开始之前,请使用此页顶部的“选择策略类型”选择器来选择要设置的策略类型。 Azure Active Directory B2C 提供了两种定义用户如何与应用程序交互的方法:通过预定义的用户流,或者通过可完全配置的自定义策略。 对于每种方法,本文中所需的步骤都不同。
当用户在 Azure Active Directory B2C (Azure AD B2C) 中登录到应用程序时,单一登录 (SSO) 可以提高安全性和便利性。 本文介绍 Azure AD B2C 中使用的单一登录方法,并在配置策略时帮助你选择最适合的 SSO 方法。
借助单一登录,用户可以使用单个帐户登录一次,然后即可访问多个应用程序。 应用程序可以是 Web、移动或单页应用程序,不管它们的平台或域名如何。
当用户最初登录到应用程序时,Azure AD B2C 会保留一个基于 Cookie 的会话。 收到后续的身份验证请求后,Azure AD B2C 会读取并验证该基于 Cookie 的会话,然后颁发访问令牌,且不提示用户重新登录。 如果基于 Cookie 的会话过期或失效,则系统会提示用户重新登录。
注意
如果用户使用阻止第三方 Cookie 的浏览器,则由于对基于 Cookie 的会话的访问存在限制,SSO 会受到限制。 对用户最明显的影响是登录需要更多交互。 此外,前端通道注销不会立即清除联合应用程序的身份验证状态。 请查看有关如何在浏览器中处理第三方 Cookie 阻止的推荐方法。
先决条件
- 完成 Active Directory B2C 中的自定义策略入门中的步骤。 本教程指导你如何更新自定义策略文件以使用 Azure AD B2C 租户配置。
- 注册 Web 应用程序。
Azure AD B2C 会话概述
与 Azure AD B2C 的集成涉及到三种类型的 SSO 会话:
- Azure AD B2C - 由 Azure AD B2C 管理的会话
- 联合标识提供者 - 由标识提供者(例如 Salesforce)管理的会话
- 应用程序 - 由 Web、移动或单页应用程序管理的会话
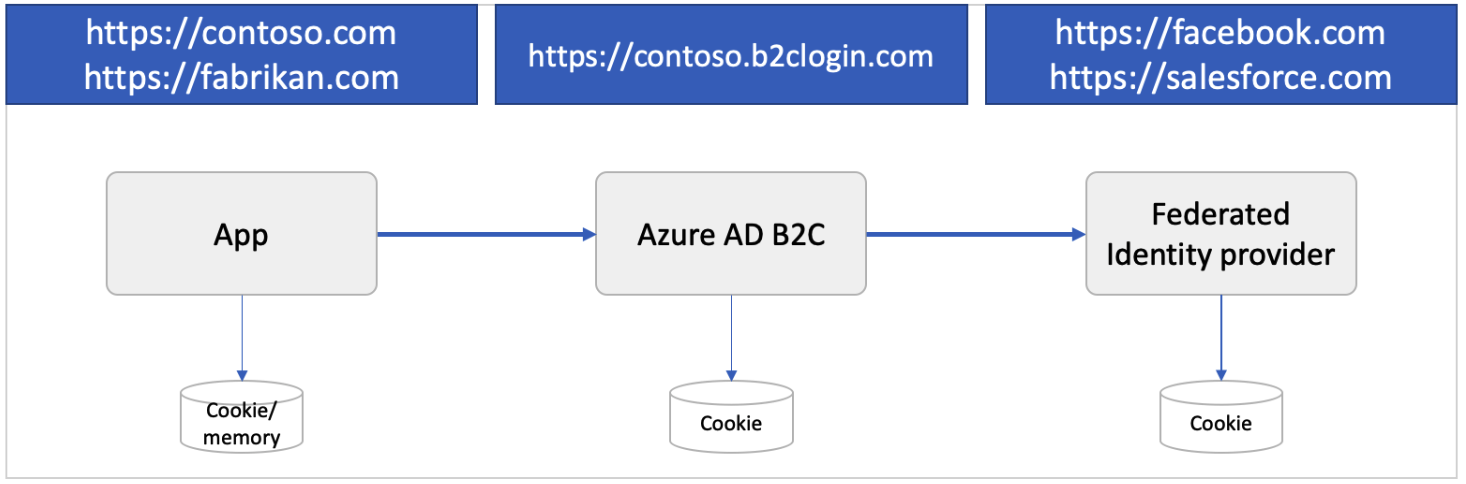
Azure AD B2C 会话
当用户使用社交帐户成功完成身份验证时,Azure AD B2C 会在用户的浏览器中存储一个基于 Cookie 的会话。 Cookie 存储在 Azure AD B2C 租户域名(例如 https://contoso.b2clogin.cn)下。
当用户使用联合帐户登录时,会话时间范围(也称为生存时间 (TTL))将启动。 如果用户在此 TTL 内登录相同或不同的应用,Azure AD B2C 将尝试从联合标识提供者处获取新访问令牌。 如果联合标识提供者会话已过期或失效,则联合标识提供者会提示用户输入其凭据。 如果用户的会话正在进行,或者用户是使用本地帐户而不是联合帐户登录的,Azure AD B2C 会授权用户并阻止任何进一步的提示。
可以配置会话行为,包括会话 TTL,以及 Azure AD B2C 如何在策略和应用程序之间共享会话。
联合标识提供者会话
社交或企业标识提供者需管理其自己的会话。 Cookie 存储在标识提供者的域名(例如 https://login.salesforce.com)下。 Azure AD B2C 不会控制联合标识提供者会话。 会话行为由联合标识提供者确定。
应用程序会话
OAuth2 访问令牌、ID 令牌或 SAML 令牌可以保护 web、移动或单页应用程序。 当用户尝试访问应用上的受保护资源时,应用会检查应用程序端是否存在活动会话。 如果应用会话不存在或会话过期,应用会将用户定向到 Azure AD B2C 登录页。
应用程序会话可以是存储在应用程序域名(例如 https://contoso.com)下的基于 Cookie 的会话。 移动应用程序可能会通过一种不同的方式(但使用类似的方法)存储会话。
配置 Azure AD B2C 会话行为
可以配置 Azure AD B2C 会话行为,包括:
