Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
This feature is in Beta.
This page describes how to configure row filter and column mask policies in Unity Catalog. For more information on attribute-based access control (ABAC) and policies, see Unity Catalog attribute-based access control (ABAC). To apply tags to objects, see Governed tags and Apply tags to Unity Catalog securable objects.
Enable ABAC
The ABAC beta is enabled at the workspace level. Databricks cannot enforce ABAC on read operations to shared catalogs unless ABAC is also enabled in each workspace that accesses those catalogs.
To enable the ABAC beta, do the following:
As a workspace admin, click your username in the top bar of the Azure Databricks workspace.
From the menu, select Previews.
Set the Attribute Based Access Control toggle to On.
Compute requirements
- You must use compute on Databricks Runtime 16.4 or above.
Compute running older runtimes cannot access tables secured by ABAC. As a temporary workaround, you can configure ABAC to apply only to a specific group. Add the users you want to restrict to that group. Users who are not in the group can still access the tables.
Create a policy on an object
To create a row filter or column mask policy, you must have:
The ABAC beta and tag policies beta enabled in your workspace. See Enable ABAC.
An existing user-defined function (UDF) that implements the row filter or column mask logic you want to enforce.\
For best practices and examples UDFs, see UDFs for ABAC policies best practices.
MANAGEon the object or ownership of the object.You must use compute on Databricks Runtime 16.4 or above.
Compute running older runtimes cannot access tables secured by ABAC. As a temporary workaround, you can configure ABAC to apply only to a specific group. Add the users you want to restrict to that group. Users who are not in the group can still access the tables.
Catalog Explorer
In your Azure Databricks workspace, click
Catalog.
Select the object that determines the policy scope, such as a catalog, schema, or table.
Click the Policies tab.
Click New policy.
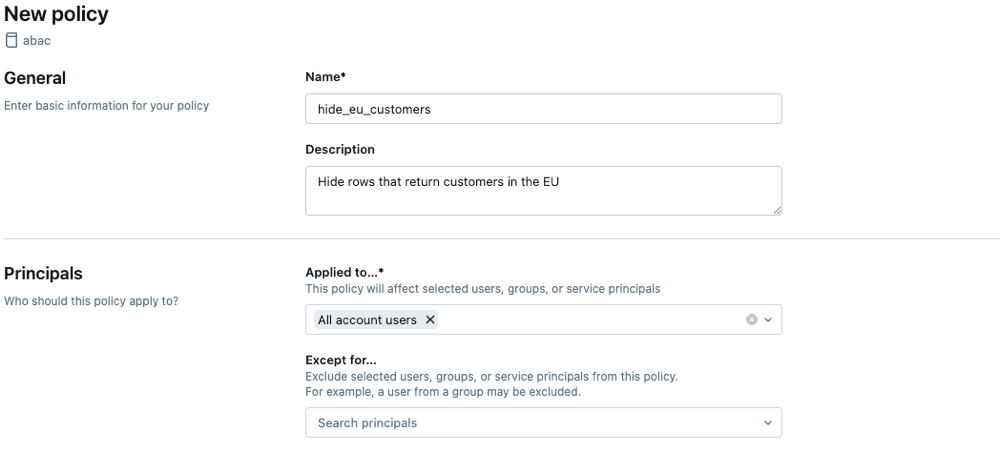
In General, enter a name and description for your policy.
In Principals:
- In Applied to…, search for and select the principals that the policy will govern.
- In Except for…, search for and select any principals to exclude from the policy. For example, you might exclude a user who belongs to a group the policy applies to.
