警告
为了提高安全性,请使用 Role-Based 访问控制(RBAC)权限模型, 而不是管理 Azure Key Vault 时的访问策略。 RBAC 仅将权限管理限制为“所有者”和“用户访问管理员”角色,确保安全与管理任务之间明确分离。 有关详细信息,请参阅 什么是 Azure RBAC? 和 Key Vault RBAC 指南。
使用访问策略权限模型、具有ContributorKey Vault Contributor权限或包含Microsoft.KeyVault/vaults/write权限的任何角色的用户可以通过配置 Key Vault 访问策略来授予自己数据平面访问权限。 这可能会导致对密钥保管库、密钥、机密和证书进行未经授权的访问和管理。 若要降低此风险,请使用访问策略模型时限制对密钥保管库的参与者角色访问权限。
Key Vault 访问策略确定给定的安全主体(即用户、应用程序或用户组)是否可对 Key Vault 机密、密钥和证书执行不同的操作。 你可以使用 Azure 门户 分配访问策略。
Key Vault 最多支持 1024 个访问策略条目,每个条目可向特定安全主体授予一组不同的权限。 由于此限制,建议你尽可能将访问策略分配给用户组,而不是单个用户。 使用组来管理组织中多个人员的权限要轻松得多。 有关详细信息,请参阅使用 Microsoft Entra 组管理应用和资源访问。