Web 应用会话生存期(分钟) - 是指成功完成身份验证后,将 Azure AD B2C 会话 Cookie 存储在用户浏览器中的时间量。 可以将会话生存期设置为最多 24 小时。
Web 应用会话超时 - 指示如何通过会话生存期设置或“使我保持登录状态 (KMSI)”设置来使会话延期。
- 滚动 - 指示每当用户执行基于 Cookie 的身份验证时都延长会话(默认值)。
- 绝对 - 指示在指定的时间段后强制用户重新进行身份验证。
单一登录配置 - 可为 Azure AD B2C 会话配置以下范围:
- 租户 - 这是默认设置。 使用此设置允许 B2C 租户中的多个应用和用户流共享相同的用户会话。 例如,一旦用户登录到某个应用程序,就还可以在访问该应用程序时无缝登录到另一个应用程序。
- 应用程序 - 此设置允许为某个应用程序维持独占式用户会话(独立于其他应用程序)。 例如,如果你希望无论用户是否已登录到 Contoso Groceries,他们都能够登录到 Contoso Pharmacy,则可以使用此设置。
- 策略 - 此设置为某个用户流维持独占式用户会话(独立于使用它的应用程序)。 例如,如果用户已登录并完成了多重身份验证 (MFA) 步骤,Azure AD B2C 会授予用户访问多个应用程序的更高安全性部分的访问权限。 只要与用户流相关联的会话保持活动,此访问权限就会继续。
- 已禁止 - 此设置强制用户在每次执行策略时都要运行完整的用户流。
配置用户流
若要在用户流中配置会话行为,请执行以下步骤:
- 登录 Azure 门户。
- 如果有权访问多个租户,请选择顶部菜单中的“设置”图标,切换到“目录 + 订阅”菜单中的 Azure AD B2C 租户。
- 选择 Azure 门户左上角的“所有服务”,然后搜索并选择“Azure AD B2C” 。
- 选择“用户流”。
- 打开之前创建的用户流。
- 选择“属性”。
- 根据需要配置 Web 应用会话生存期(分钟) 、Web 应用会话超时、单一登录配置和在注销请求中需要 ID 令牌。
- 选择“保存”。
配置自定义策略
若要在自定义策略中配置会话行为,请执行以下步骤:
打开信赖方 (RP) 文件,例如 SignUpOrSignin.xml
如果它尚不存在,请将以下
<UserJourneyBehaviors>元素添加到<RelyingParty>元素。 它必须紧接在<DefaultUserJourney ReferenceId="UserJourney Id"/>的后面。<UserJourneyBehaviors> <SingleSignOn Scope="Application" /> <SessionExpiryType>Absolute</SessionExpiryType> <SessionExpiryInSeconds>86400</SessionExpiryInSeconds> </UserJourneyBehaviors>添加用户旅程行为元素后,
RelyingParty元素应类似于以下示例:<RelyingParty> <DefaultUserJourney ReferenceId="SignUpOrSignIn" /> <UserJourneyBehaviors> <SingleSignOn Scope="Application" /> <SessionExpiryType>Absolute</SessionExpiryType> <SessionExpiryInSeconds>86400</SessionExpiryInSeconds> </UserJourneyBehaviors> <TechnicalProfile Id="PolicyProfile"> <DisplayName>PolicyProfile</DisplayName> <Protocol Name="OpenIdConnect" /> <OutputClaims> <OutputClaim ClaimTypeReferenceId="displayName" /> <OutputClaim ClaimTypeReferenceId="givenName" /> ... </OutputClaims> <SubjectNamingInfo ClaimType="sub" /> </TechnicalProfile> </RelyingParty>将
