Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
When you collaborate with external B2B guest users, protect your apps with multifactor authentication policies. External users need more than just a username and password to access your resources. In Microsoft Entra ID, you can accomplish this goal with a Conditional Access policy that requires MFA for access. You can enforce MFA policies at the tenant, app, or individual guest user level, just like for members of your own organization. The resource tenant is responsible for Microsoft Entra multifactor authentication for users, even if the guest user's organization has multifactor authentication capabilities.
Example:
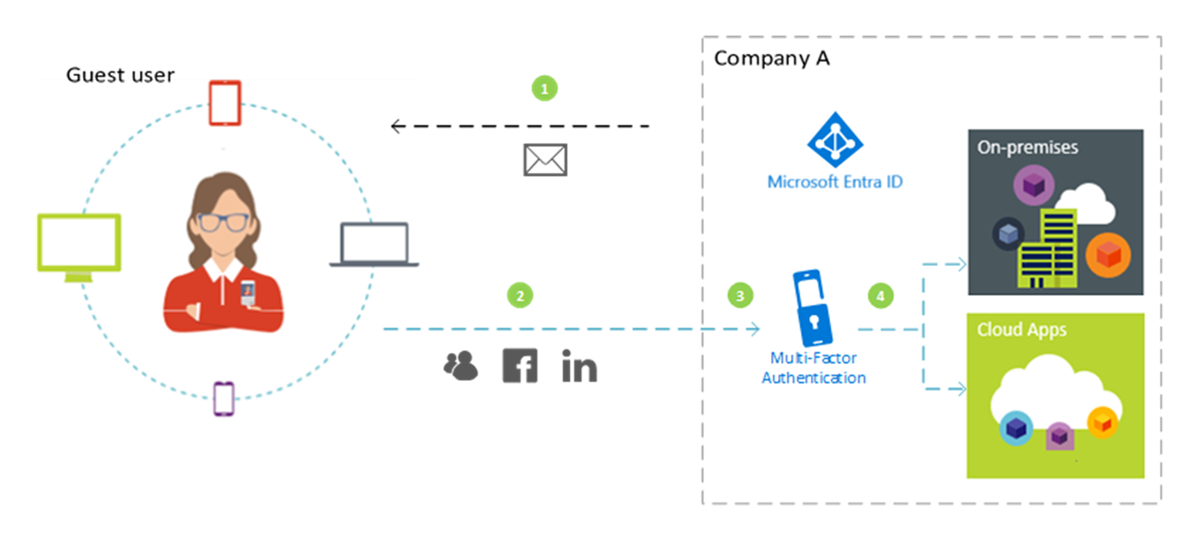
- An admin or employee at Company A invites a guest user to use a cloud or on-premises application that is configured to require MFA for access.
- The guest user signs in with their own work, school, or social identity.
- The user is asked to complete an MFA challenge.
- The user sets up MFA with Company A and chooses their MFA option. The user is allowed access to the application.
Note
Microsoft Entra multifactor authentication is done at resource tenancy to ensure predictability. When the guest user signs in, they see the resource tenant sign-in page displayed in the background, and their own home tenant sign-in page and company logo in the foreground.
In this tutorial, you will:
- Test the sign-in experience before setting up MFA.
- Create a Conditional Access policy that requires MFA for access to a cloud app in your environment. In this tutorial, we’ll use the Azure Resource Manager app to illustrate the process.
- Test your Conditional Access policy.
- Clean up the test user and policy.
If you don't have an Azure subscription, create a Trial to get started.
Prerequisites
To complete the scenario in this tutorial, you need:
- Access to Microsoft Entra ID P1 or P2 edition, which includes Conditional Access policy capabilities. To enforce MFA, create a Microsoft Entra Conditional Access policy. MFA policies are always enforced at your organization, even if the partner doesn't have MFA capabilities.
- A valid external email account that you can add to your tenant directory as a guest user and use to sign in. If you don't know how to create a guest account, follow the steps in Add a B2B guest user in the Microsoft Entra admin center.
Create a test guest user in Microsoft Entra ID
Sign in to the Microsoft Entra admin center as at least a User Administrator.
