Azure SQL 托管实例可通过公共终结点进行用户连接。 本文将介绍如何提高此配置的安全性。
方案
Azure SQL 托管实例提供 VNet 本地终结点,用于从其虚拟网络内部启用连接。 默认选项是提供最大的隔离性。 但在某些情况下,需要提供公共终结点连接:
- SQL 托管实例必须与仅限多租户的平台即服务(PaaS)产品/服务集成。
- 所需的数据交换吞吐量高于 VPN 所能提供的吞吐量。
- 公司政策禁止在企业网络中使用 PaaS。
无论连接类型设置如何,公共终结点始终使用 代理连接类型 。
部署用于公共终结点访问的 SQL 托管实例
尽管不是强制性的,但具有公共终结点访问权限的 SQL 托管实例的常见部署模型是在专用隔离虚拟网络中创建实例。 在此配置中,虚拟网络只是用于实现虚拟群集隔离。 SQL 托管实例的 IP 地址空间是否与企业网络的 IP 地址空间重叠并不重要。
保护动态数据
如果客户端驱动程序支持加密,则始终加密 SQL 托管实例数据流量。 在 SQL 托管实例和其他 Azure 虚拟机或 Azure 服务之间发送的数据永远不会离开 Azure 的主干。 如果 SQL 托管实例与本地网络之间存在连接,建议使用 Azure ExpressRoute。 ExpressRoute 有助于避免通过公共 Internet 移动数据。 对于 SQL 托管实例本地连接,只能使用专用对等互连。
锁定入站和出站连接
下图显示了建议的安全配置:
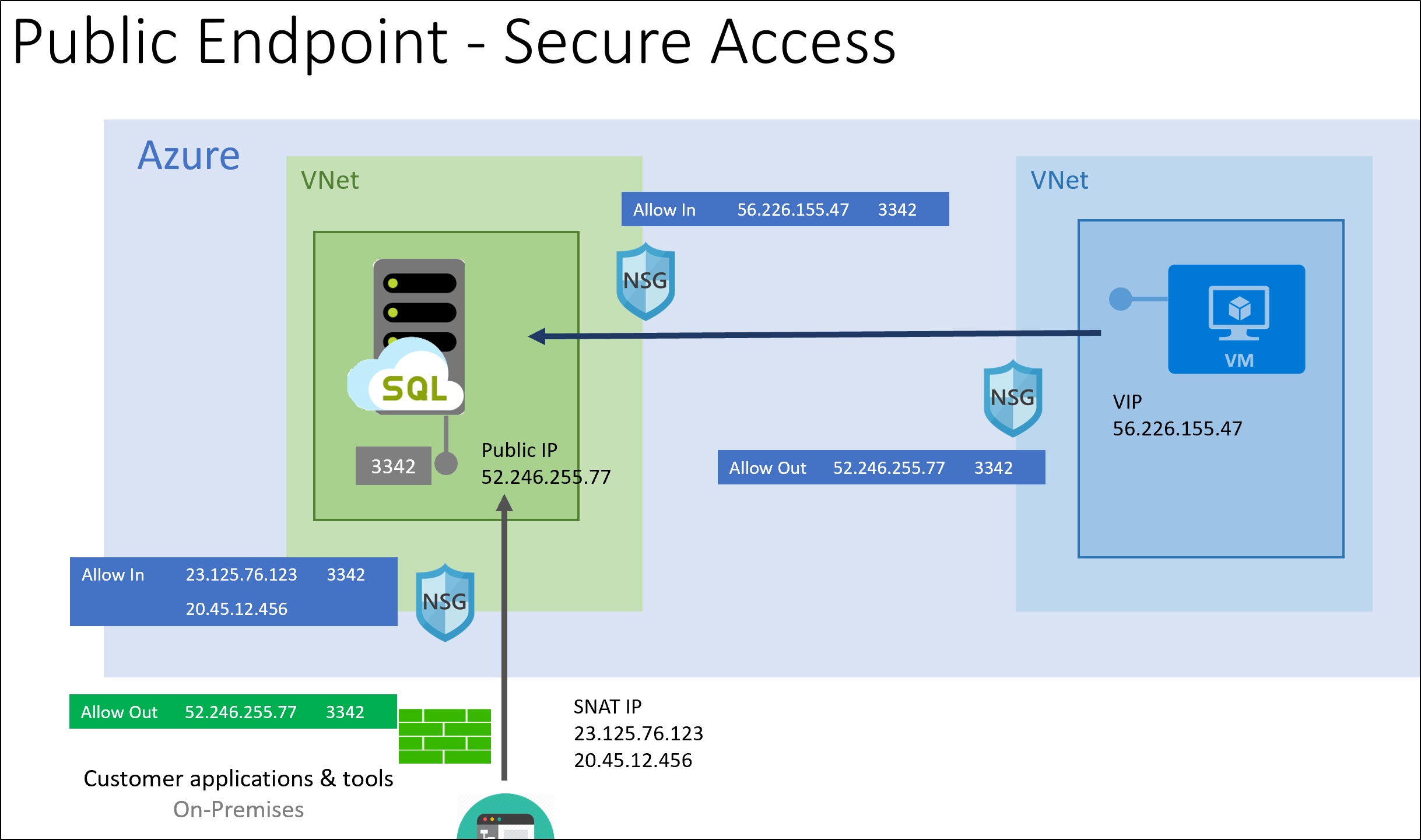
SQL 托管实例具有专用于客户的公共终结点地址。 此终结点与管理终结点共享 IP 地址,但使用不同的端口。 与 VNet 本地终结点类似,公共终结点在某些管理作后可能会更改。 始终通过解析终结点 FQDN 记录来确定公共终结点地址。 例如,配置应用程序级防火墙规则时。
为了确保流向 SQL 托管实例的流量来自受信任的源,建议从具有已知 IP 地址的源进行连接。 使用网络安全组限制对端口 3342 上的 SQL 托管实例公共终结点的访问。
如果客户端需要从本地网络发起连接,请确保发起地址可转换为一组已知的 IP 地址。 如果无法执行此作(例如,移动员工是典型方案),建议使用 点到站点 VPN 连接和 VNet 本地终结点。
如果连接是从 Azure 发起的,我们建议从分配的已知虚拟 IP 地址(例如虚拟机)发出流量。 为便于管理虚拟 IP (VIP) 地址,建议使用公共 IP 地址前缀。