Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
As an access package manager, you can assign which role you want to provide a user for a group within an access package. By managing groups with Privileged Identity Management(PIM), you're able to enhance security by designating that group access happens just-in-time. This article describes how to enable PIM for a group, adding the group to an access package, and verifying eligible assignments are available.
Prerequisites
Using this feature requires Microsoft Entra ID Governance or Microsoft Entra Suite licenses. To find the right license for your requirements, see Microsoft Entra ID Governance licensing fundamentals.
Create a group
This section walks you through creating the group that you enable to be managed by PIM. If you've already created the group you want to be managed by PIM, skip to Enable management of group with PIM.
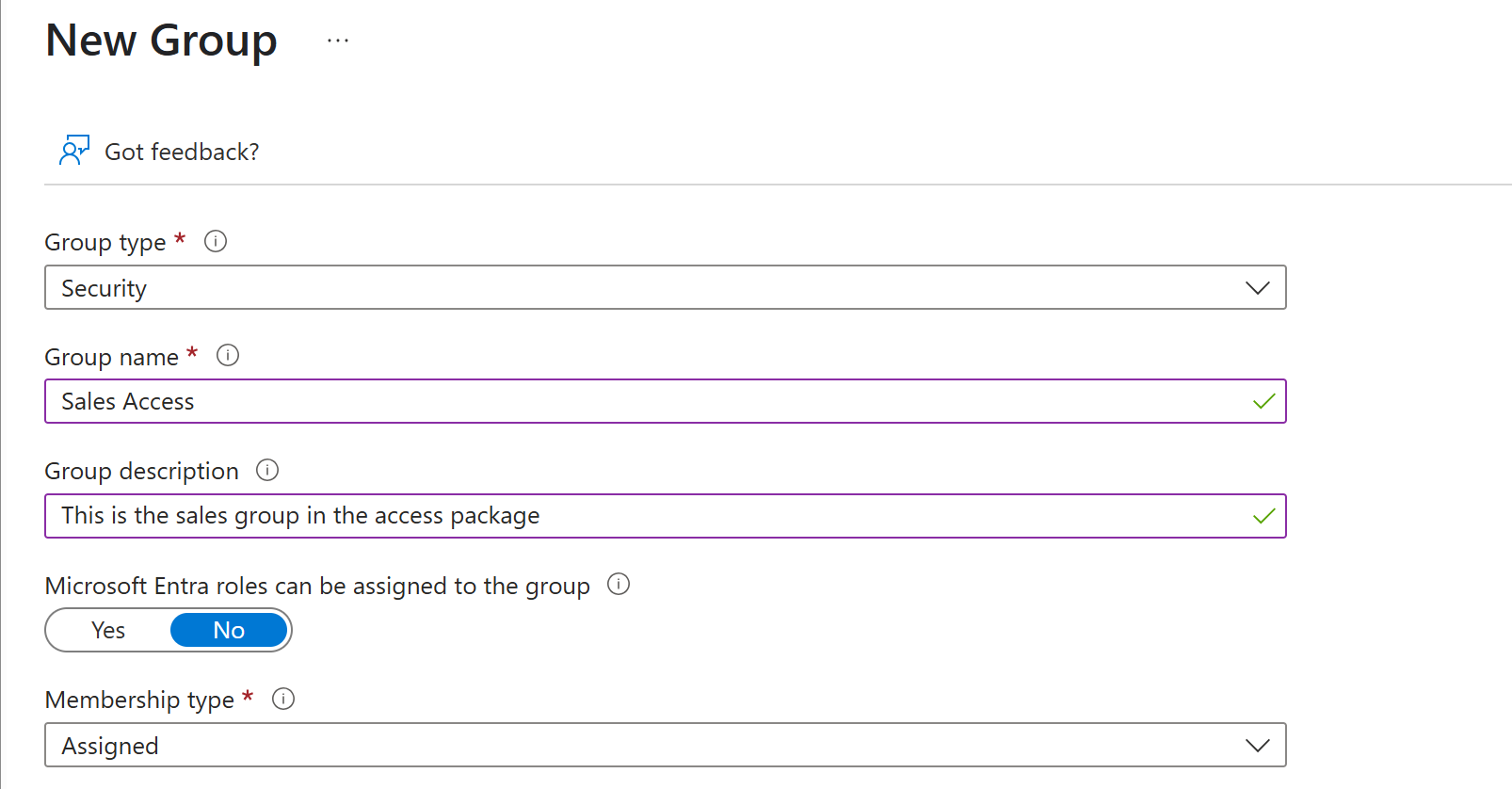
To create a group, you'd do the following steps:
Sign in to the Microsoft Entra admin center as at least an User Administrator.
Browse to Entra ID > Groups > All groups.
Select New group.
Give the group a name and description and then complete the other required options:
Select Create.
