注意
密钥保管库资源提供程序支持两种资源类型:保管库和托管 HSM。 本文中所述的访问控制仅适用于保管库。 若要详细了解托管 HSM 的访问控制,请参阅托管 HSM 访问控制。
Azure 基于角色的访问控制 (Azure RBAC) 是在 Azure 资源管理器基础上构建的授权系统,针对 Azure 资源提供集中访问权限管理。
Azure RBAC 允许用户管理密钥、机密和证书权限,并提供一个位置来管理所有密钥保管库的所有权限。
借助 Azure RBAC 模型,用户可以在不同的范围级别上设置权限:管理组、订阅、资源组或单个资源。 通过适用于密钥保管库的 Azure RBAC,用户还可以对各个密钥、机密和证书拥有单独的权限。
有关详细信息,请参阅 Azure 基于角色的访问控制 (Azure RBAC)。
Key Vault 访问模型概述
通过两个接口控制对密钥保管库的访问: 控制平面 和数据 平面。
控制平面是管理 Key Vault 本身的位置。 在此环境中的作业包括创建和删除密钥库、检索密钥库属性以及更新访问策略。
数据平面用于处理密钥保管库中存储的数据。 可以添加、删除和修改密钥、机密和证书。
这两个平面都使用 Microsoft Entra ID 进行身份验证。 对于授权,控制平面使用 Azure 基于角色的访问控制(Azure RBAC),数据平面使用 Key Vault 访问策略(旧版)或 Azure RBAC 用于 Key Vault 数据平面的操作。
若要在任一平面中访问密钥保管库,所有调用方(用户或应用程序)都必须具有适当的身份验证和授权。 身份验证会建立调用方的身份。 授权确定调用方可以执行哪些操作。
应用程序通过终结点访问平面。 两个平面的访问控制系统独立运行。 若要授予应用程序在密钥保管库中使用密钥的权限,可以通过使用 Azure RBAC 或 Key Vault 访问策略授予数据平面访问权限。 若要向用户授予对 Key Vault 属性和标记的读取访问权限,但无权访问数据(密钥、机密或证书),请使用 Azure RBAC 授予控制平面访问权限。
