Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
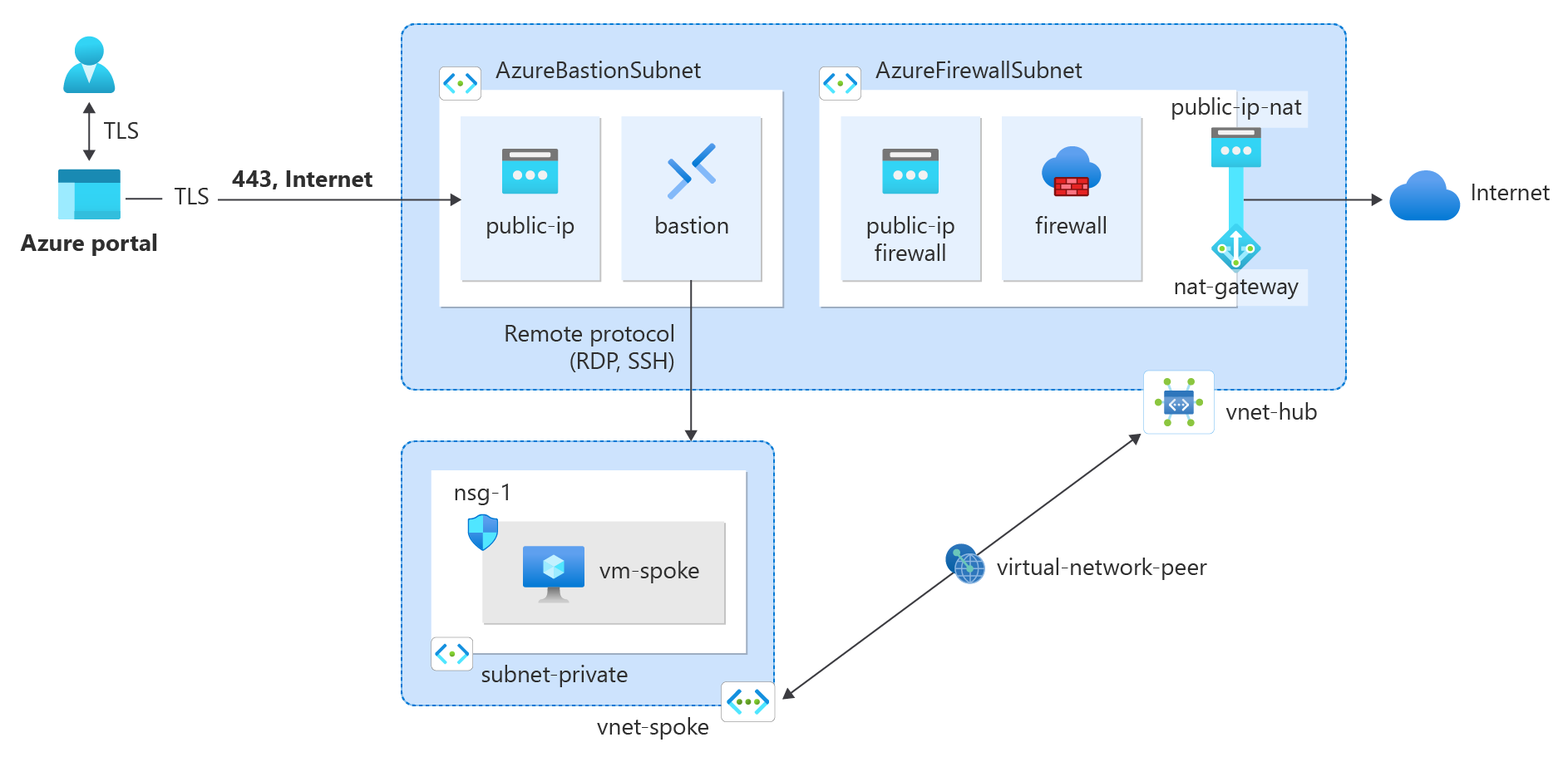
In this tutorial, you learn how to integrate a NAT gateway with Azure Firewall in a hub and spoke network for enhanced outbound connectivity and scalability.
Azure Firewall provides 2,496 SNAT ports per public IP address configured per backend Virtual Machine Scale Set instance (minimum of two instances). You can associate up to 250 public IP addresses to Azure Firewall. Depending on your architecture requirements and traffic patterns, you might require more SNAT ports than what Azure Firewall can provide. You might also require the use of fewer public IPs while also requiring more SNAT ports. A better method for outbound connectivity is to use NAT gateway. NAT gateway provides 64,512 SNAT ports per public IP address and can be used with up to 16 public IP addresses.
