Azure SQL 托管实例的公共终结点使数据能够从虚拟网络外部访问 SQL 托管实例。 可以从多租户 Azure 服务(如 Power BI、Azure 应用服务或本地网络)访问 SQL 托管实例。 通过在 SQL 托管实例上使用公共终结点,无需使用 VPN,这有助于避免 VPN 吞吐量问题。
在本文中,学习如何:
- 启用或禁用 SQL 托管实例的公共终结点
- 配置 SQL 托管实例网络安全组(NSG),以允许流量流向 SQL 托管实例公共终结点
- 获取 SQL 托管实例公共终结点连接字符串
权限
由于 SQL 托管实例中的数据敏感度,启用 SQL 托管实例公共终结点的配置需要两步过程。 这种安全措施遵守职责分离 (SoD) 的原则:
- SQL 托管实例管理员需要在 SQL 托管实例上启用公共终结点。 可以在 SQL 托管实例资源的 “概述 ”页上找到 SQL 托管实例管理员。
- 网络管理员需要使用网络安全组(NSG)允许流量流向 SQL 托管实例。 有关详细信息,请参阅网络安全组权限。
启用公共终结点
可以使用 Azure 门户、Azure PowerShell 或 Azure CLI 为 SQL 托管实例启用公共终结点。
要在 Azure 门户中为 SQL 托管实例启用公共终结点,请执行下列步骤:
- 转到 Azure 门户。
- 使用 SQL 托管实例打开资源组,然后选择要在其中配置公共终结点的 SQL 托管实例 。
- 在“安全”设置中,选择“网络”选项卡。
- 在“虚拟网络配置”页中,选择“ 启用”,然后选择 “保存” 图标以更新配置。
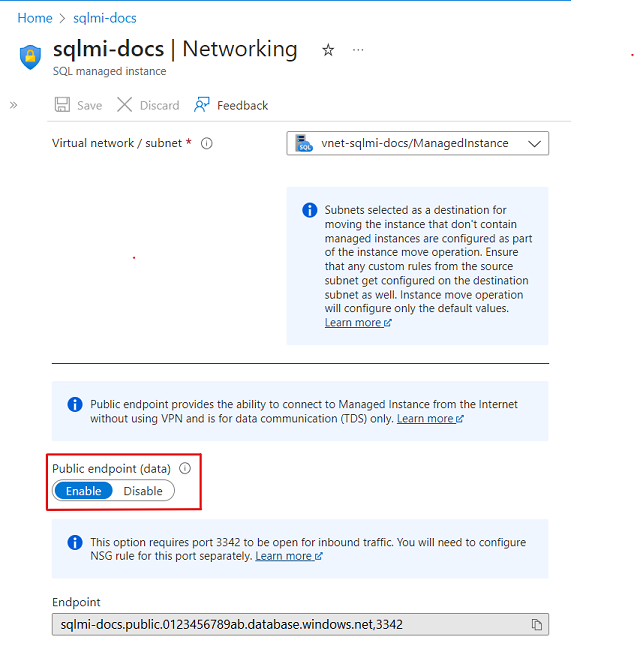
禁用公共终结点
可以使用 Azure 门户、Azure PowerShell 和 Azure CLI 为 SQL 托管实例禁用公共终结点。