分配访问策略
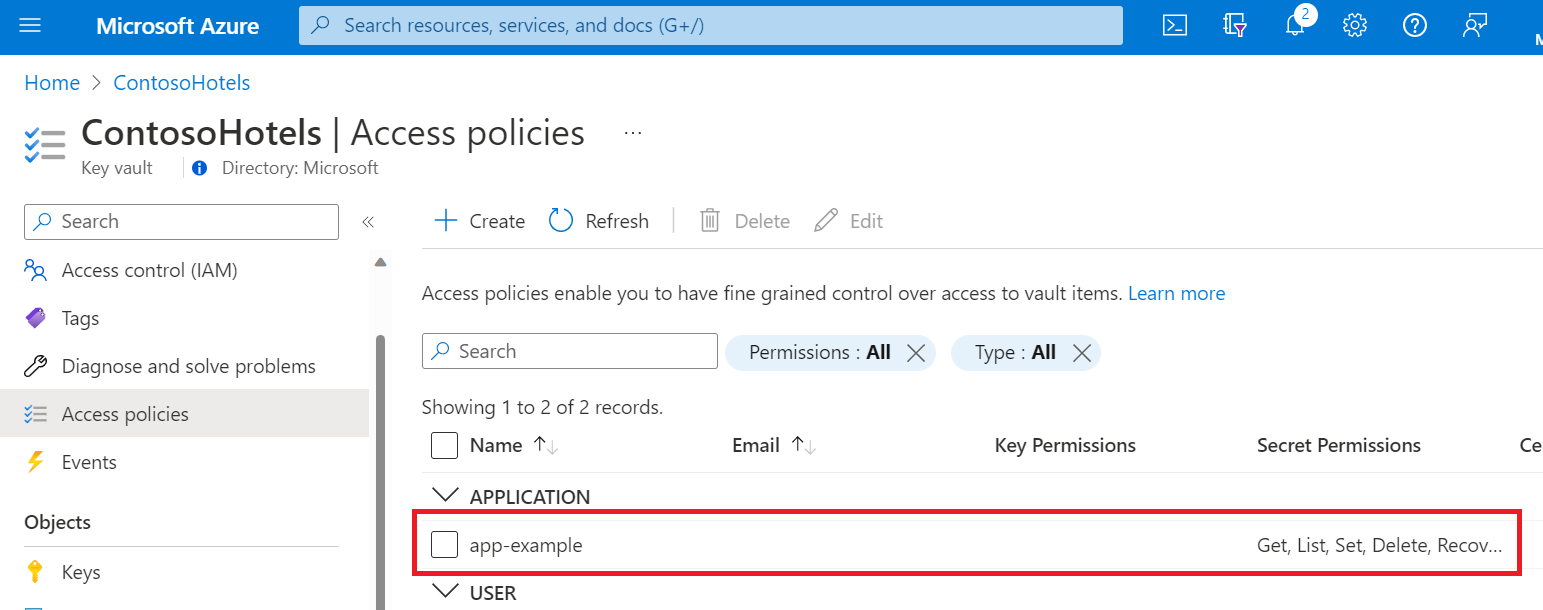
在 Azure 门户中,导航到 Key Vault 资源。
选择“访问策略”,然后选择“创建”:
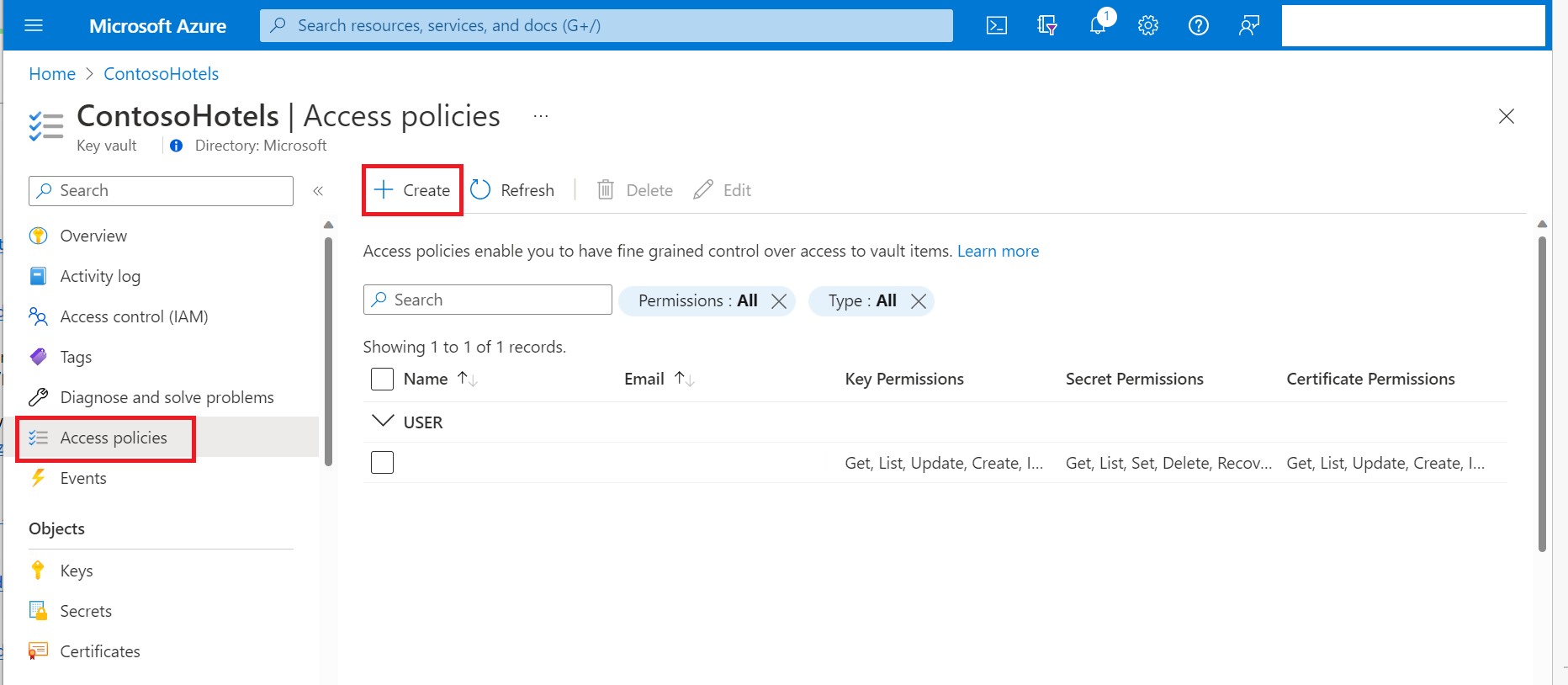
在“密钥权限”、“机密权限”和“证书权限”下选择所需要的权限。
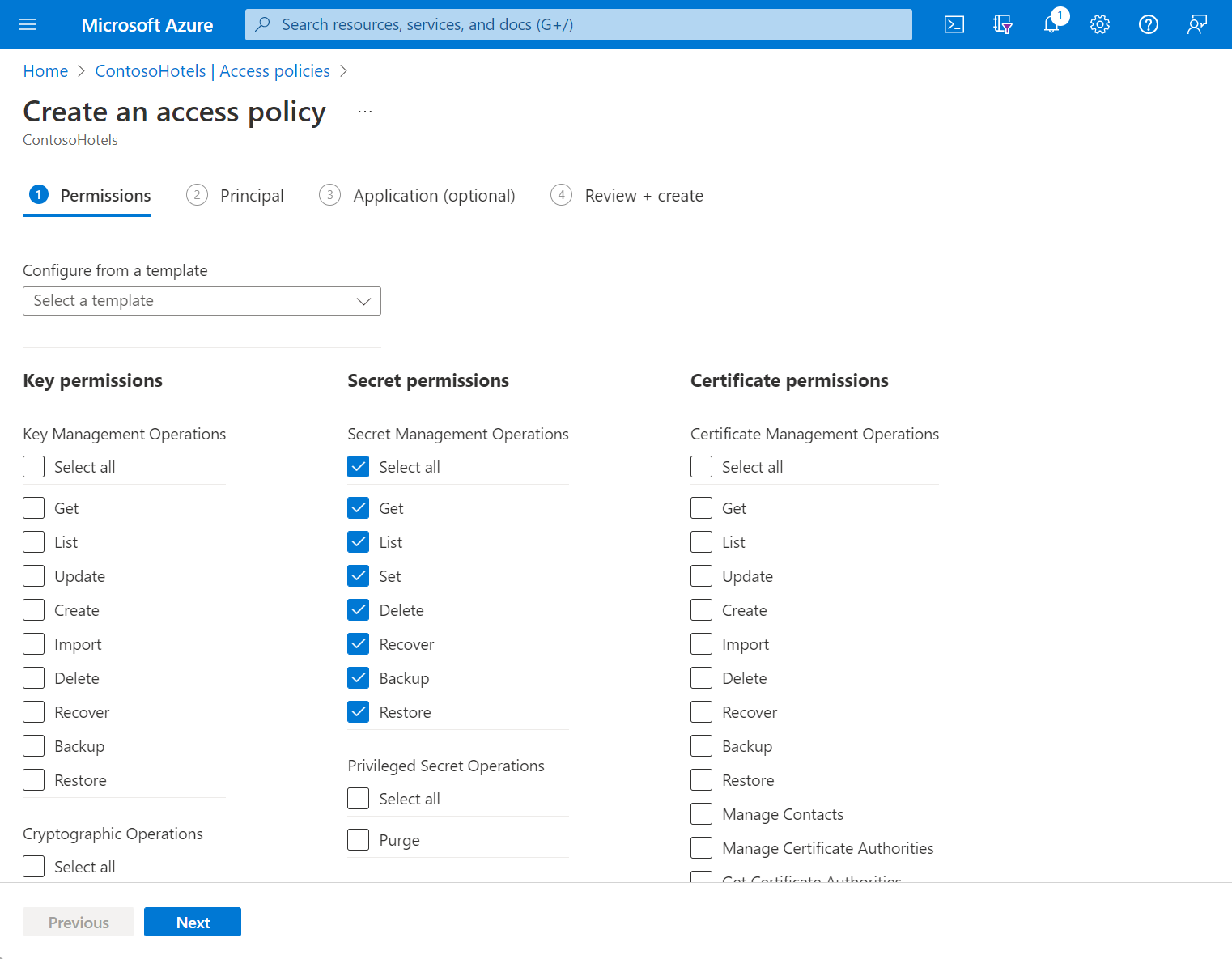
在“主体”选择窗格下,在搜索字段中输入用户、应用或服务主体的名称,然后选择相应的结果。
