Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra organizations can use External ID cross-tenant access settings to manage collaboration with other Microsoft Entra organizations and Azure clouds through B2B collaboration. The cross-tenant access settings provide granular control over inbound and outbound access, allowing you to trust multifactor authentication (MFA) and device claims from other organizations.
This article covers cross-tenant access settings for managing B2B collaboration with external Microsoft Entra organizations, including across Azure clouds. Other settings are available for B2B collaboration with non-Microsoft Entra identities (for example, social identities or non-IT managed external accounts). These external collaboration settings include options for restricting guest user access, specifying who can invite guests, and allowing or blocking domains.
There are no limits to the number of organizations you can add in cross-tenant access settings.
Manage external access with inbound and outbound settings
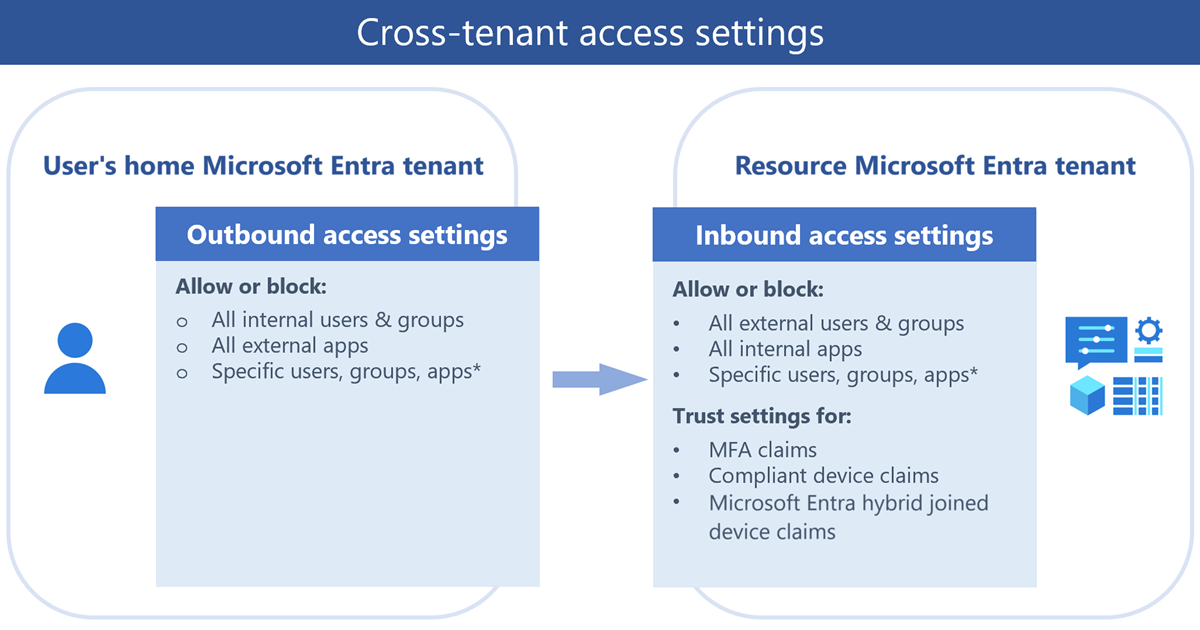
The external identities cross-tenant access settings manage how you collaborate with other Microsoft Entra organizations. These settings determine both the level of inbound access users in external Microsoft Entra organizations have to your resources, and the level of outbound access your users have to external organizations.
The following diagram shows the cross-tenant access inbound and outbound settings. The Resource Microsoft Entra tenant is the tenant containing the resources to be shared. For B2B collaboration, the resource tenant is the inviting tenant (for example, your corporate tenant, where you want to invite the external users). The User's home Microsoft Entra tenant is the tenant where the external users are managed.
By default, B2B collaboration with other Microsoft Entra organizations is enabled. But the following comprehensive admin settings let you manage both of these features.
Outbound access settings control whether your users can access resources in an external organization. You can apply these settings to everyone, or specify individual users, groups, and applications.
