本文介绍如何使用 Microsoft Entra ID 来保护事件订阅和 Webhook 终结点之间的连接。 这里使用 Azure 门户进行演示,但该功能也可通过 CLI、PowerShell 或 SDK 来启用。
重要
2021 年 3 月 30 日,事件创建或更新中引入了附加访问检查,以解决安全漏洞。 订阅服务器客户端的服务主体需要是所有者或已分配有目标应用程序服务主体中的角色。 按照以下新说明重新配置 Microsoft Entra 应用程序。有关 Microsoft Entra 应用程序和服务主体的概述,请参阅 Microsoft 标识平台 (v2.0) 概述。
方案
本文详细介绍了如何实现以下两种方案:
将事件传送到与事件订阅相同的 Microsoft Entra 租户中的 Webhook。 在这种方案中,可以使用 Microsoft Entra 用户或 Microsoft Entra 应用程序作为事件订阅写入者。
将事件传送到与事件订阅不同的 Microsoft Entra 租户中的 Webhook。 在这种方案中,只能将 Microsoft Entra 应用程序用作事件订阅写入者。
在第一种方案中,需在包含事件订阅和 Webhook 的单个租户中运行所有步骤或脚本。 在第二种方案中,需在包含事件订阅的租户中运行一些步骤,并在包含 Webhook 的租户中运行一些步骤。
将事件传送到同一 Microsoft Entra 租户中的 Webhook
下图描绘了如何将事件网格事件传送到与事件订阅相同的租户中的 Webhook。
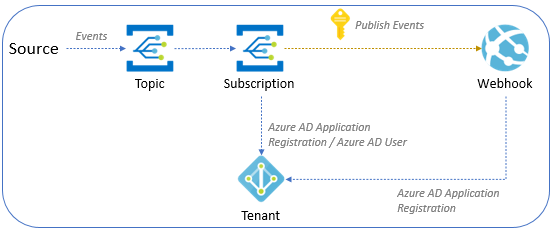
本部分有两个子部分。 请通读这两种方案或你感兴趣的方案。
使用 Microsoft Entra 用户配置事件订阅
本部分介绍如何使用 Microsoft Entra 用户配置事件订阅。
为已配置为使用 Microsoft Entra(单租户)的 Webhook 创建一个 Microsoft Entra 应用程序。
打开 PowerShell 环境。
修改 $webhookAadTenantId 的值以连接到该租户。
- 变量:
- $webhookAadTenantId:Azure 租户 ID
$webhookAadTenantId = "[REPLACE_WITH_YOUR_TENANT_ID]" Connect-MgGraph -TenantId $webhookAadTenantId -Scopes "Application.ReadWrite.All, AppRoleAssignment.ReadWrite.All"- 变量:
打开以下脚本,并使用你的标识符更新 $webhookAppObjectId 和$eventSubscriptionWriterUserPrincipalName 的值,然后继续运行该脚本 。
- 变量:
- $webhookAppObjectId:为 Webhook 创建的 Microsoft Entra 应用程序 ID
- $eventSubscriptionWriterUserPrincipalName:创建事件订阅的用户的 Azure 用户主体名称
注意
无需修改 $eventGridAppId 的值。 在此脚本中会为 $eventGridRoleName 设置 AzureEventGridSecureWebhookSubscriber。 请记住,要执行此脚本,你必须是 Microsoft Entra 应用程序管理员角色的成员,或者是 Microsoft Entra ID 中 Webhook 应用的服务主体的所有者。
如果看到以下错误消息,则需要提升到服务主体。 2021 年 3 月 30 日,我们在事件订阅的创建或更新中引入了附加访问检查,以解决安全漏洞。 订阅服务器客户端的服务主体需要是所有者或已分配有目标应用程序服务主体中的角色。
