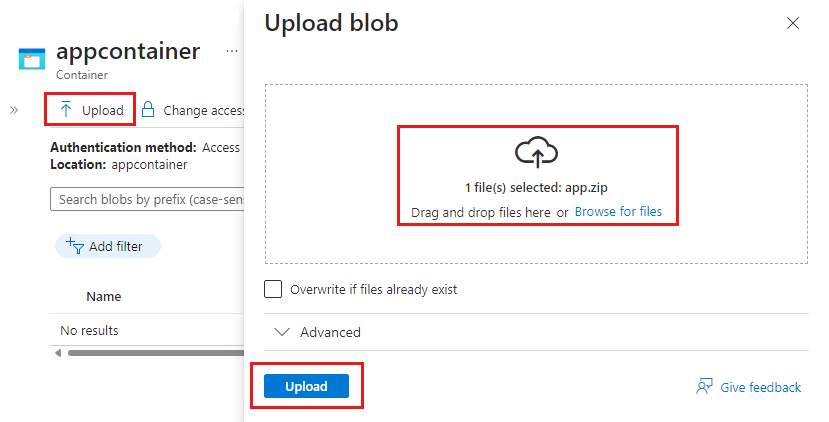
Add the two files to a package file named app.zip. The two files must be at the root level of the .zip file. If the files are in a folder, when you create the managed application definition, you receive an error that states the required files aren't present.
Upload app.zip to an Azure storage account so you can use it when you deploy the managed application's definition. The storage account name must be globally unique across Azure and the length must be 3-24 characters with only lowercase letters and numbers. In the command, replace the placeholder <pkgstorageaccountname> including the angle brackets (<>), with your unique storage account name.
In Visual Studio Code, open a new PowerShell terminal and sign in to your Azure subscription.
Connect-AzAccount
The command opens your default browser and prompts you to sign in to Azure. For more information, go to Sign in with Azure PowerShell.
New-AzResourceGroup -Name packageStorageGroup -Location chinanorth3
$pkgstorageparms = @{
ResourceGroupName = "packageStorageGroup"
Name = "<pkgstorageaccountname>"
Location = "chinanorth3"
SkuName = "Standard_LRS"
Kind = "StorageV2"
MinimumTlsVersion = "TLS1_2"
AllowBlobPublicAccess = $true
AllowSharedKeyAccess = $false
}
$pkgstorageaccount = New-AzStorageAccount @pkgstorageparms
The $pkgstorageparms variable uses PowerShell splatting to improve readability for the parameter values used in the command to create the new storage account. Splatting is used in other PowerShell commands that use multiple parameter values.
After you create the storage account, add the role assignment Storage Blob Data Contributor to the storage account scope. Assign access to your Microsoft Entra user account. Depending on your access level in Azure, you might need other permissions assigned by your administrator. For more information, see Assign an Azure role for access to blob data.
After you add the role to the storage account, it takes a few minutes to become active in Azure. You can then create the context needed to create the container and upload the file.
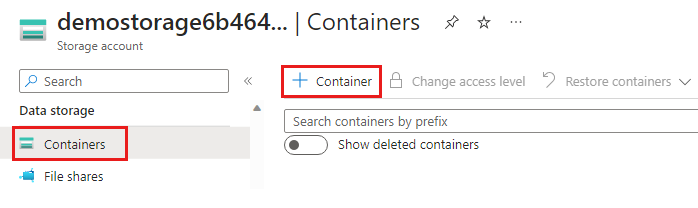
$pkgstoragecontext = New-AzStorageContext -StorageAccountName $pkgstorageaccount.StorageAccountName -UseConnectedAccount
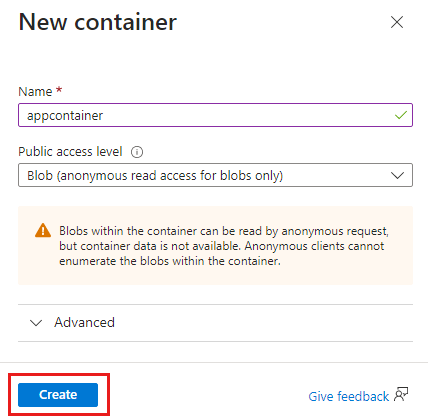
New-AzStorageContainer -Name appcontainer -Context $pkgstoragecontext -Permission blob
$blobparms = @{
File = "app.zip"
Container = "appcontainer"
Blob = "app.zip"
Context = $pkgstoragecontext
}
Set-AzStorageBlobContent @blobparms
Create the managed application definition
In this section, you get identity information from Microsoft Entra ID, create a resource group, and deploy the managed application definition.