访问平面端点
下表显示了控件和数据平面的终结点。
| 访问平面 | 访问端点 | Operations | 访问控制机制 |
|---|---|---|---|
| 控制面板 |
由世纪互联运营的 Azure: management.chinacloudapi.cn:443 |
创建、读取、更新和删除密钥保管库 设置 Key Vault 访问策略 设置 Key Vault 标签 |
Azure RBAC |
| 数据平面 |
由世纪互联运营的 Azure: <vault-name.vault.azure.cn:443> |
密钥:加密、解密、封装密钥、解封密钥、签名、验证、获取、列出、创建、更新、导入、删除、恢复、备份、还原、清除、轮换、获取轮换策略、设置轮换策略、释放 证书:managecontacts、getissuers、listissuers、setissuers、deleteissuers、manageissuers、get、list、create、import、update、delete、recover、backup、restore、purge 机密:获取、列出、设置、删除、恢复、备份、还原、清除 |
Key Vault 访问策略(旧版)或 Azure RBAC |
管理对 Key Vault 的管理访问权限
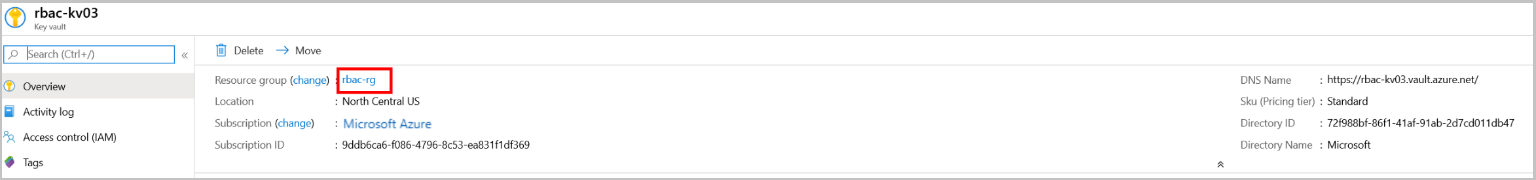
在资源组中创建密钥保管库时,可以使用 Microsoft Entra ID 管理访问权限。 授予用户或组管理资源组中的密钥保管库的能力。 可以通过分配相应的 Azure 角色,在特定的范围级别授予访问权限。 若要授予对用户管理密钥保管库的访问权限,请将预定义 Key Vault Contributor 的角色分配给特定范围内的用户。 可以将以下范围级别分配给 Azure 角色:
- 订阅:在订阅级别分配的 Azure 角色适用于该订阅中的所有资源组和资源。
- 资源组:在资源组级别分配的 Azure 角色适用于该资源组中的所有资源。