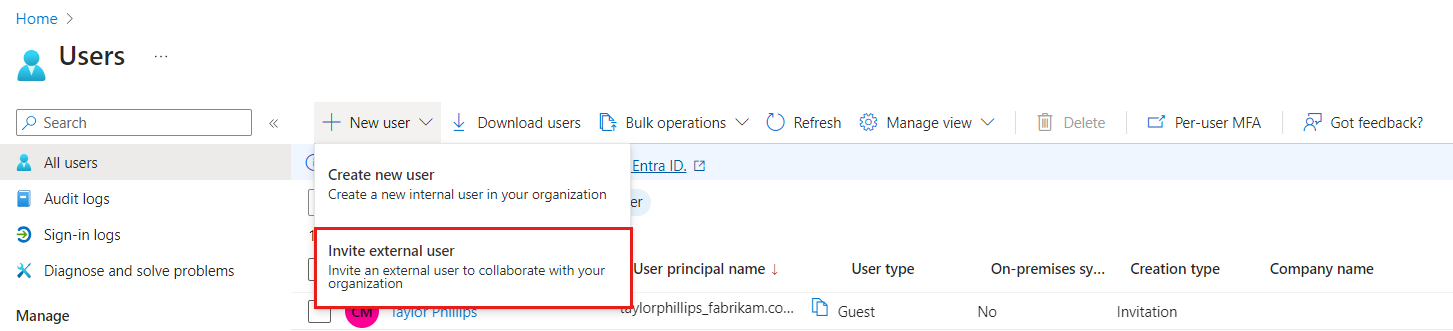
Browse to Entra ID > Users.
Select New user and then Invite external user.
Under Identity on the Basics tab, enter the email address of the external user. You can optionally include a display name and welcome message.
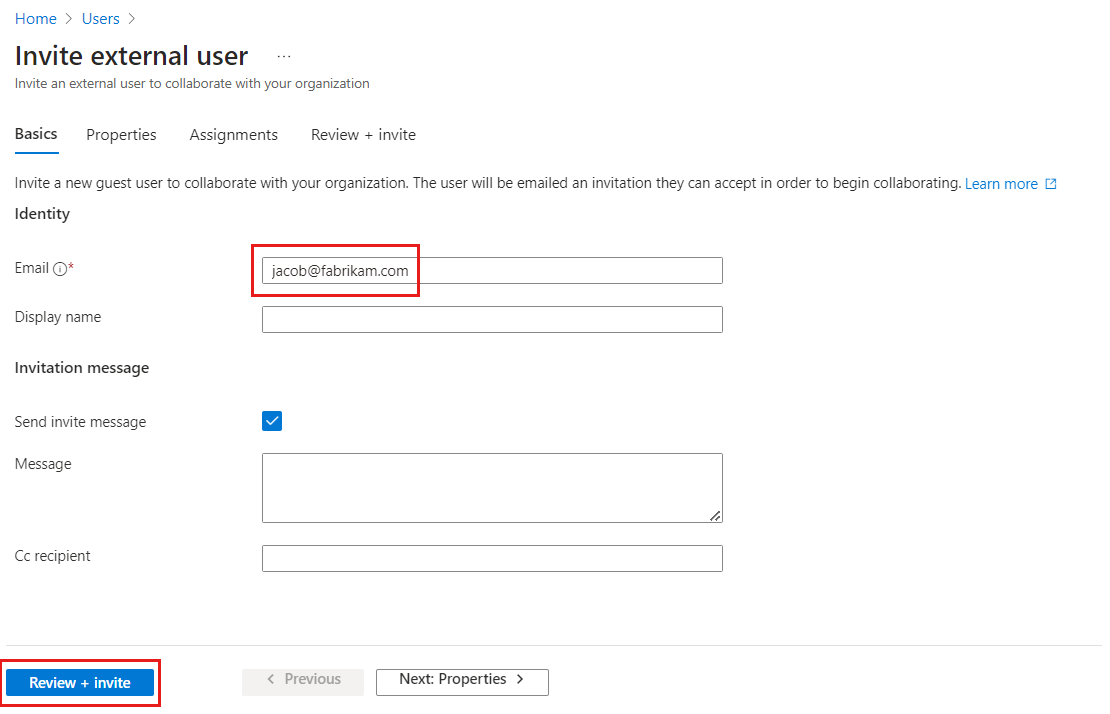
You can optionally add further details to the user under the Properties and Assignments tabs.
