应用程序网关入口控制器 (AGIC) 是一个 Kubernetes 应用程序。有了它,Azure Kubernetes 服务 (AKS) 客户就可以利用 Azure 的本机应用程序网关 L7 负载均衡器向 Internet 公开云软件。 AGIC 监视托管时所在的 Kubernetes 群集并持续更新应用程序网关,以便向 Internet 公开所选服务。
在客户的 AKS 上,入口控制器在其自己的 Pod 中运行。 AGIC 监视部分 Kubernetes 资源中的更改。 AKS 群集的状态会转换为特定于应用程序网关的配置并应用到 Azure 资源管理器 (ARM)。
应用程序网关入口控制器的好处
有了 AGIC,就不需在 AKS 群集前面设置另一个负载均衡器/公共 IP 地址,避免在请求到达 AKS 群集之前在数据路径中设置多个跃点。 应用程序网关直接使用其专用 IP 地址与 Pod 通信,不需要 NodePort 或 KubeProxy 服务。 此功能也会改进部署性能。
入口控制器完全由 Standard_v2 和 WAF_v2 SKU 提供支持,这也会带来自动缩放的好处。 应用程序网关可以响应流量负载的增减并相应地进行缩放,不消耗 AKS 群集中的任何资源。
在 AGIC 基础上使用应用程序网关还可以提供 TLS 策略和 Web 应用程序防火墙 (WAF) 功能,这有助于保护 AKS 群集。
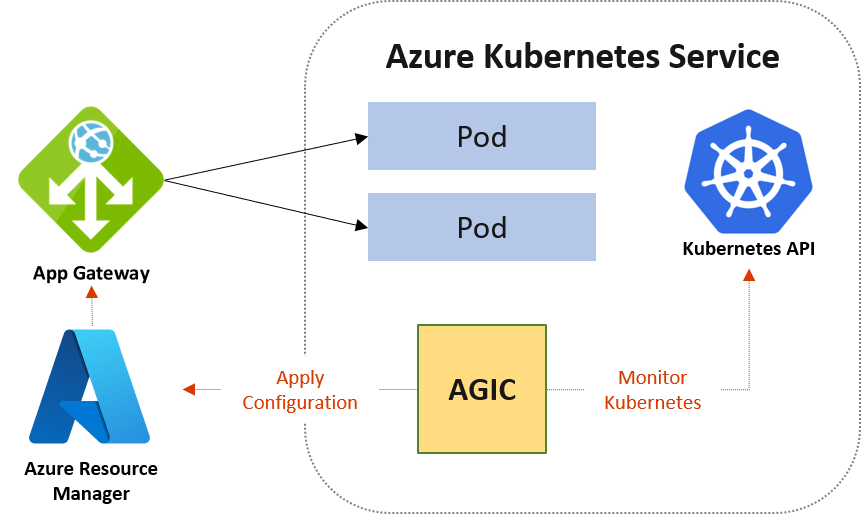
AGIC 通过 Kubernetes 入口资源以及服务和部署/Pod 进行配置。 它使用 Azure 自带的应用程序网关 L7 负载均衡器提供许多功能。 例如:
- URL 路由
- 基于 Cookie 的相关性
- TLS 终止
- 端到端 TLS
- 支持公共、专用和混合网站
- 集成式 Web 应用程序防火墙
Helm 部署与 AKS 加载项之间的差异
可通过两种方式为 AKS 群集部署 AGIC。 第一种方法是通过 Helm;第二种方式是通过 AKS 作为加载项部署。 将 AGIC 部署为 AKS 加载项的主要好处是,它比通过 Helm 部署要简单得多。 若要进行新的设置,在 Azure CLI 中通过一行内容即可部署新应用程序网关和将 AGIC 作为加载项启用的新 AKS 群集。 该加载项也是一项完全托管的服务,这提供了一些额外的优势,例如自动更新和更多的支持。 Microsoft 完全支持部署 AGIC(Helm 和 AKS 加载项)的两种方式。 此外,该加载项作为一流的加载项,允许更好地与 AKS 集成。
AGIC 加载项在客户的 AKS 群集中仍作为 pod 部署,但是 Helm 部署版本与加载项版本的 AGIC 之间存在一些差异。 下面列出了两个版本之间的差异:
- 无法在 AKS 加载项上修改 Helm 部署值:
-
verbosityLevel默认设置为 5 -
usePrivateIp默认设置为 false;但可由 use-private-ip annotation 重写此项 - 加载项不支持
shared - 加载项不支持
reconcilePeriodSeconds - 加载项不支持
armAuth.type
-
- 通过 Helm 部署的 AGIC 支持 ProhibitedTargets,这意味着 AGIC 可以专为 AKS 群集配置应用程序网关,不影响其他现有的后端。 AGIC 加载项目前不支持此功能。
