由于应用服务环境对单个客户是隔离的,因此有一些可专门应用于应用服务环境的配置设置。 本文介绍各种可用于应用服务环境的特定自定义设置。
如果没有应用服务环境,请参阅 “如何创建应用服务环境 v3”。
可以使用 clusterSettings 属性中的数组来存储应用服务环境自定义项。 可以在 hostingEnvironments Azure 资源管理器实体的“Properties”字典中找到此属性。
以下简略的 Resource Manager 模板代码片段显示了 clusterSettings 属性:
"resources": [
{
"apiVersion": "2021-03-01",
"type": "Microsoft.Web/hostingEnvironments",
"name": ...,
"location": ...,
"properties": {
"clusterSettings": [
{
"name": "nameOfCustomSetting",
"value": "valueOfCustomSetting"
}
],
"internalLoadBalancingMode": ...,
etc...
}
}
clusterSettings 属性可以包含在资源管理器模板中,也可以包含在 Azure CLI 中以更新应用服务环境。 某些设置在 Azure 门户中可用。
但是提交更改时,更改不会立即完成,更改可能需要长达 24 小时才能完全生效。 某些设置具有配置特定设置的时间和效果的特定详细信息。
启用内部加密
应用服务环境作为黑盒系统运行,在该系统中看不到内部组件或通信。 为了实现更高的吞吐量,默认情况下,在内部组件之间不启用加密。 系统很安全,因为流量无法访问,不管你是要监视流量还是要访问流量。 如果符合性要求,但需要从端到端完全加密数据路径,则可以使用 clusterSetting 启用完整数据路径加密。
"clusterSettings": [
{
"name": "InternalEncryption",
"value": "true"
}
],
还可以通过转到应用服务环境的 “配置 ”页,使用 Azure 门户启用内部加密。
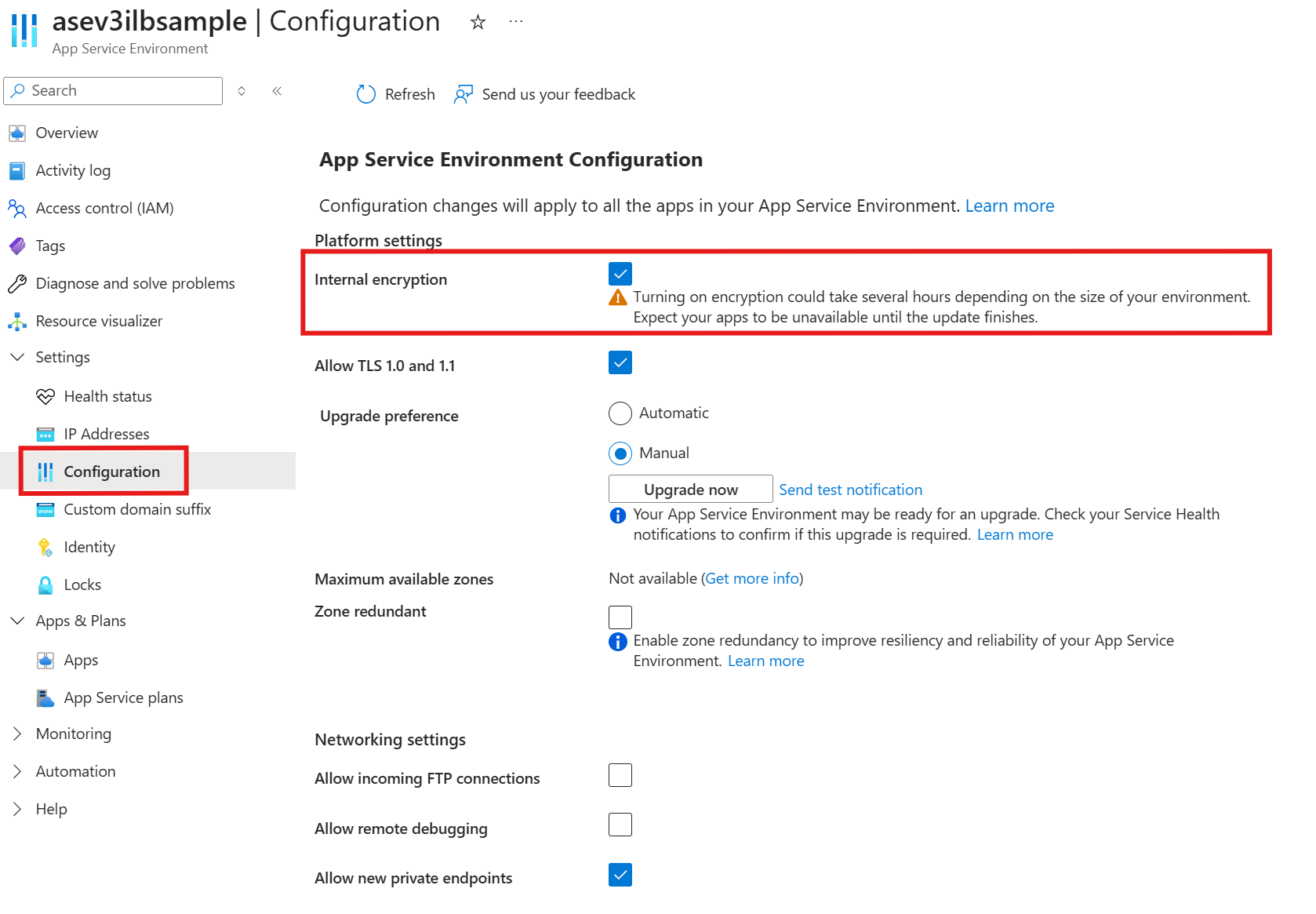
