Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Network security group (NSG) flow logs will be retired on September 30, 2027. After June 30, 2025, you'll no longer be able to create new NSG flow logs. We recommend migrating to virtual network flow logs, which address the limitations of NSG flow logs. After the retirement date, traffic analytics enabled for NSG flow logs will no longer be supported, and existing NSG flow log resources in your subscriptions will be deleted. However, existing NSG flow log records won't be deleted from Azure Storage and will continue to follow their configured retention policies. For more information, see the official announcement.
Network security group flow logging is a feature of Azure Network Watcher that allows you to log information about IP traffic flowing through a network security group. For more information about network security group flow logging, see NSG flow logs overview.
In this article, you learn how to create, change, enable, disable, or delete a network security group flow log using the Azure portal, PowerShell, and Azure CLI.
Prerequisites
An Azure account with an active subscription. Create a trial subscription.
Insights provider. For more information, see Register Insights provider.
A network security group. If you need to create a network security group, see Create, change, or delete a network security group.
An Azure storage account. If you need to create a storage account, see Create a storage account using the Azure portal.
Register Insights provider
Microsoft.Insights provider must be registered to successfully log traffic flowing through a virtual network. If you aren't sure if the Microsoft.Insights provider is registered, check its status in the Azure portal by following these steps:
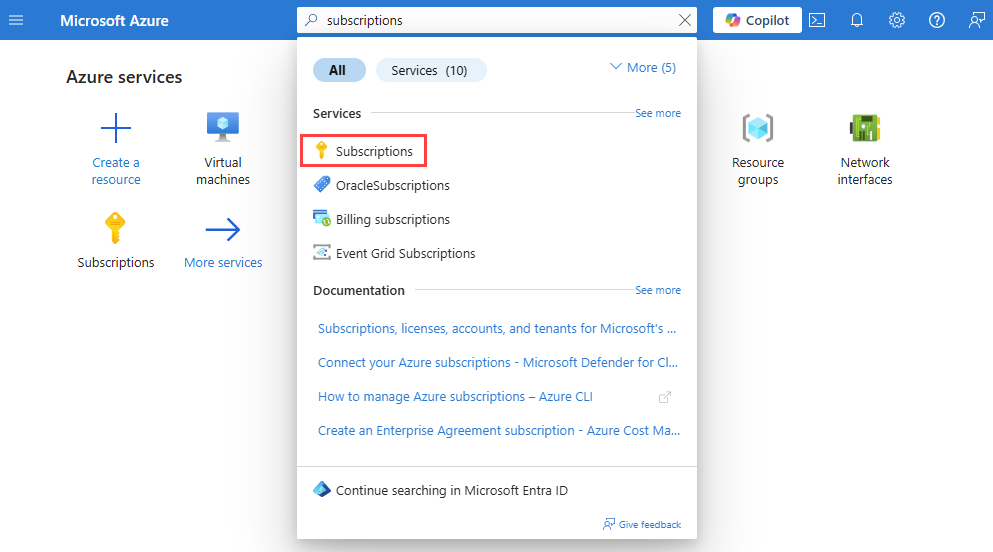
In the search box at the top of the portal, enter subscriptions. Select Subscriptions from the search results.
Select the Azure subscription that you want to enable the provider for in Subscriptions.
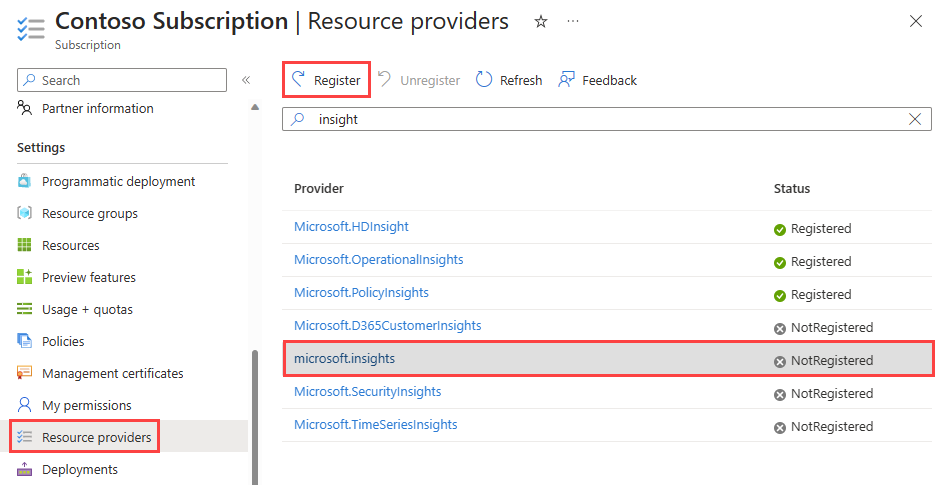
Under Settings, select Resource providers.