Inbound access settings control whether users from external Microsoft Entra organizations can access resources in your organization. You can apply these settings to everyone, or specify individual users, groups, and applications.
Trust settings (inbound) determine whether your Conditional Access policies trust the multifactor authentication (MFA), compliant device, and Microsoft Entra hybrid joined device claims from an external organization if their users already satisfied these requirements in their home tenants. For example, when you configure your trust settings to trust MFA, your MFA policies are still applied to external users, but users who already completed MFA in their home tenants don't have to complete MFA again in your tenant.
Default settings
The default cross-tenant access settings apply to all Microsoft Entra organizations external to your tenant, except organizations for which you configure custom settings. You can change your default settings, but the initial default settings for B2B collaboration as follows:
B2B collaboration: All your internal users are enabled for B2B collaboration by default. This setting means your users can invite external guests to access your resources and they can be invited to external organizations as guests. MFA and device claims from other Microsoft Entra organizations aren't trusted.
Organizational settings: No organizations are added to your Organizational settings by default. Therefore, all external Microsoft Entra organizations are enabled for B2B collaboration with your organization.
These default settings apply to B2B collaboration with other Microsoft Entra tenants in your same Azure cloud. In cross-cloud scenarios, default settings work a little differently. See Microsoft cloud settings later in this article.
Organizational settings
You can configure organization-specific settings by adding an organization and modifying the inbound and outbound settings for that organization. Organizational settings take precedence over default settings.
B2B collaboration: Use cross-tenant access settings to manage inbound and outbound B2B collaboration and scope access to specific users, groups, and applications. You can set a default configuration that applies to all external organizations, and then create individual, organization-specific settings as needed. Using cross-tenant access settings, you can also trust multifactor (MFA) and device claims (compliant claims and Microsoft Entra hybrid joined claims) from other Microsoft Entra organizations.
You can use External collaboration settings to limit who can invite external users, allow or block B2B specific domains, and set restrictions on guest user access to your directory.
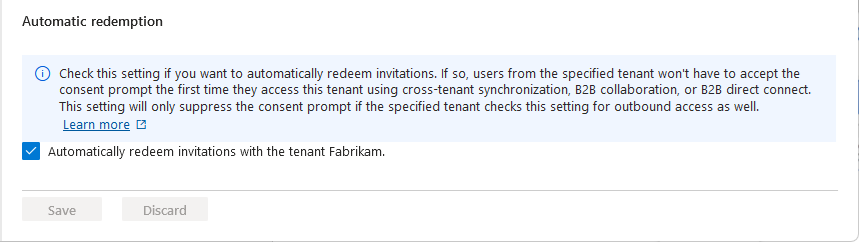
Automatic redemption setting
The automatic redemption setting is an inbound and outbound organizational trust setting to automatically redeem invitations so users don't have to accept the consent prompt the first time they access the resource/target tenant. This setting is a check box with the following name:
- Automatically redeem invitations with the tenant <tenant>
Compare setting for different scenarios
The automatic redemption setting applies to cross-tenant synchronization and B2B collaboration in the following situations:
- When users are created in a target tenant using cross-tenant synchronization.
- When users are added to a resource tenant using B2B collaboration.
The following table shows how this setting compares when enabled for these scenarios:
| Item | Cross-tenant synchronization | B2B collaboration |
|---|---|---|
| Automatic redemption setting | Required | Optional |
| Users receive a B2B collaboration invitation email | No | No |
| Users must accept a consent prompt | No | No |
| Users receive a B2B collaboration notification email | No | Yes |
This setting doesn't impact application consent experiences. For more information, see Consent experience for applications in Microsoft Entra ID. This setting is supported for organizations across different Azure cloud environments, such as Azure commercial and Azure Government.
When is consent prompt suppressed?
The automatic redemption setting will only suppress the consent prompt and invitation email if both the home/source tenant (outbound) and resource/target tenant (inbound) checks this setting.
