Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Sentinel features will be officially retired in Azure in China regions on August 18, 2026 per the announcement posted by 21Vianet.
If you no longer want to use Microsoft Sentinel, this article explains how to remove it from your Log Analytics workspace.
Prerequisites
Before you begin, make sure that you understand the effects of removing Microsoft Sentinel from your environment.
For example, you can't manage Microsoft Sentinel tables in Log Analytics after removing Microsoft Sentinel, such as to set extended data retention. Therefore, to avoid extra data retention charges, we recommend that you set per-table retention to 90 days or less for Microsoft Sentinel tables stored in Log Analytics that will be inaccessible after removing Microsoft Sentinel.
For more information, see Implications of removing Microsoft Sentinel from your workspace.
Remove Microsoft Sentinel
Complete the following steps to remove Microsoft Sentinel from your Log Analytics workspace.
For Microsoft Sentinel in the Azure portal, under Configuration, select Settings.
On the Settings page, select the Settings tab.Select Remove Microsoft Sentinel.
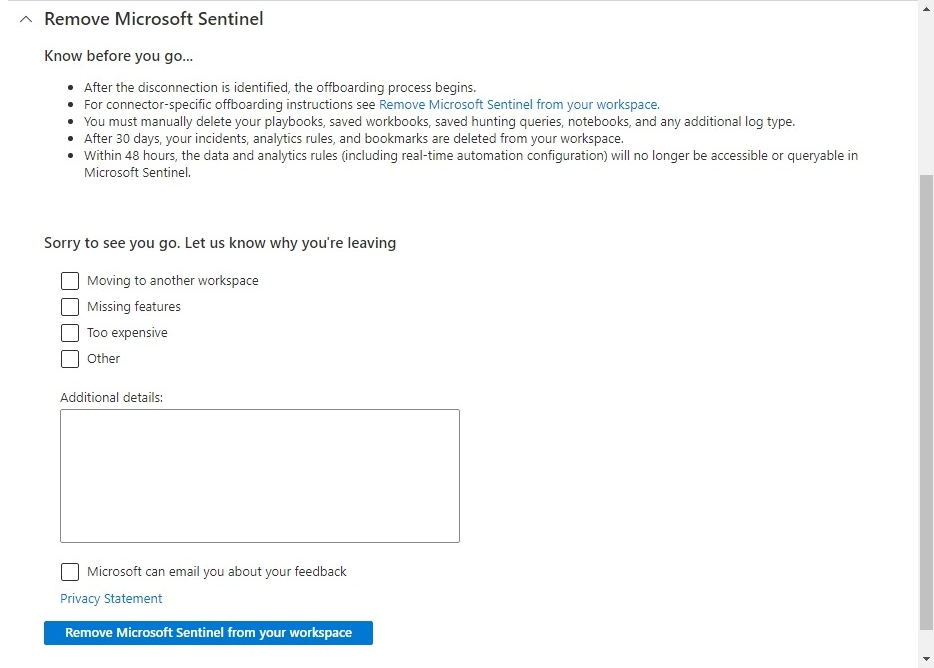
Review the Know before you go... section and the rest of this document carefully. Take all the necessary actions before proceeding.
Select the appropriate checkboxes to let us know why you're removing Microsoft Sentinel. Enter any other details in the space provided, and indicate whether you want Microsoft to email you in response to your feedback.
Select Remove Microsoft Sentinel from your workspace.
Clean up resources in the Azure portal (optional)
If you don't want to keep the workspace and the data collected for Microsoft Sentinel, delete the resources associated with the workspace in the Azure portal.
- Delete just the individual resources within the associated resource group that you no longer need. For more information, see Delete resource.
- Or, if you don't need any of the resources in the associated resource group, delete the resource group. For more information, see Delete resource group.
Related resources
If you change your mind and want to install Microsoft Sentinel again, see Onboard Microsoft Sentinel.