Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to: ✔️ SMB Azure file shares
Azure Files supports identity-based authentication for Windows file shares over Server Message Block (SMB) using the Kerberos authentication protocol through the following methods:
- On-premises Active Directory Domain Services (AD DS)
- Microsoft Entra Domain Services
- Microsoft Entra Kerberos for hybrid user identities
This article focuses on enabling Microsoft Entra Domain Services (formerly Azure Active Directory Domain Services) for identity-based authentication with Azure file shares. In this authentication scenario, Microsoft Entra credentials and Microsoft Entra Domain Services credentials are the same, and you can use them interchangeably.
We recommend that you review the How it works section to select the right identity source for your storage account. The setup is different depending on the identity source you choose.
If you're new to Azure Files, we recommend reading our planning guide before reading this article.
Note
Azure Files supports Kerberos authentication with Microsoft Entra Domain Services with AES-256 encryption (recommended).
Azure Files supports authentication for Microsoft Entra Domain Services with full or partial (scoped) synchronization with Microsoft Entra ID. For environments with scoped synchronization, administrators should be aware that Azure Files only honors Azure RBAC role assignments granted to principals that are synchronized. Role assignments granted to identities not synchronized from Microsoft Entra ID to Microsoft Entra Domain Services are ignored by the Azure Files service.
Prerequisites
Before you enable Microsoft Entra Domain Services over SMB for Azure file shares, make sure you complete the following prerequisites:
Select or create a Microsoft Entra tenant.
You can use a new or existing tenant. The tenant and the file share that you want to access must be associated with the same subscription.
To create a new Microsoft Entra tenant, you can Add a Microsoft Entra tenant and a Microsoft Entra subscription. If you have an existing Microsoft Entra tenant but want to create a new tenant for use with Azure file shares, see Create a Microsoft Entra tenant.
Enable Microsoft Entra Domain Services on the Microsoft Entra tenant.
To support authentication with Microsoft Entra credentials, you must enable Microsoft Entra Domain Services for your Microsoft Entra tenant. If you aren't the administrator of the Microsoft Entra tenant, contact the administrator and follow the step-by-step guidance to Enable Microsoft Entra Domain Services using the Azure portal.
It typically takes about 15 minutes for a Microsoft Entra Domain Services deployment to complete. Verify that the health status of Microsoft Entra Domain Services shows Running, with password hash synchronization enabled, before proceeding to the next step.
Domain-join a VM with Microsoft Entra Domain Services.
To access an Azure file share by using Microsoft Entra credentials from a VM, your VM must be domain-joined to Microsoft Entra Domain Services. For more information about how to domain-join a VM, see Join a Windows Server virtual machine to a managed domain. Microsoft Entra Domain Services authentication over SMB with Azure file shares is supported only on Windows VMs running OS versions above Windows 7 or Windows Server 2008 R2, or on Linux VMs running Ubuntu 18.04+ or an equivalent RHEL or SLES VM.
Note
Non-domain-joined VMs can access Azure file shares using Microsoft Entra Domain Services authentication only if the VM has unimpeded network connectivity to the domain controllers for Microsoft Entra Domain Services. Usually this connectivity requires either site-to-site or point-to-site VPN.
Select or create an SMB Azure file share.
Select a new or existing SMB Azure file share that's associated with the same subscription as your Microsoft Entra tenant. See Create an SMB Azure file share. For optimal performance, we recommend that your file share be in the same region as the VM from which you plan to access the share.
Regional availability
Azure Files authentication with Microsoft Entra Domain Services is available in all regions.
