Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This page describes how Azure Databricks automatically syncs users, service principals, and groups from Microsoft Entra ID using automatic identity management.
Automatic identity management overview
Automatic identity management enables you to seamlessly add users, service principals, and groups from Microsoft Entra ID into Azure Databricks without configuring an application in Microsoft Entra ID. When automatic identity management is enabled, you can directly search in identity federated workspaces for Microsoft Entra ID users, service principals, and groups, and add them to your workspace. Databricks uses Microsoft Entra ID as the source of record, so any changes to group memberships are respected in Azure Databricks.
Just-in-time (JIT) provisioning is always enabled when automatic identity management is turned on, and you cannot turn it off. New users from Microsoft Entra ID are automatically provisioned in Azure Databricks upon first login. See Automatically provision users (JIT).
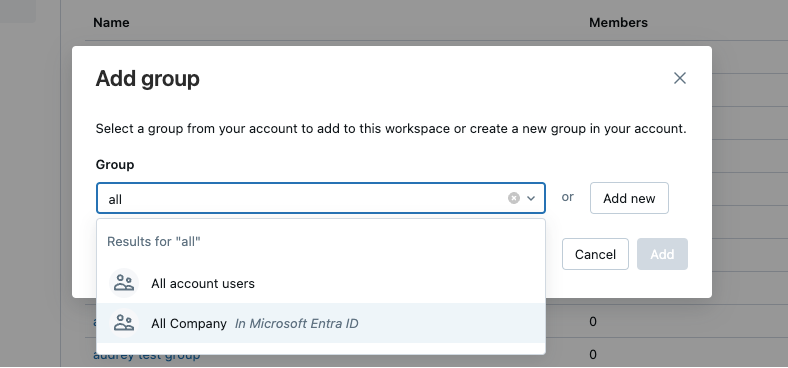
Users can also share dashboards with any user, service principal, or group in Microsoft Entra ID. When shared, those users, service principals, and members of groups are automatically added to the Azure Databricks account upon login. They are not added as members to the workspace that the dashboard is in. Members of Microsoft Entra ID who do not have access to the workspace are granted access to a view-only copy of a dashboard published with shared data permissions. For more information on dashboard sharing, see Share a dashboard.
Automatic identity management is not supported in non-identity federated workspaces. For more information on identity federation, see Identity federation.
User and group statuses
When automatic identity management is enabled, users, service principals, and groups from Microsoft Entra ID are visible in the account console and the workspace admin settings page. Their status reflects their activity and state between Microsoft Entra ID and Azure Databricks:
| Status | Meaning |
|---|---|
| Inactive: No usage | For users and service principals: identity in Microsoft Entra ID that has not logged into Azure Databricks yet. For groups: the group has not been added to a workspace. |
| Active | Identity is active in Azure Databricks. |
| Active: Removed From EntraID | Previously active in Azure Databricks and has been removed from Microsoft Entra ID. Cannot log in or authenticate to APIs. |
| Deactivated | Identity has been deactivated in Microsoft Entra ID. Cannot log in or authenticate to APIs. |
Tip
As a security best practice, Databricks recommends revoking personal access tokens for Deactivated and Active: Removed From EntraID users.
Identities that are managed using automatic identity management are shown as External in Azure Databricks. External identities cannot be updated using the Azure Databricks UI.
Automatic identity management vs SCIM provisioning
When automatic identity management is enabled, all users, groups, and group memberships sync from Microsoft Entra ID to Azure Databricks so SCIM provisioning is not necessary. If you keep the SCIM enterprise application running in parallel, the SCIM application continues to manage users and groups configured in the Microsoft Entra ID enterprise application. It does not manage Microsoft Entra ID identities that were not added using SCIM provisioning.
Databricks recommends using automatic identity management. The table below compares features of automatic identity management with the features of SCIM provisioning.
| Features | Automatic identity management | SCIM provisioning |
|---|---|---|
| Sync users | ✓ | ✓ |
| Sync groups | ✓ | ✓ (Direct members only) |
| Sync nested groups | ✓ | |
| Sync service principals | ✓ | |
| Configure and manage Microsoft Entra ID application | ✓ | |
| Requires Microsoft Entra ID Premium edition | ✓ | |
| Requires Microsoft Entra ID Cloud Application Administrator role | ✓ | |
| Requires identity federation | ✓ |
Azure Databricks external Id and Microsoft Entra ID object Id
Azure Databricks uses the Microsoft Entra ID ObjectId as the authoritative link for syncing identities and group memberships, and automatically updates the externalId field to match the ObjectId in a daily recurring flow. In some cases, mismatches or duplicate identities might still occur, especially if a user, service principal, or group is added to Azure Databricks through both automatic identity management and another method, such as SCIM provisioning. In these situations, you might see duplicate entries, with one listing with the status of Inactive: no usage. The user is not inactive and can log in Azure Databricks.
You can merge these duplicate identities by providing their external ID in Azure Databricks. Use the Account Users, Account Service Principals, or Account Groups API to update the principal to add their Microsoft Entra ID objectId in the externalId field.
Because the externalId can update over time, Azure Databricks strongly recommends that you do not use custom workflows that depend on the externalId field.