Enter insight in the filter box.
Confirm the status of the provider displayed is Registered. If the status is NotRegistered, select the Microsoft.Insights provider then select Register.
Create a flow log
Create a flow log for your network security group. The flow log is saved in an Azure storage account.
In the search box at the top of the portal, enter network watcher. Select Network Watcher from the search results.
Under Logs, select Flow logs.
In Network Watcher | Flow logs, select + Create or Create flow log blue button.
On the Basics tab of Create a flow log, enter or select the following values:
Setting Value Project details Subscription Select the Azure subscription of your network security group that you want to log. Flow log type Select Network security group then select + Select target resource.
Select the network security group that you want to flow log, then select Confirm selection.Flow Log Name Enter a name for the flow log or leave the default name. Azure portal uses {ResourceName}-{ResourceGroupName}-flowlog as a default name for the flow log. myNSG-myResourceGroup-flowlog is the default name used in this article. Instance details Subscription Select the Azure subscription of your storage account. Storage accounts Select the storage account that you want to save the flow logs to. If you want to create a new storage account, select Create a new storage account. Retention (days) Enter a retention time for the logs (this option is only available with Standard general-purpose v2 storage accounts). Enter 0 if you want to retain the flow logs data in the storage account forever (until you manually delete it from the storage account). For information about pricing, see Azure Storage pricing. 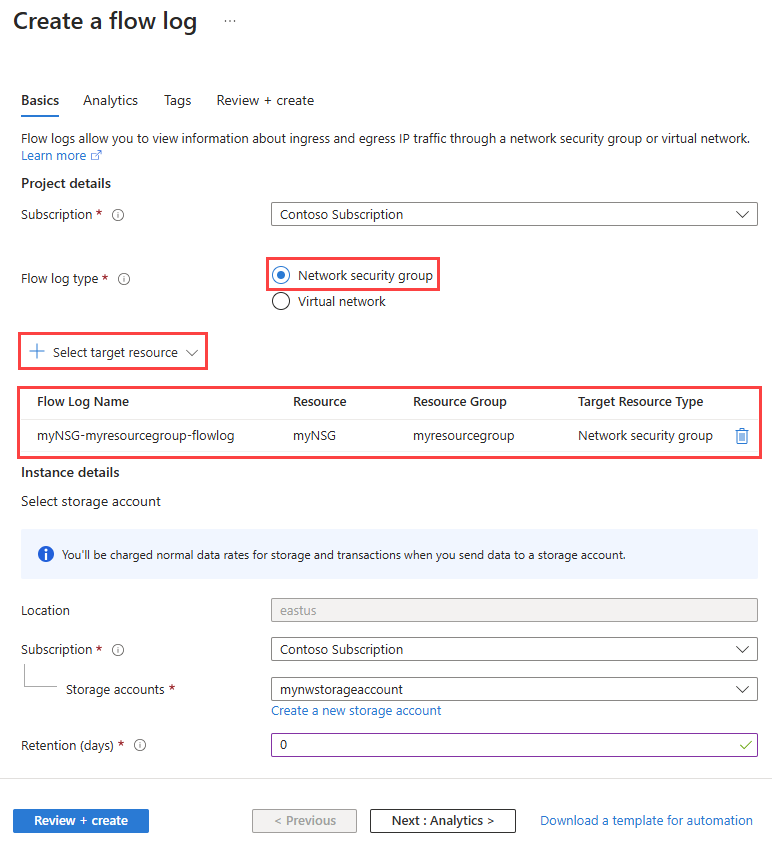
To enable traffic analytics, select Next: Analytics button, or select the Analytics tab. Enter or select the following values:
Setting Value Flow logs version Select the version of the network security group flow log, available options are: Version 1 and Version 2. The default version is version 2. For more information, see Flow logging for network security groups. Enable traffic analytics Select the checkbox to enable traffic analytics for your flow log. Traffic analytics processing interval Select the processing interval that you prefer, available options are: Every 1 hour and Every 10 mins. The default processing interval is every one hour. For more information, see Traffic analytics. Subscription Select the Azure subscription of your Log Analytics workspace. Log Analytics Workspace Select your Log Analytics workspace. By default, Azure portal creates DefaultWorkspace-{SubscriptionID}-{Region} Log Analytics workspace in defaultresourcegroup-{Region} resource group. 
Note
To create and select a Log Analytics workspace other than the default one, see Create a Log Analytics workspace
Select Review + create.
