Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
适用于:Azure SQL 托管实例
Azure SQL 托管实例审核会跟踪数据库事件,并将事件写入 Azure 存储帐户中的审核日志。 审核还可:
- 帮助保持合规性、了解数据库活动,以及深入了解可以指明业务考量因素或疑似安全违规的偏差和异常。
- 实现并促进遵从合规标准,但不能保证合规性。 有关详细信息,请参阅 Azure 信任中心,可以从中找到 SQL 托管实例合规认证的最新列表。
重要
Azure SQL 数据库、Azure Synapse 与 Azure SQL 托管实例的审核已针对可用性和性能进行优化。 在活动量极高或网络负载较高的情况下,Azure SQL 数据库、Azure Synapse 与 Azure SQL 托管实例允许操作继续进行,并且可能不会记录某些已审核的事件。
将服务器的审核设置为 Azure 存储
以下部分介绍了托管实例上的审核配置。
转到 Azure 门户。
创建一个用于存储审核日志的 Azure 存储容器。
导航到要在其中存储审核日志的 Azure 存储帐户。
- 请使用与托管实例位于同一区域中的存储帐户,以避免跨区域读取/写入。
- 如果你的存储帐户位于虚拟网络或防火墙后面,请参阅授予从虚拟网络进行访问的权限。
- 如果将保留期从 0(无限期保留)更改为任何其他值,则该保留期将仅应用于在更改保留期值后所写入的日志(即使启用了上述保留期,在保留期值设置为“无限制”期间所写入的日志仍将无限期保留)。
在存储帐户中,转到“概述”,然后选择“Blob”。
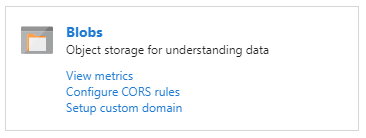
在顶部菜单中,选择“+ 容器”以创建新容器。
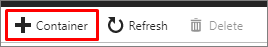
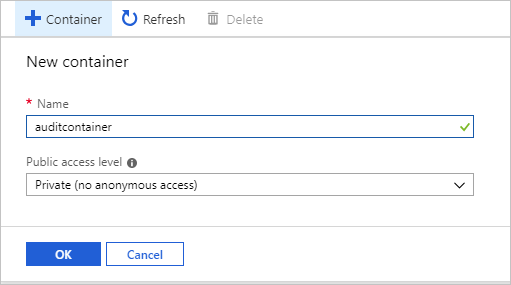
提供一个容器名称,将“公共访问级别”设置为“专用”,然后选择“确定”。
重要
如果客户希望为服务器级或数据库级审核事件配置不可变的日志存储,则应遵循 Azure 存储提供的说明。 (请确保在配置不可变的 blob 存储时,选择了“允许额外追加”。)