将 InternalEncryption 设置为 true 可对前端和辅助角色之间的应用服务环境中的内部网络流量进行加密,还可对页面文件和辅助角色磁盘进行加密。 启用 InternalEncryption clusterSetting 后,系统性能可能会产生影响。 进行更改以启用 InternalEncryption 时,应用服务环境处于不稳定状态,直到完全传播更改。 更改的传播可能需要几个小时才能完成,具体取决于应用服务环境中有多少实例。 强烈建议在应用服务环境中不使用 InternalEncryption。 如果需要对主动使用的应用服务环境启用 InternalEncryption,强烈建议将流量转移到备份环境,直到操作完成。
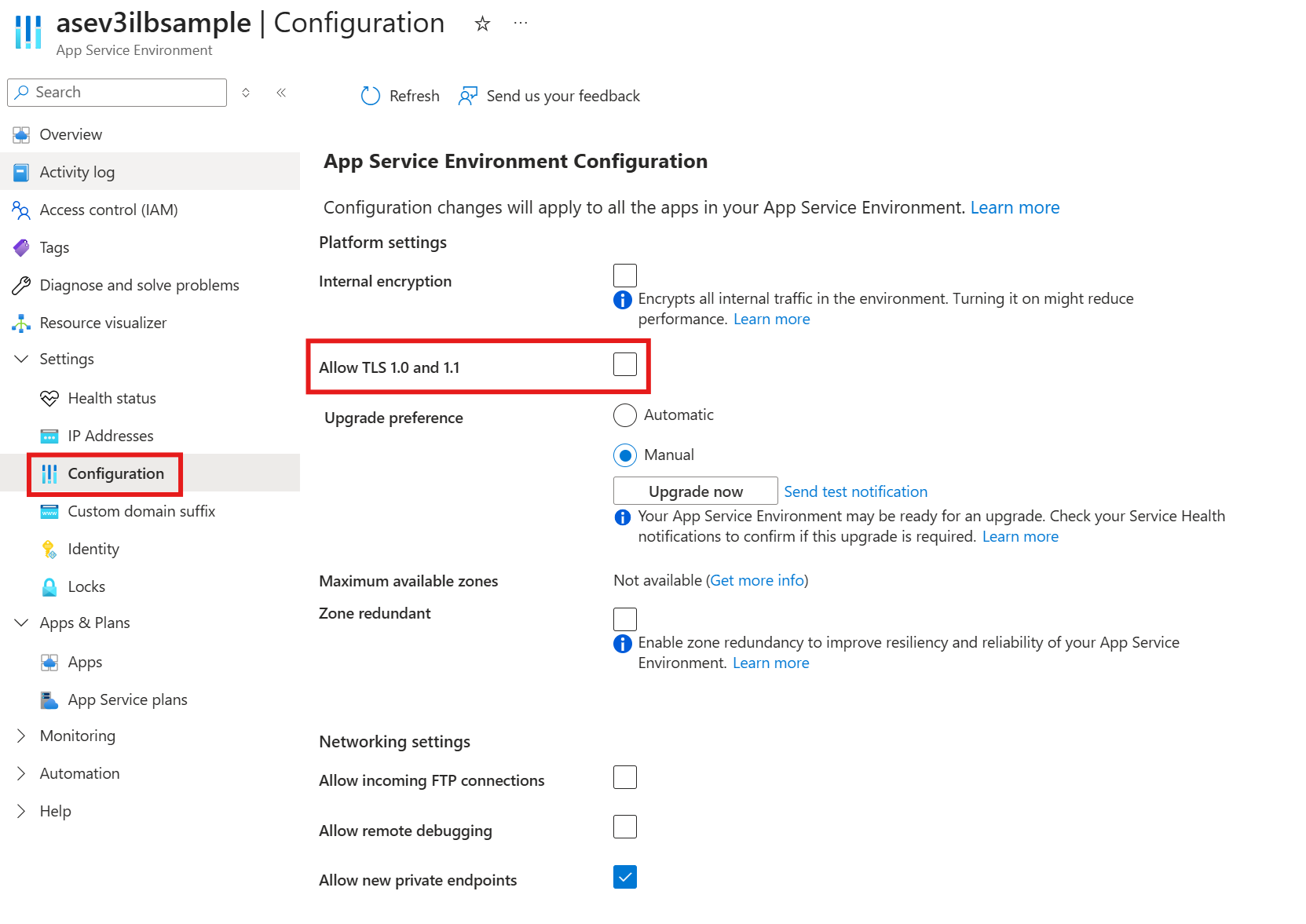
禁用 TLS 1.0 和 TLS 1.1
若要逐个应用地管理 TLS 设置,则可按实施 TLS 设置文档提供的指南进行操作。
对于应用服务环境中的所有应用,若要禁用所有入站 TLS 1.0 和 TLS 1.1 流量,可以设置以下 clusterSettings 条目:
"clusterSettings": [
{
"name": "DisableTls1.0",
"value": "1"
}
],
设置的名称显示 1.0,但在配置以后,却禁用了 TLS 1.0 和 TLS 1.1。
还可以通过转到应用服务环境的 “配置 ”页并取消选中复选框,使用 Azure 门户禁用 TLS 1.0 和 TLS 1.1。
更改 TLS 密码套件顺序
应用服务环境支持从默认值更改密码套件。 默认密码集是多租户应用服务中使用的同一组密码。 只有应用服务环境(单租户产品/服务而不是多租户产品/服务)才能更改密码套件,因为更改它会影响整个应用服务部署。 应用服务环境需要两个密码套件:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 和 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256。 此外,还应包括 TLS 1.3 所需的以下密码套件:TLS_AES_256_GCM_SHA384 和 TLS_AES_128_GCM_SHA256。