Enable management of group with PIM
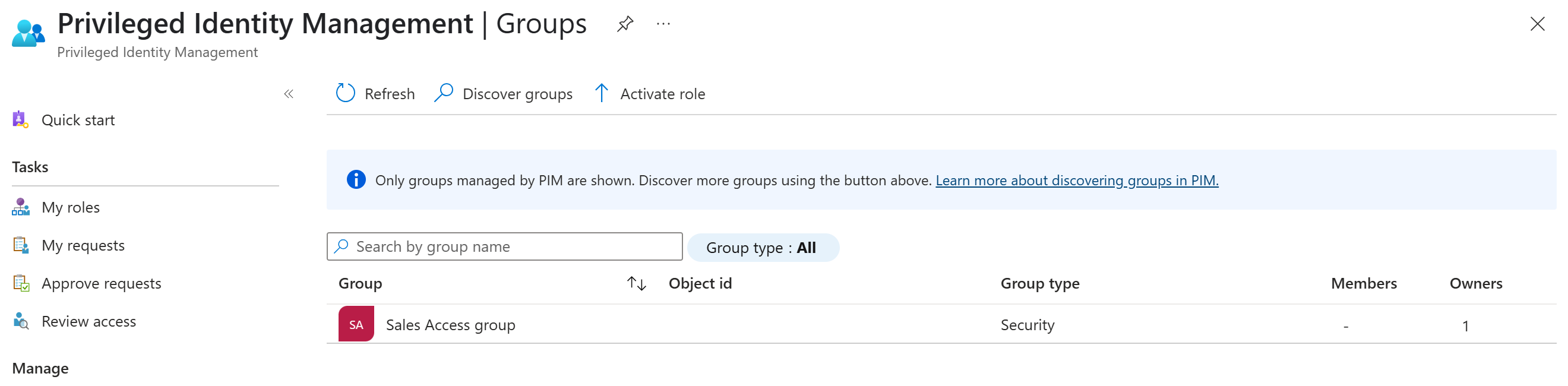
To enable PIM management for the group, you'd do the following steps:
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to ID Governance > Privileged Identity Management > Groups.
Select Discover groups and select a group that you want to bring under management with PIM.
Select Manage groups and OK.
Select Groups to return to the list of groups enabled in PIM for Groups, and notice the group you added is now on the list.
Important
Once a group is managed, it can't be taken out of management. This prevents another resource administrator from removing PIM settings. If a group is deleted from Microsoft Entra ID, it can take up to 24 hours for the group to be removed from the PIM for Groups option.
Add the resource to an access package
Once the resource is managed by PIM, eligible roles can be added as its role assignment in an access package. To verify this, do the following:
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
Tip
Other least privileged roles that can complete this task include the Catalog owner and the Access package manager.
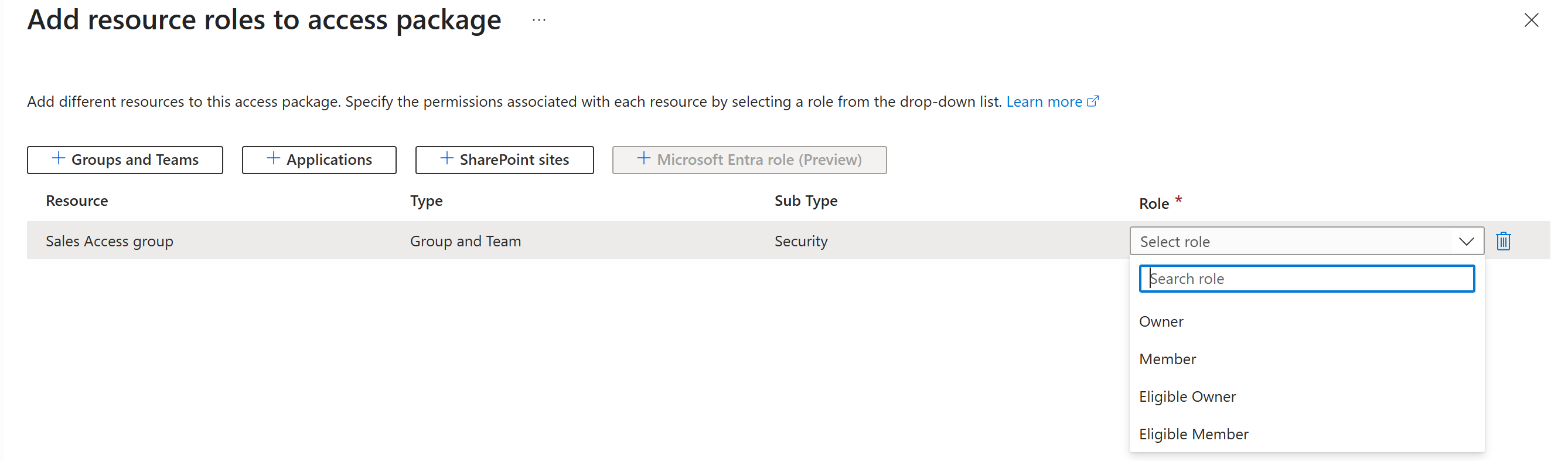
Browse to ID Governance > Entitlement management > Access package.
On the Access packages page, open the access package you want to add resource roles to.
In the left menu, select Resource roles.
Select Add resource roles to open the Add resource roles to access package page.
On the resource roles page, select Groups and Teams.
Select the group you want to add, and under roles verify that you can assign both active and eligible roles. After choosing the role, select Next.
When you're finished filling in required Requests information, go to Lifecycle.
Verify the Access Package expiration period doesn't exceed the Expire eligible assignments after setting in the PIM managed group.
Note
If an Access Package expiration period exceeds the "Expire eligible assignments after" policy setting in the PIM managed group, it can cause discrepancies between Entitlement Management and Privileged Identity Management, leading to identities losing access while EM shows they're still assigned. For more information, see: Using groups managed by Privileged Identity Management with access packages reference.