为审核日志创建容器后,可通过两种方式将其配置为审核日志的目标:使用 T-SQL,或使用 SQL Server Management Studio (SSMS) UI:
-
在容器列表中,选择新创建的容器,然后选择“容器属性”。
通过选择复制图标来复制容器 URL并保存该 URL(例如在记事本中)供将来使用。 容器 URL 格式应当为
https://<StorageName>.blob.core.chinacloudapi.cn/<ContainerName>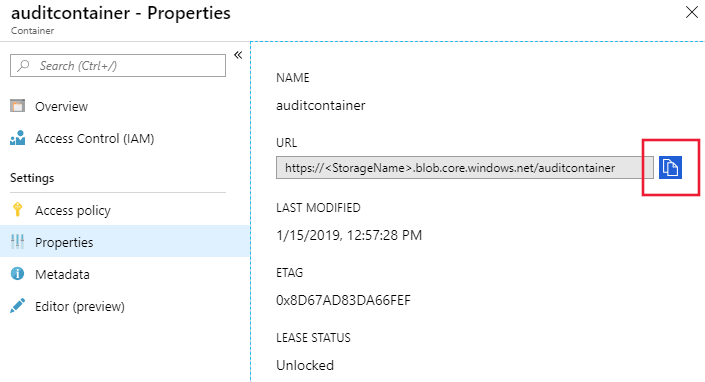
生成一个 Azure 存储 SAS 令牌,用于向存储帐户授予托管实例审核访问权限:
导航到在前面的步骤中你在其中创建了容器的 Azure 存储帐户。
在“存储设置”菜单中选择“共享访问签名”。
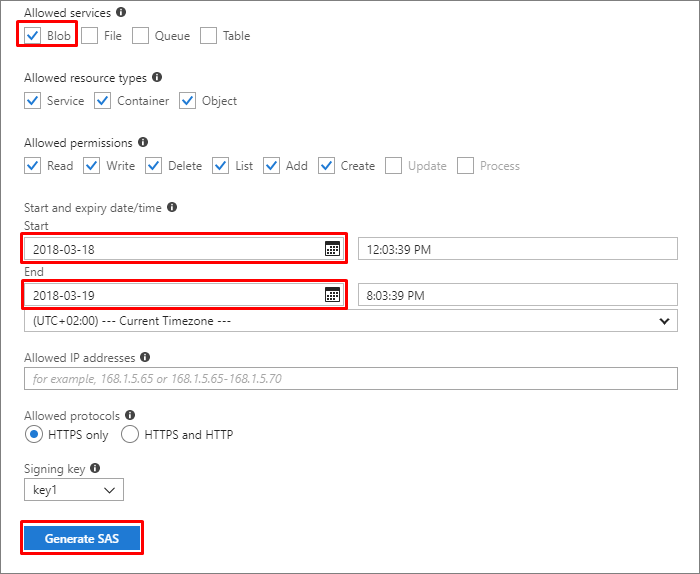
如下所述配置 SAS:
允许的服务:Blob
开始日期:为避免与时区相关的问题,请使用昨天的日期
结束日期:选择此 SAS 令牌的到期日期
注意
在到期时续订令牌,以避免审核失败。
选择“生成 SAS”。
SAS 令牌会显示在底部。 通过选择复制图标来复制令牌并保存该令牌(例如在记事本中)供将来使用。
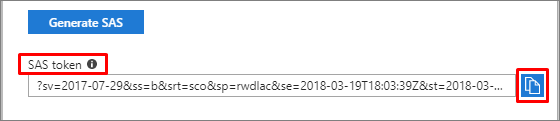
重要
从令牌的开头删除问号 (
?) 字符。
通过 SQL Server Management Studio 或任何其他支持的工具连接到托管实例。
执行以下 T-SQL 语句来使用你在前面的步骤中创建的容器 URL 和 SAS 令牌创建新凭据:
CREATE CREDENTIAL [<container_url>] WITH IDENTITY='SHARED ACCESS SIGNATURE', SECRET = '<SAS KEY>' GO执行以下 T-SQL 语句来创建新的服务器审核(请选择自己的审核名称,并使用在前面步骤中创建的容器 URL)。 如果未指定,则
RETENTION_DAYS默认为 0(无限期保留):CREATE SERVER AUDIT [<your_audit_name>] TO URL (PATH ='<container_url>', RETENTION_DAYS = <integer>); GO