Review the settings, and then select Create.
Note
If the storage account is in a different subscription, the network security group and storage account must be associated with the same Microsoft Entra tenant. The account you use for each subscription must have the necessary permissions.
Important
The storage account must not have network rules that restrict network access to only Azure services or specific virtual networks.
Enable or disable traffic analytics
Enable traffic analytics for a flow log to analyze the flow log data. Traffic analytics provides insights into the traffic patterns of your virtual network. You can enable or disable traffic analytics for a flow log at any time.
Note
In addition to enabling or disabling traffic analytics, you can also change other flow log settings.
To enable traffic analytics for a flow log, follow these steps:
In the search box at the top of the portal, enter network watcher. Select Network Watcher from the search results.
Under Logs, select Flow logs.
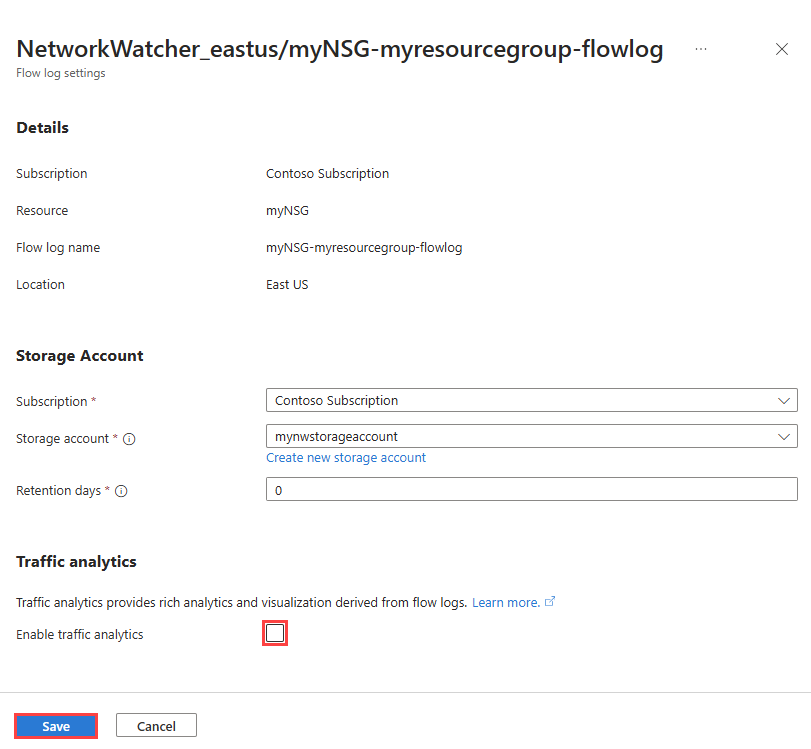
In Network Watcher | Flow logs, select the flow log that you want to enable traffic analytics for.
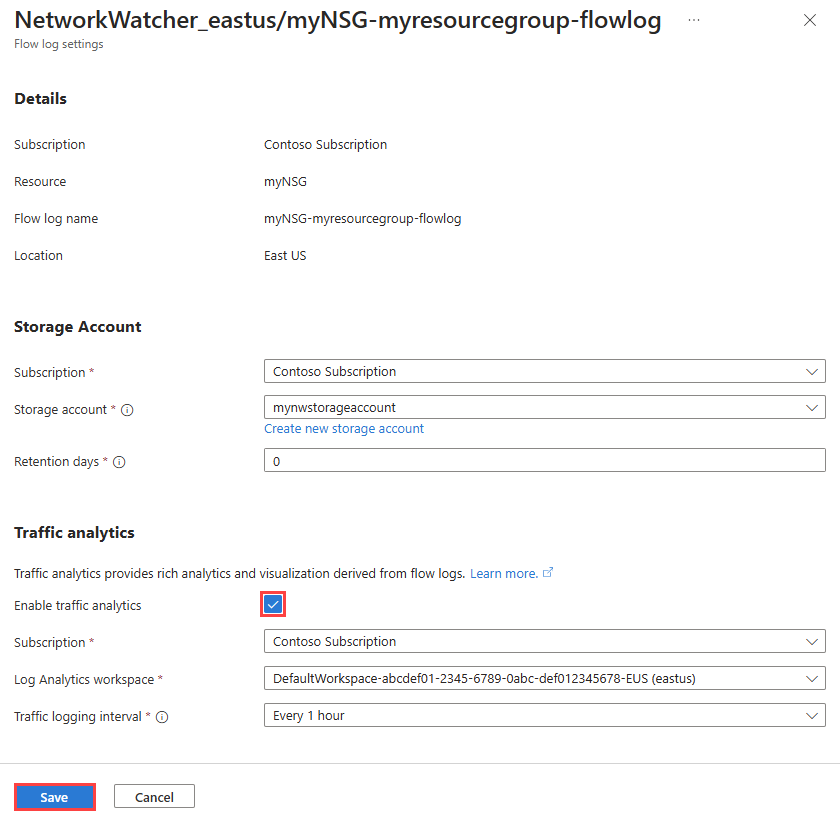
In Flow logs settings, under Traffic analytics, check the Enable traffic analytics checkbox.