NAT gateway can be integrated with Azure Firewall by configuring NAT gateway directly to the Azure Firewall subnet. This association provides a more scalable method of outbound connectivity. For production deployments, a hub and spoke network is recommended, where the firewall is in its own virtual network. The workload servers are peered virtual networks in the same region as the hub virtual network where the firewall resides. In this architectural setup, NAT gateway can provide outbound connectivity from the hub virtual network for all spoke virtual networks peered.
Note
While you can deploy NAT Gateway in a hub and spoke virtual network architecture as described in this tutorial, NAT Gateway isn't supported in the hub virtual network of a vWAN architecture. To use in a vWAN architecture, NAT Gateway must be configured directly to the spoke virtual networks associated with the secured virtual hub (vWAN). For more information about Azure Firewall architecture options, see What are the Azure Firewall Manager architecture options?
In this tutorial, you learn how to:
- Create a hub virtual network and deploy an Azure Firewall and Azure Bastion during deployment
- Create a NAT gateway and associate it with the firewall subnet in the hub virtual network
- Create a spoke virtual network
- Create a virtual network peering
- Create a route table for the spoke virtual network
- Create a firewall policy for the hub virtual network
- Create a virtual machine to test the outbound connectivity through the NAT gateway
Prerequisites
- An Azure account with an active subscription. Create an account for trial.
Create a resource group
Create a resource group to contain all resources for this quickstart.
Sign in to the Azure portal.
In the search box at the top of the portal enter Resource group. Select Resource groups in the search results.
Select + Create.
In the Basics tab of Create a resource group, enter, or select the following information.
Setting Value Subscription Select your subscription Resource group test-rg Region China North 3 Select Review + create.
Select Create.
Create the hub virtual network
The hub virtual network contains the firewall subnet that is associated with the Azure Firewall and NAT gateway. Use the following example to create the hub virtual network.
Sign in to the Azure portal.
In the search box at the top of the Azure portal, enter Virtual network. Select Virtual networks in the search results.
Select Create.
Enter or select the following information in the Basics tab of Create virtual network.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg or your resource group. Instance details Name Enter vnet-hub. Region Select your region. This example uses China North 3. Select the IP Addresses tab, or select Next: Security, then Next: IP Addresses.
In Subnets select the default subnet.
Enter or select the following information in Edit subnet.
Setting Value Subnet purpose Leave the default. Name Enter subnet-1. Leave the rest of the settings as default, then select Save.
Select + Add a subnet.
In Add a subnet enter or select the following information.
Setting Value Subnet purpose Select Azure Bastion. Leave the rest of the settings as default, then select Add.
Select + Add a subnet.
In Add a subnet enter or select the following information.
Setting Value Subnet purpose Select Azure Firewall. Leave the rest of the settings as default, then select Add.
Select Review + create, then select Create.
Create Azure Bastion host
Azure Bastion provides secure RDP and SSH connectivity to virtual machines over TLS without requiring public IP addresses on the VMs.
In the search box at the top of the Azure portal, enter Bastion. Select Bastions in the search results.
Select Create.
Enter or select the following information in the Basics tab of Create a Bastion.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg or your resource group. Instance details Name Enter bastion. Region Select your region. This example uses China North 3. Tier Select Developer. Virtual network Select vnet-1. Subnet Select AzureBastionSubnet. Select Review + create, then select Create.
Create Azure Firewall
In the search box at the top of the portal, enter Firewall. Select Firewalls in the search results.
Select + Create.
On the Create a Firewall page, use the following table to configure the firewall:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Name Enter firewall. Region Select China North 3. Availability zone Accept the default None. Firewall SKU Select Standard. Firewall management Select Use a Firewall Policy to manage this firewall. Firewall policy Select Add new.
Name: Enter firewall-policy.
Region: Select China North 3.
Policy tier: Standard.
Select OK.Choose a virtual network Virtual network Select Use existing. Virtual network Select vnet-hub. Public IP address Public IP address Select Add new.
Name: Enter public-ip-firewall.
SKU: Standard.
Assignment: Static.
Availability zone: Zone-redundant.
Select OK.Accept the other default values, then select Review + create.
Review the summary, and then select Create to create the firewall.
The firewall takes a few minutes to deploy.
After deployment completes, go to the test-rg resource group, and select the firewall resource.
Note the firewall private and public IP addresses. You use these addresses later.