使用 SQL Server Management Studio 18 及更高版本为审核日志配置 Blob 存储:
使用 SQL Server Management Studio UI 连接到托管实例。
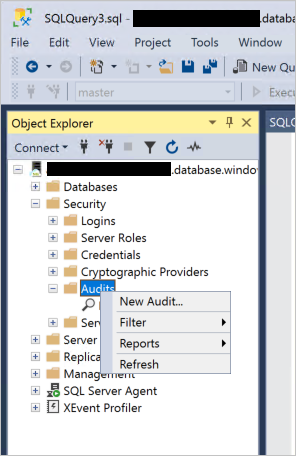
展开对象资源管理器的根节点。
展开“安全性”节点,右键单击“审核”节点,然后选择“新建审核”:
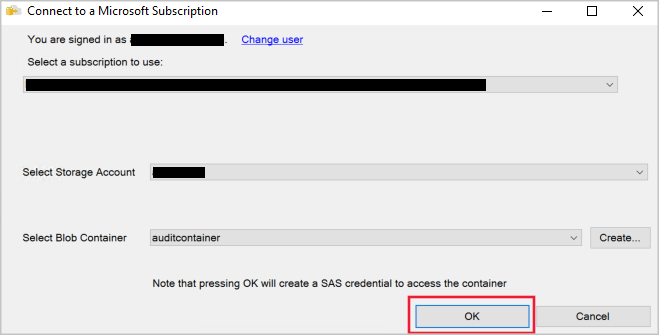
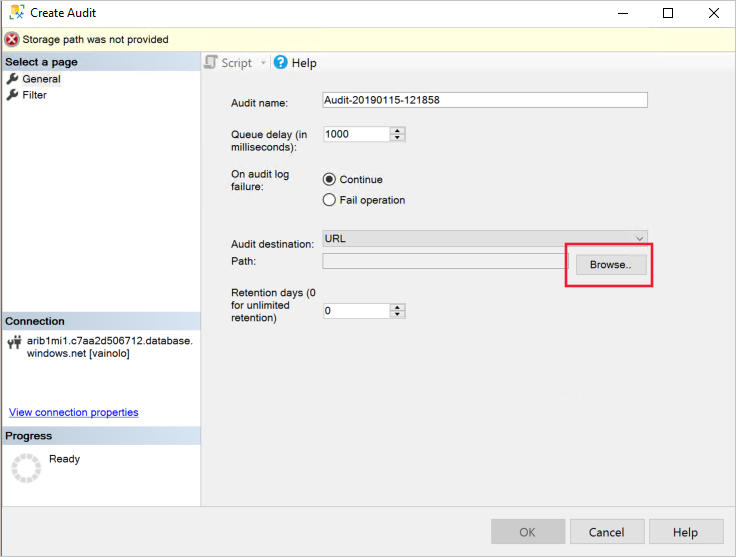
确保“审核目标”中已选择“URL”,然后选择“浏览”:
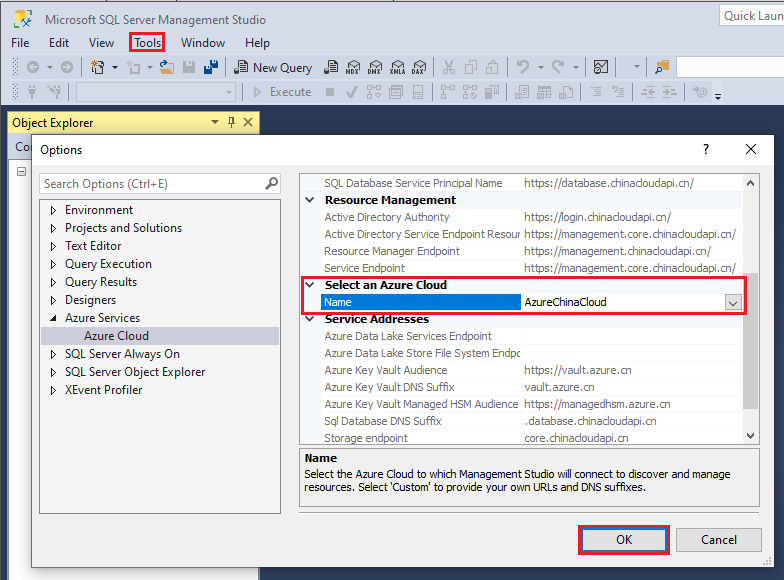
(可选)登录到 Azure 帐户:
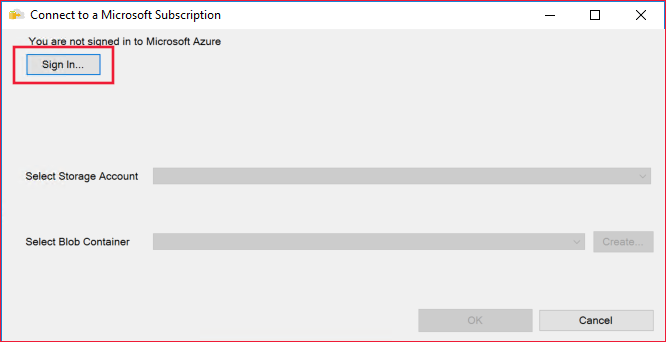
重要
在连接到订阅之前,需要配置云环境。 请导航至“工具”并选择“选项”,然后在“Azure 服务”下的“Azure 云”选项中选择“AzureChinaCloud”。
-
启用在步骤 3 中创建的服务器审核:
ALTER SERVER AUDIT [<your_audit_name>] WITH (STATE = ON); GO
了解更多信息:
审核 Microsoft 支持操作
通过对 SQL 托管实例的 Microsoft 支持操作审核,你可以在 Microsoft 支持工程师需要在支持请求期间访问你的服务器时审核他们的操作。 将此功能与审核结合使用,可以提高工作人员的透明度,并可以进行异常情况检测、趋势可视化和数据丢失防护。
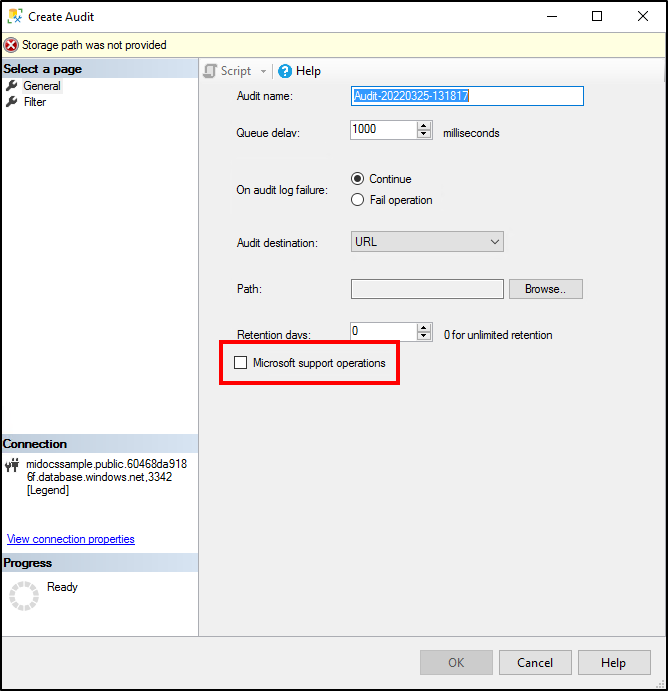
要启用对 Microsoft 支持操作的审核,请在 SQL 托管实例中导航到“安全”>“审核”下的“创建审核”,然后选择“Microsoft 支持操作”。
注意
必须创建单独的服务器审核来审核 Microsoft 操作。 如果为现有审核启用此复选框,它将覆盖审核,并且只记录支持操作。
将服务器的审核设置为事件中心或 Azure Monitor 日志