Enter or select the following values:
Setting Value Subscription Select the Azure subscription of your Log Analytics workspace. Log Analytics workspace Select your Log Analytics workspace. By default, Azure portal creates DefaultWorkspace-{SubscriptionID}-{Region} Log Analytics workspace in defaultresourcegroup-{Region} resource group. Traffic logging interval Select the processing interval that you prefer, available options are: Every 1 hour and Every 10 mins. The default processing interval is every one hour. For more information, see Traffic analytics. Select Save to apply the changes.
To disable traffic analytics for a flow log, take the previous steps 1-3, then uncheck the Enable traffic analytics checkbox and select Save.
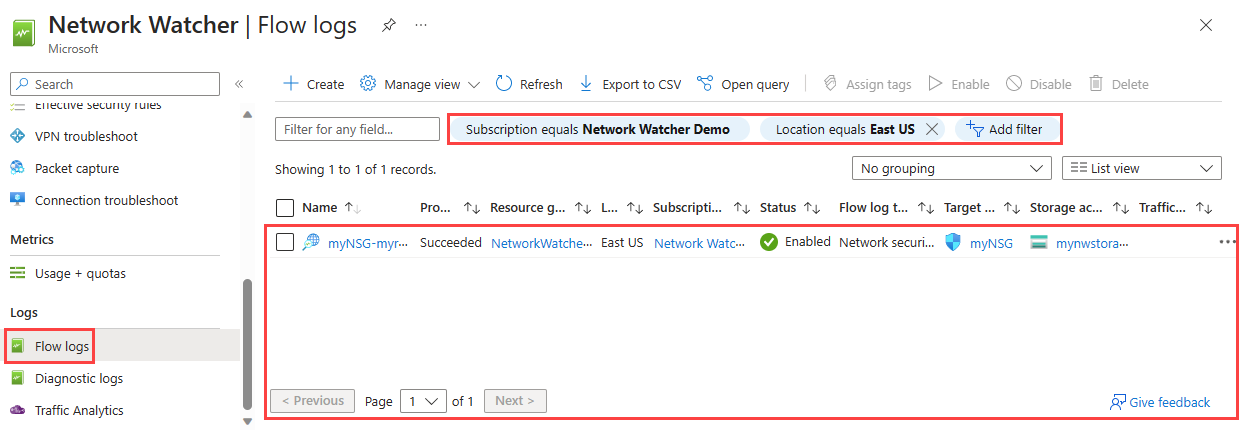
List all flow logs
You can list all flow logs in a subscription or a group of subscriptions (Azure portal). You can also list all flow logs in a region.
In the search box at the top of the portal, enter network watcher. Select Network Watcher from the search results.
Under Logs, select Flow logs.
Select Subscription equals filter to choose one or more of your subscriptions. You can apply other filters like Location equals to list all flow logs in a region.
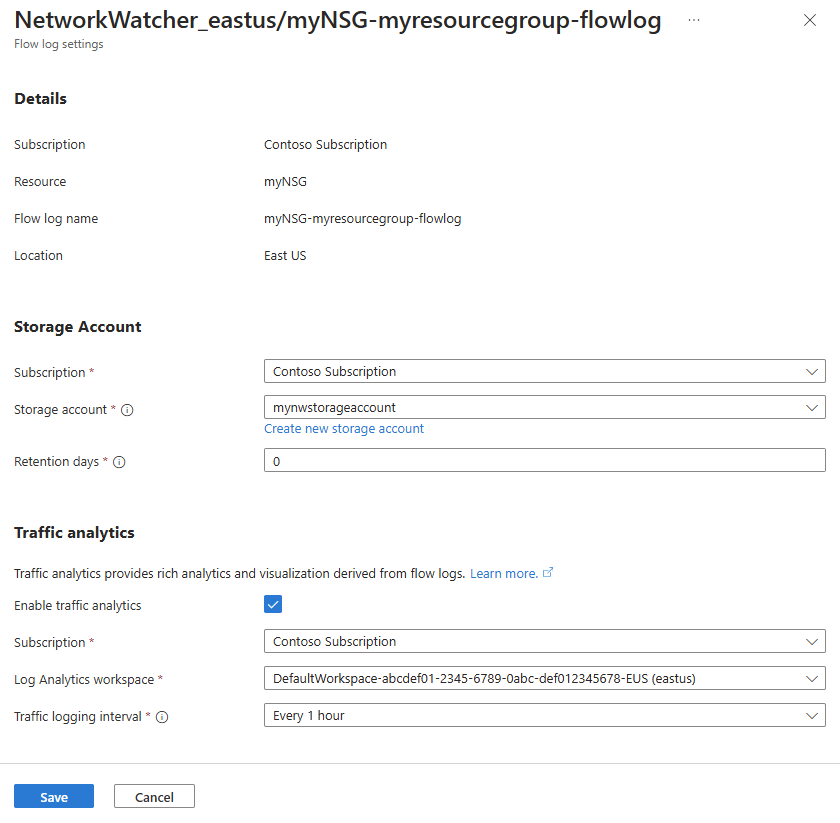
View details of a flow log resource
You can view the details of a flow log.
