本指南可帮助你开始在 Key Vault 中管理证书。
此处介绍的方案列表:
- 创建第一个 Key Vault 证书
- 使用与 Key Vault 合作的证书颁发机构创建证书
- 使用未与 Key Vault 合作的证书颁发机构创建证书
- 导入证书
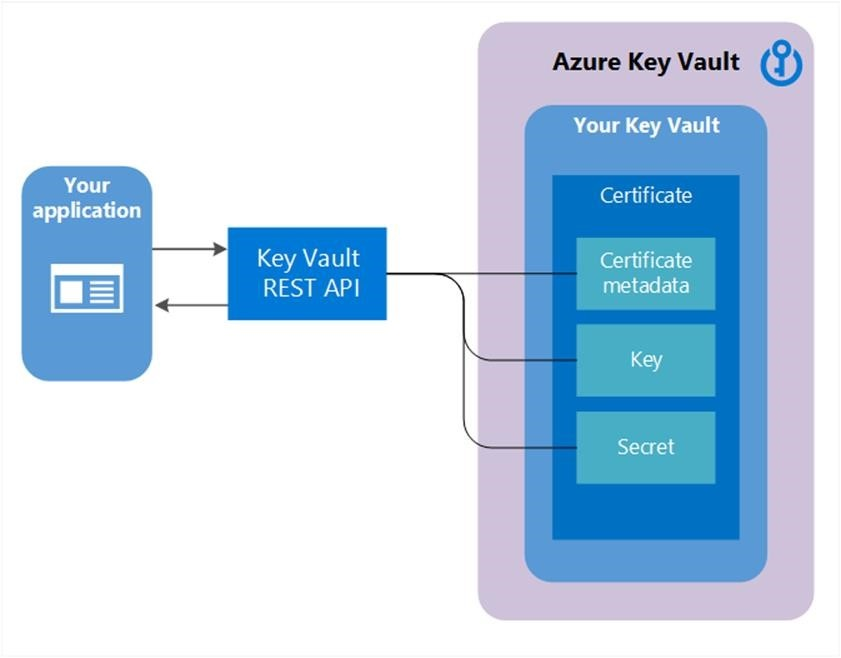
证书是复杂的对象
证书由三个关联资源组成,这些资源作为 Key Vault 证书链接在一起;证书元数据、密钥和机密。
创建第一个 Key Vault 证书
在 Key Vault(KV)中创建证书之前,必须成功完成先决条件步骤 1 和 2,并且此用户/组织必须存在密钥保管库。
步骤 1: 证书颁发机构 (CA) 提供商
- 对于给定公司(例如 Contoso),作为 IT 管理员、PKI 管理员或负责管理与 CA 相关账户的任何人,进行入职培训是使用 Key Vault 证书的先决条件。
以下 CA 是 Key Vault 的当前合作伙伴提供商。 有关详细信息,请参阅 合作 CA 供应商。- DigiCert - Key Vault 通过 DigiCert 提供 OV TLS/SSL 证书。
- GlobalSign - Key Vault 提供具有 GlobalSign 的 OV TLS/SSL 证书。
步骤 2: CA 提供程序的帐户管理员为密钥保管库创建凭据,用于通过 Key Vault 注册、续订和使用 TLS/SSL 证书。
步骤 3a: Contoso 管理员以及拥有证书的 Contoso 员工(Key Vault 用户)可以从管理员处获取证书,也可以直接从具有 CA 的帐户获取证书。
- 通过设置证书颁发者资源,开始在密钥保管库中添加凭据操作。 证书颁发者是一个在 Azure Key Vault (KV) 中表示为 CertificateIssuer 资源的实体。 它用于提供有关 KV 证书源的信息;颁发者名称、提供程序、凭据和其他管理详细信息。
例如,MyDigiCertIssuer
- Provider
- 凭据 - CA 帐户凭据。 每个 CA 都有自己的特定数据。
有关使用 CA 提供程序创建帐户的详细信息,请参阅 Key Vault 博客上的相关文章。
步骤 3b: 为通知设置 证书联系人。 这是 Key Vault 用户的联系人。 Key Vault 不强制执行此步骤。
注意 - 此过程(通过 步骤 3b)是一次性操作。
使用与 Key Vault 合作的 CA 创建证书
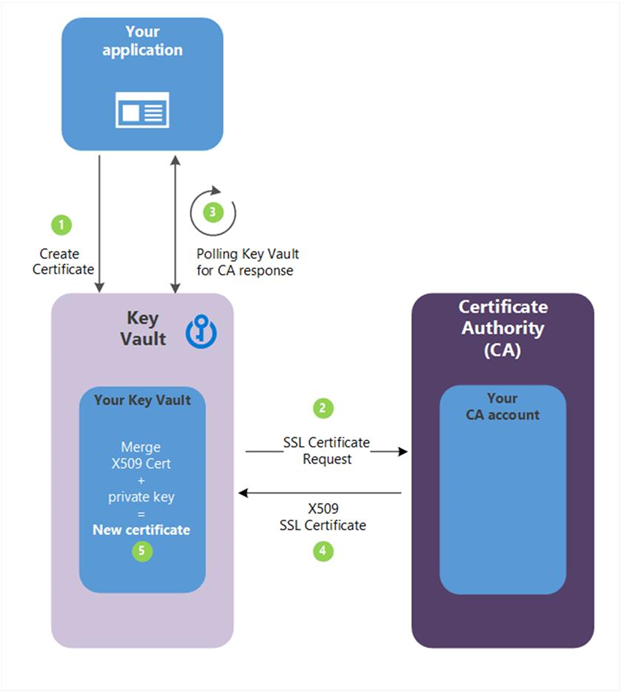
步骤 4: 以下说明对应于上图中的绿色编号步骤。
(1) - 在上图中,您的应用程序正在创建一个证书,首先会在密钥保管库中创建一个密钥。
(2) - Key Vault 向 CA 发送 TLS/SSL 证书请求。
(3)- 应用程序在“循环等待”过程中不断地轮询 Key Vault,以确认证书是否已经完成。 当 Key Vault 收到具有 x509 证书的 CA 响应时,证书创建已完成。
(4) - CA 使用 X509 TLS/SSL 证书响应 Key Vault 的 TLS/SSL 证书请求。
(5)- 通过合并 CA 的 X509 证书,新的证书创建已完成。
Key Vault 用户 - 通过指定策略创建证书
根据需要重复
策略约束
- X509 属性
- 键属性
- 提供者引用 -> 例如 MyDigiCertIssuer
- 续订信息 -> 例如,到期前 90 天
证书创建过程通常是一个异步过程,涉及轮询密钥保管库,了解创建证书作的状态。
获取证书操作- 状态:已完成、失败并显示错误信息或已取消
- 由于创建的延迟,可以启动取消操作。 取消可能有效或可能无效。
与集成 CA 关联的网络安全和访问策略
Key Vault 服务将请求发送到 CA(出站流量)。 因此,它与已启用防火墙的密钥保管库完全兼容。 Key Vault 不会与 CA 共享访问策略。 CA 必须配置为独立接受签名请求。 集成可信证书颁发机构的指南
导入证书
或者 , 证书可以导入 Key Vault - PFX 或 PEM。
导入证书 - 要求 PEM 或 PFX 位于磁盘上并具有私钥。
必须指定:保管库名称和证书名称(策略是可选的)
PEM/PFX 文件包含 KV 可以分析和用于填充证书策略的属性。 如果已指定证书策略,KV 将尝试匹配 PFX/PEM 文件中的数据。
导入完成后,后续作将使用新策略(新版本)。
如果没有进一步的操作,Key Vault 首先做的事情就是发送过期通知。
此外,用户可以编辑策略,该策略在导入时正常运行,但包含未在导入时指定任何信息的默认值。 例如,没有颁发者信息
我们支持的导入格式
Azure Key Vault 支持 .pem 和 .pfx 证书文件,用于将证书导入 Key Vault。 我们支持以下 PEM 文件格式的导入类型。 单个 PEM 编码证书以及 PKCS#8 编码的未加密密钥,其格式如下:
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-----BEGIN 私钥-----
-----END PRIVATE KEY-----
导入证书时,需要确保密钥包含在文件本身中。 如果私钥以不同的格式单独使用,则需要将密钥与证书组合在一起。 某些证书颁发机构提供不同格式的证书,因此在导入证书之前,请确保它们采用 .pem 或 .pfx 格式。
注释
确保证书文件中没有其他元数据,并且私钥未显示为加密。
我们支持的合并 CSR 的格式
Azure Key Vault 支持具有以下标头的 PKCS#8 编码证书:
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
注释
支持由证书颁发机构(CA)常用的 P7B(PKCS#7)签名的证书链,只要是 base64 编码。 可以使用 certutil -encode 转换为受支持的格式。
创建具有未与 Key Vault 合作的 CA 的证书
此方法允许使用 Key Vault 的合作伙伴提供商以外的其他 CA,这意味着组织可以使用所选 CA。
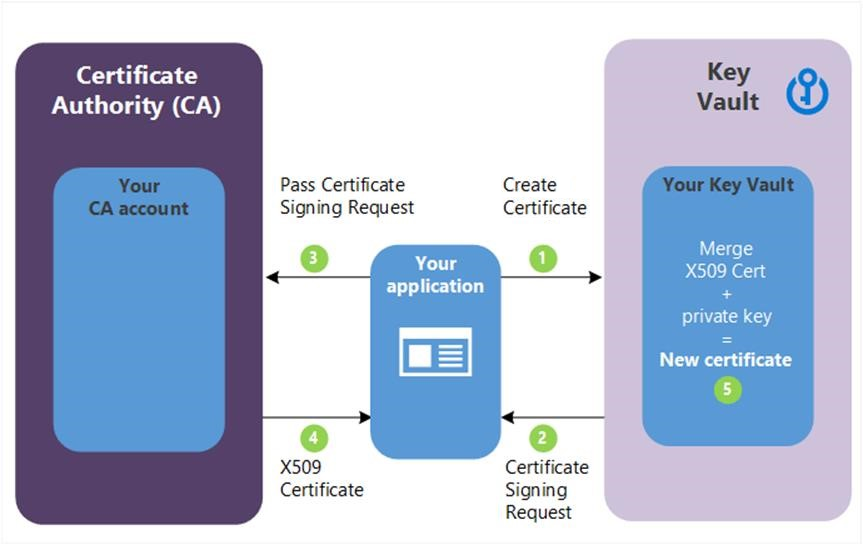
以下步骤说明对应于上图中的绿色字母步骤。
(1)- 在上图中,您的应用程序正在创建证书,这包括首先在您的密钥保管库中创建一个密钥。
(2) - Key Vault 向应用程序返回证书签名请求(CSR)。
(3) - 应用程序将 CSR 传递给所选 CA。
(4) - 所选的 CA 使用 X509 证书进行响应。
(5) - 您的应用程序通过合并来自 CA 的 X509 证书来完成新证书的创建。