可将托管实例的审核日志发送到 Azure 事件中心或 Azure Monitor 日志。 本部分介绍如何进行以下配置:
在 Azure 门户中导航到托管实例。
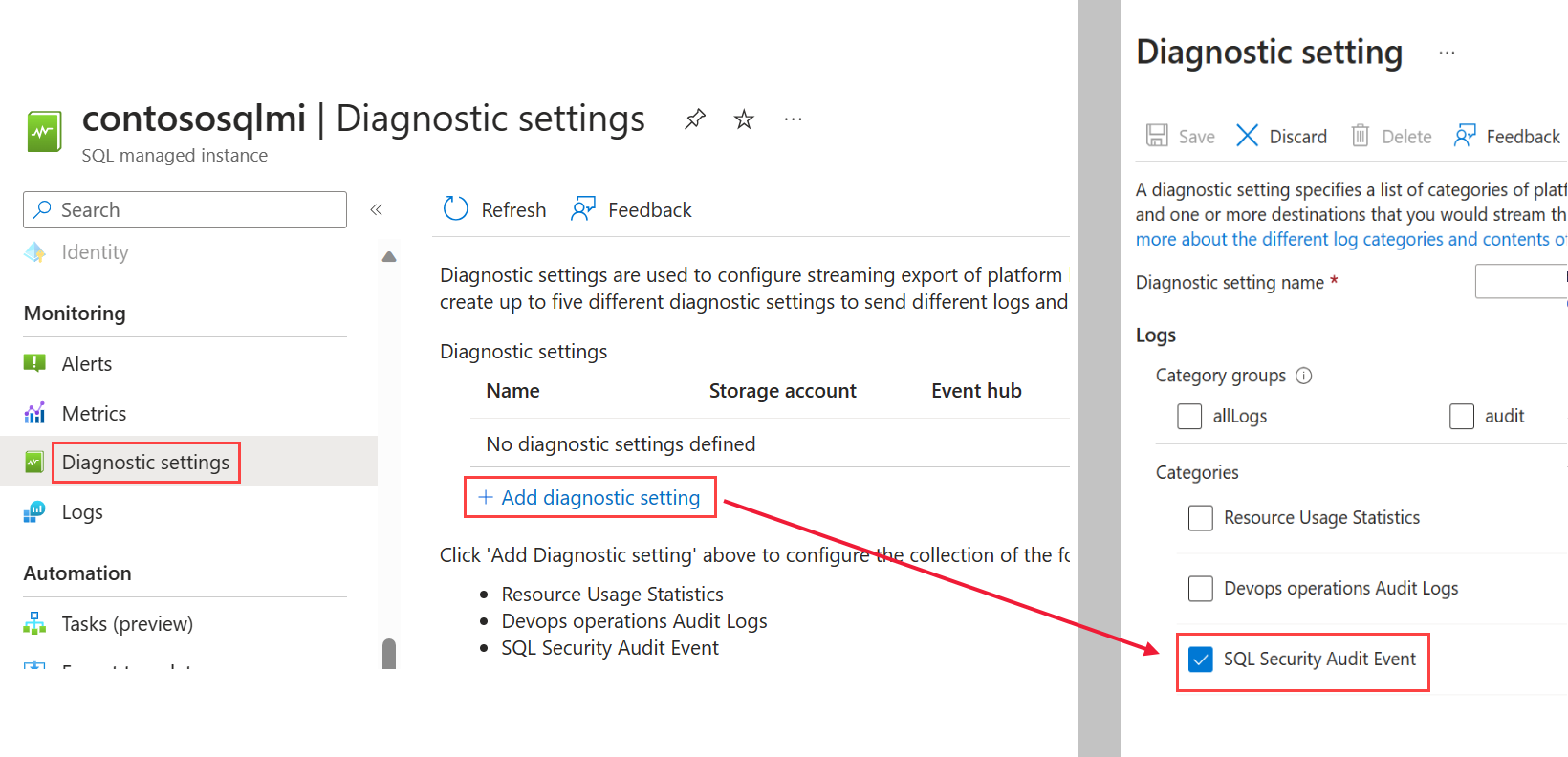
选择“诊断设置”。
选择“启用诊断”。 如果已启用诊断,则会显示“+ 添加诊断设置”。
在日志列表中选择“SQLSecurityAuditEvents”。
如果要配置 Microsoft 支持操作,请在日志列表中选择“DevOps 操作审核日志”。
选择审核事件的目标:事件中心和/或 Azure Monitor 日志。 为每个目标配置所需的参数(例如,Log Analytics 工作区)。
选择“保存” 。
使用 SQL Server Management Studio (SSMS) 或任何其他支持的客户端连接到托管实例。
执行下面的 T-SQL 语句,创建服务器审核:
CREATE SERVER AUDIT [<your_audit_name>] TO EXTERNAL_MONITOR; GO像对 SQL Server 操作一样创建并启用服务器审核规范或数据库审核规范:
启用在步骤 8 中创建的服务器审核:
ALTER SERVER AUDIT [<your_audit_name>] WITH (STATE = ON); GO
使用 T-SQL 设置审核
-- Create audit without OPERATOR_AUDIT - Will audit standard SQL Audit events
USE [master];
GO
CREATE SERVER AUDIT testingauditnodevops TO EXTERNAL_MONITOR;
GO
CREATE SERVER AUDIT SPECIFICATION testingaudit_Specification_nodevops
FOR SERVER AUDIT testingauditnodevops ADD (SUCCESSFUL_LOGIN_GROUP),
ADD (BATCH_COMPLETED_GROUP),
ADD (FAILED_LOGIN_GROUP)
WITH (STATE = ON);
GO