Scope属性的值更改为可能的值之一:Suppressed、Tenant、Application或Policy。 有关详细信息,请查看 RelyingParty 参考文章。将
SessionExpiryType元素设置为Rolling或Absolute。 有关详细信息,请查看 RelyingParty 参考文章。将
SessionExpiryInSeconds元素设置为介于 900 秒(15 分钟)和 86,400 秒(24 小时)之间的数值。 有关详细信息,请查看 RelyingParty 参考文章。
启用“使我保持登录状态 (KMSI)”
可以为在 Azure AD B2C 目录中拥有本地帐户的 Web 和本机应用程序的用户启用 KMSI 功能。 该功能启用时,用户能够选择保持登录状态,这样当他们关闭浏览器后会话也保持活动状态。 通过设置永久性 Cookie 维护会话。 选择 KMSI 的用户重新打开浏览器时不会提示他们重新输入用户名和密码。 当用户注销时,会撤销此访问权限(永久性 cookie)。有关详细信息,请查看实时演示。
仅可在单个用户流级别配置 KMSI。 为用户流启用 KMSI 之前,请注意以下几点:
- 只有建议版本的注册和登录 (SUSI)、登录以及配置文件编辑用户流才支持 KMSI。 如果当前这些用户流版本是标准版(旧版)或者旧预览 - v2 版,并且希望启用 KMSI,那么需要针对这些用户流创建新的建议版本。
- 密码重置或注册用户流不支持 KMSI。
- 如果要为租户中的所有应用程序启用 KMSI,建议为租户中的所有用户流启用 KMSI。 由于会话过程中可以向用户显示多个策略,因此他们可能会遇到未启用 KMSI 的策略,这将从会话中删除 KMSI Cookie。
- 不应在公共计算机上启用 KMSI。
为用户流配置 KMSI
为用户流启用 KMSI:
登录 Azure 门户。
如果有权访问多个租户,请选择顶部菜单中的“设置”图标,切换到“目录 + 订阅”菜单中的 Azure AD B2C 租户。
选择 Azure 门户左上角的“所有服务”,然后搜索并选择“Azure AD B2C” 。
选择“用户流(策略)”。
打开之前创建的用户流。
选择“属性”。
在“会话行为”下,选择“启用‘使我保持登录会话状态’” 。 在“使我保持登录会话状态(天)”旁边输入一个介于 1 到 90 之间的值,指定会话可以保持打开状态的天数。
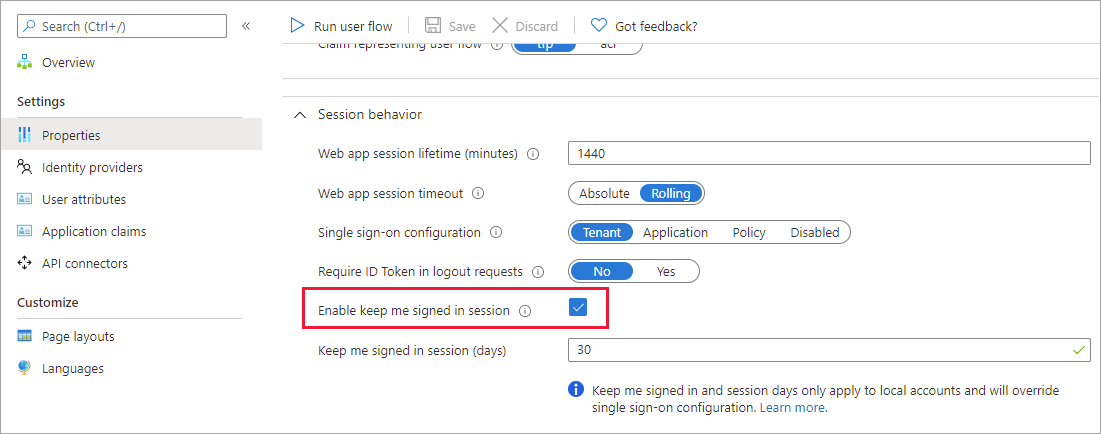
用户不应在公共计算机上启用此选项。
配置页面标识符
若要启用 KMSI,请将内容定义 DataUri 元素设置为页面标识符unifiedssp 和页面版本 1.1.0 或更高版本。
打开策略的扩展文件。 例如
SocialAndLocalAccounts/TrustFrameworkExtensions.xml。 此扩展文件是自定义策略启动程序包中包含的策略文件之一,在先决条件“开始使用自定义策略”中获得该文件。搜索 BuildingBlocks 元素。 如果该元素不存在,请添加该元素。
将 ContentDefinitions 元素添加到策略的 BuildingBlocks 元素。
自定义策略应如下代码片段所示:
<BuildingBlocks> <ContentDefinitions> <ContentDefinition Id="api.signuporsignin"> <DataUri>urn:com:microsoft:aad:b2c:elements:unifiedssp:1.1.0</DataUri> </ContentDefinition> </ContentDefinitions> </BuildingBlocks>
将元数据添加到自断言技术配置文件
