Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Controlling outbound network access is an important part of an overall network security plan. For example, you might want to limit access to web sites. Or, you might want to limit the outbound IP addresses and ports that can be accessed.
One way you can control outbound network access from an Azure subnet is with Azure Firewall. With Azure Firewall, you can configure:
- Application rules that define fully qualified domain names (FQDNs) that can be accessed from a subnet.
- Network rules that define source address, protocol, destination port, and destination address.
Network traffic is subjected to the configured firewall rules when you route your network traffic to the firewall as the subnet default gateway.
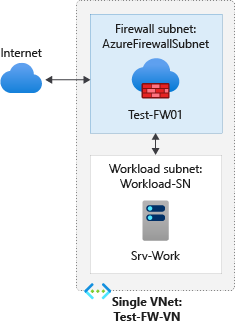
For this article, you create a simplified single virtual network with two subnets for easy deployment.
For production deployments, a hub and spoke model is recommended, where the firewall is in its own virtual network. The workload servers are in peered virtual networks in the same region with one or more subnets.
- AzureFirewallSubnet - the firewall is in this subnet.
- Workload-SN - the workload server is in this subnet. This subnet's network traffic goes through the firewall.
In this article, you learn how to:
- Set up a test network environment
- Deploy a firewall
- Create a default route
- Configure an application rule to allow access to www.qq.com
- Configure a network rule to allow access to external DNS servers
- Configure a NAT rule to allow a remote desktop to the test server
- Test the firewall
Note
This article uses classic Firewall rules to manage the firewall. The preferred method is to use Firewall Policy. To complete this procedure using Firewall Policy, see Tutorial: Deploy and configure Azure Firewall and policy using the Azure portal
If you prefer, you can complete this procedure using Azure PowerShell.
Prerequisites
If you don't have an Azure subscription, create a trial subscription before you begin.
Set up the network
First, create a resource group to contain the resources needed to deploy the firewall. Then create a virtual network, subnets, and a test server.
Create a resource group
The resource group contains all the resources used in this procedure.
- Sign in to the Azure portal.
- On the Azure portal menu, select Resource groups or search for and select Resource groups from any page. Then select Create.
- For Subscription, select your subscription.
- For Resource group name, type Test-FW-RG.
- For Region, select a region. All other resources that you create must be in the same region.
- Select Review + create.
- Select Create.
Create a virtual network
This virtual network has two subnets.
Note
The size of the AzureFirewallSubnet subnet is /26. For more information about the subnet size, see Azure Firewall FAQ.
- On the Azure portal menu or from the Home page, search for Virtual networks.
- Select Virtual networks in the result pane.
- Select Create.
- For Subscription, select your subscription.
- For Resource group, select Test-FW-RG.
- For Virtual network name, type Test-FW-VN.
- For Region, select the same region that you used previously.
- Select Next.
- On the Security tab, select Enable Azure Firewall.
- For Azure Firewall name, type Test-FW01.
- For Azure Firewall public IP address, select Create a public IP address.
- For Name, type fw-pip and select OK.
- Select Next.
- For Address space, accept the default 10.0.0.0/16.
- Under Subnets, select default and change the Name to Workload-SN.
- For Starting address, change it to 10.0.2.0/24.
- Select Save.
- Select Review + create.
- Select Create.
Note
Azure Firewall uses public IPs as needed based on available ports. After randomly selecting a public IP to connect outbound from, it will only use the next available public IP after no more connections can be made from the current public IP. In scenarios with high traffic volume and throughput, it's recommended to use a NAT Gateway to provide outbound connectivity. SNAT ports are dynamically allocated across all public IPs associated with NAT Gateway. To learn more, see Scale SNAT ports with Azure NAT Gateway.
Create a virtual machine
Now create the workload virtual machine, and place it in the Workload-SN subnet.
On the Azure portal menu or from the Home page, select Create a resource.
Select Windows Server 2019 Datacenter.
Enter these values for the virtual machine:
Setting Value Resource group Test-FW-RG Virtual machine name Srv-Work Region Same as previous Image Windows Server 2019 Datacenter Administrator user name Type a user name Password Type a password Under Inbound port rules, Public inbound ports, select None.
Accept the other defaults and select Next: Disks.
Accept the disk defaults and select Next: Networking.
Make sure that Test-FW-VN is selected for the virtual network and the subnet is Workload-SN.
For Public IP, select None.
Accept the other defaults and select Next: Management.
Accept the defaults and select Next: Monitoring.
For Boot diagnostics, select Disable to disable boot diagnostics. Accept the other defaults and select Review + create.
Review the settings on the summary page, and then select Create.
After the deployment is complete, select Go to resource and note the Srv-Work private IP address that you'll need to use later.
