本文介绍如何使用 Microsoft Entra 管理中心、Microsoft Graph PowerShell 或 Microsoft Graph API 将 Microsoft Entra 角色分配给用户和组。 还介绍如何在不同范围分配角色,如租户、应用程序注册和管理单元范围。
你可以向用户分配直接和间接角色分配。 如果按组成员身份向用户分配了角色,则在相应组中添加该用户以添加角色分配。 有关详细信息,请参阅使用 Microsoft Entra 组来管理角色分配。
在 Microsoft Entra ID 中,角色通常分配适用于整个租户。 但是,还可以为不同的资源(例如应用程序注册或管理单元)分配Microsoft Entra 角色。 例如,你可以分配支持管理员角色,以便它仅适用于特定的管理单元,而不是整个租户。 角色分配适用的资源也称为范围。 限制角色分配范围的功能适用于内置角色和自定义角色。 有关范围的详细信息,请参阅 Microsoft Entra ID中
PIM 中的 Microsoft Entra 角色
如果你有一个Microsoft Entra ID P2 许可证和 Privileged Identity Management (PIM),则分配角色时具有其他功能,例如,使用户有资格获得角色分配或定义角色分配的开始和结束时间。 有关在 PIM 中分配Microsoft Entra 角色的信息,请参阅以下文章:
| 方法 | 信息 |
|---|---|
| Microsoft Entra 管理中心 | 在 Privileged Identity Management 中分配 Microsoft Entra 角色 |