若要将 KMSI 复选框添加到注册和登录页,请将 setting.enableRememberMe 元数据设置为 true。 覆盖扩展文件中的 SelfAsserted-LocalAccountSignin-Email 技术配置文件。
找到 ClaimsProviders 元素。 如果该元素不存在,请添加该元素。
将以下声明提供程序添加到 ClaimsProviders 元素:
<ClaimsProvider> <DisplayName>Local Account</DisplayName> <TechnicalProfiles> <TechnicalProfile Id="SelfAsserted-LocalAccountSignin-Email"> <Metadata> <Item Key="setting.enableRememberMe">True</Item> </Metadata> </TechnicalProfile> </TechnicalProfiles> </ClaimsProvider>保存扩展文件。
配置信赖方文件
更新用于启动创建的用户旅程的信赖方 (RP) 文件。
keepAliveInDays 参数允许配置“使我保持登录状态 (KMSI)”会话 Cookie 的持续时间。 例如,如果将值设置为 30,则 KMSI 会话 cookie 将持续 30 天。 该值的范围为 1 到 90 天。 将此值设置为 0 会关闭 KMSI 功能。
打开自定义策略文件。 例如,SignUpOrSignin.xml。
如果它尚不存在,请将
<UserJourneyBehaviors>子节点添加到<RelyingParty>节点。 它必须紧跟在<DefaultUserJourney ReferenceId="User journey Id" />之后,例如:<DefaultUserJourney ReferenceId="SignUpOrSignIn" />。将以下节点添加为
<UserJourneyBehaviors>元素的子级。<UserJourneyBehaviors> <SingleSignOn Scope="Tenant" KeepAliveInDays="30" /> <SessionExpiryType>Absolute</SessionExpiryType> <SessionExpiryInSeconds>1200</SessionExpiryInSeconds> </UserJourneyBehaviors>
同时设置 KeepAliveInDays 和 SessionExpiryInSeconds,以便在登录期间,如果用户启用 KMSI,则使用 KeepAliveInDays 设置 Cookie,否则使用 SessionExpiryInSeconds 参数中指定的值。 建议将 SessionExpiryInSeconds 的值设置为较短时间段(1200 秒),KeepAliveInDays 的值可以设置为相对较长的时间段(30 天),如下例所示:
<RelyingParty>
<DefaultUserJourney ReferenceId="SignUpOrSignIn" />
<UserJourneyBehaviors>
<SingleSignOn Scope="Tenant" KeepAliveInDays="30" />
<SessionExpiryType>Absolute</SessionExpiryType>
<SessionExpiryInSeconds>1200</SessionExpiryInSeconds>
</UserJourneyBehaviors>
<TechnicalProfile Id="PolicyProfile">
<DisplayName>PolicyProfile</DisplayName>
<Protocol Name="OpenIdConnect" />
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="displayName" />