若要使用 Azure 门户禁用公共终结点,请执行以下步骤:
- 转到 Azure 门户。
- 使用 SQL 托管实例打开资源组,然后选择要在其中配置公共终结点的 SQL 托管实例 。
- 在“安全”设置中,选择“网络”选项卡。
- 在“虚拟网络配置”页中,选择“ 禁用”,然后选择 “保存” 图标以更新配置。
在网络安全组上允许公共终结点流量
使用 Azure 门户允许网络安全组中的公共流量。 执行以下步骤:
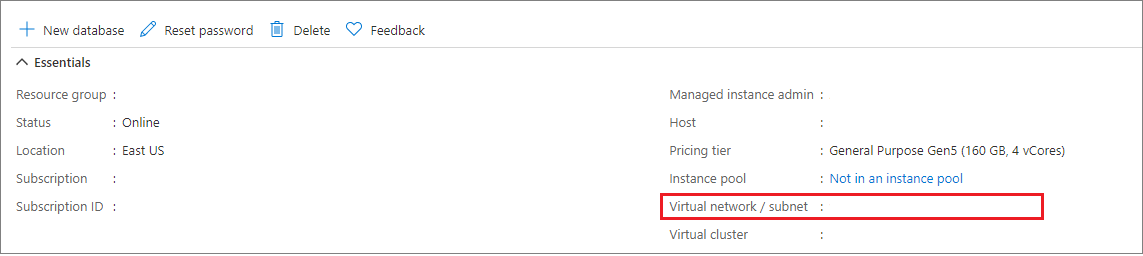
在 Azure 门户中,转到 SQL 托管实例的“概述”页。
选择“虚拟网络/子网”链接,然后你将转到“虚拟网络配置”页。
在虚拟网络的配置窗格中选择“ 子网 ”选项卡,并记下 SQL 托管实例的 安全组 名称。
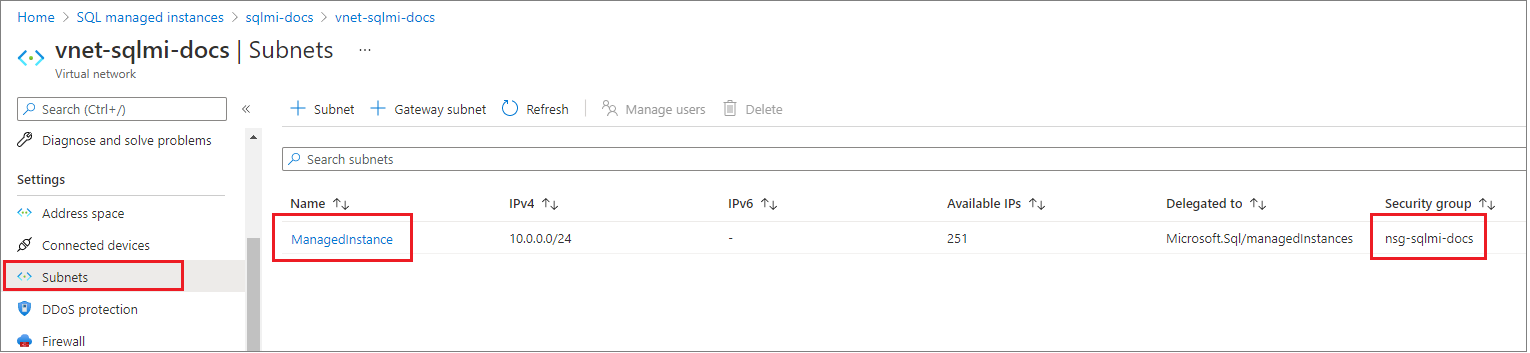
返回到包含 SQL 托管实例的资源组。 你应该会看到上面记下的网络安全组名称。 选择“网络安全组”名称,打开“网络安全组”配置页。
选择“入站安全规则”选项卡,并添加一条优先级高于deny_all_inbound规则的新规则,配置如下:
设置 建议值 说明 Source 任何 IP 地址或服务标记 - 对于 Power BI 等 Azure 服务,请选择“Azure 云服务标记”
- 对于你的计算机或 Azure 虚拟机,请使用 NAT IP 地址
源端口范围 * 请将此保留为 *(任何),因为源端口通常是动态分配的,因而也是不可预测的 目标 任意 将目标保留为 Any,以允许流量进入子网的 SQL 托管实例。 目标端口范围 3342 将目标端口范围限定为 3342,即 SQL 托管实例的公共 TDS 终结点 协议 TCP SQL 托管实例对 TDS 使用 TCP 协议 操作 允许 允许通过公共终结点向 SQL 托管实例的入站流量 Priority 1300 请确保此规则的优先级高于 deny_all_inbound 规则 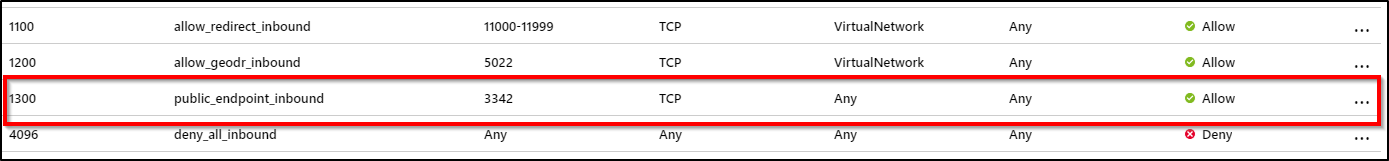