| Microsoft Graph PowerShell | 教程:使用 Microsoft Graph PowerShell 在 Privileged Identity Management 中分配 Microsoft Entra 角色 |
| Microsoft图形 API |
使用 PIM API 管理 Microsoft Entra 角色分配 在 Privileged Identity Management 中分配 Microsoft Entra 角色 |
先决条件
- 特权角色管理员
- 使用 PowerShell 时的 Microsoft Graph PowerShell 模块
有关详细信息,请参阅使用 PowerShell 的先决条件。
分配租户范围的角色
本部分介绍如何在租户范围分配角色。
至少以特权角色管理员身份登录到 Microsoft Entra 管理中心。
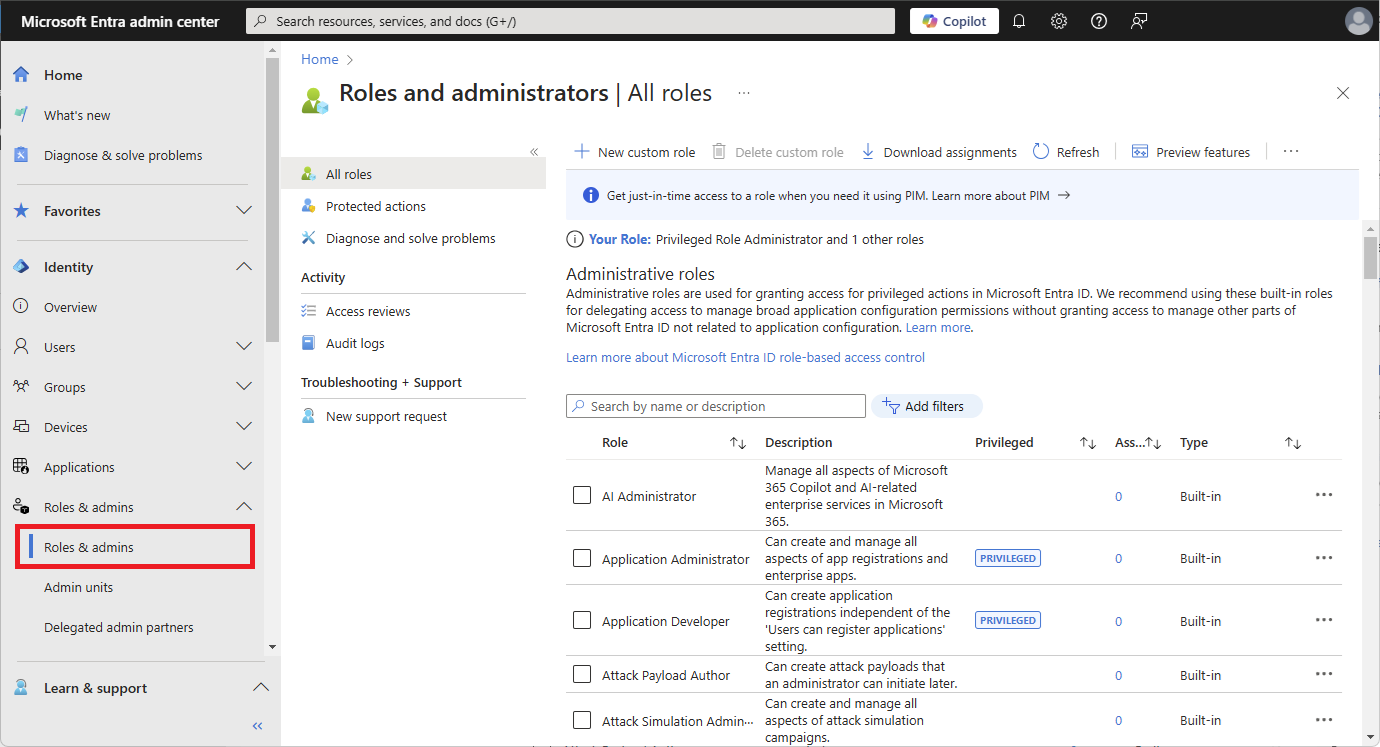
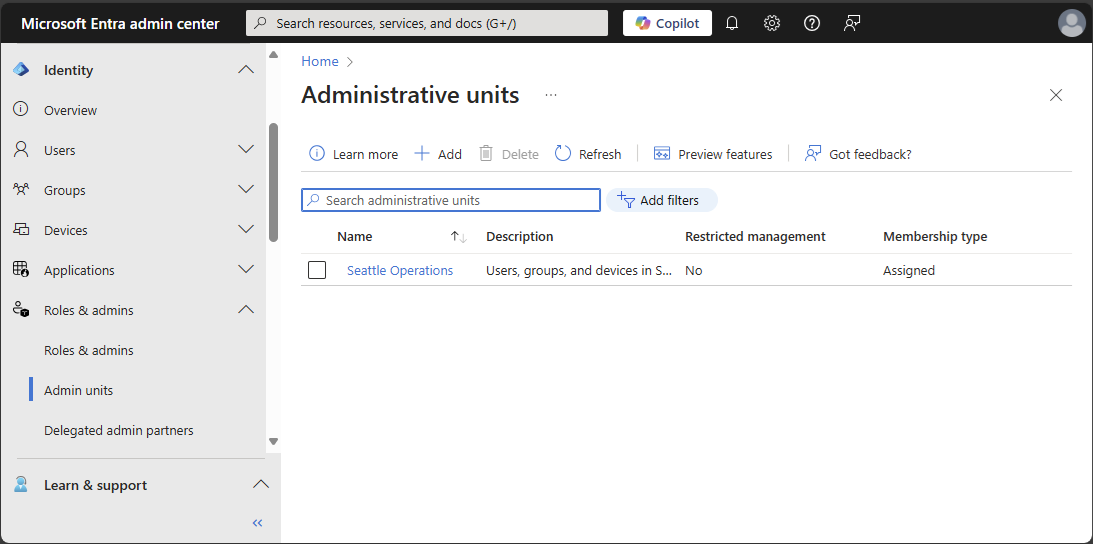
导航到 Entra ID>角色和管理员。
选择角色名称以打开该角色。 不要勾选该角色。
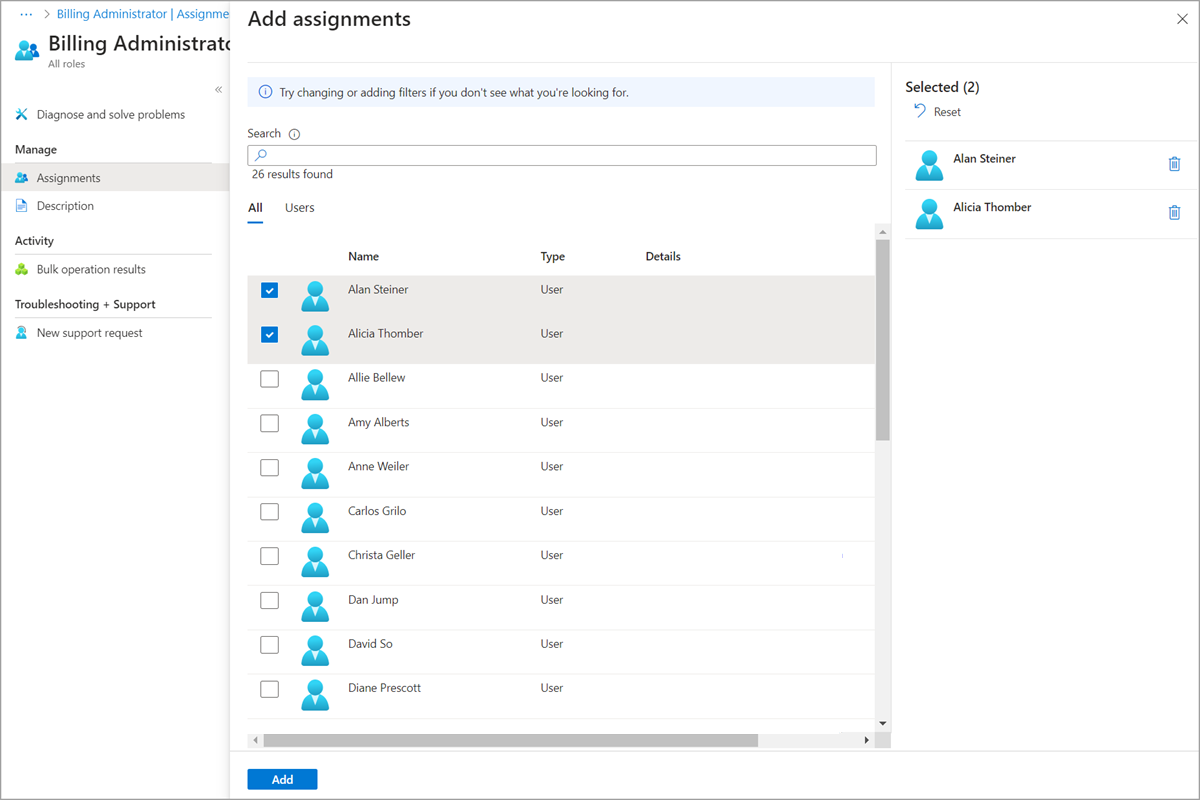
选择 添加任务,然后选择要分配给此角色的用户或组。
只会显示可分配角色的组。 如果未列出组,则需要创建可分配角色的组。
如果您的体验不同于以下的屏幕截图,可能是因为您有 Microsoft Entra ID P2 和 PIM。 有关详细信息,请参阅在 Privileged Identity Management 中分配 Microsoft Entra 角色。
