重要
从 2025 年 7 月 28 日起,对应用服务 托管证书 (ASMC)的更改会影响某些情况下证书的颁发和续订方式。 虽然大多数客户不需要采取措施,但我们建议查看 ASMC 的详细博客文章 以了解详细信息。
本文介绍如何通过创建证书绑定为 Azure 应用服务应用或函数应用中的自定义域提供安全性。 完成后,您可以通过自定义域名系统(DNS)名称的端点 https:// 访问您的应用服务应用。 示例为 https://www.contoso.com。

先决条件
- 将应用服务应用纵向扩展到 受支持的定价层之一:基本层、标准层或高级层。
- 将域名映射到应用。
添加绑定
在 Azure 门户中:
在左窗格中,选择 “应用服务><”应用名称>。
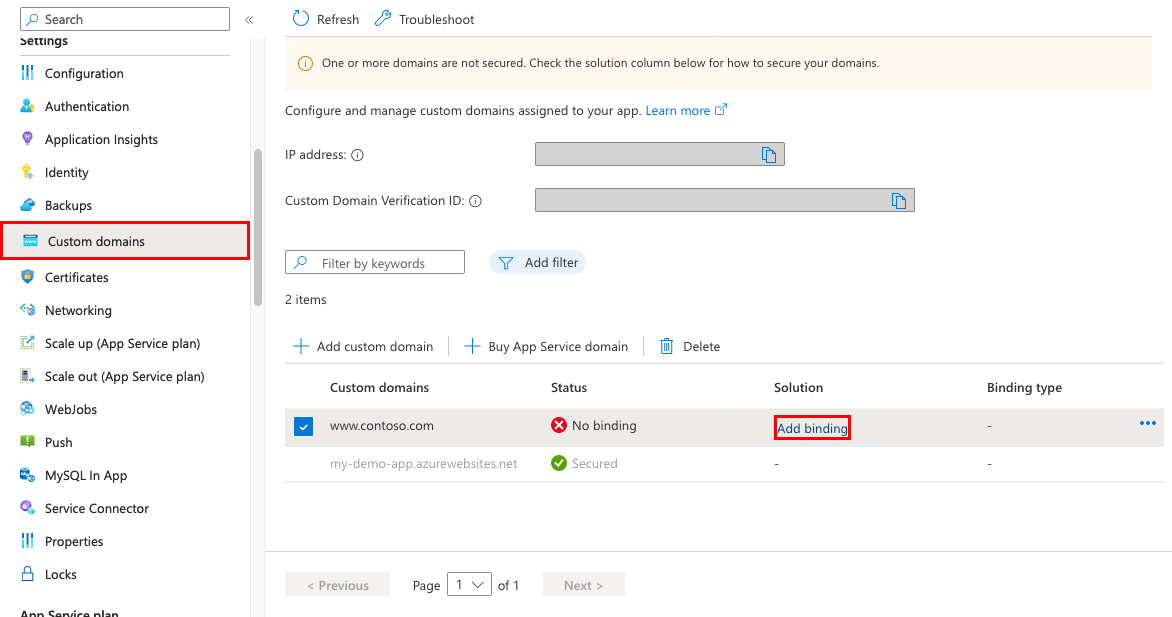
在应用的左窗格中,选择 “自定义域”。
在自定义域旁边,选择“添加绑定”。
如果你的应用已有所选自定义域的证书,则可以在“证书”中选择它。 否则,必须使用 源中选择之一来添加证书:
- 创建应用服务托管证书:让应用服务为所选域创建托管证书。 此选项是最简单的。
- 导入应用服务证书:在 应用服务证书中,选择应用服务证书。
- 上传证书(.pfx):按照 “上传专用证书 ”中的工作流从本地计算机上传 PFX 证书并指定证书密码。
- 从 Key Vault 导入: 选择密钥保管库证书 ,然后在对话框中选择证书。
在 TLS/SSL 类型中,选择 SNI SSL 或 基于 IP 的 SSL:
- SNI SSL:可以添加多个服务器名称指示(SNI)安全套接字层(SSL)绑定。 此选项允许多个传输层安全性(TLS)/SSL 证书帮助保护同一 IP 地址上的多个域。 大多数新式浏览器(包括 Microsoft Edge、Chrome、Firefox 和 Opera)都支持 SNI。
- 基于 IP 的 SSL:只能添加一个 IP SSL 绑定。 选择此选项只能使用一个 TLS/SSL 证书来帮助保护专用公共 IP 地址。 配置绑定后,请按照重新映射基于 IP 的 SSL 的记录中的步骤进行操作。 基于 IP 的 SSL 仅在标准层或更高版本中受支持。
添加新证书时,选择“ 验证 ”以验证新证书。
选择 添加 。
作完成后,自定义域的 TLS/SSL 状态将更改为 “安全”。
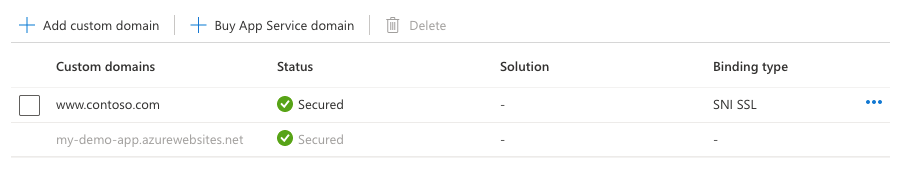
自定义域中的安全状态意味着证书提供安全性。 应用服务不会检查证书是否已自签名或已过期,这也可能导致浏览器显示错误或警告。
为基于 IP 的 SSL 重新映射记录
只有基于 IP 的 SSL 才需要此步骤。 对于 SNI SSL 绑定,请跳到“测试 HTTPS”。
可能需要进行两项更改:
默认情况下,应用使用共享的公共 IP 地址。 将证书与 IP SSL 绑定时,应用服务会为应用创建新的专用 IP 地址。 如果已将 A 记录映射到应用,请使用这个新的专用 IP 地址更新域注册表。
将使用新的专用 IP 地址更新应用的“自定义域”页。 复制此 IP 地址,然后将 A 记录重新映射到 此新 IP 地址。
如果有与
<app-name>.chinacloudsites.cn的 SNI SSL 绑定,请重新映射任何 CNAME 映射以指向sni.<app-name>.chinacloudsites.cn。 (添加sni前缀。)
测试 HTTPS
在各种浏览器中浏览到 https://<your.custom.domain>,以验证应用是否显示。

应用程序代码可以通过 x-appservice-proto 标头检查协议。 标头具有 http 或 https 值。
如果应用显示证书验证错误,可能是因为使用自签名证书。 如果不是这种情况,在将证书导出到 .pfx 文件时,可能会遗漏中间证书。
常见问题解答
如何确保在更改证书绑定时应用的 IP 地址不会更改?
在删除某个绑定时,即使该绑定是 IP SSL,入站 IP 地址也可能会更改。 续订 IP SSL 绑定中的证书时,此行为尤其重要。 若要避免更改应用的 IP 地址,请执行以下步骤:
- 上传新证书。
- 将新证书绑定到所需的自定义域,而无需删除旧证书。 此操作替换而不是删除旧的绑定。
- 删除旧证书。
是否可以禁用从 HTTP 到 HTTPS 的强制重定向?
默认情况下,应用服务强制从 HTTP 请求重定向到 HTTPS。 若要禁用此行为,请参阅配置常规设置。
如何更改应用的最低 TLS 版本?
应用默认情况下允许 TLS 1.2,这是行业标准(例如 PCI DSS)建议的 TLS 级别。 若要强制实施不同的 TLS 版本,请参阅配置常规设置。