Get group ID and role definition ID
The next step is to select a user, security group, or application for managing the resources for the customer. This identity has permissions on the managed resource group according to the assigned role. The role can be any Azure built-in role like Owner or Contributor.
This example uses a security group, and your Microsoft Entra account should be a member of the group. To get the group's object ID, replace the placeholder <managedAppDemo> including the angle brackets (<>), with your group's name. You use this variable's value when you deploy the managed application definition.
To create a new Microsoft Entra group, go to Manage Microsoft Entra groups and group membership.
$principalid=(Get-AzADGroup -DisplayName <managedAppDemo>).Id
Next, get the role definition ID of the Azure built-in role you want to grant access to the user, group, or application. You use this variable's value when you deploy the managed application definition.
$roleid=(Get-AzRoleDefinition -Name Owner).Id
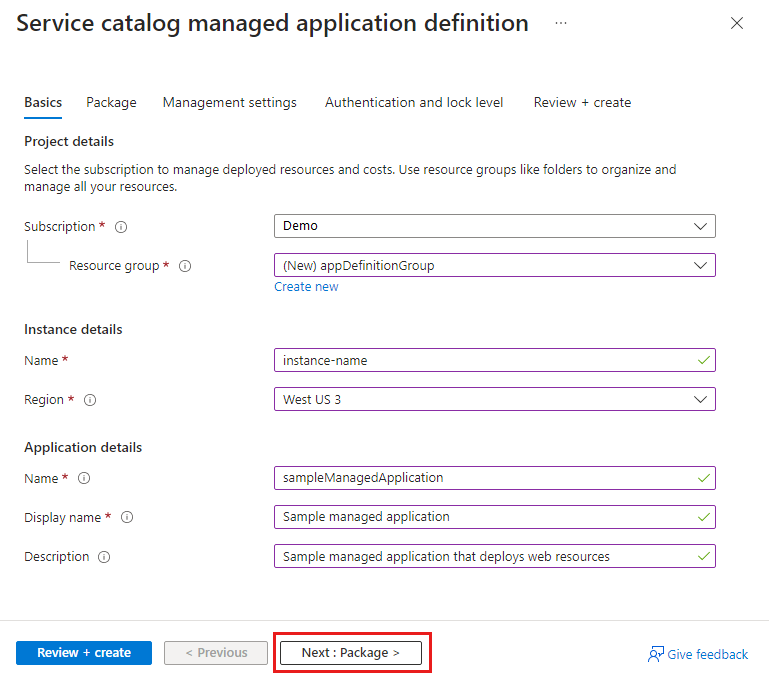
Publish the managed application definition
Create a resource group for your managed application definition.
New-AzResourceGroup -Name appDefinitionGroup -Location chinanorth3
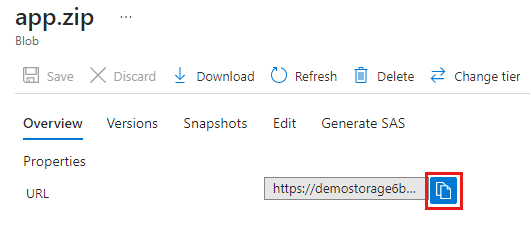
The blob command creates a variable to store the URL for the package .zip file. That variable is used in the command that creates the managed application definition.