选择“”,再选择“”以分配角色。
分配应用注册范围的角色
默认情况下在租户范围内分配内置角色和自定义角色,以授予对组织中所有应用注册的访问权限。 此外,还可以在单个Microsoft Entra 资源的范围内分配自定义角色和一些相关的内置角色(具体取决于Microsoft Entra 资源的类型)。 这样,用户就有权更新单个应用的凭据和基本属性,而无需创建第二个自定义角色。
本部分介绍如何在应用程序注册范围内分配角色。
请至少以 应用程序开发人员的身份登录到 Microsoft Entra 管理中心。
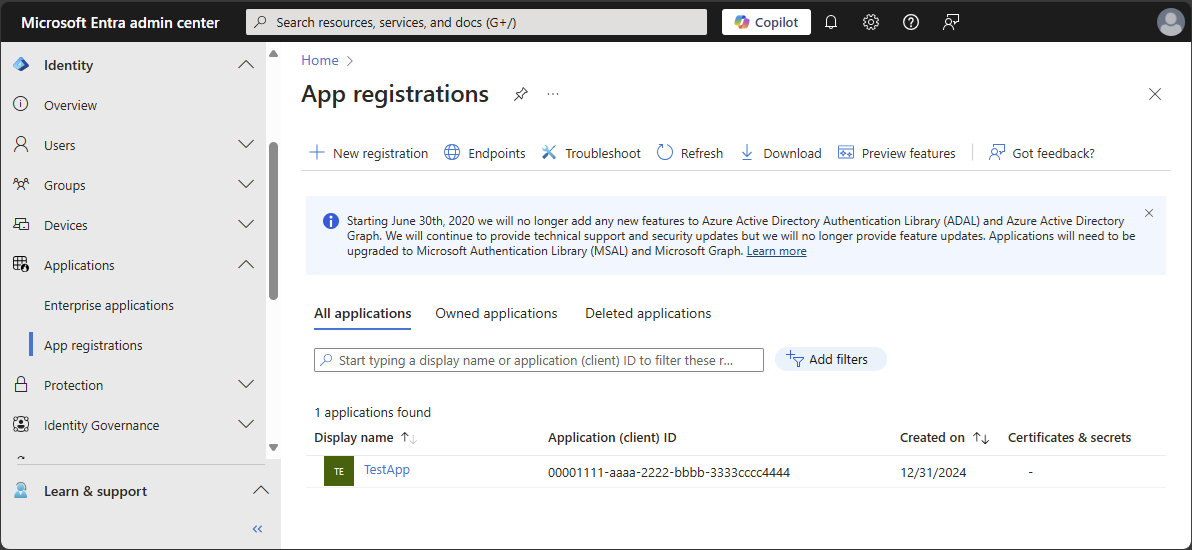
访问 Entra ID>应用注册。
选择应用程序。 可以使用搜索框查找所需的应用。
可能需要选择 所有应用程序 才能查看租户中应用注册的完整列表。
从左侧导航菜单中选择 角色和管理员,以查看可通过应用注册分配的所有角色的列表。
选择所需的角色。
小窍门
此处看不到Microsoft Entra 内置角色或自定义角色的完整列表。 这是预期的。 我们显示了与仅管理应用注册相关的权限的角色。
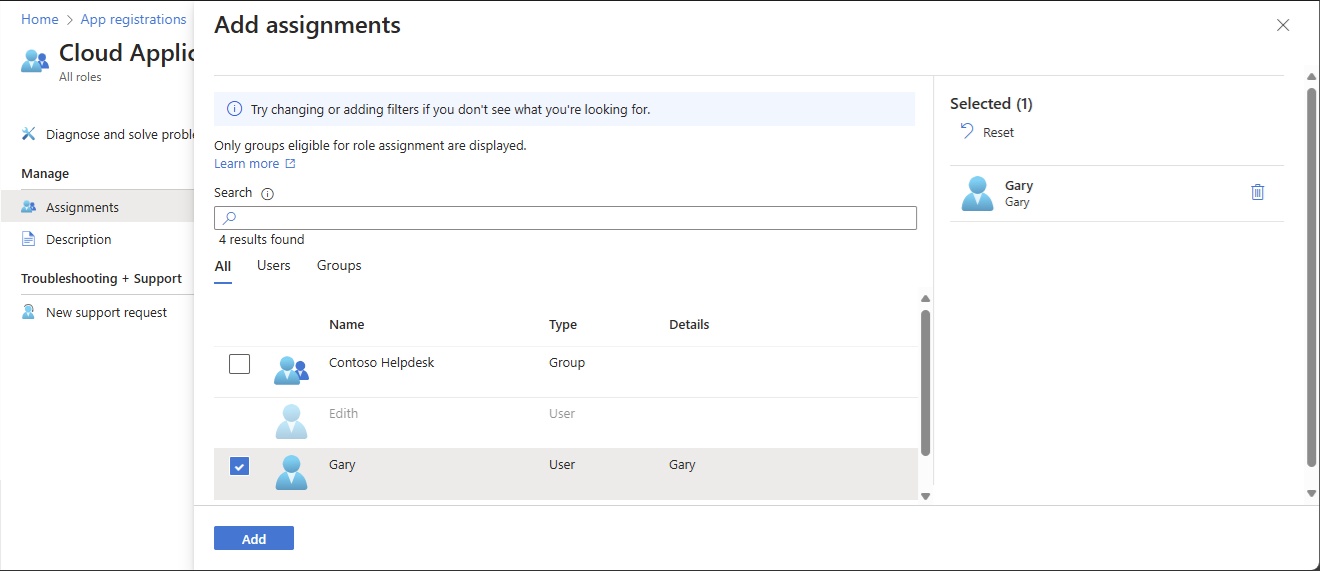
选择“添加分配”,然后选择要向其分配此角色的用户或组。
选择“添加”分配以应用注册为作用域的角色。
分配角色并设定管理单元范围
在Microsoft Entra ID 中,若要进行更精细的管理控制,可以分配一个Microsoft Entra 角色,该角色的范围限制为一个或多个 管理单元。 在管理单元范围内分配Microsoft Entra 角色时,角色权限仅适用于管理单元本身的成员,并且不适用于租户范围的设置或配置。