注意
端口 3342 用于与 SQL 托管实例的公共终结点连接,当前无法更改。
确认路由配置正确
具有 0.0.0.0/0 地址前缀的路由指示 Azure 如何路由发往 IP 地址的流量,该地址不在子网路由表中任何其他路由的地址前缀内。 创建子网时,Azure 会创建地址前缀为“0.0.0.0/0”且下一跃点类型为“Internet”的默认路由。
在不添加必要的路由的情况下重写此默认路由以确保将公共终结点流量直接路由到 Internet 可能会导致非对称路由问题,因为传入流量不会通过虚拟设备/虚拟网络网关流动。 确保通过公共 Internet 访问 SQL 托管实例的所有流量都通过公共 Internet 传回,方法是为每个源添加特定路由,或者将默认路由设置为 0.0.0.0/0 地址前缀作为下一跃点类型返回 Internet 。
如需详细了解更改对此默认路由有何影响,请参阅 0.0.0.0/0 地址前缀。
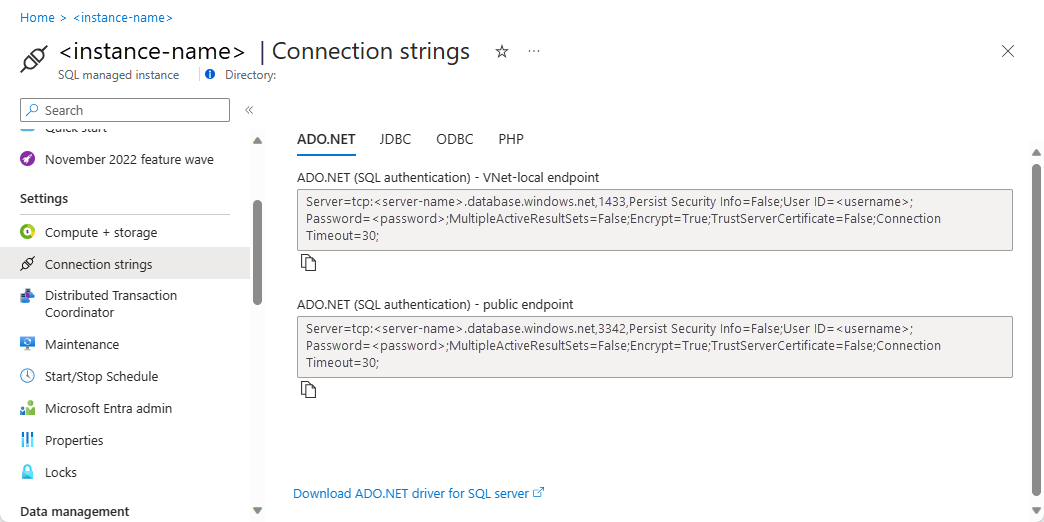
获取公共终结点连接字符串
导航到已为公共终结点启用的 SQL 托管实例配置页。 选择“设置”配置下的“连接字符串”选项卡。
公共终结点主机名采用格式
<mi_name>.public.<dns_zone>.database.chinacloudapi.cn,用于连接的端口为 3342。 下面是表示可在 SQL Server Management Studio 连接中使用的公共终结点端口的连接字符串示例:<mi_name>.public.<dns_zone>.database.chinacloudapi.cn,3342