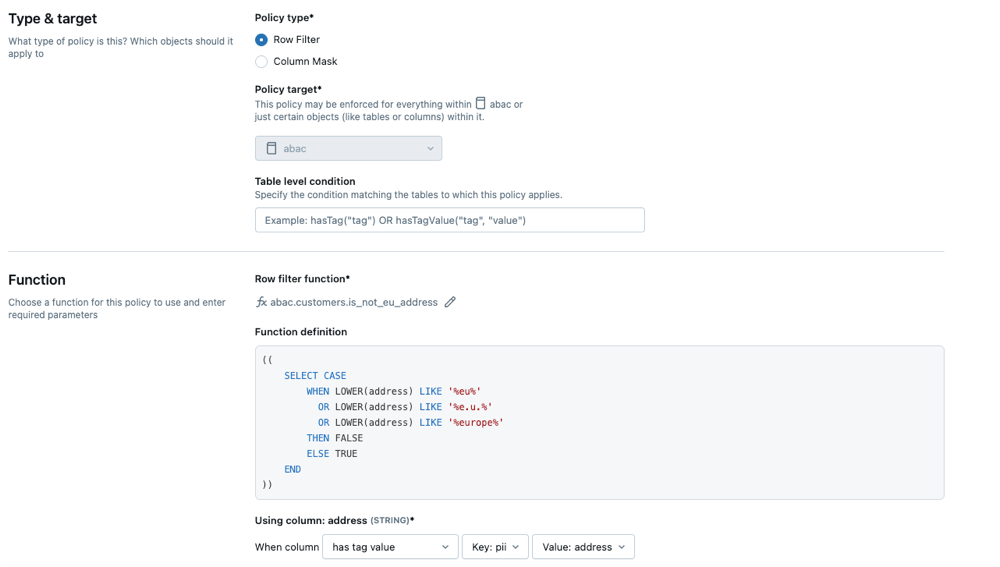
In Type & target:
- In Policy type, select Row Filter or Column Mask.
- In Policy target, select the scope of the policy. This can be a broad scope, such as an entire catalog or schema, or a narrower scope, such as specific tables or columns within it.
- In Table level condition, specify the condition matching the tables to which this policy applies. For example,
hasTag("tag")orhasTagValue("tag", "value").
In Function, select a function for this policy to use and enter required parameters. To create a new function, see Creating UDFs in Unity Catalog. For best practices and examples functions, see UDFs for ABAC policies best practices.
Click Create policy.
SQL
The following is the general syntax for creating a policy:
CREATE POLICY <policy_name>
ON <securable_type> <securable_name>
COMMENT '<policy_description>'
-- One of the following:
ROW FILTER <udf_name>
| COLUMN MASK <udf_name> ON COLUMN <target_column>
TO <principal_name>[, <principal_name>, ...]
[EXCEPT <principal_name>[, <principal_name>, ...]]
FOR TABLES
[WHEN hasTag('<key>') OR hasTagValue('<key>', '<value>')]
MATCH COLUMNS hasTag('<key>') OR hasTagValue('<key>', '<value>') AS <alias>
USING COLUMNS <alias>[, <alias>, ...];
This example defines a row filter policy that excludes rows for European customers from queries by US-based analysts:
CREATE POLICY hide_eu_customers
ON SCHEMA prod.customers
COMMENT 'Hide rows with European customers from sensitive tables'
ROW FILTER non_eu_region
TO us_analysts
FOR TABLES
MATCH COLUMNS
hasTag('geo_region') AS region
USING COLUMNS (region);
This example defines a column mask policy that hides social security numbers from US analysts, except for those with in the admins group:
CREATE POLICY mask_SSN
ON SCHEMA prod.customers
COMMENT 'Mask social security numbers'
COLUMN MASK mask_SSN
TO us_analysts
EXCEPT admins
FOR TABLES
MATCH COLUMNS
hasTagValue('pii', 'ssn') AS ssn
ON COLUMN ssn;
Warning
Tag data is stored as plain text and may be replicated globally. Do not use tag names, values, or descriptors that could compromise the security of your resources. For example, do not use tag names, values or descriptors that contain personal or sensitive information.
Edit a policy
Permissions required: MANAGE on the object or the owner of the object.
Catalog Explorer
In your Azure Databricks workspace, click
Catalog.
Select the object that determines the policy scope, such as a catalog, schema, or table.
Click the Policies tab.
Select the policy and make edits.
Click Update policy.
SQL
CREATE OR REPLACE POLICY <policy_name>
ON <securable_type> <securable_name>
COMMENT '<policy_description>'
-- One of the following:
ROW FILTER <udf_name>
| COLUMN MASK <udf_name> ON COLUMN <target_column>
TO <principal_name>[, <principal_name>, ...]
[EXCEPT <principal_name>[, <principal_name>, ...]]
FOR TABLES
[WHEN hasTag('<key>') OR hasTagValue('<key>', '<value>')]
MATCH COLUMNS hasTag('<key>') OR hasTagValue('<key>', '<value>') AS <alias>
USING COLUMNS <alias>[, <alias>, ...];
Delete a policy
Permissions required: MANAGE on the object or the owner of the object.
Catalog Explorer
In your Azure Databricks workspace, click
Catalog.
Select the object that determines the policy scope, such as a catalog, schema, or table.
Click the Policies tab.
Select the policy.
Click Delete policy.
SQL
DROP POLICY <policy_name> ON <securable_type> <securable_name>