默认情况下,Azure 容器注册表接受来自任何网络上的主机的 Internet 连接。 本文介绍如何将容器注册表配置为仅允许来自特定公共 IP 地址或地址范围的访问。 它使用 Azure CLI 和 Azure 门户提供等效的步骤。
IP 网络规则在公共注册表终结点上进行配置。 IP 网络规则不适用于配置有专用链接的专用终结点。
可在“高级”容器注册表服务层级配置 IP 访问规则。 有关注册表服务层级和限制的信息,请参阅 Azure 容器注册表层级。
每个注册表最多支持 200 个 IP 访问规则。
重要
某些功能可能不可用,或者需要在容器注册表中进行更多配置,以限制对专用终结点、选定子网或 IP 地址的访问。
- 在禁止公用网络访问注册表时,某些受信任的服务(包括 Azure 安全中心)访问注册表就需要启用某个网络设置来绕过网络规则。
- 禁用公用网络访问后,某些 Azure 服务(包括 Azure DevOps 服务)的实例当前无法访问容器注册表。
- Azure DevOps 托管代理当前不支持专用终结点。 需要使用与专用终结点建立了网络直通的自托管代理。
- 如果注册表具有已批准的专用终结点,并且公用网络访问已禁用,则无法使用 Azure 门户、Azure CLI 或其他工具在虚拟网络外部列出存储库和标记。
从所选的公用网络进行访问 - CLI
更改默认网络对注册表的访问权限
要将访问权限仅授予所选公用网络,请先将默认操作更改为拒绝访问。 在以下 az acr update 命令中,替换注册表的名称:
az acr update --name myContainerRegistry --default-action Deny
向注册表添加网络规则
使用 az acr network-rule add 命令向注册表添加允许从公共 IP 地址或范围进行访问的网络规则。 例如,替换容器注册表的名称和虚拟网络中 VM 的公共 IP 地址。
az acr network-rule add \
--name mycontainerregistry \
--ip-address <public-IP-address>
注意
添加规则后,请等待几分钟,使规则生效。
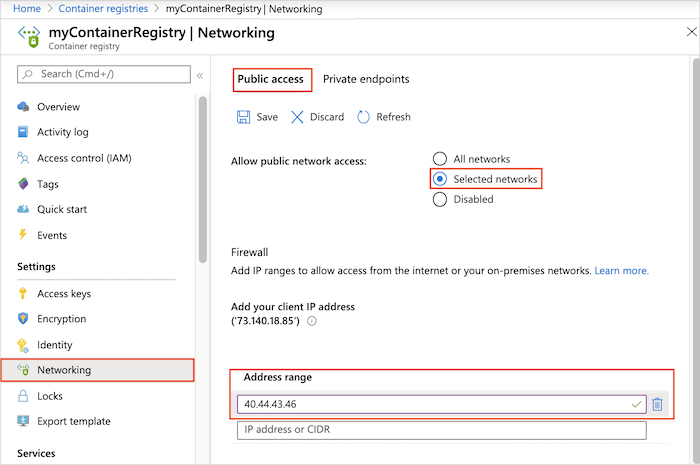
从所选的公用网络访问 - 门户
在门户中,导航到容器注册表。
在“设置”下选择“网络” 。
在“公共访问”选项卡上,选择允许从“所选网络”进行公共访问 。
在“防火墙”下,输入公共 IP 地址,如虚拟网络中 VM 的公共 IP 地址。 或者,以 CIDR 表示法输入包含 VM IP 地址的地址范围。
选择“保存”。
注意
添加规则后,请等待几分钟,使规则生效。
提示
或者,也可通过本地客户端计算机或 IP 地址范围启用注册表访问。 要允许此访问,需要计算机的公共 IPv4 地址。 可通过在 Internet 浏览器中搜索“我的 IP 地址是多少”来查找此地址。 在门户中的“网络”页面上配置防火墙设置时,当前客户端 IPv4 地址也会自动出现。
禁用公用网络访问
(可选)禁用注册表上的公共终结点。 禁用公共终结点会重写所有防火墙配置。 例如,建议使用专用链接禁用对虚拟网络中受保护注册表的公共访问。
注意
如果在虚拟网络中使用服务终结点设置了注册表,则禁用对注册表的公共终结点的访问也会在虚拟网络中禁用对注册表的访问。
禁用公共访问 - CLI
若要使用 Azure CLI 禁用公共访问,请运行 az acr update,并将 --public-network-enabled 设置为 false。