New-MgServicePrincipalAppRoleAssignment: Error occurred while executing NewServicePrincipalAppRoleAssignment Code: Authorization_RequestDenied Message: Insufficient privileges to complete the operation.- 变量:
在门户中创建事件订阅时,请执行以下步骤:
选择“Web Hook”作为终结点类型。
指定终结点 URI。
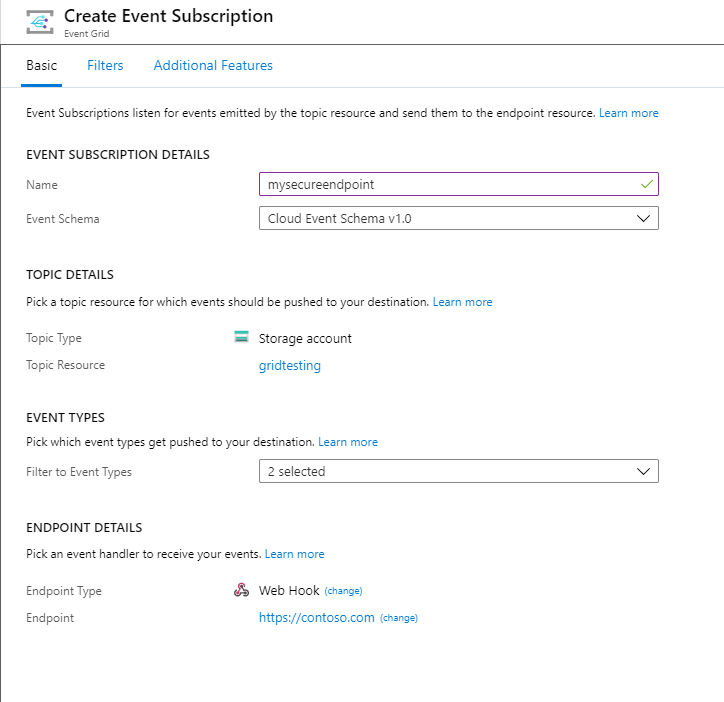
选择“创建事件订阅”页顶部的“其他功能”选项卡 。
在“其他功能”选项卡上,执行以下步骤:
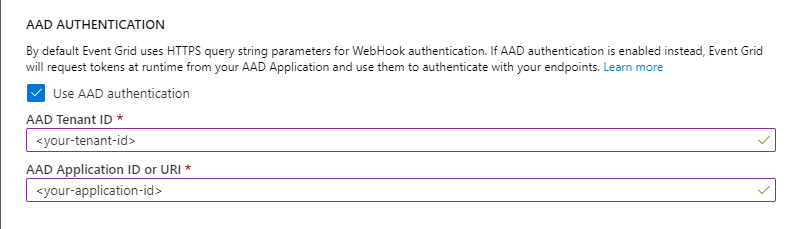
选择“使用 Microsoft Entra 身份验证”,并配置租户 ID 和应用程序 ID:
从脚本输出中复制 Microsoft Entra 租户 ID,将其输入“Microsoft Entra 租户 ID”字段中。
从脚本输出中复制 Microsoft Entra 应用程序 ID,将其输入“Microsoft Entra 应用程序 ID”字段中。 你可以使用 Microsoft Entra 应用程序 ID URI,而不是使用应用程序 ID。 有关应用程序 ID URI 的详细信息,请参阅本文。
使用 Microsoft Entra 应用程序配置事件订阅
本部分介绍如何使用 Microsoft Entra 应用程序配置事件订阅。
为已配置为使用 Microsoft Entra(单租户)的 Azure 事件网络订阅写入者创建一个 Microsoft Entra 应用程序。
为该 Microsoft Entra 应用程序创建机密并保存此值(稍后需要用到此值)。
转到事件网格主题的“访问控制(IAM)”页,并将“事件网格参与者”角色分配给事件网格订阅写入者应用。 通过执行此步骤,你可以在使用 Azure CLI 通过 Microsoft Entra 应用程序登录到 Azure 后访问 Azure 事件网格资源。
为已配置为使用 Microsoft Entra(单租户)的 Webhook 创建一个 Microsoft Entra 应用程序。
打开 PowerShell 环境。
修改 $webhookAadTenantId 的值以连接到该租户。
- 变量:
- $webhookAadTenantId:Azure 租户 ID
$webhookAadTenantId = "[REPLACE_WITH_YOUR_TENANT_ID]" Connect-MgGraph -TenantId $webhookAadTenantId -Scopes "Application.ReadWrite.All, AppRoleAssignment.ReadWrite.All"- 变量:
打开以下脚本,并使用你的标识符更新 $webhookAppObjectId 和$eventSubscriptionWriterAppId 的值,然后继续运行该脚本 。
- 变量:
- $webhookAppObjectId:为 Webhook 创建的 Microsoft Entra 应用程序 ID
- $eventSubscriptionWriterAppId:Azure 事件网格订阅写入者应用的 Microsoft Entra 应用程序 ID。
注意
无需修改
$eventGridAppId的值。 在此脚本中会为$eventGridRoleName设置 AzureEventGridSecureWebhookSubscriber。 请记住,要执行此脚本,你必须是 Microsoft Entra 应用程序管理员角色的成员,或者是 Microsoft Entra ID 中 Webhook 应用的服务主体的所有者。- 变量:
运行以下命令,以 Azure 事件网格订阅写入者 Microsoft Entra 应用程序的身份登录。
az login --service-principal -u [REPLACE_WITH_EVENT_GRID_SUBSCRIPTION_WRITER_APP_ID] -p [REPLACE_WITH_EVENT_GRID_SUBSCRIPTION_WRITER_APP_SECRET_VALUE] --tenant [REPLACE_WITH_TENANT_ID]运行以下命令以创建订阅。
az eventgrid system-topic event-subscription create --name [REPLACE_WITH_SUBSCRIPTION_NAME] -g [REPLACE_WITH_RESOURCE_GROUP] --system-topic-name [REPLACE_WITH_SYSTEM_TOPIC] --endpoint [REPLACE_WITH_WEBHOOK_ENDPOINT] --event-delivery-schema [REPLACE_WITH_WEBHOOK_EVENT_SCHEMA] --azure-active-directory-tenant-id [REPLACE_WITH_TENANT_ID] --azure-active-directory-application-id-or-uri [REPLACE_WITH_APPLICATION_ID_FROM_SCRIPT] --endpoint-type webhook注意
这种方案使用系统主题。 如果想要使用 Azure CLI 创建自定义主题或域的订阅,请参阅 CLI 参考。
如果正确配置了所有设置,则可以在事件网格主题中成功创建 Webhook 订阅。
注意
Azure 事件网格此时正在每条消息中向 Webhook 客户端传递 Microsoft Entra 持有者令牌。 你需要验证 Webhook 中的授权令牌。
将事件传送到不同 Microsoft Entra 租户中的 Webhook
若要保护位于不同 Microsoft Entra 租户中的事件订阅与 Webhook 终结点之间的连接,你需要如本部分所示使用一个 Microsoft Entra ID 应用程序。 目前,无法在 Azure 门户中使用 Microsoft Entra ID 用户保护此连接。
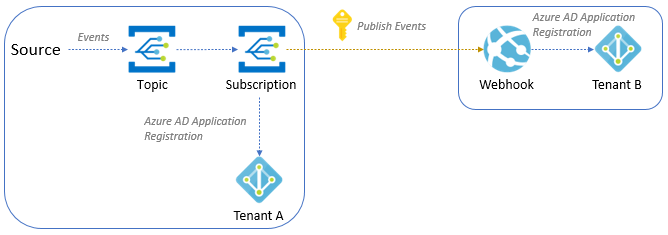
根据该图执行以下步骤来配置两个租户。
租户 A
在租户 A 中执行以下步骤:
为已配置为使用任何 Microsoft Entra(多租户)的 Azure 事件网络订阅写入者创建一个 Microsoft Entra 应用程序。
为该 Microsoft Entra 应用程序创建机密并保存此值(稍后需要用到此值)。
导航到事件网格主题的“访问控制(IAM)”页。 将“Azure 事件网格参与者”角色添加到 Azure 事件网格写入者的 Microsoft Entra 应用程序。 通过执行此步骤,应用程序可以在使用 Azure CLI 通过 Microsoft Entra 应用程序登录到 Azure 后访问 Azure 事件网格资源。
租户 B
在租户 B 中执行以下步骤:
为已配置为使用 Microsoft Entra(单租户)的 Webhook 创建一个 Microsoft Entra 应用程序。
打开 PowerShell 环境。
修改 $webhookAadTenantId 值以连接到租户 B 。
变量:
- $webhookAadTenantId:租户 B 的 Azure 租户 ID
$webhookAadTenantId = "[REPLACE_WITH_YOUR_TENANT_ID]" Connect-MgGraph -TenantId $webhookAadTenantId -Scopes "Application.ReadWrite.All, AppRoleAssignment.ReadWrite.All"
打开以下脚本,并使用你的标识符更新 $webhookAppObjectId 和 $eventSubscriptionWriterAppId 的值,然后继续运行该脚本。
- 变量:
$webhookAppObjectId:为 Webhook 创建的 Microsoft Entra 应用程序 ID
$eventSubscriptionWriterAppId:Azure 事件网格订阅写入者的 Microsoft Entra 应用程序 ID
注意
无需修改
$eventGridAppId的值。 在此脚本中会为$eventGridRoleName设置 AzureEventGridSecureWebhookSubscriber。 请记住,要执行此脚本,你必须是 Microsoft Entra 应用程序管理员角色的成员,或者是 Microsoft Entra ID 中 Webhook 应用的服务主体的所有者。
如果看到以下错误消息,则需要提升到服务主体。 2021 年 3 月 30 日,我们在事件订阅的创建或更新中引入了附加访问检查,以解决安全漏洞。 订阅服务器客户端的服务主体需要是所有者或已分配有目标应用程序服务主体中的角色。
New-MgServicePrincipalAppRoleAssignment: Error occurred while executing NewServicePrincipalAppRoleAssignment Code: Authorization_RequestDenied Message: Insufficient privileges to complete the operation.- 变量:
租户 A
返回到租户 A,执行以下步骤:
打开 PowerShell 并通过运行命令以事件网格订阅写入者 Microsoft Entra 应用程序的身份登录。
az login --service-principal -u [REPLACE_WITH_APP_ID] -p [REPLACE_WITH_SECRET_VALUE] --tenant [REPLACE_WITH_TENANT_ID]运行以下命令以创建订阅。
az eventgrid system-topic event-subscription create --name [REPLACE_WITH_SUBSCRIPTION_NAME] -g [REPLACE_WITH_RESOURCE_GROUP] --system-topic-name [REPLACE_WITH_SYSTEM_TOPIC] --endpoint [REPLACE_WITH_WEBHOOK_ENDPOINT] --event-delivery-schema [REPLACE_WITH_WEBHOOK_EVENT_SCHEMA] --azure-active-directory-tenant-id [REPLACE_WITH_TENANT_B_ID] --azure-active-directory-application-id-or-uri [REPLACE_WITH_APPLICATION_ID_FROM_SCRIPT] --endpoint-type webhook注意
在此方案中,我们使用的是事件网格系统主题。 如果你要使用 Azure CLI 创建自定义主题或事件网格域的订阅,请参阅此文。
如果正确配置了所有设置,则可以在事件网格主题中成功创建 Webhook 订阅。
注意
Azure 事件网格此时正在每条消息中向 Webhook 客户端传递 Microsoft Entra 持有者令牌。 你需要验证 Webhook 中的授权令牌。
后续步骤
- 有关概念性信息,请参阅 WebHook 事件传送。
- 有关监视事件传送的信息,请参阅监视事件网格消息传送。
- 有关身份验证密钥的详细信息,请参阅事件网格安全性和身份验证。
- 有关创建 Azure 事件网格订阅的详细信息,请参阅事件网格订阅架构。