ALTER SERVER AUDIT testingauditnodevops
WITH (STATE = ON);
GO
-- Create separate audit without OPERATOR_AUDIT ON - Will audit Microsoft Support Operations
USE [master]
CREATE SERVER AUDIT testingauditdevops TO EXTERNAL_MONITOR
WITH (OPERATOR_AUDIT = ON);
GO
CREATE SERVER AUDIT SPECIFICATION testingaudit_Specification_devops
FOR SERVER AUDIT testingauditdevops ADD (SUCCESSFUL_LOGIN_GROUP),
ADD (BATCH_COMPLETED_GROUP),
ADD (FAILED_LOGIN_GROUP)
WITH (STATE = ON);
GO
ALTER SERVER AUDIT testingauditdevops
WITH (STATE = ON);
GO
使用审核日志
使用存储在 Azure 存储中的日志
可使用多种方法查看 blob 审核日志。
使用系统函数
sys.fn_get_audit_file(T-SQL) 以表格格式返回审核日志数据。 有关使用此函数的详细信息,请参阅 sys.fn_get_audit_file 文档。可使用 Azure 存储资源管理器等工具浏览审核日志。 在 Azure 存储中,审核日志作为 Blob 文件的集合保存在定义为存储审核日志的容器中。 有关存储文件夹的层次、命名约定和日志格式的详细信息,请参阅 Blob 审核日志格式参考。
有关审核日志使用方法的完整列表,请参阅 Azure SQL 数据库审核入门。
使用在事件中心中存储的日志
若要使用事件中心的审核日志数据,需设置一个流来使用事件并将其写入到目标。 有关详细信息,请参阅 Azure 事件中心文档。
使用和分析存储在 Azure Monitor 日志中的日志