Note
Azure provides a default outbound access IP for VMs that either aren't assigned a public IP address or are in the backend pool of an internal basic Azure load balancer. The default outbound access IP mechanism provides an outbound IP address that isn't configurable.
The default outbound access IP is disabled when one of the following events happens:
- A public IP address is assigned to the VM.
- The VM is placed in the backend pool of a standard load balancer, with or without outbound rules.
- An Azure NAT Gateway resource is assigned to the subnet of the VM.
VMs that you create by using virtual machine scale sets in flexible orchestration mode don't have default outbound access.
For more information about outbound connections in Azure, see Default outbound access in Azure and Use Source Network Address Translation (SNAT) for outbound connections.
Examine the firewall
- Go to the resource group and select the firewall.
- Note the firewall private and public IP addresses. You use these addresses later.
Create a default route
When you create a route for outbound and inbound connectivity through the firewall, a default route to 0.0.0.0/0 with the virtual appliance private IP as a next hop is sufficient. This directs any outgoing and incoming connections through the firewall. As an example, if the firewall is fulfilling a TCP-handshake and responding to an incoming request, then the response is directed to the IP address who sent the traffic. This is by design.
As a result, there's no need create another user defined route to include the AzureFirewallSubnet IP range. This might result in dropped connections. The original default route is sufficient.
For the Workload-SN subnet, configure the outbound default route to go through the firewall.
- On the Azure portal, search for Route tables.
- Select Route tables in the results pane.
- Select Create.
- For Subscription, select your subscription.
- For Resource group, select Test-FW-RG.
- For Region, select the same location that you used previously.
- For Name, type Firewall-route.
- Select Review + create.
- Select Create.
After deployment completes, select Go to resource.
On the Firewall-route page, select Subnets and then select Associate.
For Virtual network, select Test-FW-VN.
For Subnet, select Workload-SN. Make sure that you select only the Workload-SN subnet for this route, otherwise your firewall won't work correctly.
Select OK.
Select Routes and then select Add.
For Route name, type fw-dg.
For Destination type, select IP Addresses.
For Destination IP addresses/CIDR ranges, type 0.0.0.0/0.
For Next hop type, select Virtual appliance.
Azure Firewall is actually a managed service, but virtual appliance works in this situation.
For Next hop address, type the private IP address for the firewall that you noted previously.
Select Add.
Configure a network rule
This is the network rule that allows outbound access to two IP addresses at port 53 (DNS).
Select the Network rule collection tab.
Select Add network rule collection.
For Name, type Net-Coll01.
For Priority, type 200.
For Action, select Allow.
Under Rules, IP addresses, for Name, type Allow-DNS.
For Protocol, select UDP.
For Source type, select IP address.
For Source, type 10.0.2.0/24.
For Destination type select IP address.
For Destination address, type 209.244.0.3,209.244.0.4
These addresses are public DNS servers operated by Level3.
For Destination Ports, type 53.
Select Add.
Configure a DNAT rule
This rule allows you to connect a remote desktop to the Srv-Work virtual machine through the firewall.
- Select the NAT rule collection tab.
- Select Add NAT rule collection.
- For Name, type rdp.
- For Priority, type 200.
- Under Rules, for Name, type rdp-nat.
- For Protocol, select TCP.
- For Source type, select IP address.
- For Source, type *.
- For Destination address, type the firewall public IP address.
- For Destination Ports, type 3389.
- For Translated address, type the Srv-work private IP address.
- For Translated port, type 3389.
- Select Add.
Change the primary and secondary DNS address for the Srv-Work network interface
For testing purposes, configure the server's primary and secondary DNS addresses. This isn't a general Azure Firewall requirement.
- On the Azure portal menu, select Resource groups or search for and select Resource groups from any page. Select the Test-FW-RG resource group.
- Select the network interface for the Srv-Work virtual machine.
- Under Settings, select DNS servers.
- Under DNS servers, select Custom.
- Type 209.244.0.3 and press Enter in the Add DNS server text box, and 209.244.0.4 in the next text box.
- Select Save.
- Restart the Srv-Work virtual machine.
Test the firewall
Now, test the firewall to confirm that it works as expected.
Connect a remote desktop to firewall public IP address and sign in to the Srv-Work virtual machine.
Open Internet Explorer and browse to
https://www.qq.com.Select OK > Close on the Internet Explorer security alerts.
You should see the QQ home page.
Browse to
https://www.microsoft.com.The firewall should block you.
So now you verified that the firewall rules are working:
- You can connect to the virtual machine using RDP.
- You can browse to the one allowed FQDN, but not to any others.
- You can resolve DNS names using the configured external DNS server.
Clean up resources
You can keep your firewall resources to continue testing, or if no longer needed, delete the Test-FW-RG resource group to delete all firewall-related resources.