可以使用本地 Git 部署或 FTP/S 部署将本地应用部署到 Azure 应用服务。 本文介绍如何为本地 Git 或 FTP/S 部署创建和管理部署凭据。
部署凭据不同于 Azure 订阅凭据。 应用服务支持用于安全本地应用部署的两种类型的凭据: 用户范围 和 应用范围 凭据。
用户范围 或用户级凭据为用户的整个 Azure 帐户提供一组部署凭据。 通过基于角色的访问控制(RBAC)或共同管理员权限授予应用访问权限的用户,只要他们具有这些权限,就可以使用其用户级凭据。
可以使用用户范围凭据通过本地 Git 或 FTP/S 将任何应用部署到你的 Azure 帐户有权访问的任何订阅中的应用服务。 不会与任何其他 Azure 用户共享这些凭据。 可以随时重置用户范围凭据。
应用范围 或应用程序级凭据是每个应用一组凭据,可用于仅部署该应用。 这些凭据在创建时会自动为每个应用生成,无法手动配置,但可以随时重置密码。
用户必须至少具有对应用(包括内置网站参与者角色)的参与者级别权限,才能通过 RBAC 授予对应用级凭据的访问权限。 读取者 角色无法发布,无法访问这些凭据。
先决条件
若要设置、重置、访问或使用部署凭据,必须对应用服务应用具有 参与者级权限。
基本身份验证要求
若要通过本地 Git 或 FTP/S 发布应用服务应用,必须启用基本身份验证。 SCM 基本身份验证发布凭据和 FTP 基本身份验证发布凭据都必须在 Azure 门户的应用配置页上设置为 On。
基本身份验证的安全性低于其他身份验证方法,默认情况下为新应用禁用。 如果禁用了基本身份验证,则无法在应用的 部署中心 中查看或设置部署凭据,也不能使用这些凭据进行发布。 有关详细信息,请参阅 “在 Azure 应用服务部署中禁用基本身份验证”。
设置用户范围凭据
对于 FTP/S 部署,需要用户名和密码。 本地 Git 部署只需要用户名。 用户名在 Azure 中必须唯一。
对于本地 Git 部署,用户名不能包含 @ 字符。
对于 FTP/S 部署:
用户名必须遵循格式
<app-name>\<user-name>。 由于用户范围凭据已链接到用户而不是应用,因此此格式会将登录作定向到应用的正确 FTP/S 终结点。密码必须至少为 8 个字符,并且包含大写字母、小写字母、数字和符号。 Azure 门户不显示用户范围密码,JSON 输出将显示为
null。 如果丢失或忘记密码,可以 重置凭据 以获取新凭据。
可以使用 Azure CLI 或 Azure 门户配置用户范围凭据。
- Azure CLI
- Azure PowerShell
- Azure 门户
要通过 Azure CLI 创建用户范围凭据,请运行 az webapp deployment user set 命令,并将 <username> 和 <password> 替换为您选择的值。
az webapp deployment user set --user-name <username> --password <password>
设置用户范围凭据后,可以在 Azure 门户的应用 “概述 ”页上看到部署用户名。 如果配置了本地 Git 部署,则标签为 Git/部署用户名。 否则,标签为 FTP/部署用户名。
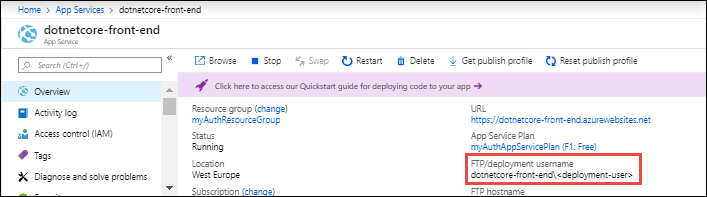
获取应用程序范围凭据
应用程序范围凭据在创建应用时自动创建。 FTP/S 应用范围用户名始终遵循格式 app-name\$app-name。 本地 Git 应用范围用户名使用格式 $app-name。
注释
在使用美元符号($)进行变量插值的 shell(例如 Bash)中,必须使用 git remote add 来转义用户名或密码中的任何美元符号,以避免身份验证错误。
可以使用 Azure CLI、Azure PowerShell 或 Azure 门户获取应用范围凭据。
- Azure CLI
- Azure PowerShell
- Azure 门户
在 Azure CLI 中,使用 az webapp deployment list-publishing-profiles 命令获取应用程序范围凭据。 例如:
az webapp deployment list-publishing-profiles --resource-group myResourceGroup --name myApp
对于 本地 Git 部署,还可以使用 az webapp deployment list-publishing-credentials 命令。 以下示例返回一个 Git 远程 URI,其中包含已嵌入的应用的应用程序范围凭据。
az webapp deployment list-publishing-credentials --resource-group myResourceGroup --name myApp --query scmUri
返回的 Git 远程 URI 在末尾没有 /<app-name>.git 。 如果使用 URI 添加远程,请追加/<app-name>.git到 URI 以避免出现错误22git-http-push。
重置凭据
可以使用 Azure CLI、Azure PowerShell 或 Azure 门户重置应用程序范围的部署凭据并获取新密码。 应用范围用户名保留其自动生成的值。
在 Azure CLI 和 Azure 门户中,还可以通过创建新凭据来重置用户范围凭据。 此操作会影响帐户中所有使用用户范围凭据的应用。
重置部署凭据时,通过发布配置文件进行的任何外部集成和自动化都会停止工作,必须使用新值重新配置这些集成和自动化。
- Azure CLI
- Azure PowerShell
- Azure 门户
在 Azure CLI 中,使用 az resource invoke-action 命令和 newpassword 动作重置应用程序范围内的密码。
az resource invoke-action --action newpassword --resource-group <group-name> --name <app-name> --resource-type Microsoft.Web/sites
通过重新运行 az webapp deployment user set 命令以创建新的用户名和密码值来重置用户范围凭据。
az webapp deployment user set --user-name <new-username> --password <new-password>