如何在应用服务中处理 TLS 终止?
在应用服务中,TLS 终止在网络负载均衡器上发生,因此,所有 HTTPS 请求将以未加密的 HTTP 请求形式访问你的应用。 如果应用逻辑需要检查用户请求是否已加密,可以检查 X-Forwarded-Proto 标头。
特定于语言的配置指南(如 Linux Node.js 配置指南)介绍了如何在应用程序代码中检测 HTTPS 会话。
使用脚本自动化
Azure CLI
PowerShell
$fqdn="<Replace with your custom domain name>"
$pfxPath="<Replace with path to your .PFX file>"
$pfxPassword="<Replace with your .PFX password>"
$webappname="mywebapp$(Get-Random)"
$location="China North"
# Create a resource group.
New-AzResourceGroup -Name $webappname -Location $location
# Create an App Service plan in Free tier.
New-AzAppServicePlan -Name $webappname -Location $location `
-ResourceGroupName $webappname -Tier Free
# Create a web app.
$webapp = New-AzWebApp -Name $webappname -Location $location -AppServicePlan $webappname `
-ResourceGroupName $webappname
Write-Host "Sign in to your domain provider's website and configure the following records:"
Write-Host "A CNAME record that maps $fqdn to $webappname.chinacloudsites.cn"
Write-Host "A TXT record that maps asuid.$fqdn to the domain verification ID $($webapp.CustomDomainVerificationId)"
Read-Host "Press [Enter] key when ready ..."
# Before continuing, go to your DNS configuration UI for your custom domain and follow the
# instructions at /app-service/app-service-web-tutorial-custom-domain#step-2-create-the-dns-records to configure a CNAME record for the
# hostname "www" and point it your web app's default domain name.
# Upgrade App Service plan to Basic tier (minimum required by custom SSL certificates)
Set-AzAppServicePlan -Name $webappname -ResourceGroupName $webappname `
-Tier Basic
# Add a custom domain name to the web app.
Set-AzWebApp -Name $webappname -ResourceGroupName $webappname `
-HostNames @($fqdn,"$webappname.chinacloudsites.cn")
# Upload and bind the SSL certificate to the web app.
New-AzWebAppSSLBinding -WebAppName $webappname -ResourceGroupName $webappname -Name $fqdn `
-CertificateFilePath $pfxPath -CertificatePassword $pfxPassword -SslState SniEnabled