- 特定资源:为特定资源分配的 Azure 角色适用于该资源。 在这种情况下,资源是特定的密钥保管库。
有多个预定义角色。 如果预定义角色不符合你的需求,则可以定义自己的角色。 有关详细信息,请参阅 Azure RBAC:内置角色。
重要
如果用户有权 Contributor 访问 Key Vault 控制平面,则用户可以通过设置 Key Vault 访问策略授予自己对数据平面的访问权限。 应严格控制谁可以访问您密钥保管库的Contributor角色。 确保只有经过授权的人员才能访问和管理密钥保管库、密钥、机密和证书。
单个密钥、机密和证书角色分配的最佳做法
我们的建议是,对每个环境(开发环境、预生产环境和生产环境)的每个应用程序使用一个保管库,并在密钥保管库范围内分配角色。
应避免在单个密钥、机密和证书上分配角色。 必须在多个应用程序之间共享单个密钥属于例外情况;例如,一个应用程序需要从另一个应用程序访问数据的情况。
有关 Azure Key Vault 管理指南的详细信息,请参阅:
用于 Key Vault 数据平面操作的 Azure 内置角色
注意
Key Vault Contributor 角色仅适用于控制平面操作,用于管理密钥保管库。 它不允许访问密钥、机密和证书。
| 内置角色 | 说明 | ID |
|---|---|---|
| Key Vault 管理员 | 对密钥保管库以及其中的所有对象(包括证书、密钥和机密)执行所有数据平面操作。 无法管理密钥保管库资源或管理角色分配。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | 00482a5a-887f-4fb3-b363-3b7fe8e74483 |
| Key Vault 读取者 | 读取密钥保管库及其证书、密钥和机密的元数据。 无法读取机密内容或密钥材料等敏感值。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | 21090545-7ca7-4776-b22c-e363652d74d2 |