Select Review + invite to automatically send the invitation to the guest user. A Successfully invited user message appears.
After you send the invitation, the user account is added to the directory as a guest.
Test the sign-in experience before MFA setup
- Sign in to the Microsoft Entra admin center using your test user name and password.
- Access the Microsoft Entra admin center using only your sign-in credentials. No other authentication is required.
- Sign out of the Microsoft Entra admin center.
Create a Conditional Access policy that requires MFA
Sign in to the Azure portal as a security administrator or a Conditional Access administrator.
In the Azure portal, select Microsoft Entra ID.
In the left menu, under Manage, select Security.
Under Protect, select Conditional Access.
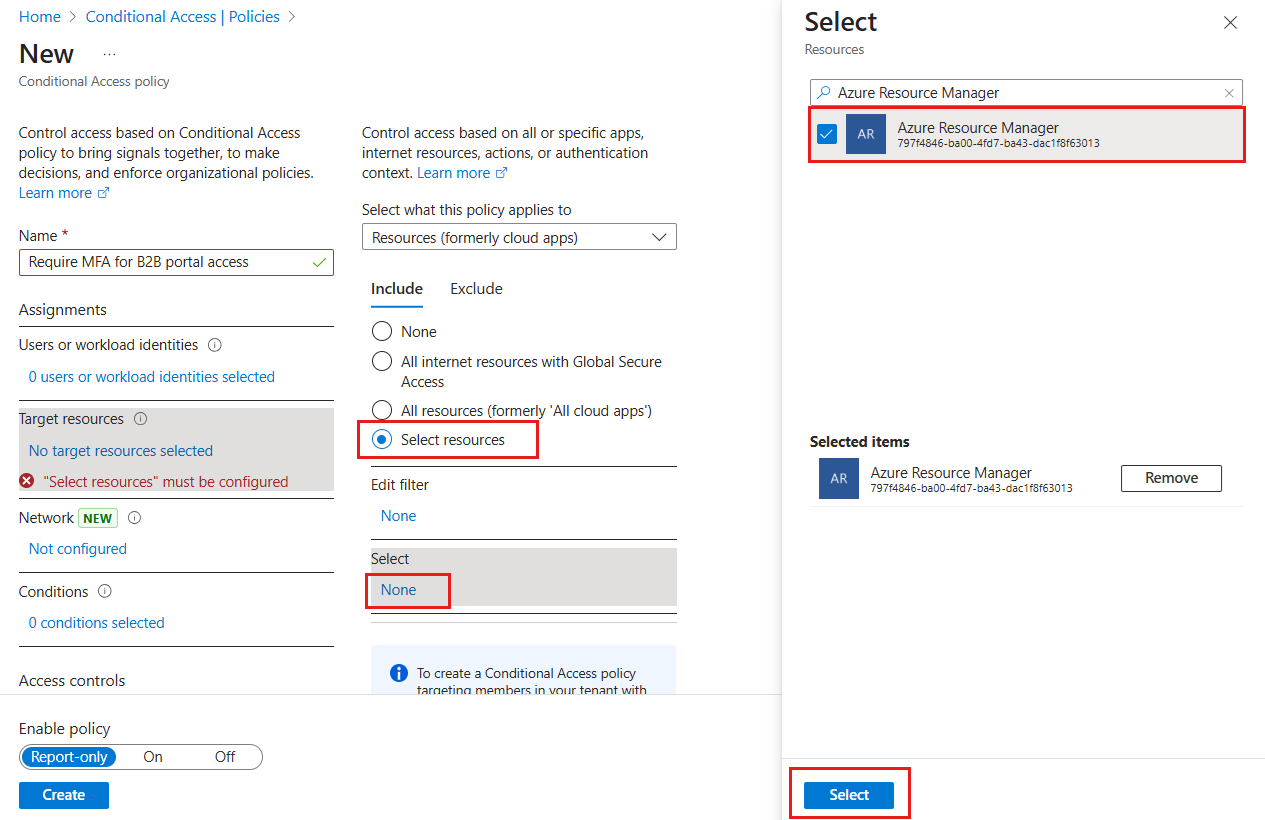
Select + New policy.
Name your policy, like Require MFA for B2B portal access. Create a meaningful standard for naming policies.
Under Assignments, select Users or workload identities.
- Under Include, choose Select users and groups, and then select Guest or external users. You can assign the policy to different external user types, built-in directory roles, or users and groups.
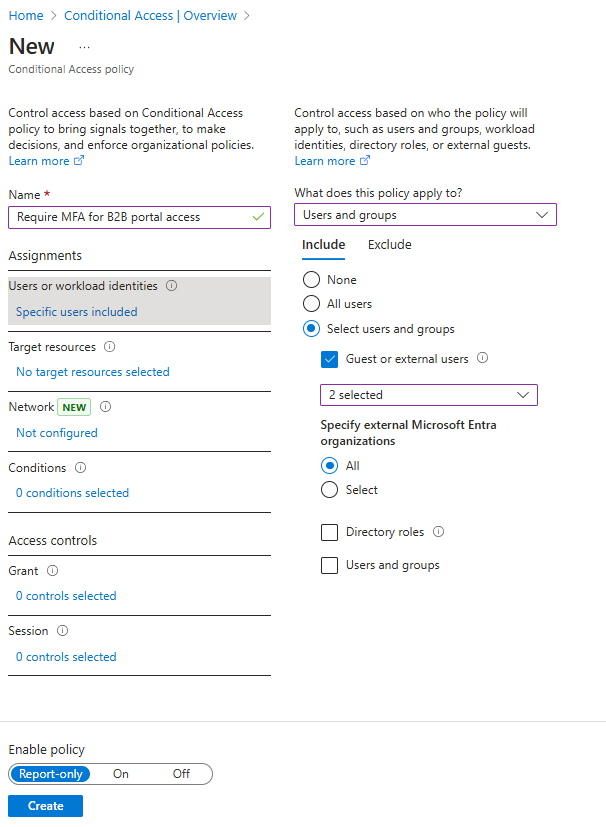
Under Target resources > Resources (formerly cloud apps) > Include > Select resources, choose Azure Resource Manager, and then Select the resource.
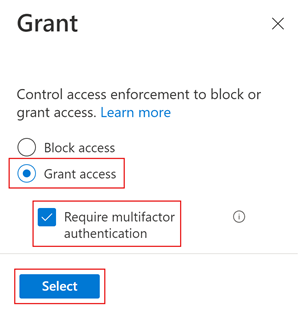
Under Access controls > Grant, select Grant access, Require multifactor authentication, and select Select.
Under Enable policy, select On.
Select Create.
Test your Conditional Access policy
Use your test user name and password to sign in to the Microsoft Entra admin center.
You should see a request for more authentication methods. It can take some time for the policy to take effect.

Note
You can also configure cross-tenant access settings to trust the MFA from the Microsoft Entra home tenant. This allows external Microsoft Entra users to use the MFA registered in their own tenant rather than register in the resource tenant.
Sign out.
Clean up resources
When no longer needed, remove the test user and the test Conditional Access policy.
- Sign in to the Azure portal as a Microsoft Entra administrator.
- In the left pane, select Microsoft Entra ID.
- Under Manage, select Users.
- Select the test user, and then select Delete user.
- In the left pane, select Microsoft Entra ID.
- Under Security, select Conditional Access > Policies.
- In the Policy Name list, select the context menu (…) for your test policy, then select Delete, and confirm by selecting Yes.
Next steps
In this tutorial, you created a Conditional Access policy that requires guest users to use MFA when signing in to one of your cloud apps. To learn more about adding guest users for collaboration, go to Add Microsoft Entra B2B collaboration users in the Microsoft Entra admin center.