Create the NAT gateway
All outbound internet traffic traverses the NAT gateway to the internet. Use the following example to create a NAT gateway for the hub and spoke network and associate it with the AzureFirewallSubnet.
In the search box at the top of the portal, enter Public IP address. Select Public IP addresses in the search results.
Select + Create.
Enter the following information in Create public IP address.
Setting Value Subscription Select your subscription. Resource group Select test-rg. Region Select China North 3. Name Enter public-ip-nat. IP version Select IPv4. SKU Select Standard. Availability zone Select Zone-redundant. Tier Select Regional. Select Review + create and then select Create.
In the search box at the top of the portal, enter NAT gateway. Select NAT gateways in the search results.
Select + Create.
Enter or select the following information in the Basics tab of Create network address translation (NAT) gateway.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details NAT gateway name Enter nat-gateway. Region Select China North 3. Availability zone Select a Zone or No zone. TCP idle timeout (minutes) Leave the default of 4. Select Next.
In the Outbound IP tab, select public IP addresses or prefixes.
Select Next.
In the Subnet tab, in Virtual network, select vnet-hub.
Select specific subnets, select AzureFirewallSubnet.
Select Review + create, then select Create.
Create spoke virtual network
The spoke virtual network contains the test virtual machine used to test the routing of the internet traffic to the NAT gateway. Use the following example to create the spoke network.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select + Create.
In the Basics tab of Create virtual network, enter, or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Name Enter vnet-spoke. Region Select China North 3. Select Next to proceed to the Security tab.
Select Next to proceed to the IP addresses tab.
In the IP Addresses tab in IPv4 address space, select Delete address space to delete the address space that is auto populated.
Select + Add IPv4 address space.
In IPv4 address space enter 10.1.0.0. Leave the default of /16 (65,536 addresses) in the mask selection.
Select + Add a subnet.
In Add a subnet enter or select the following information:
Setting Value Subnet purpose Leave the default Default. Name Enter subnet-private. IPv4 IPv4 address range Leave the default of 10.1.0.0/16. Starting address Leave the default of 10.1.0.0. Size Leave the default of /24(256 addresses). Select Add.
Select Review + create.
Select Create.
Create peering between the hub and spoke
A virtual network peering is used to connect the hub to the spoke and the spoke to the hub. Use the following example to create a two-way network peering between the hub and spoke.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select vnet-hub.
Select Peerings in Settings.
Select + Add.
Enter or select the following information in Add peering:
Setting Value Remote virtual network summary Peering link name Enter vnet-spoke-to-vnet-hub. Virtual network deployment model Leave the default of Resource manager. Subscription Select your subscription. Virtual network Select vnet-spoke (test-rg). Remote virtual network peering settings Allow 'vnet-spoke' to access 'vnet-hub' Leave the default of Selected. Allow 'vnet-spoke' to receive forwarded traffic from 'vnet-hub' Select the checkbox. Allow gateway or route server in 'vnet-spoke' to forward traffic to 'vnet-hub' Leave the default of Unselected. Enable 'vnet-spoke' to use 'vnet-hub's' remote gateway or route server Leave the default of Unselected. Local virtual network summary Peering link name Enter vnet-hub-to-vnet-spoke. Local virtual network peering settings Allow 'vnet-hub' to access 'vnet-spoke' Leave the default of Selected. Allow 'vnet-hub' to receive forwarded traffic from 'vnet-spoke' Select the checkbox. Allow gateway or route server in 'vnet-hub' to forward traffic to 'vnet-spoke' Leave the default of Unselected. Enable 'vnet-hub' to use 'vnet-spoke's' remote gateway or route server Leave the default of Unselected. Select Add.
Select Refresh and verify Peering status is Connected.
Create spoke network route table
A route table forces all traffic leaving the spoke virtual network to the hub virtual network. The route table is configured with the private IP address of the Azure Firewall as the virtual appliance.
Obtain private IP address of firewall
The private IP address of the firewall is needed for the route table created later in this article. Use the following example to obtain the firewall private IP address.
In the search box at the top of the portal, enter Firewall. Select Firewalls in the search results.
Select firewall.
In the Overview of firewall, note the IP address in the field Firewall private IP. The IP address in this example is 10.0.1.68.
Create route table
Create a route table to force all inter-spoke and internet egress traffic through the firewall in the hub virtual network.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select + Create.
In Create Route table enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Region Select China North 3. Name Enter route-table-spoke. Propagate gateway routes Select No. Select Review + create.