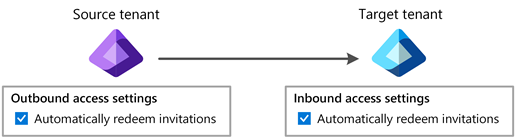
The following table shows the consent prompt behavior for source tenant users when the automatic redemption setting is checked for different cross-tenant access setting combinations.
| Home/source tenant | Resource/target tenant | Consent prompt behavior for source tenant users |
|---|---|---|
| Outbound | Inbound | |
| Suppressed | ||
| Not suppressed | ||
| Not suppressed | ||
| Not suppressed | ||
| Inbound | Outbound | |
| Not suppressed | ||
| Not suppressed | ||
| Not suppressed | ||
| Not suppressed |
To configure this setting using Microsoft Graph, see the Update crossTenantAccessPolicyConfigurationPartner API. For information about building your own onboarding experience, see B2B collaboration invitation manager.
For more information, see Configure cross-tenant access settings for B2B collaboration.
Configurable redemption
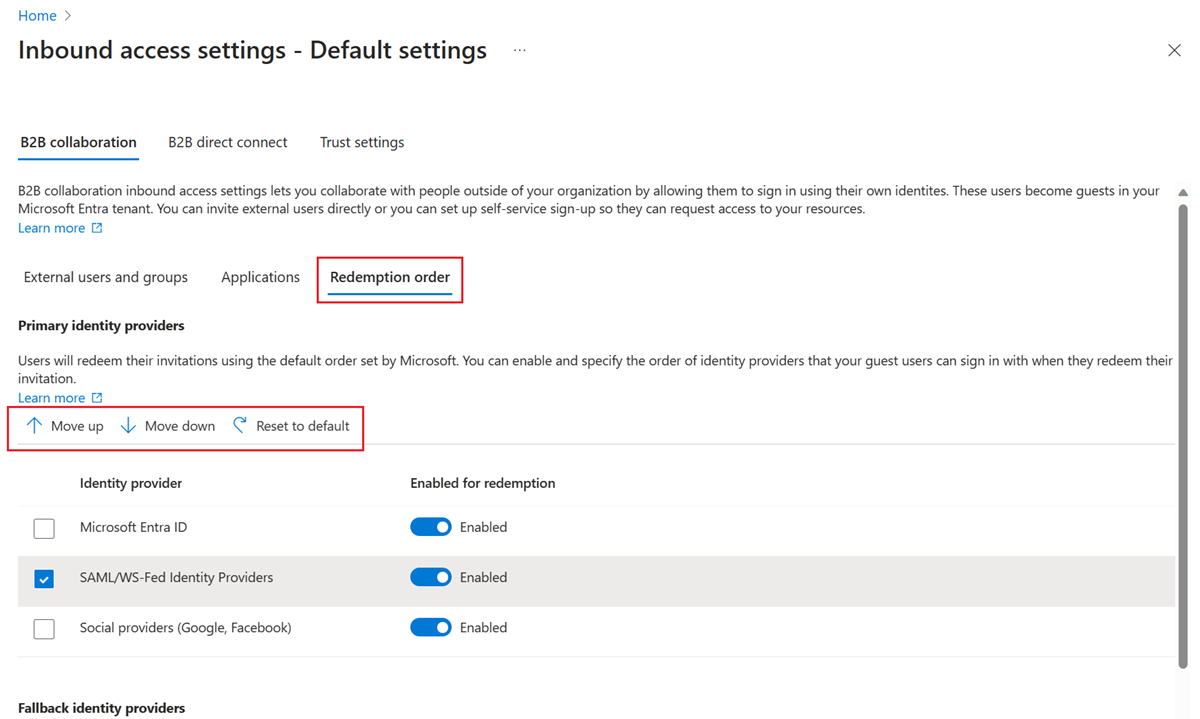
With configurable redemption, you can customize the order of identity providers that your guest users can sign in with when they accept your invitation. You can enable the feature and specify the redemption order under the Redemption order tab.