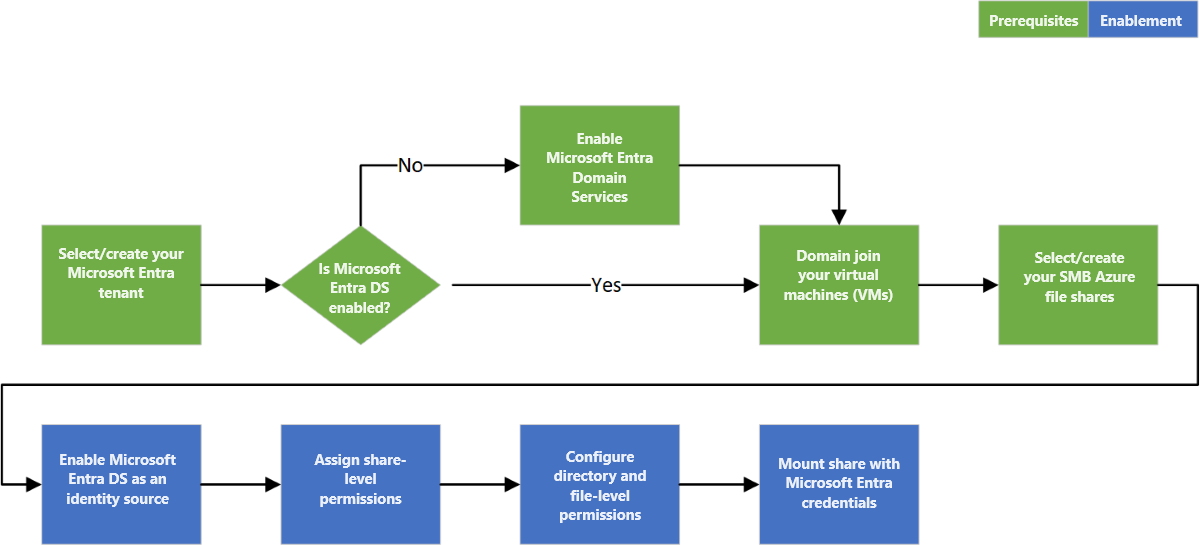
Overview of the workflow
The following diagram shows the end-to-end workflow for enabling Microsoft Entra Domain Services authentication over SMB for Azure Files.
Enable Microsoft Entra Domain Services authentication for your account
To enable Microsoft Entra Domain Services authentication over SMB for Azure Files, set a property on storage accounts by using the Azure portal, Azure PowerShell, or Azure CLI. Setting this property implicitly "domain joins" the storage account with the associated Microsoft Entra Domain Services deployment. Microsoft Entra Domain Services authentication over SMB is then enabled for all new and existing file shares in the storage account.
You can enable Microsoft Entra Domain Services authentication over SMB only after you successfully deploy Microsoft Entra Domain Services to your Microsoft Entra tenant. For more information, see the prerequisites.
To enable Microsoft Entra Domain Services authentication over SMB with the Azure portal, follow these steps:
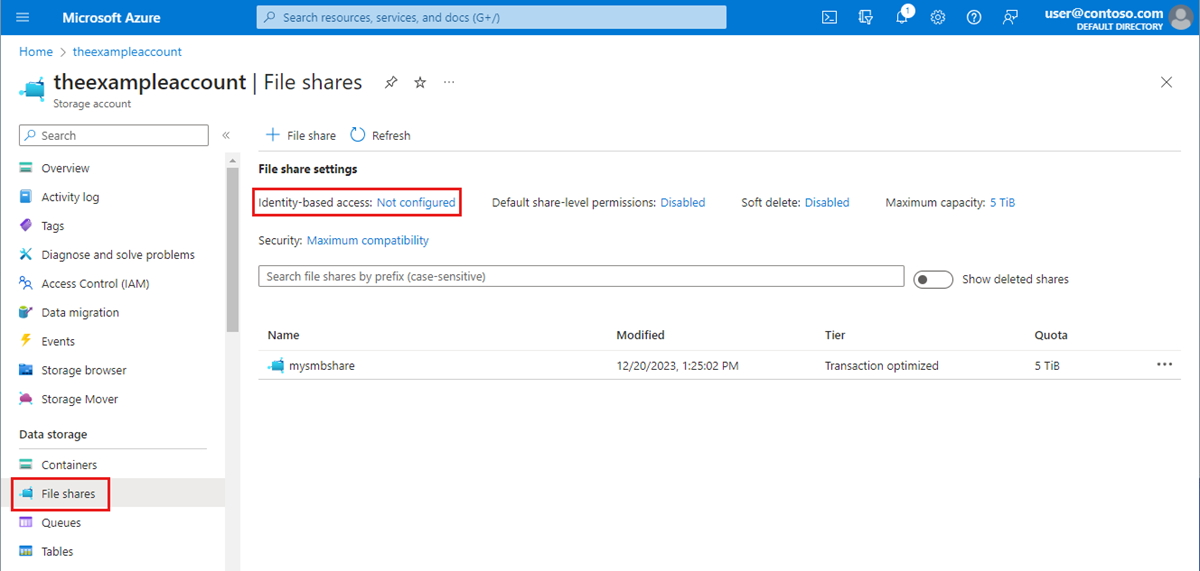
In the Azure portal, go to your existing storage account, or create a storage account.
Select Data storage > File shares.
In the File share settings section, select Identity-based access: Not configured.
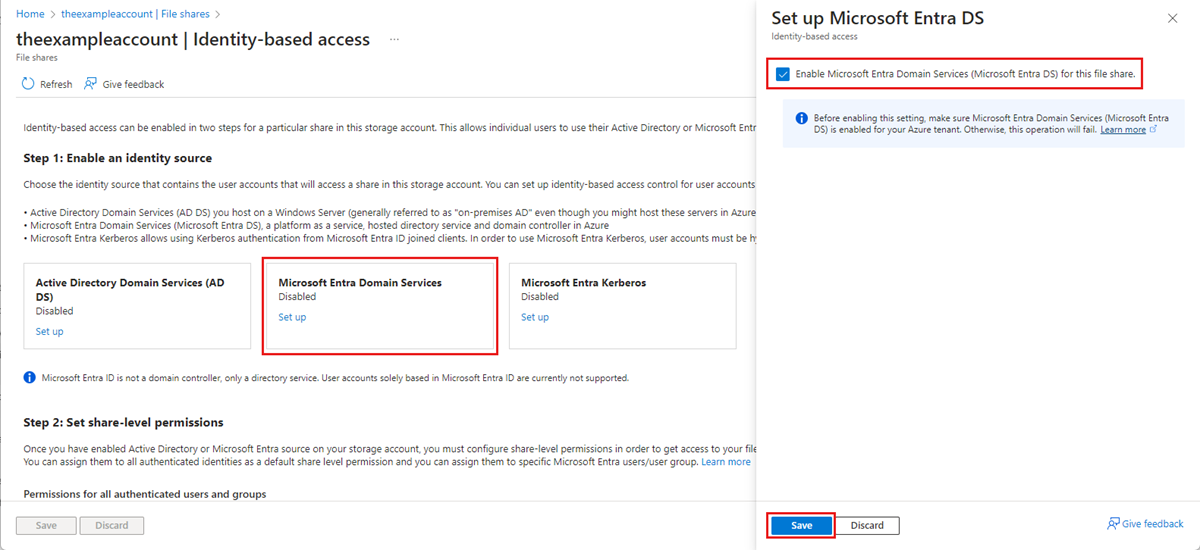
Under Microsoft Entra Domain Services, select Set up, then enable the feature by selecting the checkbox.
Select Save.
Recommended: Use AES-256 encryption
We recommend configuring your storage account to use Kerberos AES-256 encryption by following these instructions.
This action requires running an operation on the domain that's managed by Microsoft Entra Domain Services to reach a domain controller and request a property change to the domain object. The cmdlets below are Windows Server Active Directory PowerShell cmdlets, not Azure PowerShell cmdlets. Because of this distinction, you must run these PowerShell commands from a client machine that's domain-joined to the Microsoft Entra Domain Services domain.
Important
The Windows Server Active Directory PowerShell cmdlets in this section must be run in Windows PowerShell 5.1 from a client machine that's domain-joined to the Microsoft Entra Domain Services domain. PowerShell 7.x won't work in this scenario.
Sign in to the domain-joined client machine as a Microsoft Entra Domain Services user with the required permissions. You must have write access to the msDS-SupportedEncryptionTypes attribute of the domain object. Typically, members of the AAD DC Administrators group have the necessary permissions. Open a normal (non-elevated) PowerShell session and execute the following commands.
# 1. Find the service account in your managed domain that represents the storage account.
$storageAccountName= "<InsertStorageAccountNameHere>"
$searchFilter = "Name -like '*{0}*'" -f $storageAccountName
$userObject = Get-ADUser -filter $searchFilter
if ($userObject -eq $null)
{
Write-Error "Cannot find AD object for storage account:$storageAccountName" -ErrorAction Stop
}
# 2. Set the KerberosEncryptionType of the object
Set-ADUser $userObject -KerberosEncryptionType AES256
# 3. Validate that the object now has the expected (AES256) encryption type.
Get-ADUser $userObject -properties KerberosEncryptionType
Important
If you were previously using RC4 encryption and updated the storage account to use AES-256 (recommended), run klist purge on the client and then remount the file share to get new Kerberos tickets with AES-256.
Next step
- To grant users access to your file share, follow the instructions in Assign share-level permissions.