如果将审核日志写入到 Azure Monitor 日志,则可以在 Log Analytics 工作区中使用它们,可以在其中对审核数据运行高级搜索。 首先,导航到 Log Analytics 工作区。 在“常规”部分下,选择“日志”,然后输入一个基本的查询(例如 search "SQLSecurityAuditEvents")以查看审核日志。
有了 Azure Monitor 日志,就可以使用集成的搜索和自定义仪表板来轻松分析所有工作负荷和服务器上的数百万记录,获得实时操作见解。 有关 Azure Monitor 日志搜索语言和命令的详细信息,请参阅 Azure Monitor 日志搜索参考。
注意
本文最近已更新,从使用术语“Log Analytics”改为使用术语“Azure Monitor 日志”。 日志数据仍然存储在 Log Analytics 工作区中,并仍然由同一 Log Analytics 服务收集并分析。 我们正在更新术语,以便更好地反映 Azure Monitor 中的日志的角色。 有关详细信息,请参阅 Azure Monitor 术语更改。
Azure SQL 托管实例中的数据库与 SQL Server 中的数据库之间的审核差异
在审核 Azure SQL 托管实例和 SQL Server 中的数据库方面,主要差异是:
- 使用 Azure SQL 托管实例,审核在服务器级别进行,并在 Azure Blob 存储中存储
.xel日志文件。 - 在 SQL Server 中,审核在服务器级别工作,但在文件系统和 Windows 事件日志中存储事件。
托管实例中的 XEvent 审核支持 Azure Blob 存储目标。 不支持文件和 Windows 日志。
Azure Blob 存储审核的主要 CREATE AUDIT 语法差异为:
- 提供了新语法
TO URL,该语法允许指定用于放置.xel文件的 Azure Blob 存储容器的 URL。 - 提供了新语法
TO EXTERNAL MONITOR以启用事件中心和 Azure Monitor 日志这两个目标。 - 不支持语法
TO FILE,因为 Azure SQL 托管实例无法访问 Windows 文件共享。 - 不支持关闭选项。
- 不支持
queue_delay为 0。
后续步骤
- 有关审核日志使用方法的完整列表,请参阅 Azure SQL 数据库审核入门。