When a guest user selects the Accept invitation link in an invitation email, Microsoft Entra ID automatically redeems the invitation based on the default redemption order. When you change the identity provider order under the new Redemption order tab, the new order overrides the default redemption order.
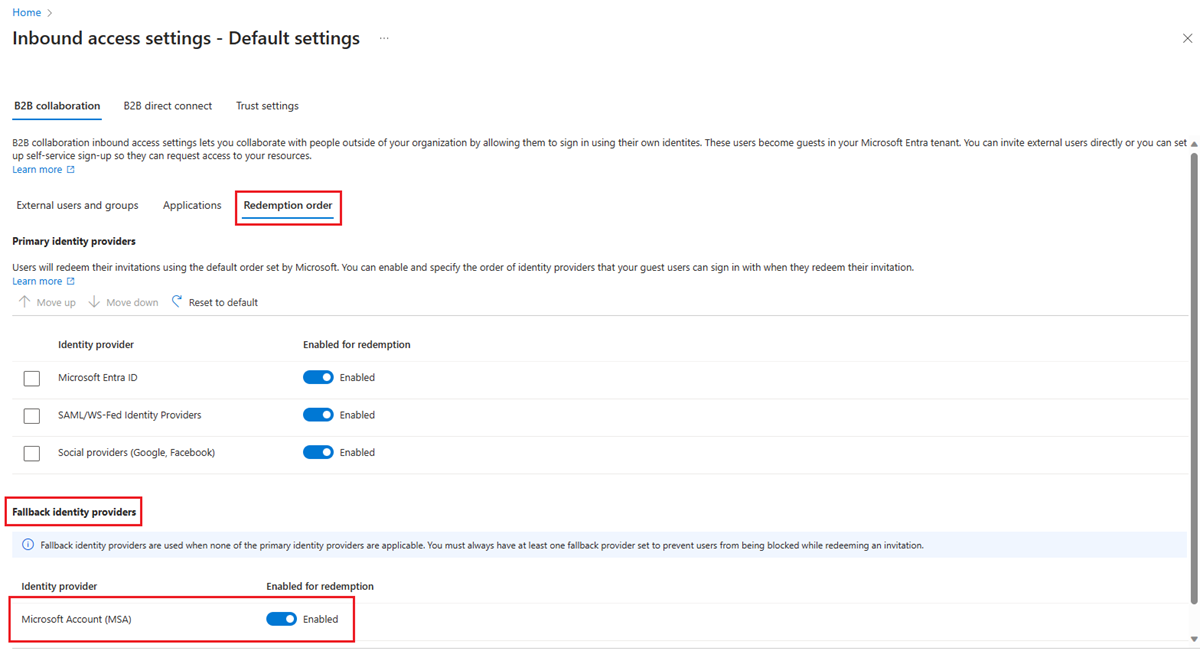
You find both primary identity providers and fallback identity providers under the Redemption order tab.
Primary identity providers are the ones that have federations with other sources of authentication. Fallback identity providers are the ones that are used, when a user doesn't match a primary identity provider.
Fallback identity providers can be either Microsoft account (MSA), email one-time passcode, or both. You can't disable both fallback identity providers, but you can disable all primary identity providers and only use fallback identity providers for redemption options.
When using this feature, consider the following known limitations:
If a Microsoft Entra ID user who has an existing single sign-on (SSO) session is authenticating using email one-time passcode (OTP), they need to choose Use another account and reenter their username to trigger the OTP flow. Otherwise the user gets an error indicating their account doesn’t exist in the resource tenant.
When a user has the same email in both their Microsoft Entra ID and Microsoft accounts, they're prompted to choose between using their Microsoft Entra ID or their Microsoft account even after the admin disables the Microsoft account as a redemption method. Choosing Microsoft account as a redemption option is allowed, even if the method is disabled.