| 密钥保管库清除操作员 | 允许永久删除软删除的保管库。 | a68e7c17-0ab2-4c09-9a58-125dae29748c |
| Key Vault 证书管理人员 | 对密钥保管库的证书执行任何操作,但管理权限除外。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | a4417e6f-fecd-4de8-b567-7b0420556985 |
| 密钥保管库证书用户 | 读取整个证书内容,包括机密和密钥部分。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | db79e9a7-68ee-4b58-9aeb-b90e7c24fcba |
| Key Vault 加密管理人员 | 对密钥保管库的密钥执行任何操作(管理权限除外)。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | 14b46e9e-c2b7-41b4-b07b-48a6ebf60603 |
| 密钥保管库加密服务加密用户 | 读取密钥的元数据并执行包装/展开操作。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | e147488a-f6f5-4113-8e2d-b22465e65bf6 |
| Key Vault 加密用户 | 使用密钥执行加密操作。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | 12338af0-0e69-4776-bea7-57ae8d297424 |
| 密钥保管库加密服务发布用户 | Azure 机密计算和等效环境的发布密钥。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | |
| Key Vault 机密管理人员 | 对密钥保管库的机密执行任何操作(管理权限除外)。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | b86a8fe4-44ce-4948-aee5-eccb2c155cd7 |
| Key Vault 机密用户 | 读取机密内容,包括带有私钥的证书的机密部分。 仅适用于使用“Azure 基于角色的访问控制”权限模型的密钥保管库。 | 4633458b-17de-408a-b874-0445c86b69e6 |
有关 Azure 内置角色定义的详细信息,请参阅 Azure 内置角色。
管理内置的密钥保管库数据平面角色分配
| 内置角色 | 说明 | ID |
|---|---|---|
| 密钥保管库数据访问管理员 | 通过添加或删除 Key Vault 管理员、Key Vault 证书主管、Key Vault 加密管理人员、Key Vault 加密服务加密用户、Key Vault 加密用户、Key Vault 加密用户、Key Vault 读取者、Key Vault 机密主管或 Key Vault 机密用户角色来管理对 Azure Key Vault 的访问。 包括用于约束角色分配的 ABAC 条件。 | 8b54135c-b56d-4d72-a534-26097cfdc8d8 |
对密钥保管库使用 Azure RBAC 机密、密钥和证书权限
用于密钥保管库的新 Azure RBAC 权限模型提供了保管库访问策略权限模型的替代方案。
先决条件
必须拥有 Azure 订阅。 如果没有 Azure 订阅,可以在开始之前创建一个试用版订阅。
若要管理角色分配,必须具有 Microsoft.Authorization/roleAssignments/write 和 Microsoft.Authorization/roleAssignments/delete 权限,例如 Key Vault 数据访问管理员(具有仅分配/删除特定 Key Vault 角色的受限权限)、用户访问管理员或所有者。
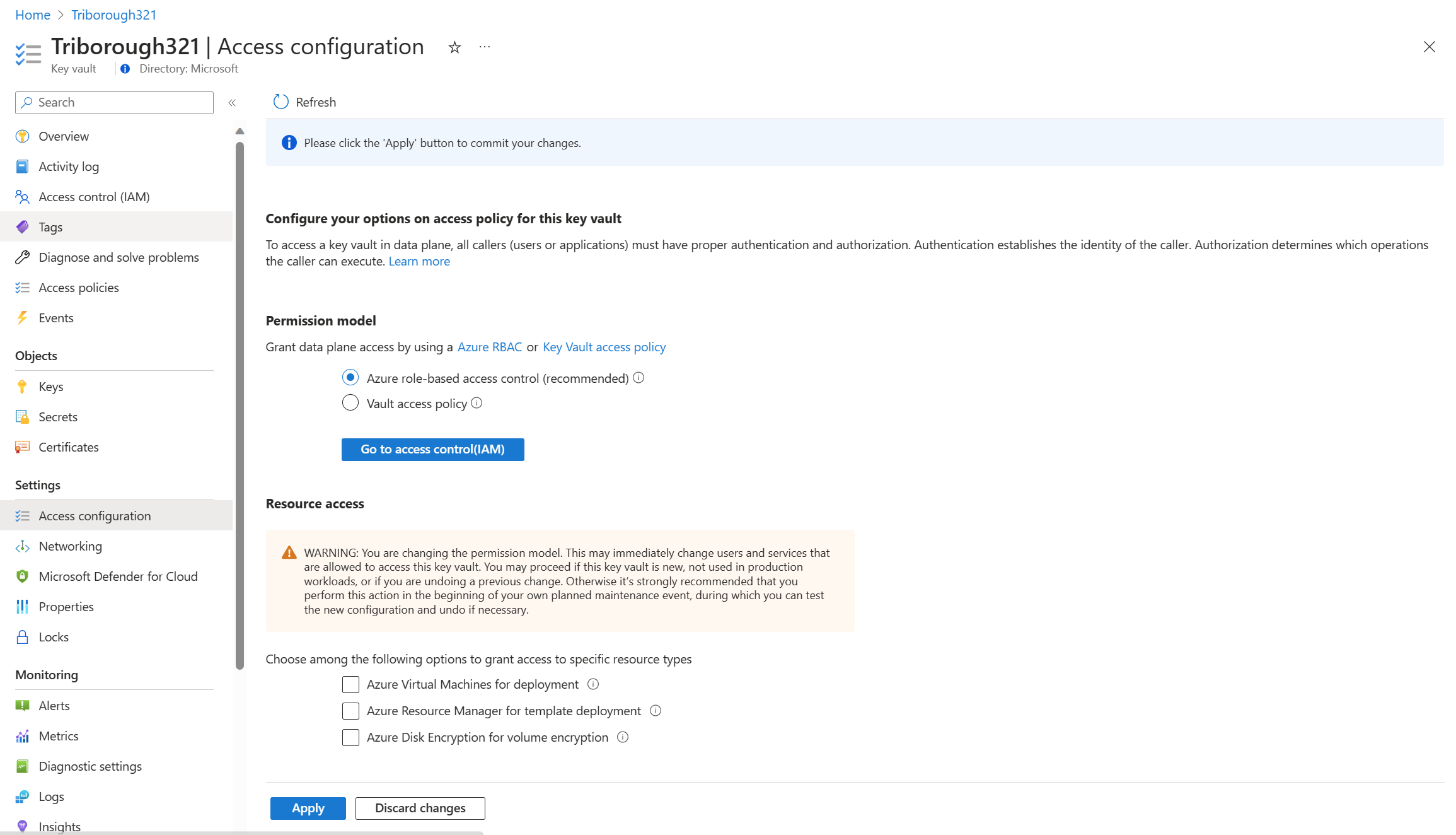
对密钥保管库启用 Azure RBAC 权限