例如,在管理单元范围内分配组管理员角色的管理员可以管理属于管理单元成员的组,但他们不能管理租户中的其他组。 它们也不能管理与组相关的租户级别设置,例如过期策略或组命名策略。
本部分介绍如何分配管理单元范围的 Microsoft Entra 角色。
先决条件
- 每个管理单元管理员需要配备 Microsoft Entra ID P1 或 P2 许可证。
- Microsoft Entra ID 免费许可证适用于管理单元成员
- 特权角色管理员
- 使用 PowerShell 时的 Microsoft Graph PowerShell 模块
有关详细信息,请参阅使用 PowerShell 的先决条件。
可在管理单位范围分配的角色
可为以下 Microsoft Entra 角色分配管理单元范围。 此外,只要自定义角色的权限至少包含一个与用户、组或设备相关的权限,就可以将任何 自定义角色 分配在管理单元范围内。
| 角色 | DESCRIPTION |
|---|---|
| 身份验证管理员 | 仅可访问并查看、设置和重置分配的管理单元中的非管理员用户的身份验证方法信息。 |
| 属性分配管理员 | 只能读取和更新管理单元中用户或服务主体的自定义安全属性分配(来自任何属性集)。 |
| 属性分配读取器 | 只能读取管理单元中用户或服务主体的自定义安全属性(从任何属性集)。 |
| 云设备管理员 | 在 Microsoft Entra ID 中对设备进行管理的权限有限。 |
| 组管理员 | 只能在分配的管理单元中管理组的所有方面。 |
| 支持管理员 | 只能为分配的管理单元中的非管理员重置密码。 |