How group membership sync works
When automatic identity management is enabled, Azure Databricks refreshes user group memberships from Microsoft Entra ID during activities that trigger authentication and authorization checks, for example, browser logins, token authentication, or job runs. This ensures that group-based permissions in Azure Databricks stay synced with changes made in Microsoft Entra ID.
When Azure Databricks refreshes group memberships, it fetches transitive (nested) group memberships from Microsoft Entra ID. This means that if a user is a member of Group A, and Group A is a member of Group B, Azure Databricks recognizes the user as having membership in both groups. Azure Databricks only fetches memberships for groups that have been added to Azure Databricks. It does not sync or reconstruct the full parent group hierarchy from Microsoft Entra ID.
Azure Databricks refreshes group memberships on different schedules depending on the activity:
- Browser logins: Group memberships sync if more than 5 minutes have passed since the last sync
- Other activities (for example, token authentication, or running jobs): Group memberships sync if more than 40 minutes have passed since the last sync
Nested groups and service principals
When automatic identity management is enabled, members of nested groups inherit permissions from provisioned groups. Permissions assigned to a parent group apply to all users and service principals who belong to the group, including those added directly to the group and those who belong through nested group memberships. However, nested groups and service principals in a group are not automatically referenceable in the account, with the exception of dashboard sharing.
Nested group visibility
Nested groups are visible in Azure Databricks. Consider a child group, Group-C, which is a member of a parent group, Group-P. If you add Group-P to a workspace, all identities in both Group-P and Group-C have access to the workspace. In the account admin and workspace admin UIs, Group-C appears as a member within Group-P on the group members detail page. Only the first level of nesting appears on the group detail page.
Considerations for nested groups
- Workspace access: Nested groups and service principals do not need to be directly added to a workspace to gain access. If a parent group is added to a workspace, all members of that group can access the workspace.
- Unity Catalog referenceability: Nested groups and service principals that are members of a provisioned parent group are not directly provisioned to the Azure Databricks account. For example, a user or service principal who is a member of
Group-Ccan access a workspace where you provisioned access toGroup-P. However,Group-Cisn't referenceable in Unity Catalog until it has been provisioned to the account. - Dashboard sharing: Nested groups are referenceable in the account for dashboard sharing. When you share a dashboard, you can reference nested groups, and members of those nested groups are automatically added to the Azure Databricks account upon login.
- Account group and service principal limits: Nested groups and service principals that are not directly provisioned to the account don't count toward account group limits. Only groups that are explicitly provisioned to the account count toward the limits.
For example, in Microsoft Entra ID, you have the following group structure:
Marketing-All(parent group)Marketing-US(child group)Marketing-EU(child group)Marketing-APAC(child group)
If a workspace admin adds Marketing-All to their workspace:
- Access granted: All members of
Marketing-Alland all its child groups (Marketing-US,Marketing-EU,Marketing-APAC) can access the workspace. For example, users and service principals inMarketing-APACcan authenticate and use the workspace. - Account provisioning: Only
Marketing-Allis provisioned to the Azure Databricks account and counts toward account group limits. The child groups don't count toward limits unless you explicitly provision them. - Unity Catalog referenceability: Only
Marketing-Allis referenceable within Unity Catalog because it's provisioned to the account. Child groups aren't referenceable in Unity Catalog unless you provision them separately. - Dashboard sharing:
Marketing-Alland all its child groups (Marketing-US,Marketing-EU,Marketing-APAC) referenceable in the account for dashboard sharing.
Enable automatic identity management
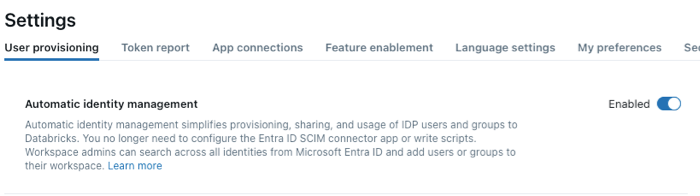
Automatic identity management is enabled by default for accounts created after August 1, 2025. Account admins can enable automatic identity management in the account console.
As an account admin, log in to the account console.
In the sidebar, click Security.
In the User provisioning tab, toggle Automatic identity management to Enabled.
Changes take five to ten minutes to take effect.
After your account is enabled, to add and remove users, service principals, and groups from Microsoft Entra ID, follow the instructions below:
Disable automatic identity management
When automatic identity management is disabled:
- Users and service principals remain: They retain access but are no longer synced with Microsoft Entra ID. You can manually remove or deactivate users and service principals in the account console after disabling automatic identity management.
- Groups lose membership: Groups remain in Azure Databricks, but all group members are removed.
- No sync with Microsoft Entra ID: Changes in Microsoft Entra ID (such as user removals or group updates) are not reflected in Azure Databricks.
- No permission inheritance: Users managed by automatic identity management cannot inherit permissions from parent groups. This affects nested group-based permission models.
If you plan to disable automatic identity management, Databricks recommends setting up SCIM provisioning in advance as a fallback. SCIM can then take over identity and group synchronization.
As an account admin, log in to the account console.
In the sidebar, click Security.
In the User provisioning tab, toggle Automatic identity management to Disabled.