注意
更改权限模型需要不受限制的“Microsoft.Authorization/roleAssignments/write”权限,这是所有者和用户访问管理员角色的一部分。 经典订阅管理员角色(如“服务管理员”和“共同管理员”)或受限的“Key Vault 数据访问管理员”不能用于更改权限模型。
对新密钥保管库启用 Azure RBAC 权限:
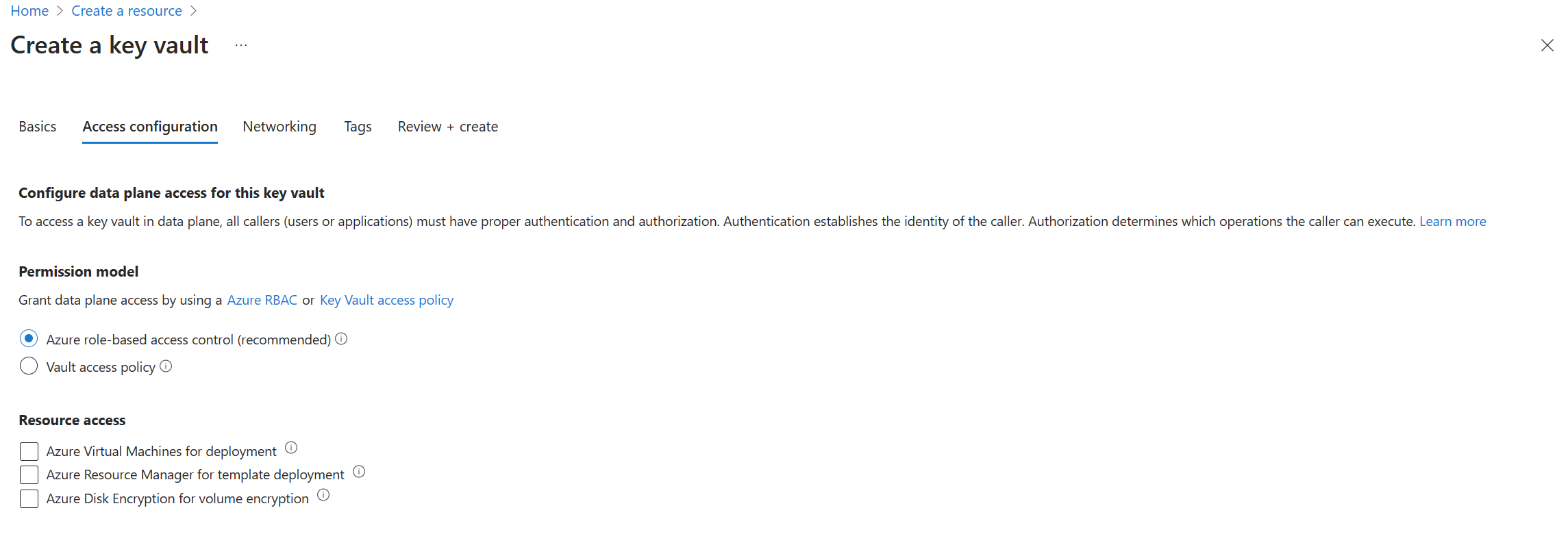
对现有密钥保管库启用 Azure RBAC 权限:
重要
设置 Azure RBAC 权限模型会使所有访问策略权限失效。 若未分配对等的 Azure 角色,它可能会导致故障。
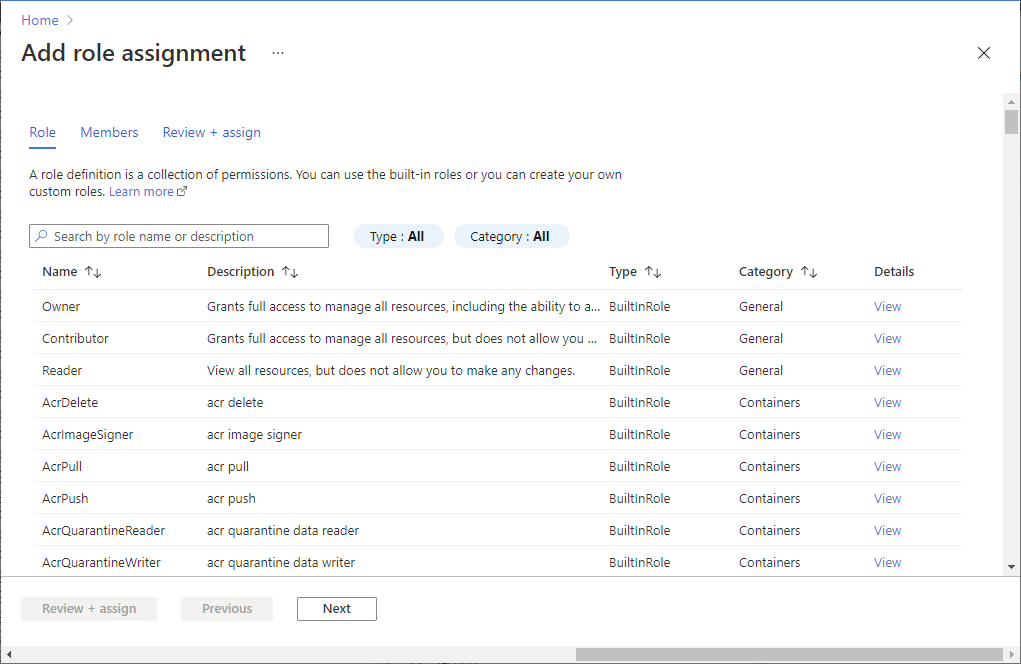
分配角色
注意
建议在脚本中使用唯一的角色 ID,而不是角色名称。 这样一来,即使角色重命名,脚本仍可以继续使用。 在本文档中,角色名称用于提高可读性。
若要使用 Azure CLI 创建角色分配,请使用 az role assignment 命令:
az role assignment create --role {role-name-or-id} --assignee {assignee-upn}> --scope {scope}
有关详细信息,请参阅使用 Azure CLI 分配 Azure 角色。
资源组范围的角色分配
az role assignment create --role "Key Vault Reader" --assignee {i.e user@microsoft.com} --scope /subscriptions/{subscriptionid}/resourcegroups/{resource-group-name}
有关详细信息,请参阅使用 Azure CLI 分配 Azure 角色。
上述角色分配提供了在密钥保管库中列出密钥保管库对象的功能。
Key Vault 范围角色分配
