使用 Azure 门户分配 Key Vault 访问策略
Key Vault 访问策略确定给定的安全主体(即用户、应用程序或用户组)是否可以对 Key Vault 机密、密钥和证书执行不同的操作。 可以使用 Azure 门户(本文)、Azure CLI 或 Azure PowerShell 来分配访问策略。
Key Vault 最多支持 1024 个访问策略条目,每个条目可向特定安全主体授予一组不同的权限。 由于此限制,建议你尽可能将访问策略分配给用户组,而不是单个用户。 使用组来管理组织中多个人员的权限要轻松得多。 有关详细信息,请参阅使用 Azure Active Directory 组管理应用和资源访问
有关 Key Vault 访问控制的完整详细信息,请参阅 Azure Key Vault 安全性功能:标识和访问管理。
若要详细了解如何通过 Azure 门户在 Microsoft Entra ID 中创建组,请参阅创建基本组并添加成员
分配访问策略
在 Azure 门户中,导航到 Key Vault 资源。
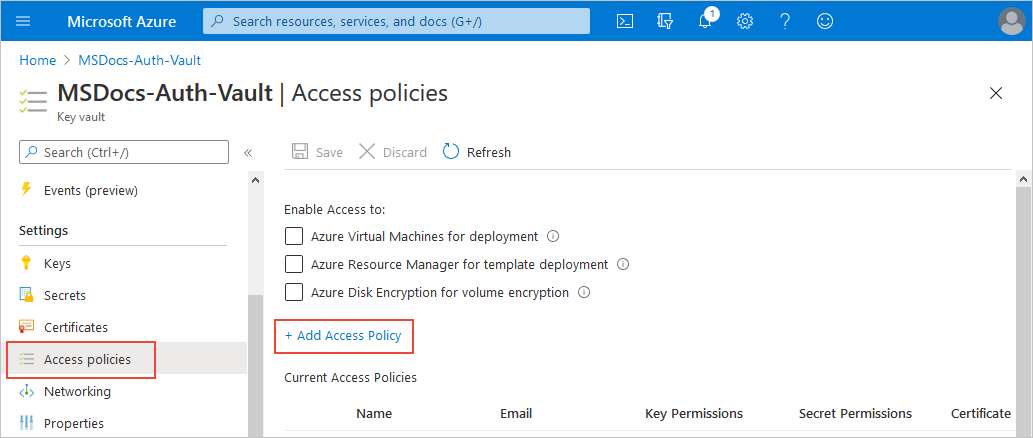