$blob = Get-AzStorageBlob -Container appcontainer -Blob app.zip -Context $pkgstoragecontext
$publishparms = @{
Name = "sampleManagedApplication"
Location = "chinanorth3"
ResourceGroupName = "appDefinitionGroup"
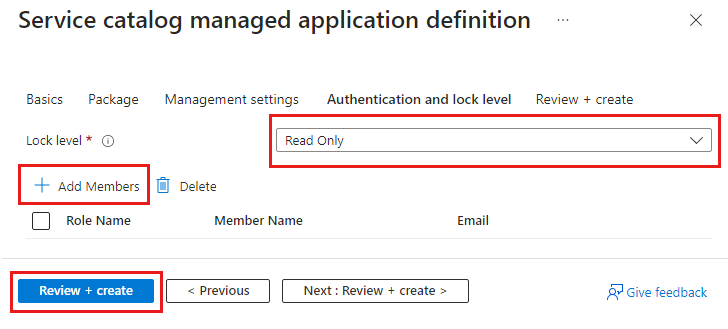
LockLevel = "ReadOnly"
DisplayName = "Sample managed application"
Description = "Sample managed application that deploys web resources"
Authorization = "${principalid}:$roleid"
PackageFileUri = $blob.ICloudBlob.StorageUri.PrimaryUri.AbsoluteUri
}
New-AzManagedApplicationDefinition @publishparms
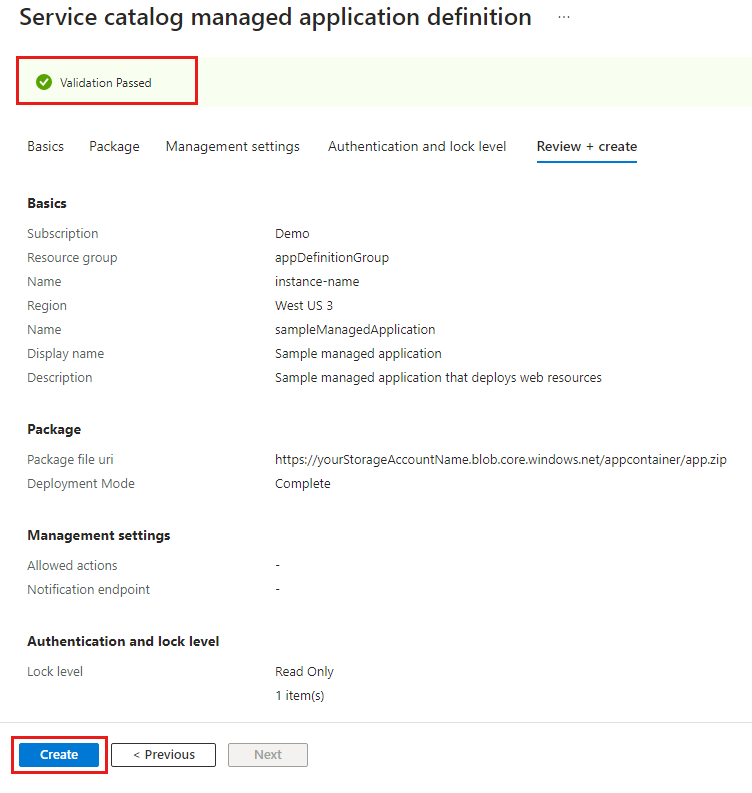
When the command completes, you have a managed application definition in your resource group.
Some of the parameters used in the preceding example are:
ResourceGroupName: The name of the resource group where the managed application definition is created.LockLevel: ThelockLevelon the managed resource group prevents the customer from performing undesirable operations on this resource group. Currently,ReadOnlyis the only supported lock level.ReadOnlyspecifies that the customer can only read the resources present in the managed resource group. The publisher identities that are granted access to the managed resource group are exempt from the lock level.Authorization: Describes the principal ID and the role definition ID that are used to grant permission to the managed resource group."${principalid}:$roleid"or you can use curly braces for each variable"${principalid}:${roleid}".- Use a comma to separate multiple values:
"${principalid1}:$roleid1", "${principalid2}:$roleid2".
PackageFileUri: The location of a .zip package file that contains the required files.
Make sure users can see your definition
You have access to the managed application definition, but you want to make sure other users in your organization can access it. Grant them at least the Reader role on the definition. They might have inherited this level of access from the subscription or resource group. To check who has access to the definition and add users or groups, see Assign Azure roles using the Azure portal.
Clean up resources
If you're going to deploy the definition, continue with the Next steps section that links to the article to deploy the definition.
If you're finished with the managed application definition, you can delete the resource groups you created named packageStorageGroup and appDefinitionGroup.
The command prompts you to confirm that you want to remove the resource group.
Remove-AzResourceGroup -Name packageStorageGroup
Remove-AzResourceGroup -Name appDefinitionGroup
Next steps
You published the managed application definition. The next step is to learn how to deploy an instance of that definition.