如果使用的是应用的托管标识,请搜索并选择该应用本身的名称。 有关安全主体的详细信息,请参阅 Key Vault 身份验证。
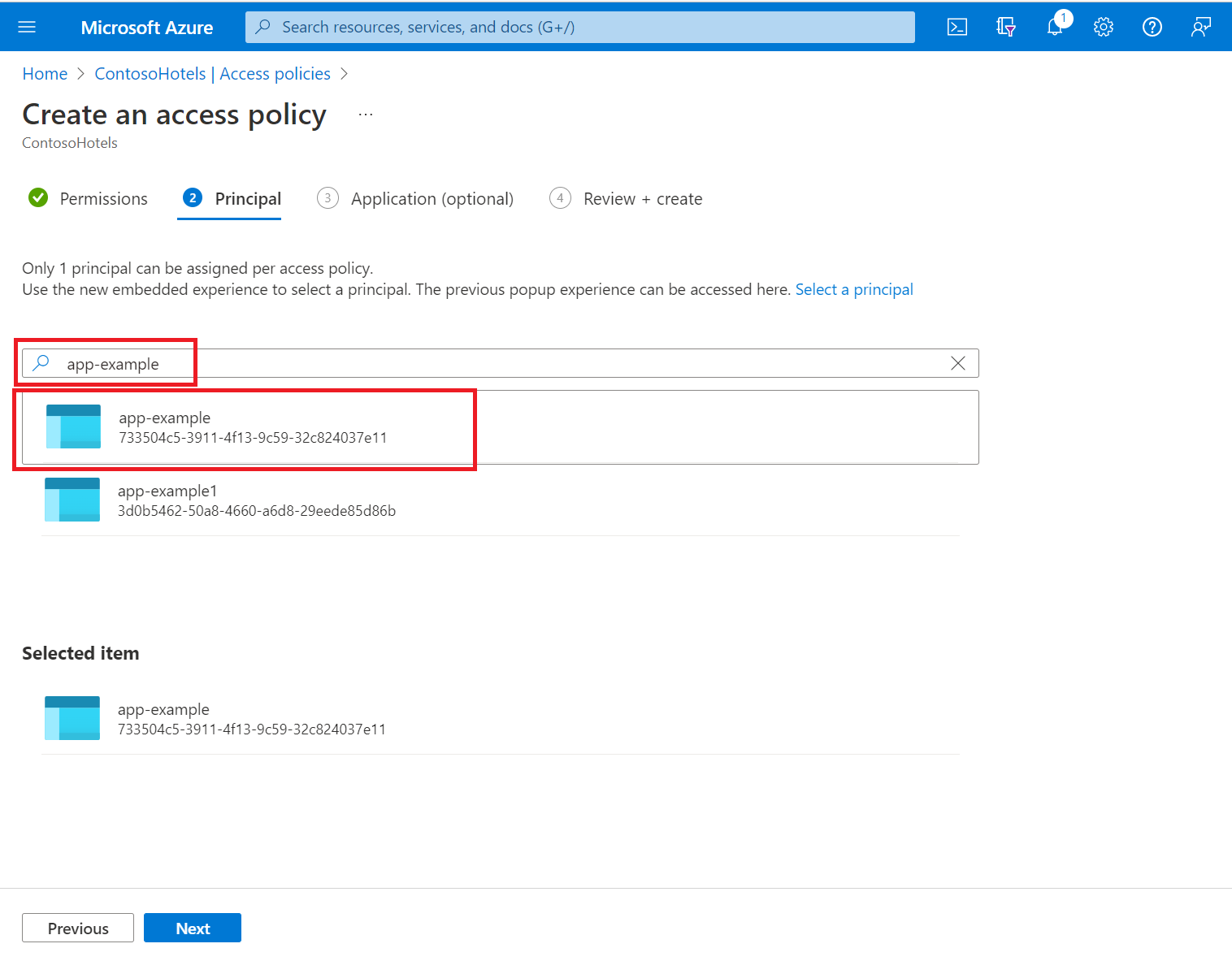
查看访问策略更改,然后选择“创建”以保存访问策略。
返回“访问策略”页,验证是否已列出你的访问策略。
若要详细了解如何使用 Azure CLI 在 Microsoft Entra ID 中创建组,请参阅 az ad group create 和 az ad group member add。
若要在本地运行 Azure CLI 命令,请安装 Azure CLI。
仅限本地 CLI:使用 az login 登录到 Azure:
az cloud set -n AzureChinaCloud
az login
# az cloud set -n AzureCloud //means return to Public Azure.
az login 命令会打开浏览器窗口来收集凭据(如果需要)。
获取对象 ID
确定要为其分配访问策略的应用程序、组或用户的对象 ID:
应用程序和其他服务主体:请使用 az ad sp list 命令来检索服务主体。 请检查命令的输出,以确定要为其分配访问策略的安全主体的对象 ID。
az ad sp list --show-mine
组:请使用 az ad group list 命令,并通过 --display-name 参数筛选结果:
az ad group list --display-name <search-string>
用户:请使用 az ad user show 命令,并在 --id 参数中传递用户的电子邮件地址:
az ad user show --id <email-address-of-user>
分配访问策略
使用 az keyvault set-policy 命令来分配所需的权限:
az keyvault set-policy --name myKeyVault --object-id <object-id> --secret-permissions <secret-permissions> --key-permissions <key-permissions> --certificate-permissions <certificate-permissions>
将 <object-id> 替换为安全主体的对象 ID。
为这些特定类型分配权限时,只需包括 --secret-permissions、--key-permissions 和 --certificate-permissions。
<secret-permissions> 文档中提供了 <key-permissions>、<certificate-permissions> 和 的允许值。
若要详细了解如何使用 Azure PowerShell 在 Microsoft Entra ID 中创建组,请参阅 New-AzADGroup 和 Add-AzADGroupMember。
若要在本地运行命令,请安装 Azure PowerShell(如果尚未这样做)。
仅限本地 PowerShell:
安装 Microsoft Entra ID PowerShell 模块。
登录 Azure:
Connect-AzAccount -Environment AzureChinaCloud
获取对象 ID
确定要为其分配访问策略的应用程序、组或用户的对象 ID:
应用程序和其他服务主体:使用带有 参数的 -SearchString cmdlet 根据所需服务主体的名称筛选结果:
Get-AzADServicePrincipal -SearchString <search-string>
组:使用带有 参数的 -SearchString cmdlet 根据所需组的名称筛选结果:
Get-AzADGroup -SearchString <search-string>
在输出中,对象 ID 将作为 Id 列出。
用户:使用 Get-AzADUser cmdlet,将用户的电子邮件地址传递给 -UserPrincipalName 参数。
Get-AzAdUser -UserPrincipalName <email-address-of-user>
在输出中,对象 ID 将作为 Id 列出。
分配访问策略
使用 Set-AzKeyVaultAccessPolicy cmdlet 分配访问策略:
Set-AzKeyVaultAccessPolicy -VaultName <key-vault-name> -ObjectId <Id> -PermissionsToSecrets <secrets-permissions> -PermissionsToKeys <keys-permissions> -PermissionsToCertificates <certificate-permissions
为这些特定类型分配权限时,只需包括 -PermissionsToSecrets、-PermissionsToKeys 和 -PermissionsToCertificates。
<secret-permissions>、<key-permissions> 和 <certificate-permissions> 的允许值在 Set-AzKeyVaultAccessPolicy - 参数文档中提供。
后续步骤