Select Create.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select route-table-spoke.
In Settings select Routes.
Select + Add in Routes.
Enter or select the following information in Add route:
Setting Value Route name Enter route-to-hub. Destination type Select IP Addresses. Destination IP addresses/CIDR ranges Enter 0.0.0.0/0. Next hop type Select Virtual appliance. Next hop address Enter 10.0.1.68. Select Add.
Select Subnets in Settings.
Select + Associate.
Enter or select the following information in Associate subnet:
Setting Value Virtual network Select vnet-spoke (test-rg). Subnet Select subnet-private. Select OK.
Configure firewall
Traffic from the spoke through the hub must be allowed through and firewall policy and a network rule. Use the following example to create the firewall policy and network rule.
Configure network rule
In the search box at the top of the portal, enter Firewall. Select Firewall Policies in the search results.
Select firewall-policy.
Expand Settings then select Network rules.
Select + Add a rule collection.
In Add a rule collection enter or select the following information:
Setting Value Name Enter spoke-to-internet. Rule collection type Select Network. Priority Enter 100. Rule collection action Select Allow. Rule collection group Select DefaultNetworkRuleCollectionGroup. Rules Name Enter allow-web. Source type IP Address. Source Enter 10.1.0.0/24. Protocol Select TCP. Destination Ports Enter 80,443. Destination Type Select IP Address. Destination Enter * Select Add.
Create test virtual machine
An Ubuntu virtual machine is used to test the outbound internet traffic through the NAT gateway. Use the following example to create an Ubuntu virtual machine.
In the portal, search for and select Virtual machines.
In Virtual machines, select + Create, then Azure virtual machine.
On the Basics tab of Create a virtual machine, enter, or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Virtual machine name Enter vm-spoke. Region Select China North 3. Availability options Select No infrastructure redundancy required. Security type Leave the default of Standard. Image Select Ubuntu Server 24.04 LTS - Gen2. Size Select a size. Administrator account Authentication type Select SSH public key. Username Enter azureuser. SSH public key source Select Generate new key pair. Key pair name Enter vm-spoke-key. Inbound port rules Public inbound ports Select None. Select the Networking tab at the top of the page or select Next:Disks, then Next:Networking.
Enter or select the following information in the Networking tab:
Setting Value Network interface Virtual network Select vnet-spoke. Subnet Select subnet-private (10.1.0.0/24). Public IP Select None. NIC network security group Select Advanced. Configure network security group Select Create new.
Enter nsg-1 for the name.
Leave the rest at the defaults and select OK.Leave the rest of the settings at the defaults and select Review + create.
Review the settings and select Create.
The Generate new key pair dialog box appears. Select Download private key and create resource.
The private key downloads to your local machine. The private key is needed in later steps for connecting to the virtual machine with Azure Bastion. The name of the private key file is the name you entered in the Key pair name field. In this example, the private key file is named ssh-key.
Wait for the virtual machine to finishing deploying before proceeding to the next steps.
Note
Virtual machines in a virtual network with a bastion host don't need public IP addresses. Bastion provides the public IP, and the VMs use private IPs to communicate within the network. You can remove the public IPs from any VMs in bastion hosted virtual networks. For more information, see Dissociate a public IP address from an Azure VM.
Test NAT gateway
You connect to the Ubuntu virtual machines you created in the previous steps to verify that the outbound internet traffic is leaving the NAT gateway.
Obtain NAT gateway public IP address
Obtain the NAT gateway public IP address for verification of the steps later in the article.
In the search box at the top of the portal, enter Public IP. Select Public IP addresses in the search results.
Select public-ip-nat.
Make note of value in IP address. The example used in this article is 203.0.113.0.25.
Test NAT gateway from spoke
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-spoke.
In Overview, select Connect then Connect via Bastion.
Select SSH as the connection type. Upload your SSH private key file. Select Connect.
In the bash prompt, enter the following command:
curl ifconfig.meVerify the IP address returned by the command matches the public IP address of the NAT gateway.
azureuser@vm-1:~$ curl ifconfig.me 203.0.113.0.25Close the Bastion connection to vm-spoke.
Clean up resources
When you finish using the resources that you created, you can delete the resource group and all its resources:
In the Azure portal, search for and select Resource groups.
On the Resource groups page, select the test-rg resource group.
On the test-rg page, select Delete resource group.
Enter test-rg in Enter resource group name to confirm deletion, and then select Delete.
Next steps
Advance to the next article to learn how to integrate a NAT gateway with an Azure Load Balancer: