适用于:![]() IoT Edge 1.5
IoT Edge 1.5
重要
IoT Edge 1.5 LTS 是受支持的版本。 IoT Edge 1.4 LTS 的生命周期结束日期为 2024 年 11 月 12 日。 如果你使用的是较低的版本,请参阅更新 IoT Edge。
在透明网关方案中,下游设备(有时称为子设备)需要像任何其他设备一样在 IoT 中心内标识。 本文介绍将下游设备身份验证到 IoT 中心的选项,并演示如何声明网关连接。
注意
下游设备将数据直接发送到 Internet 或网关设备,无论它们是否已启用 IoT Edge。 子设备可以是下游设备,也可以是嵌套拓扑中的网关设备。
成功设置透明网关连接需要完成三个常规步骤。 本文将介绍其中的第二个步骤:
- 将网关设备配置为服务器,以便下游设备能够安全地连接到该设备。 设置网关以接收来自下游设备的消息,并将消息路由到适当的目标。 有关这些步骤,请参阅配置 IoT Edge 设备以充当透明网关。
- 为下游设备创建设备标识,以便它可以向 IoT 中心进行身份验证。 配置下游设备,使其通过网关设备发送消息。
- 将下游设备连接到网关设备并开始发送消息。 有关这些步骤,请参阅将下游设备连接到 Azure IoT Edge 网关。
下游设备可以使用以下三种方法之一向 IoT 中心进行身份验证:对称密钥(有时称为共享访问密钥)、X.509 自签名证书或 X.509 证书颁发机构(CA)签名证书。 身份验证步骤与使用 IoT 中心设置任何非 IoT Edge 设备的步骤类似,在声明网关关系时略有不同。
不支持使用 Azure IoT 中心设备预配服务(DPS)自动预配下游设备。
先决条件
完成 配置 IoT Edge 设备以充当透明网关的步骤。
如果使用 X.509 身份验证,请为下游设备生成证书。 请确保您拥有在透明网关文章中使用的相同根 CA 证书和证书生成脚本。
本文在多个位置提到了“网关主机名”。 网关主机名是在 IoT Edge 网关设备上的配置文件的 主机名 参数中设置的。 它还在下游设备的连接字符串中使用。 网关主机名必须通过使用 DNS 或下游设备上的主机文件项解析为 IP 地址。
将设备注册到 IoT 中心
选择你希望下游设备如何向 IoT 中心进行身份验证:
对称密钥身份验证:IoT 中心会创建一个你放置在下游设备上的密钥。 当设备进行身份验证时,IoT 中心会检查两个密钥是否匹配。 不需创建其他证书便可使用对称密钥身份验证。
如果要在开发或测试场景中测试网关,则此方法有助于更快地开始测试。
X.509 自签名身份验证:有时称为指纹身份验证,因为你与 IoT 中心共享来自设备的 X.509 证书的指纹。
建议在生产场景中对设备进行证书身份验证。
X.509 CA 签名的身份验证:将根 CA 证书上传到 IoT 中心。 当设备提供其 x.509 证书进行身份验证时,IoT 中心会检查它是否属于由同一根 CA 证书签名的信任链。
建议在生产场景中对设备进行证书身份验证。
对称密钥身份验证
对称密钥身份验证(也称为共享访问密钥身份验证)是在 IoT 中心进行身份验证的最简单方法。 使用对称密钥身份验证时,某个 base64 密钥将与 IoT 中心内的 IoT 设备 ID 相关联。 需将该密钥包含在 IoT 应用程序中,使设备在连接到 IoT 中心时可以出示该密钥。
使用 Azure 门户、Azure CLI 或适用于 Visual Studio Code 的 IoT 扩展在 IoT 中心添加新的 IoT 设备。 请记住,需要在 IoT 中心将下游设备标识为常规 IoT 设备,而不是 IoT Edge 设备。
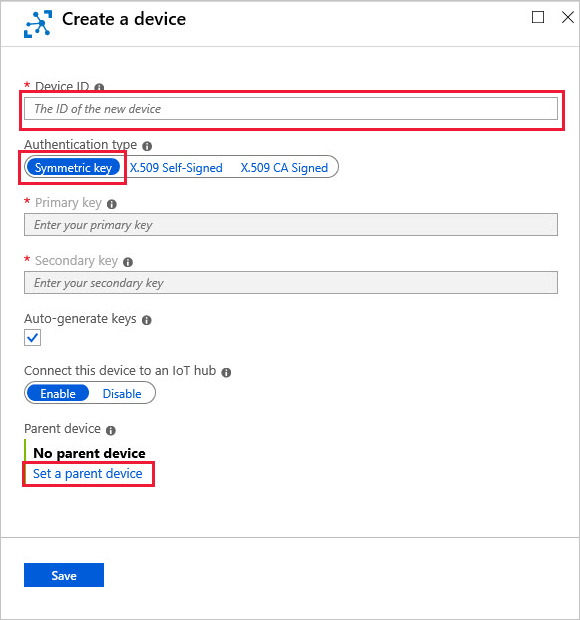
创建新的设备标识时,请提供以下信息:
创建设备的 ID。
选择“对称密钥”作为身份验证类型。
选择 “设置父设备” ,然后选择此下游设备连接的 IoT Edge 网关设备。 之后可以随时更改父设备。
注意
对于使用对称密钥身份验证的下游设备来说,设置父设备曾是一个可选步骤。 但是,从 IoT Edge 版本 1.1.0 开始,每个下游设备都必须分配给父设备。
可以通过将环境变量 AuthenticationMode 设置为值 CloudAndScope 来将 IoT Edge 中心配置为返回到以前的行为 。
还可以使用适用于 Azure CLI 的 IoT 扩展来完成相同的操作。 以下示例使用 az iot hub device-identity 命令创建具有对称密钥身份验证的新 IoT 设备,并分配父设备:
az iot hub device-identity create -n {iothub name} -d {new device ID} --device-scope {deviceScope of parent device}
提示
你可以使用 az iot hub device-identity list --hub-name {iothub name} 来列出包括设备范围在内的设备属性。
接下来,检索并修改连接字符串,从而使设备知道通过其网关进行连接。
X.509 CA 自签名身份验证
对于 X.509 自签名身份验证(有时称为指纹身份验证),你需要创建证书并将其放在下游设备上。 这些证书包含一个指纹,你可以与 IoT 中心共享该指纹以完成身份验证。
使用 CA 证书,为下游设备创建两个设备证书(主要和辅助)。
如果你没有用于创建 X.509 证书的证书颁发机构,可以使用 IoT Edge 演示证书脚本创建下游设备证书。 请按照创建自签名证书的步骤进行操作。 请使用已为网关设备生成证书的同一根 CA 证书。
如果你创建自己的证书,请确保将设备证书的使用者名称设置为你在 Azure IoT 中心注册 IoT 设备时使用的设备 ID。 身份验证需要此设置。
检索每个证书的 SHA1 指纹 - 包含 40 个十六进制字符的字符串。 使用以下 openssl 命令查看证书并查找指纹:
窗户:
openssl x509 -in <path to primary device certificate>.cert.pem -text -fingerprintLinux:
openssl x509 -in <path to primary device certificate>.cert.pem -text -fingerprint | sed 's/[:]//g'
运行此命令两次,一次针对主要证书,另一次针对辅助证书。 使用自签名的 X.509 证书注册新 IoT 设备时,为这两个证书提供指纹。
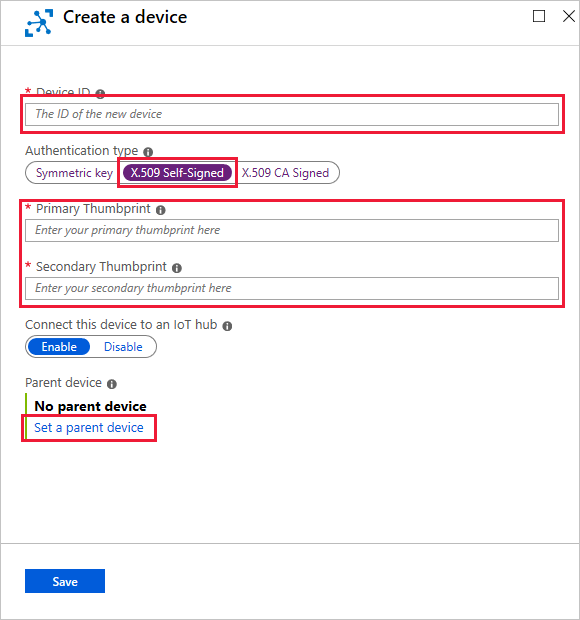
在 Azure 门户中导航到 IoT 中心,并使用以下值创建新的 IoT 设备标识:
- 提供与设备证书的使用者名称匹配的设备 ID。
- 选择“X.509 自签名”作为身份验证类型。
- 粘贴从设备的主要和辅助证书中复制的十六进制字符串。
- 选择 “设置父设备” ,然后选择此下游设备连接的 IoT Edge 网关设备。 之后可以随时更改父设备。
将主要和辅助设备证书及其密钥复制到下游设备上的任何位置。 此外,移动生成网关设备证书和下游设备证书的共享根 CA 证书的副本。
你将在下游设备上连接到 IoT 中心的任何应用程序中引用这些证书文件。 可以使用 Azure Key Vault 之类的服务或安全复制协议之类的功能来移动证书文件。
根据首选语言,查看在 IoT 应用程序中引用 X.509 证书的示例:
- C#: 带链示例的 x509 设备证书
- C:iotedge_downstream_device_sample.c
- Node.js:simple_sample_device_x509.js
- Java:SendEventX509.java
- Python:send_message_x509.py
还可以使用适用于 Azure CLI 的 IoT 扩展来完成相同的设备创建操作。 以下示例使用 az iot hub device-identity 命令创建具有 X.509 自签名身份验证的新 IoT 设备,并分配父设备:
az iot hub device-identity create -n {iothub name} -d {device ID} --device-scope {deviceScope of gateway device} --am x509_thumbprint --ptp {primary thumbprint} --stp {secondary thumbprint}
提示
你可以使用 az iot hub device-identity list --hub-name {iothub name} 来列出包括设备范围在内的设备属性。
接下来,检索并修改连接字符串,从而使设备知道通过其网关进行连接。
X.509 CA 签名的身份验证
对于 X.509 证书颁发机构 (CA) 签名的身份验证,你需要在 IoT 中心注册一个用来为下游设备的证书签名的根 CA 证书。 使用根 CA 证书或其任何中间证书颁发的证书的任何设备都允许进行身份验证。
有关在 IoT 中心使用 X.509 CA 证书进行身份验证的简介,请参阅 X.509 CA 证书身份验证的优点。
若要为下游设备设置 X.509 CA 签名的身份验证,请执行以下步骤:
获取可用于为下游设备签名证书的 X.509 CA 证书。 有关如何设置 X.509 CA 签名身份验证的示例,请参阅 以下示例方案。
创建下游设备的证书链。 若要了解详细信息,请按照 创建从属 CA 中的步骤作。
在 IoT 中心注册 X.509 CA 证书。 若要了解详细信息,请按照将从属 CA 证书注册到 IoT 中心的步骤进行操作。
将设备证书和密钥复制到下游设备。 有关详细信息,请参阅 管理 IoT Edge 证书。
将设备注册到 IoT 中心以使用 X.509 CA 签名的身份验证。 有关详细信息,请参阅 创建和管理设备标识。
根据首选语言,查看在 IoT 应用程序中引用 X.509 证书的示例:
- C#: 带链示例的 x509 设备证书
- C:iotedge_downstream_device_sample.c
- Node.js:simple_sample_device_x509.js
- Java:SendEventX509.java
- Python:send_message_x509.py
检索并修改连接字符串
在门户中创建 IoT 设备标识后,获取其主密钥或辅助密钥。 将其中一个密钥添加到应用程序用来与 IoT 中心通信的连接字符串。 对于对称密钥身份验证,IoT 中心在设备详细信息中显示完整的连接字符串。 将网关设备信息添加到连接字符串。
下游设备的连接字符串需要以下部分:
- 设备连接到的 IoT 中心:
Hostname=<Iot-Hub-Name>.azure-devices.cn - 已注册到中心的设备 ID:
DeviceID=<Device-ID> - 身份验证方法(对称密钥或 X.509 证书)。
- 对于对称密钥身份验证,请输入主密钥或辅助密钥:
SharedAccessKey=<Key> - 对于 X.509 证书身份验证,请提供一个标志:
x509=true
- 对于对称密钥身份验证,请输入主密钥或辅助密钥:
- 设备连接的网关设备。 输入 IoT Edge 网关设备的配置文件中的 主机名 值:
GatewayHostName=<Gateway-Hostname>
完整的连接字符串如以下示例所示:
HostName=myiothub.azure-devices.cn;DeviceId=myDownstreamDevice;SharedAccessKey=xxxyyyzzz;GatewayHostName=myGatewayDevice
或,对于 X.509 证书身份验证:
HostName=myiothub.azure-devices.cn;DeviceId=myDownstreamDevice;x509=true;GatewayHostName=myGatewayDevice
由于父子关系的存在,可以直接使用网关作为连接主机来简化连接字符串。 例如:
HostName=myGatewayDevice;DeviceId=myDownstreamDevice;SharedAccessKey=xxxyyyzzz
在透明网关系列的下一篇文章中使用此修改后的连接字符串。
后续步骤
此时,已将 IoT Edge 设备注册到 IoT 中心,并将其设置为透明网关。 还有注册了 IoT 中心的下游设备,并将其指向其网关设备。
接下来,设置下游设备,以信任网关设备并安全地连接到它。 继续阅读透明网关系列中的下一篇文章: 将下游设备连接到 Azure IoT Edge 网关。