<OutputClaim ClaimTypeReferenceId="givenName" />
<OutputClaim ClaimTypeReferenceId="surname" />
<OutputClaim ClaimTypeReferenceId="email" />
<OutputClaim ClaimTypeReferenceId="objectId" PartnerClaimType="sub"/>
<OutputClaim ClaimTypeReferenceId="identityProvider" />
<OutputClaim ClaimTypeReferenceId="tenantId" AlwaysUseDefaultValue="true" DefaultValue="{Policy:TenantObjectId}" />
</OutputClaims>
<SubjectNamingInfo ClaimType="sub" />
</TechnicalProfile>
</RelyingParty>
注销
如果想要从应用程序中注销用户,只是清除应用程序的 Cookie 或者结束与用户的会话是不够的。 必须将用户重定向到 Azure AD B2C 进行注销。否则,用户可能可以在应用程序中重新进行身份验证,且无需再次输入其凭据。
收到注销请求后,Azure AD B2C 将会:
- 使 Azure AD B2C 基于 Cookie 的会话失效。
- 尝试从联合标识提供者注销。
- 使 Azure AD B2C 基于 Cookie 的会话失效。
- 尝试从联合标识提供者注销:
- 选择性地从其他应用程序注销。 有关详细信息,请参阅单一注销部分。
注意
可以通过将标识提供者技术配置文件元数据 SingleLogoutEnabled 设置为 false 来禁用从联合标识提供者注销。
注销会清除用户在 Azure AD B2C 中的单一登录状态,但可能不会将用户从其社交标识提供者会话中注销。 如果用户在后续登录期间选择相同的标识提供者,那么他们可以重新进行身份验证,且无需输入其凭据。 如果用户想要注销应用程序,并不一定意味着他们想要注销其帐户。 但是,如果使用了本地帐户,则用户的会话将正常结束。
单一登录
当将用户重定向到 Azure AD B2C 注销终结点(对于 OAuth2 和 OpenID Connect)或发送 LogoutRequest(对于 SAML)时,Azure AD B2C 会从浏览器中清除用户的会话。 但是,用户可能在其他使用 Azure AD B2C 进行身份验证的应用程序中仍处于已登录状态。 为了让用户注销具有活动会话的所有应用程序,Azure AD B2C 支持单一注销 (SLO),也称为单一退出登录 (SLO)。
在注销过程中,Azure AD B2C 同时向用户当前登录到的所有应用程序的注册注销 URL 发送 HTTP 请求。
配置自定义策略
若要支持单一注销,JWT 和 SAML 的令牌颁发者技术配置文件必须指定以下内容:
- 协议名称,例如
<Protocol Name="OpenIdConnect" /> - 对会话技术配置文件的引用,例如
UseTechnicalProfileForSessionManagement ReferenceId="SM-jwt-issuer" />。
下面的示例演示了单一注销的 JWT 和 SAML 令牌颁发者:
<ClaimsProvider>
<DisplayName>Local Account SignIn</DisplayName>
<TechnicalProfiles>
<!-- JWT Issuer -->
<TechnicalProfile Id="JwtIssuer">
<DisplayName>JWT Issuer</DisplayName>
<Protocol Name="OpenIdConnect" />
<OutputTokenFormat>JWT</OutputTokenFormat>
...
