Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In Defender for Cloud, regulatory compliance standards are implemented using Azure Policy initiatives and evaluated through the Regulatory compliance dashboard.
You can assign regulatory compliance standards to specific scopes such as Azure subscriptions.
Defender for Cloud continually assesses the scoped environment against the standards. Based on these assessments, it shows whether in-scope resources are compliant or noncompliant with the standard and provides remediation recommendations.
Prerequisites
- To access compliance standards in Defender for Cloud, onboard any Defender for Cloud plan.
- You need
OwnerorPolicy Contributorpermissions to add a standard.
Assign a standard
If you assign a regulatory standard but don't have any relevant assessed resources in that standard, the standard doesn't appear on your regulatory compliance dashboard.
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Regulatory compliance. For each standard, you can see the applied subscription.
Select Manage compliance policies.
Select an account or management account (Azure subscription or management group) to assign the regulatory compliance standard.
Note
We recommend selecting the highest scope applicable to the standard so that compliance data is aggregated and tracked for all nested resources.
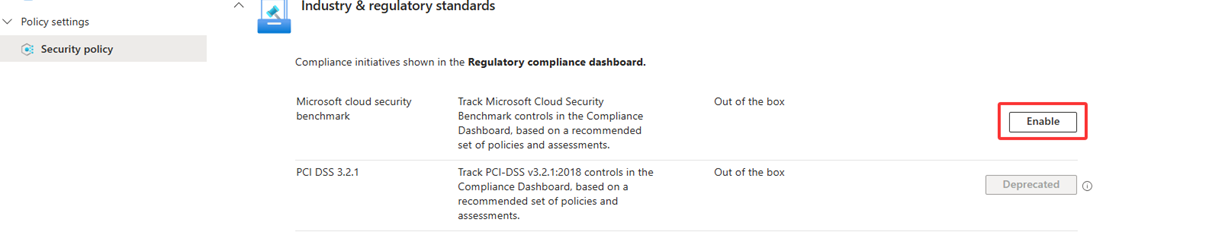
Select Security policies.
Locate the standard you want to enable and click the Enable button.
If any information is needed to enable the standard, the Set parameters page appears for you to type in the information.
The selected standard appears in the Regulatory compliance dashboard as enabled for the subscription it was enabled on.