- 由于 AGIC 加载项是一种托管服务,因此客户的 AGIC 加载项将自动更新为最新版本,不像通过 Helm 部署的 AGIC,客户必须手动更新 AGIC。
注意
客户只能为每个 AKS 群集部署一个 AGIC 加载项,并且每个 AGIC 加载项当前只能面向一个应用程序网关。 对于每个群集需要多个 AGIC 的部署或需要多个面向某个应用程序网关的 AGIC 的部署,请继续使用通过 Helm 部署的 AGIC。
Helm 和 AGIC 加载项都不支持 ExternalName 服务。
容器网络和 AGIC
应用程序网关入口控制器支持以下 AKS 网络产品/服务:
- Kubenet
- CNI
- CNI 覆盖网络
Azure CNI 和 Azure CNI 覆盖是应用程序网关入口控制器的两个推荐选项。 选择网络模型时,请考虑每个 CNI 插件的用例及其使用的网络模型类型:
| CNI 插件 | 网络模型 | 用例要点 |
|---|---|---|
| Azure CNI 覆盖 | 覆盖 | - 最适合 VNET IP 保护 - API 服务器支持的最大节点数 + 每个节点 250 个 Pod - 更简单的配置 - 无法直接从外部访问 Pod IP |
| Azure CNI Pod 子网 | 平坦 | - 可直接从外部访问 Pod - 有效 VNet IP 使用率 或 大型群集规模支持的模式 |
| Azure CNI 节点子网 | 平坦 | - 可直接从外部访问 Pod - 更简单的配置 - 扩展性受限 - VNet IP 使用效率低下 |
将用于容器的应用程序网关预配到启用了 CNI 覆盖或 CNI 的群集时,适用于容器的应用程序网关会自动检测预期的网络配置。 网关或入口 API 配置无需更改即可指定 CNI overlay 或 CNI。
使用 Azure CNI 重叠网络,请考虑以下限制:
- AGIC 控制器:必须运行版本 v1.9.1 或更高版本才能利用 CNI 覆盖。
- 子网大小:应用程序网关子网的前缀最大为 /24;每个子网仅支持一个部署。
- 子网委派:应用程序网关子网必须具有Microsoft.Network/applicationGateways 的子网委派。
- 区域 VNet 对等互连:不支持在区域 A 的虚拟网络中部署的应用程序网关和区域 A 中的虚拟网络中的 AKS 群集节点。
- 全局 VNet 对等互连:不支持将应用程序网关部署在区域 A 的虚拟网络中,并将 AKS 群集节点置于区域 B 的虚拟网络中。
- 由世纪互联运营的 Microsoft Azure(中国版)不支持 Azure CNI Overlay 与应用程序网关入口控制器。
注意
应用网关入口控制器会自动检测到 AKS 群集从 Kubenet 或 CNI 升级到 CNI Overlay。 建议在维护时段内计划升级,因为可能发生流量中断。 控制器可能需要几分钟的群集后升级来检测和配置对 CNI 覆盖的支持。
警告
在升级之前,请确保应用程序网关子网是 /24 或更小的子网。 从 CNI 升级到具有较大子网(即 /23)的 CNI 覆盖层将导致中断,并要求使用支持的子网大小重新创建应用程序网关子网。
后续步骤
- Helm“绿色地带”部署:在白板基础结构上通过 Helm、新 AKS 群集和新应用程序网关安装 AGIC。
- Helm“棕色地带”部署:在现有的 AKS 群集和应用程序网关上通过 Helm 部署 AGIC。