az role assignment create --role "Key Vault Secrets Officer" --assignee {assignee-upn} --scope /subscriptions/{subscriptionid}/resourcegroups/{resource-group-name}/providers/Microsoft.KeyVault/vaults/{key-vault-name}
有关详细信息,请参阅使用 Azure CLI 分配 Azure 角色。
机密范围角色分配
注意
密钥保管库机密、证书、密钥范围角色分配仅适用于此处所述的有限方案,以符合安全最佳做法。
az role assignment create --role "Key Vault Secrets Officer" --assignee {i.e user@microsoft.com} --scope /subscriptions/{subscriptionid}/resourcegroups/{resource-group-name}/providers/Microsoft.KeyVault/vaults/{key-vault-name}/secrets/RBACSecret
有关详细信息,请参阅使用 Azure CLI 分配 Azure 角色。
测试和验证
注意
浏览器使用缓存,删除角色分配后需要刷新页面。 预留几分钟时间供角色分配刷新
验证在密钥库级别上没有“Key Vault 机管理人员”角色的情况下添加新机密。
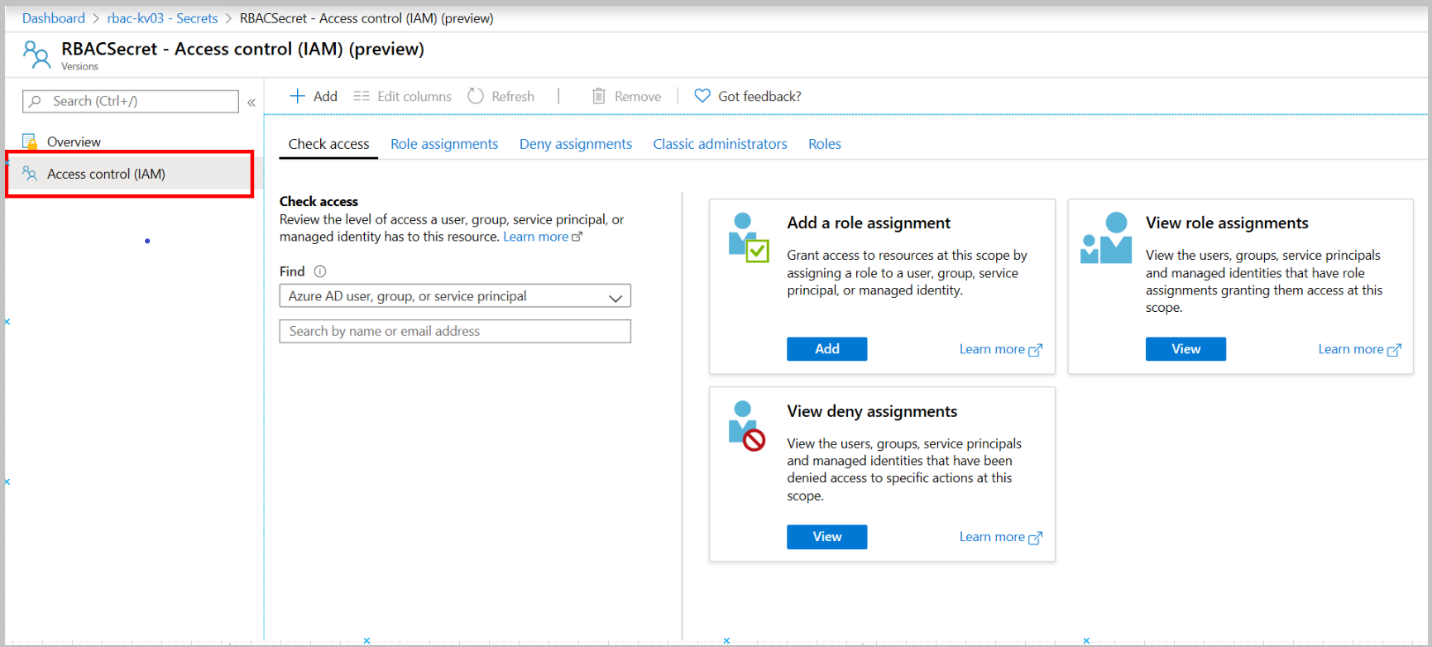
转到密钥保管库“访问控制(IAM)”选项卡,删除此资源的“Key Vault 机密管理人员”角色分配。
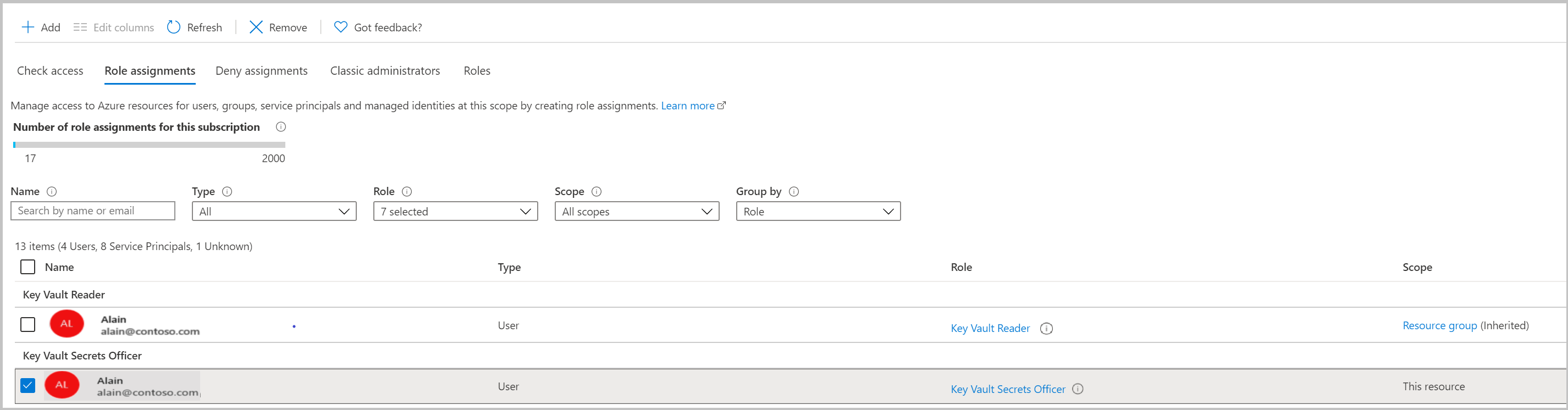
导航到以前创建的机密。 你可以看到所有机密属性。
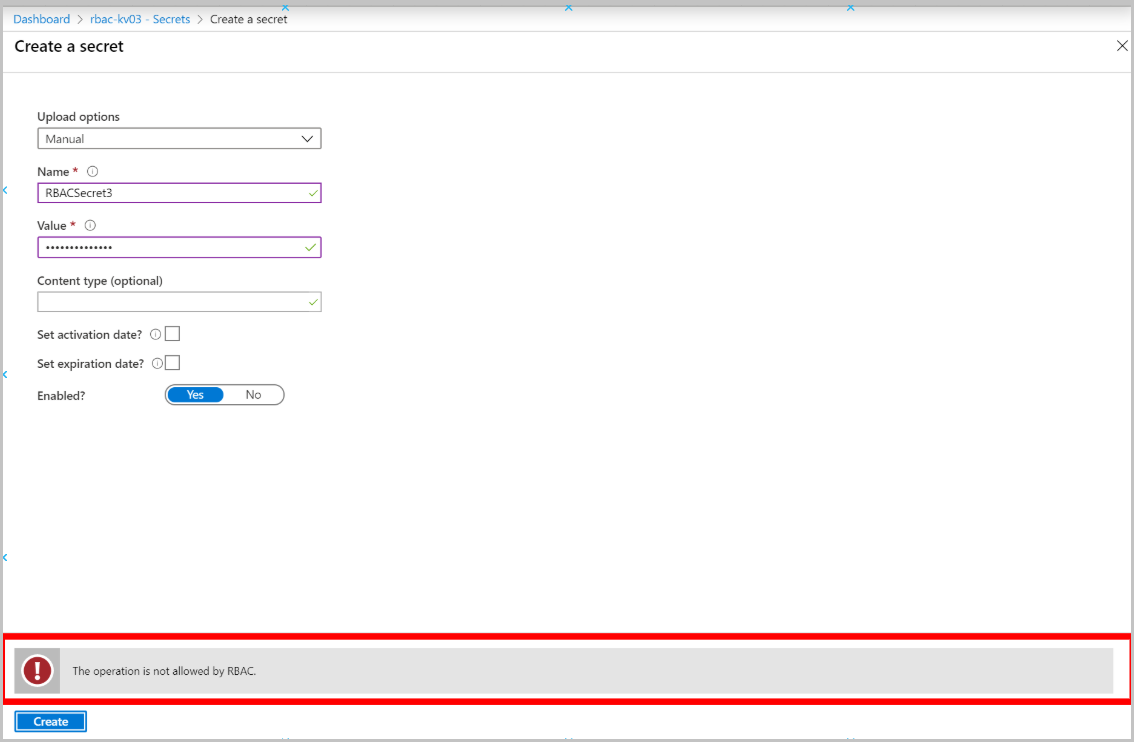
若创建新机密(“机密”>“+ 生成/导入”),应会看到此错误:
验证在机密级别上没有“Key Vault 机密管理人员”角色的情况下编辑机密。
转到先前创建的机密“访问控制(IAM)”选项卡,删除此资源的“Key Vault 机密管理人员”角色分配。
导航到以前创建的机密。 你可以看到机密属性。
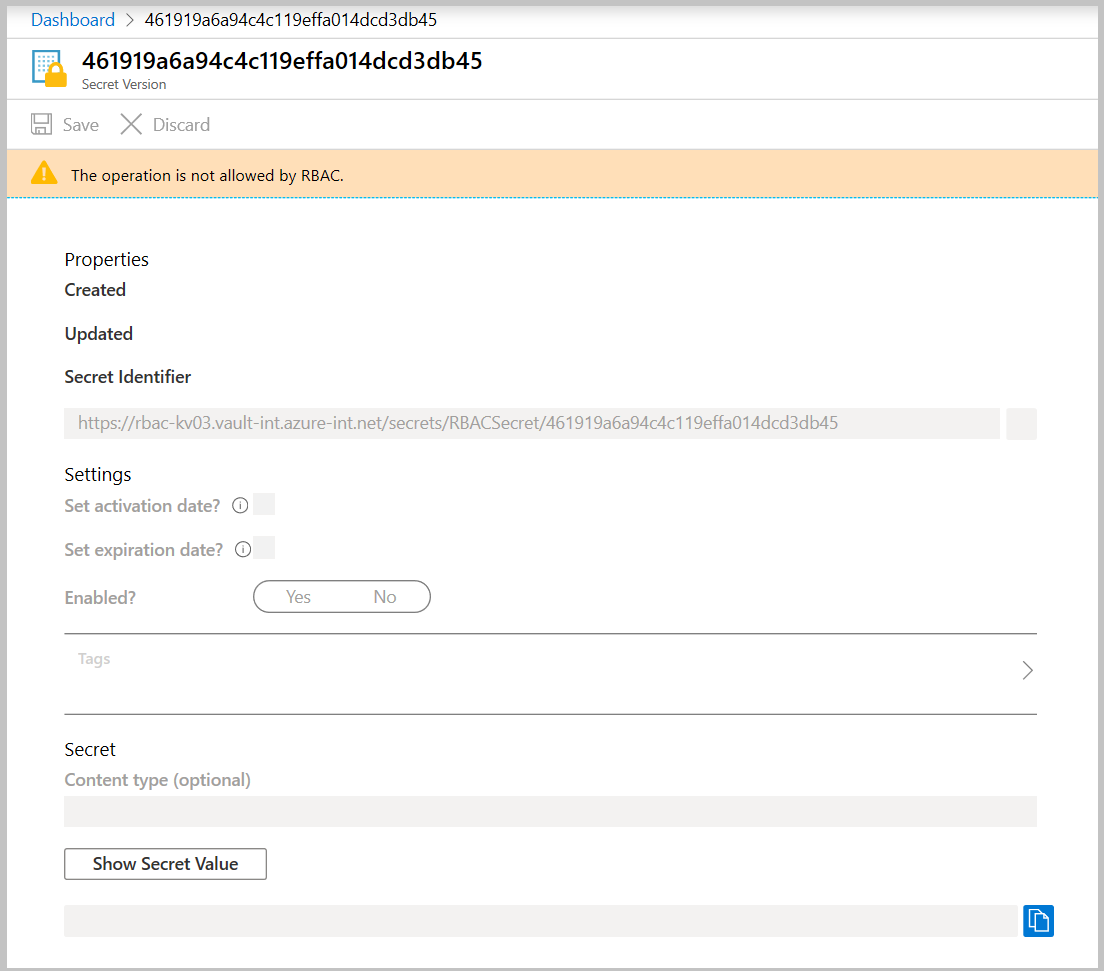
验证在密钥库级别没有读取者角色的情况下读取机密。
转到密钥保管库资源组“访问控制(IAM)”选项卡,删除“Key Vault 读取者”角色分配。
若导航到密钥保管库的“机密”选项卡,应会看到此错误:
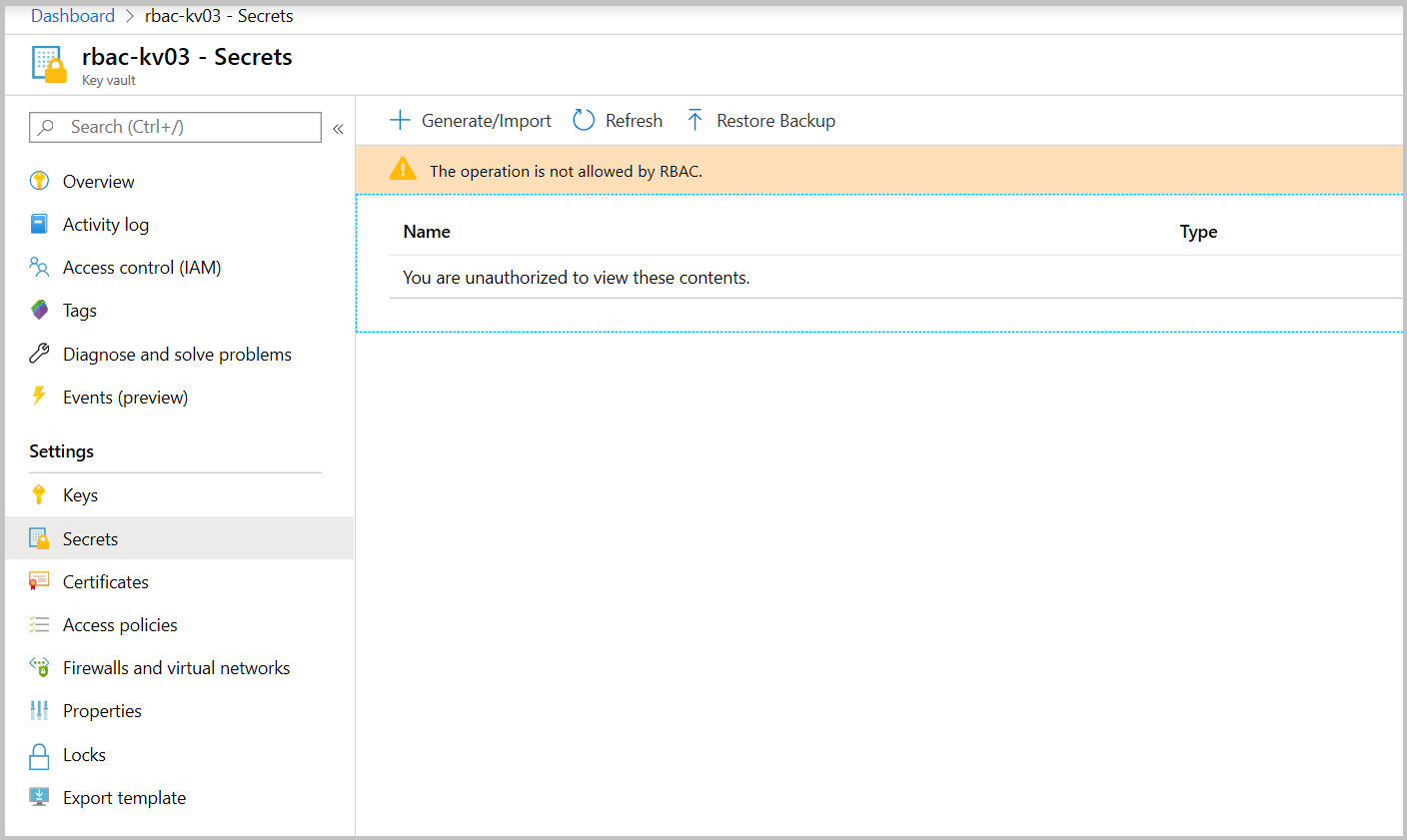
创建自定义角色
az role definition create --role-definition '{ \
"Name": "Backup Keys Operator", \
"Description": "Perform key backup/restore operations", \
"Actions": [], \
"DataActions": [ \
"Microsoft.KeyVault/vaults/keys/read ", \
"Microsoft.KeyVault/vaults/keys/backup/action", \
"Microsoft.KeyVault/vaults/keys/restore/action" \
], \
"NotDataActions": [], \
"AssignableScopes": ["/subscriptions/{subscriptionId}"] \
}'
有关如何创建自定义角色的详细信息,请参阅:
常见问题
是否可以使用 Azure RBAC 对象范围分配为 Key Vault 中的应用程序团队提供隔离?
否。 Azure RBAC 权限模型允许向用户或应用程序分配对 Key Vault 中各个对象的访问,但任何管理作(如网络访问控制、监视和对象管理)都需要保管库级别权限,这样就可以向应用程序团队中的操作员公开安全信息。