重要
应用 FrontEndSSLCipherSuiteOrder 服务环境群集设置与应用级 minTlsCipherSuite 设置不兼容。 如果在FrontEndSSLCipherSuiteOrder应用服务环境层面配置了密码套件顺序,请不要在单个应用层面配置最低 TLS 密码套件。 必须使用一个或另一个,而不是同时使用两者。 配置这两个设置可能会导致 SSL 错误和拒绝的请求。
若要将应用服务环境配置为仅使用它所需的密码,请修改 clusterSettings,如以下示例所示。 确保列表开头包含 TLS 1.3 密码。
"clusterSettings": [
{
"name": "FrontEndSSLCipherSuiteOrder",
"value": "TLS_AES_256_GCM_SHA384,TLS_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256"
}
],
警告
如果为 SChannel 无法理解的密码套件设置了不正确的值,则与服务器的所有 TLS 通信都可能会停止运行。 在这种情况下,需要从 clusterSettings 中删除 FrontEndSSLCipherSuiteOrder 条目,并提交更新的资源管理器模板以还原回默认密码套件设置。 请谨慎使用此功能。
启用 FIPS 模式
此设置适用于应用服务环境中的基于 Linux 的工作负载。 可以配置在应用服务环境中运行的基于 Linux 的工作负荷,以在 FIPS(联邦信息处理标准)模式下运行。 启用后,FIPS 模式可确保加密作符合 FIPS 140-2 标准。
若要在应用服务环境中启用 FIPS 模式,可以设置以下 clusterSettings 条目:
"clusterSettings": [
{
"name": "LinuxFipsModeEnabled",
"value": "true"
}
],
应用服务环境在 LinuxFipsModeEnabled 设置为 true 时使用符合 FIPS 的加密模块进行加密操作。
开始
Azure 快速入门 Resource Manager 模板站点包含具有创建应用服务环境基本定义的模板。