在“设置”下,选择“访问策略”,然后选择“添加访问策略” :
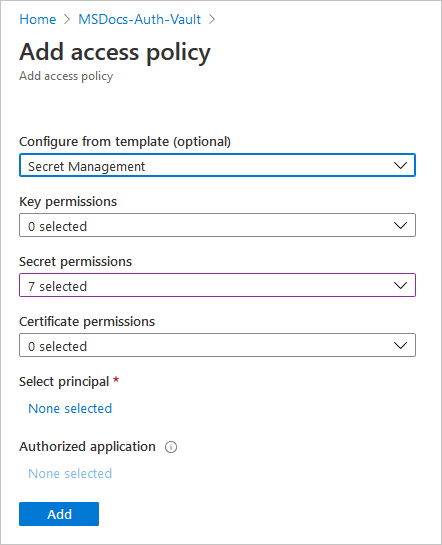
在“证书权限”、“密钥权限”和“机密权限”下选择所需要的权限 。 也可以选择包含常见权限组合的模板:
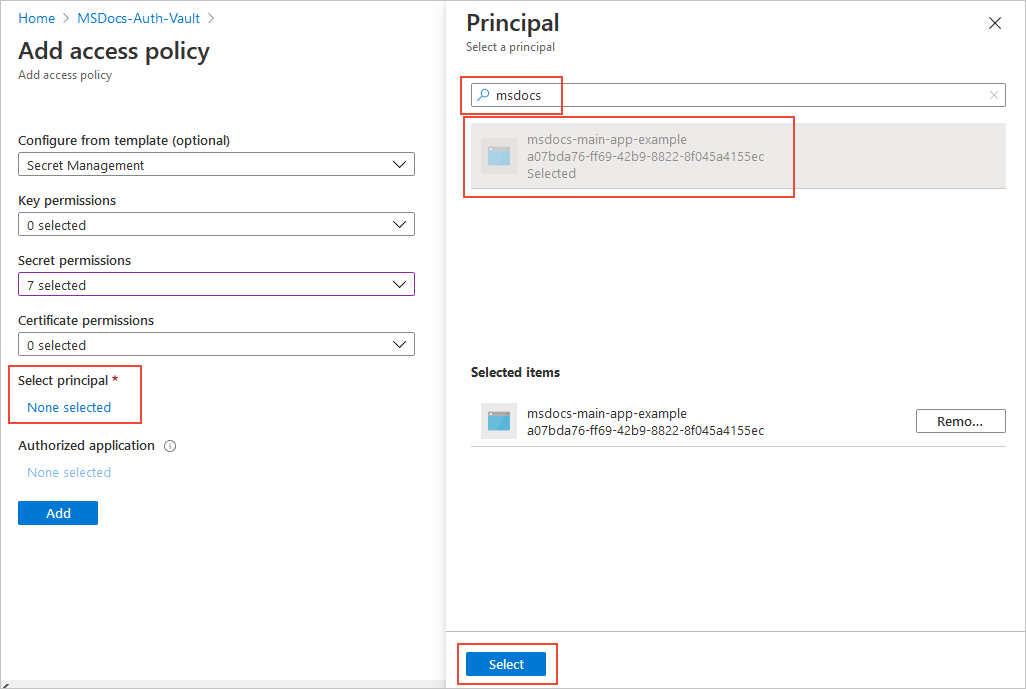
在“选择主体”下,选择“未选择任何项”链接,以打开“主体”选择窗格 。 在搜索字段中输入用户、应用或服务主体的名称,选择相应的结果,然后选择“选择”。
如果使用的是应用的托管标识,请搜索并选择该应用本身的名称。 有关安全主体的详细信息,请参阅 Key Vault 身份验证。
返回“添加访问策略”窗格,选择“添加”以保存该访问策略 。
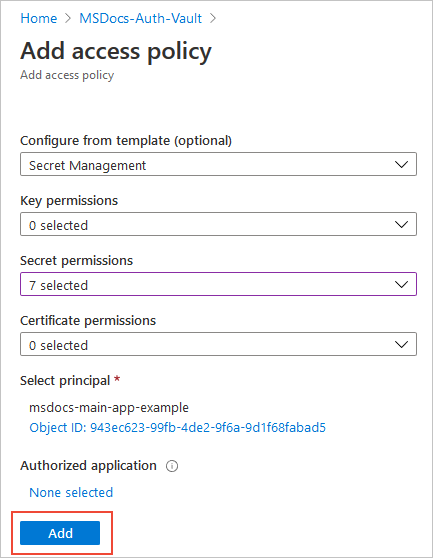
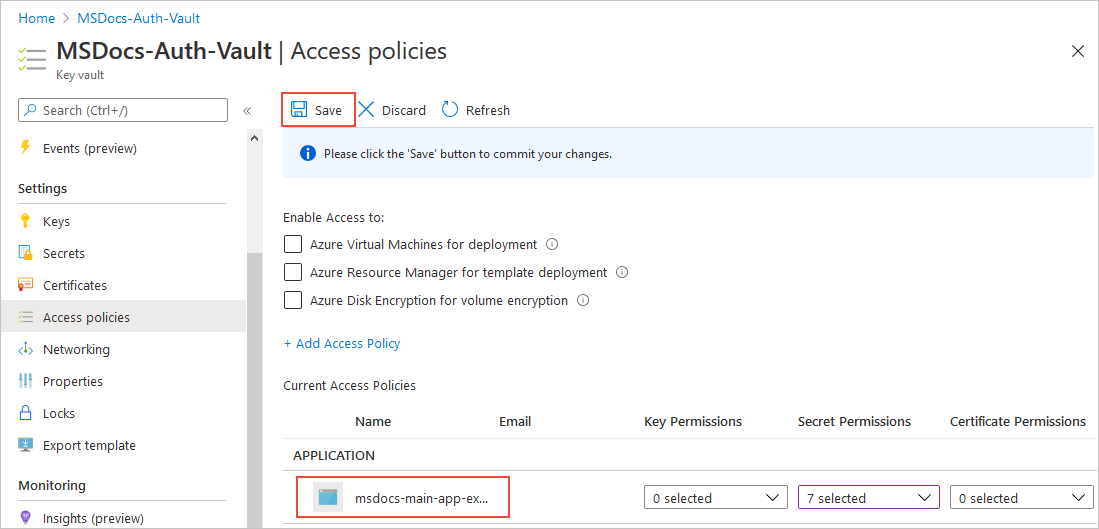
返回“访问策略”页,验证“当前访问策略”下是否已列出你的访问策略,然后选择“保存” 。 访问策略在保存之后才会应用。