| 许可证管理员 | 只能在管理单元内分配、删除和更新许可证分配。 |
| 密码管理员 | 只能为分配的管理单元中的非管理员重置密码。 |
| 打印机管理员 | 可以管理打印机和打印机连接器。 有关详细信息,请参阅在通用打印中委派打印机管理。 |
| 特权身份验证管理员 | 可以访问以查看、设置和重置任何用户(管理员或非管理员)的身份验证方法信息。 |
| SharePoint 管理员 | 只能在分配的管理单元中管理Microsoft 365 个组。 对于与管理单元中Microsoft 365 组关联的 SharePoint 网站,还可以使用 Microsoft 365 管理中心更新网站属性(网站名称、URL 和外部共享策略)。 无法使用 SharePoint 管理中心或 SharePoint API 来管理网站。 |
| Teams 管理员 | 只能在分配的管理单元中管理Microsoft 365 个组。 可以在 Microsoft 365 管理中心内管理与指定管理单元中的组关联的团队成员。 无法使用 Teams 管理中心。 |
| Teams 设备管理员 | 可以在 Teams 认证设备上执行管理相关任务。 |
| 用户管理员 | 可以管理用户和组的所有方面,包括仅为分配的管理单元中的有限管理员重置密码。 当前无法管理用户的个人资料照片。 |
| <自定义角色> | 可以根据自定义角色的定义,执行应用于用户、组或设备的操作。 |
当与管理单元范围一起分配时,某些角色权限仅适用于非管理员用户。 换言之,仅当用户没有管理员角色时,管理单元范围的支持管理员才能在管理单元中重置这些用户的密码。 当操作的目标是另一个管理员时,以下权限列表受到限制:
