Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft is enhancing security by disabling TLS versions 1.0 and 1.1 as communicated on November 10, 2023. While the Microsoft implementation of TLS 1.0 and TLS 1.1 versions isn't known to have vulnerabilities, TLS 1.2 or later versions provide improved security features, including perfect forward secrecy and stronger cipher suites. This change helps protect customer data and ensures compliance with industry standards.
Microsoft Entra Domain Services supports TLS versions 1.0 and 1.1, but they're disabled by default. Domain Services has removed the ability to disable TLS 1.2 Only Mode. Customers who disable TLS 1.2 Only Mode can enable it.
You can use the Azure portal or PowerShell to enable TLS 1.2 Only Mode.
Prerequisites
You need the Application Administrator and Groups Administrator roles in Microsoft Entra ID to change security settings such as TLS 1.2 Only Mode.
Identify applications that use deprecated TLS versions
Before you enable TLS 1.2 Only Mode, it's important to identify applications that still use TLS 1.0 or 1.1, and update them or replace them with alternatives that support TLS 1.2. For more information about apps that are expected to be impacted, see TLS 1.0 and TLS 1.1 deprecation in Windows.
Sign in to the Microsoft Entra admin center as an Application Administrator and a Groups Administrator.
Search for Domain Services, and select your Domain Services instance.
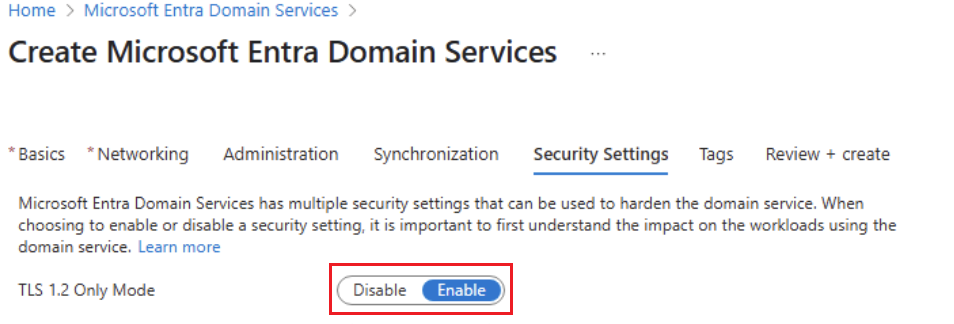
Select Security Settings.
If TLS 1.2 Only Mode is set to Disable, the instance enables TLS versions 1.0 and 1.1. Set TLS 1.2 Only Mode to Enable, and then click Save.
This change may take about 10 minutes to complete as domain security updates are enforced.
Note
Until June 30, 2026, you can select Disable to temporarily allow legacy TLS traffic while you update or replace apps that might fail. Select Enable again to remain compliant.