public-network-enabled 参数需要 Azure CLI 2.6.0 或更高版本。
az acr update --name myContainerRegistry --public-network-enabled false
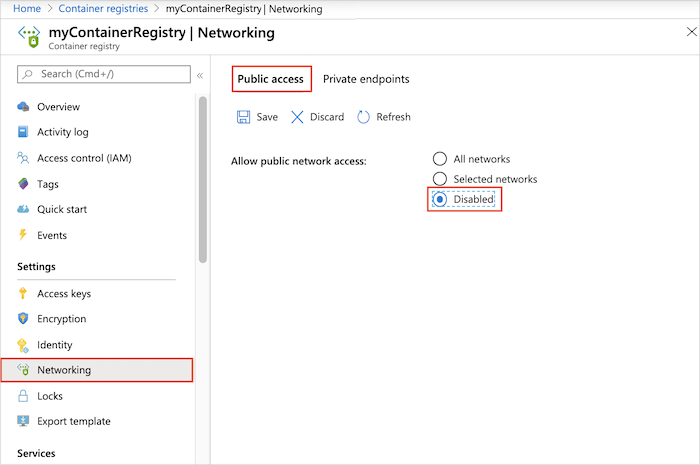
禁用公共访问 - 门户
在门户中,导航到容器注册表,选择“设置”>“网络”。
在“公共访问”选项卡上的“允许公用网络访问”中,选择“禁用” 。 再选择“保存”。
还原公用网络访问
要重新启用公共终结点,请更新网络设置以允许公共访问。 启用公共终结点会重写所有防火墙配置。
还原公共访问 - CLI
运行 az acr update 并将 --public-network-enabled 设置为 true。
注意
public-network-enabled 参数需要 Azure CLI 2.6.0 或更高版本。
az acr update --name myContainerRegistry --public-network-enabled true --default-action Allow
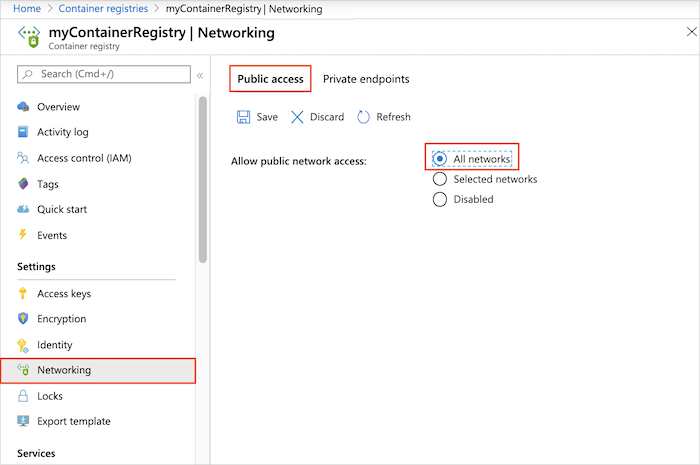
还原公共访问 - 门户
在门户中,导航到容器注册表,选择“设置”>“网络”。
在“公共访问”选项卡上的“允许公用网络访问”中,选择“所有网络” 。 再选择“保存”。
故障排除
从 HTTPS 代理后面进行访问
如果设置公共网络规则或拒绝对注册表的公共访问,则无法从不允许的公共网络登录到注册表。 如果未为代理设置访问规则,则来自 HTTPS 代理后面的客户端访问也会失败。 你会看到类似于Error response from daemon: login attempt failed with status: 403 Forbidden或Looks like you don't have access to registry的错误信息。
如果使用网络访问规则允许的 HTTPS 代理,但在客户端环境中未正确配置代理,则也会发生这些错误。 检查 Docker 客户端和 Docker 守护程序均已针对代理行为进行了配置。 有关详细信息,请参阅 Docker 文档中的 HTTP/HTTPS 代理。
从 Azure Pipelines 进行的访问
如果将 Azure Pipelines 用于限制对特定 IP 地址的访问的 Azure 容器注册表,则管道可能无法访问注册表。 管道中的出站 IP 地址未修复。 默认情况下,管道会使用 Microsoft 托管的代理在具有一组变化的 IP 地址的虚拟机池上运行作业。
一种解决方法是将用于运行管道的代理从 Microsoft 托管的代理更改为自托管代理。 使用在您管理的 Windows 或 Linux 计算机上运行的自承载代理,您可以控制管道的出站 IP 地址。 可以在注册表 IP 访问规则中添加此地址。
从 AKS 访问
如果将 AKS Azure Kubernetes 服务 (AKS) 与限制对特定 IP 地址的访问的 Azure 容器注册表结合使用,则默认情况下无法配置固定的 AKS IP 地址。 从 AKS 群集的出口 IP 地址是随机分配的。
若要允许 AKS 群集访问注册表,请使用以下选项之一:
后续步骤
- 要使用虚拟网络中的专用终结点限制对注册表的访问,请参阅为 Azure 容器注册表配置 Azure 专用链接。
- 若要从客户端防火墙后面设置注册表访问规则,请参阅 配置规则以访问防火墙后面的 Azure 容器注册表。
- 有关更多故障排除指南,请参阅排查注册表的网络问题。