In the search box at the top of the portal, enter network watcher. Select Network Watcher from the search results.
Under Logs, select Flow logs.
In Network Watcher | Flow logs, select the flow log that you want to see.
In Flow logs settings, you can view the settings of the flow log resource.
Select Cancel to close the settings page without making changes.
Download a flow log
You can download the flow logs data from the storage account that you saved the flow logs to.
In the search box at the top of the portal, enter storage accounts. Select Storage accounts from the search results.
Select the storage account you used to store the logs.
Under Data storage, select Containers.
Select the insights-logs-networksecuritygroupflowevent container.
In insights-logs-networksecuritygroupflowevent, navigate the folder hierarchy until you get to the
PT1H.jsonfile that you want to download. NSG flow log files follow the following path:https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-networksecuritygroupflowevent/resourceId=/SUBSCRIPTIONS/{subscriptionID}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/{NetworkSecurityGroupName}/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.jsonSelect the ellipsis ... to the right of the
PT1H.jsonfile, then select Download.
Note
As an alternative way to access and download flow logs from your storage account, you can use Azure Storage Explorer. For more information, see Get started with Storage Explorer and Download blobs using Storage Explorer.
For information about the structure of a flow log, see Log format of NSG flow logs.
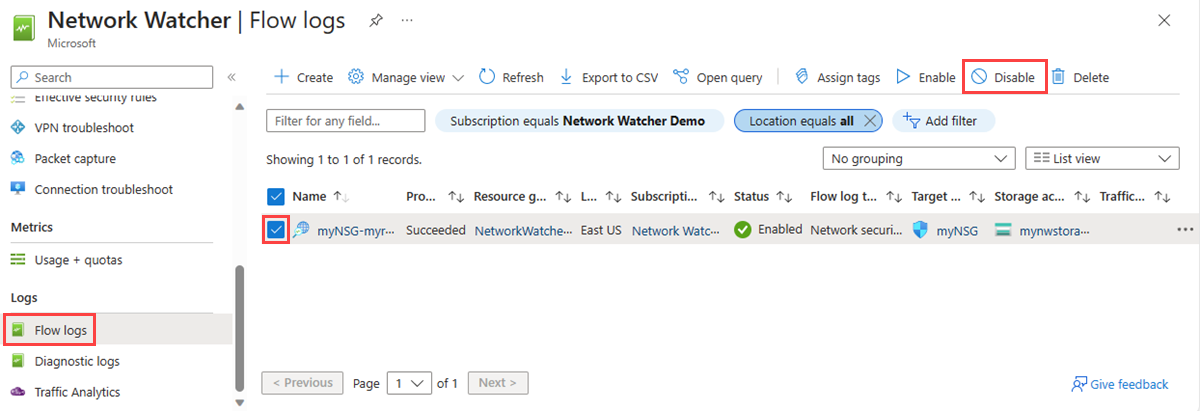
Disable a flow log
You can temporarily disable a flow log without deleting it. Disabling a flow log stops flow logging for the associated network security group. However, the flow log resource remains with all its settings and associations. You can re-enable it at any time to resume flow logging for the configured network security group.
Note
If traffic analytics is enabled for a flow log, it must disabled before you can disable the flow log. To disable traffic analytics, see Enable or disable traffic analytics.
Delete a flow log
You can permanently delete a virtual network flow log. Deleting a flow log deletes all its settings and associations. To begin flow logging again for the same resource, you must create a new flow log for it.
Note
Deleting a flow log does not delete the flow log data from the storage account. Flow logs data stored in a storage account follows the configured retention policy or stays stored in the storage account until manually deleted.