Direct federation for Microsoft Entra ID verified domains
SAML/WS-Fed identity provider federation (Direct federation) is now supported for Microsoft Entra ID verified domains. This feature allows you to set up a Direct federation with an external identity provider for a domain that is verified in another Microsoft Entra tenant
Note
Ensure that the domain is not verified in the same tenant in which you are trying to set up the Direct federation configuration. Once you have set up a Direct federation, you can configure the tenant’s redemption preference and move SAML/WS-Fed identity provider over Microsoft Entra ID through the new configurable redemption cross-tenant access settings.
When the guest user redeems the invite, they see a traditional consent screen and are redirected to the My Apps page. In the resource tenant, the profile for this direct federation user shows that the invite is successfully redeemed, with external federation listed as the issuer.
Prevent your B2B users from redeeming an invite using Microsoft accounts
You can now prevent your B2B guest users from using Microsoft accounts to redeem invitations. Instead, they use a one-time passcode sent to their email as the fallback identity provider. They're not allowed to use an existing Microsoft account to redeem invitations, nor are they prompted to create a new one. You can enable this feature in your redemption order settings by turning off Microsoft accounts in the fallback identity provider options.
You must always have at least one fallback identity provider active. So, if you decide to disable Microsoft accounts, you need to enable the email one-time passcode option. Existing guest users who already sign in with Microsoft accounts continue to do so for future sign-ins. To apply the new settings to them, you need to reset their redemption status.
Tenant restrictions
With Tenant Restrictions settings, you can control the types of external accounts your users can use on the devices you manage, including:
- Accounts your users created in unknown tenants.
- Accounts that external organizations gave to your users so they can access that organization's resources.
We recommend configuring your tenant restrictions to disallow these types of external accounts and use B2B collaboration instead. B2B collaboration gives you the ability to:
- Use Conditional Access and force multifactor authentication for B2B collaboration users.
- Manage inbound and outbound access.
- Terminate sessions and credentials when a B2B collaboration user's employment status changes or their credentials are breached.
- Use sign-in logs to view details about the B2B collaboration user.
Tenant restrictions are independent of other cross-tenant access settings, so any inbound, outbound, or trust settings you configure don't affect tenant restrictions. For details about configuring tenant restrictions, see Set up tenant restrictions V2.
Microsoft cloud settings
Microsoft cloud settings let you collaborate with organizations from different Azure clouds. With Microsoft cloud settings, you can establish mutual B2B collaboration between the following clouds:
- Azure commercial cloud and Azure Government, which includes the Office GCC-High and DoD clouds
- Azure commercial cloud and Microsoft Azure operated by 21Vianet
For more information, see the Configure Microsoft cloud settings for B2B collaboration article.
Important considerations
Important
Changing the default inbound or outbound settings to block access could block existing business-critical access to apps in your organization or partner organizations. Be sure to use the tools described in this article and consult with your business stakeholders to identify the required access.
To configure cross-tenant access settings in the Azure portal, you need an account with at least Security Administrator, or a custom role.
To configure trust settings or apply access settings to specific users, groups, or applications, you need a Microsoft Entra ID P1 license. The license is required on the tenant that you configure.
Cross-tenant access settings are used to manage B2B collaboration with other Microsoft Entra organizations. For B2B collaboration with non-Microsoft Entra identities (for example, social identities or non-IT managed external accounts), use external collaboration settings. External collaboration settings include B2B collaboration options for restricting guest user access, specifying who can invite guests, and allowing or blocking domains.
To apply access settings to specific users, groups, or applications in an external organization, you need to contact the organization for information before configuring your settings. Obtain their user object IDs, group object IDs, or application IDs (client app IDs or resource app IDs) so you can target your settings correctly.
Tip
You might be able to find the application IDs for apps in external organizations by checking your sign-in logs. See the Identify inbound and outbound sign-ins section.
The access settings you configure for users and groups must match the access settings for applications. Conflicting settings aren't allowed, and warning messages appear if you try to configure them.
Example 1: If you block inbound access for all external users and groups, access to all your applications must also be blocked.
Example 2: If you allow outbound access for all your users (or specific users or groups), you're prevented from blocking all access to external applications; access to at least one application must be allowed.
If you block access to all apps by default, users are unable to read emails encrypted with Microsoft Rights Management Service, also known as Office 365 Message Encryption (OME). To avoid this issue, we recommend configuring your outbound settings to allow your users to access this app ID: 00000012-0000-0000-c000-000000000000. If you allow only this application, access to all other apps is blocked by default.
If an organization requires MFA or Terms of Use (ToU) by Conditional Access policies, users might be blocked from registering MFA methods or consenting to ToU. To avoid this issue, configure outbound settings (home tenant) and inbound settings (resource tenant) to let users access app ID 0000000c-0000-0000-c000-000000000000 (Microsoft App Access Panel) for MFA registration and app ID d52792f4-ba38-424d-8140-ada5b883f293 (AAD Terms of Use) for ToU. The configuration of the outbound settings can be achieved via the Microsoft Entra admin center by selecting 'Add other applications' and providing the app ID. Due to a current user interface (UI) limitation the configuration of the inbound settings must be performed via Microsoft Graph APIs.
Custom roles for managing cross-tenant access settings
You can create custom roles to manage cross-tenant access settings. Learn more about the recommended custom roles here.
Protect cross-tenant access administrative actions
Any actions that modify cross-tenant access settings are considered protected actions and can be additionally protected with Conditional Access policies. For more information about configuration steps, see protected actions.
Identify inbound and outbound sign-ins
Several tools are available to help you identify the access your users and partners need before you set inbound and outbound access settings. To ensure you don’t remove access that your users and partners need, you should examine current sign-in behavior. Taking this preliminary step helps prevent loss of desired access for your end users and partner users. However, in some cases these logs are only retained for 30 days, so we strongly recommend you speak with your business stakeholders to ensure required access isn't lost.
| Tool | Method |
|---|---|
| PowerShell script for cross-tenant sign-in activity | To review user sign-in activity associated with external organizations, use the cross-tenant user sign-in activity PowerShell script from the MSIdentityTools. |
| PowerShell script for sign-in logs | To determine your users' access to external Microsoft Entra organizations, use the Get-MgAuditLogSignIn cmdlet. |
| Azure Monitor | If your organization subscribes to the Azure Monitor service, use the Cross-tenant access activity workbook. |
| Security Information and Event Management (SIEM) systems | If your organization exports sign-in logs to a Security Information and Event Management (SIEM) system, you can retrieve the required information from your SIEM system. |
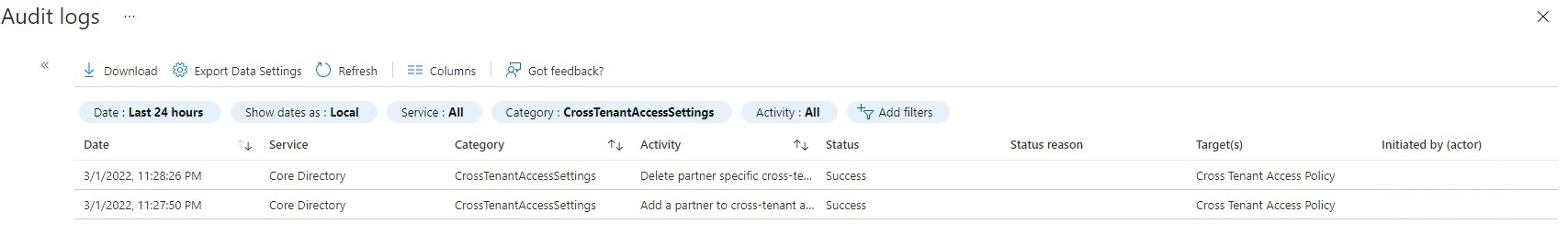
Identify changes to cross-tenant access settings
The Microsoft Entra audit logs capture all activity around cross-tenant access setting changes and activity. To audit changes to your cross-tenant access settings, use the category of CrossTenantAccessSettings to filter all activity to show changes to cross-tenant access settings.
Next steps
Configure cross-tenant access settings for B2B collaboration