<UseTechnicalProfileForSessionManagement ReferenceId="SM-jwt-issuer" />
</TechnicalProfile>
<!-- Session management technical profile for OIDC based tokens -->
<TechnicalProfile Id="SM-jwt-issuer">
<DisplayName>Session Management Provider</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.SSO.OAuthSSOSessionProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
</TechnicalProfile>
<!--SAML token issuer-->
<TechnicalProfile Id="Saml2AssertionIssuer">
<DisplayName>SAML token issuer</DisplayName>
<Protocol Name="SAML2" />
<OutputTokenFormat>SAML2</OutputTokenFormat>
...
<UseTechnicalProfileForSessionManagement ReferenceId="SM-Saml-issuer" />
</TechnicalProfile>
<!-- Session management technical profile for SAML based tokens -->
<TechnicalProfile Id="SM-Saml-issuer">
<DisplayName>Session Management Provider</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.SSO.SamlSSOSessionProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
</TechnicalProfile>
</TechnicalProfiles>
</ClaimsProvider>
配置应用程序
为了使应用程序参与单一注销,请执行以下操作:
- 对于 SAML 服务提供者,请使用 SAML 元数据文档中的 SingleLogoutService 位置配置应用程序。 你还可以配置应用注册
logoutUrl。 有关详细信息,请参阅 设置注销 URL。 - 对于 OpenID Connect 或 OAuth2 应用程序,请设置应用注册清单的
logoutUrl属性。 若要配置注销 URL,请执行以下操作:- 从 Azure AD B2C 菜单中,选择“应用注册”。
- 选择应用程序注册。
- 在“管理”下,选择“身份验证”。
- 在“前通道注销 URL”下,配置注销 URL。
处理单一注销请求
Azure AD B2C 收到注销请求时,它将使用一个前通道 HTML iframe 将 HTTP 请求发送到用户当前登录到的每个参与应用程序的注册注销 URL。 请注意,触发注销请求的应用程序会收到此注销消息。 应用程序必须通过清除标识用户的应用程序会话来响应注销请求。
- 对于 OpenID Connect 和 OAuth2 应用程序,Azure AD B2C 向注册的注销 URL 发送 HTTP GET 请求。
- 对于 SAML 应用程序,Azure AD B2C 向注册的注销 URL 发送 SAML 注销请求。
当 Azure AD B2C 通知所有应用程序注销时,它将继续执行以下操作之一:
- 对于 OpenID Connect 或 OAuth2 应用程序,它会将用户重定向到请求的
post_logout_redirect_uri,包括初始请求中指定的(可选)state参数。 例如,https://contoso.com/logout?state=foo。 - 对于 SAML 应用程序,它通过 HTTP POST 向最初发送注销请求的应用程序发送 SAML 注销响应。
保护注销重定向
注销后,用户将重定向到 post_logout_redirect_uri 参数中指定的 URI,而不考虑为应用程序指定的回复 URL。 但是,如果传递了有效的 id_token_hint 并启用了id_token_hint,则在执行重定向之前,Azure AD B2C 将验证 post_logout_redirect_uri 的值是否与应用程序的某个已配置重定向 URI 相匹配。 如果没有为应用程序配置匹配的回复 URL,则会显示一条错误消息,而不会重定向用户。
要求在注销请求中提供 ID 令牌:
- 登录 Azure 门户。
- 如果有权访问多个租户,请选择顶部菜单中的“设置”图标,切换到“目录 + 订阅”菜单中的 Azure AD B2C 租户。
- 选择 Azure 门户左上角的“所有服务”,然后搜索并选择“Azure AD B2C” 。
- 选择“用户流”。
- 打开之前创建的用户流。
- 选择“属性”。
- 启用“注销请求中需要 ID 令牌”。
若要启用要求在注销请求中提供 ID 令牌,请在 RelyingParty 元素中添加 UserJourneyBehaviors 元素。 然后将 SingleSignOn 元素的 EnforceIdTokenHintOnLogout 设置为 。 有关详细信息,请查看实时演示。 UserJourneyBehaviors 元素应当如以下示例所示:
<UserJourneyBehaviors>
<SingleSignOn Scope="Tenant" EnforceIdTokenHintOnLogout="true"/>
</UserJourneyBehaviors>
配置应用程序注销 URL:
- 选择“应用注册”,然后选择自己的应用程序。
- 选择“身份验证”。
- 在“注销 URL”文本框中,键入注销后重定向 URI,然后选择“保存” 。
相关内容
- 了解如何在 Azure AD B2C 中配置令牌。