- 读取和修改用户身份验证方法,或重置用户密码
- 修改敏感用户属性,如电话号码、备用电子邮件地址或打开授权(OAuth)密钥
- 删除或还原用户帐户
可在管理单位范围分配的安全主体
可以将以下安全主体分配给具有管理单元范围的角色:
- 用户
- Microsoft Entra 可分配角色的组
- 服务主体
服务主体和来宾用户
服务主体和来宾用户将无法使用范围为管理单元的角色分配,除非他们还被分配了读取对象的相应权限。 这是因为服务主体和来宾用户默认情况下不会收到目录读取权限,这是执行管理操作所必需的。 若要使服务主体或来宾用户能够使用作用域为管理单元的角色分配,必须分配租户范围内的目录读取者角色(或其他角色,该角色包括读取权限)。
目前无法将目录读取权限分配给特定的管理单元。 有关用户的默认权限的详细信息,请参阅 默认用户权限。
分配角色并设定管理单元范围
本部分介绍如何在管理单元范围内分配角色。
至少以特权角色管理员身份登录到 Microsoft Entra 管理中心。
浏览到 Entra ID>角色与管理员>管理单元。
选择一个管理单元。
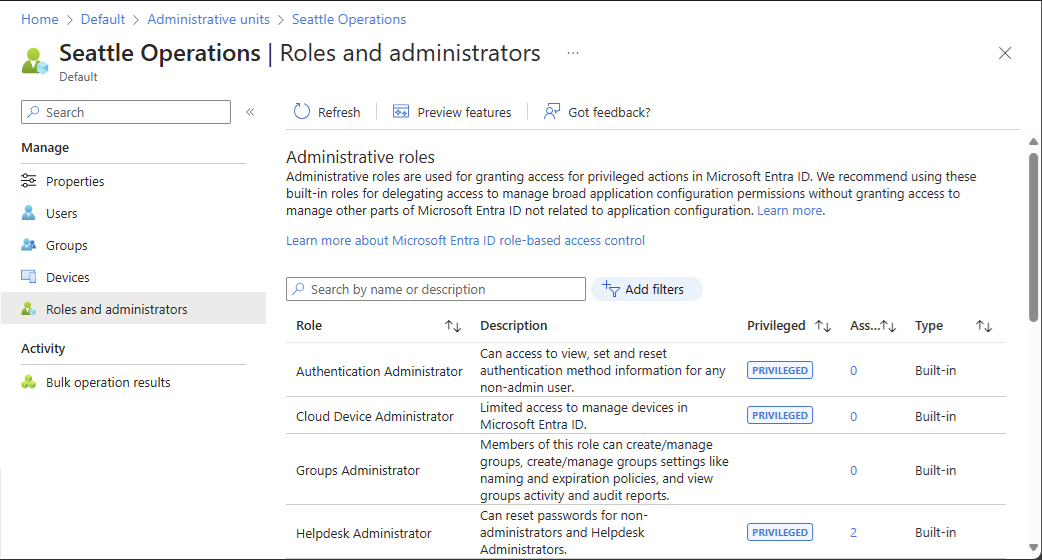
从左侧导航菜单中选择 角色和管理员,以查看可在管理单元上分配的所有角色的列表。
选择所需的角色。
小窍门
此处看不到Microsoft Entra 内置角色或自定义角色的完整列表。 这是预期的。 我们展示了哪些角色具有与管理单元中支持的对象相关的权限。 若要查看管理单元中支持的对象列表,请参阅Microsoft Entra ID中的
管理单元。 选择“添加分配”,然后选择要向其分配此角色的用户或组。
选择“添加”分配以管理单元为作用域的角色。