了解 Azure 负载均衡器中出站连接的故障排除指南。 这包括了解源网络地址转换 (SNAT) 及其对连接的影响、使用 VM 上的单个公共 IP 以及设计应用程序以确保连接效率,以避免 SNAT 端口耗尽。 客户遇到的大多数出站连接问题是由于 SNAT 端口耗尽和连接超时导致数据包丢失。
若要了解有关 SNAT 端口的详细信息,请参阅出站连接的源网络地址转换。
了解 SNAT 端口使用情况
遵循通过指标、警报和资源运行状况进行标准负载均衡器诊断中的说明,监视现有负载均衡器的 SNAT 端口使用情况和分配。 监视以确认或确定 SNAT 耗尽的风险。 如果难以理解出站连接行为,请使用 IP 堆栈统计 (netstat) 或收集数据包捕获。 可以在实例的来宾 OS 中执行这些数据包捕获,或使用网络观察程序来捕获数据包。 对于大多数方案,Azure 建议使用 NAT 网关进行出站连接,以减少 SNAT 耗尽的风险。 如果服务启动到同一目标的重复 TCP 或 UDP 出站连接,则强烈建议使用 NAT 网关。
优化 Azure 部署以建立出站连接
优化 Azure 部署以建立出站连接非常重要。 优化可以防范或缓解出站连接的问题。
为出站 Internet 连接部署 NAT 网关
Azure NAT 网关是一种高度可复原且可缩放的 Azure 服务,它提供从虚拟网络到 Internet 的出站连接。 NAT 网关使用 SNAT 端口的唯一方法有助于解决常见的 SNAT 耗尽和连接问题。 有关 Azure NAT 网关的详细信息,请参阅什么是 Azure NAT 网关?。
NAT 网关如何降低 SNAT 端口耗尽的风险?
Azure 负载均衡器将固定数量的 SNAT 端口分配给后端池中的每个虚拟机实例。 这种分配方法可能会导致 SNAT 耗尽,尤其遇到流量模式不均衡导致特定虚拟机发送更高的传出连接量的情况。 与负载均衡器不同,NAT 网关在子网中的所有 VM 实例之间动态分配 SNAT 端口。
NAT 网关让子网中的每个实例都可以使用 SNAT 端口。 利用此动态分配,VM 实例可从可用端口池中使用每个实例所需数量的 SNAT 端口进行新连接。 动态分配可降低 SNAT 耗尽的风险。
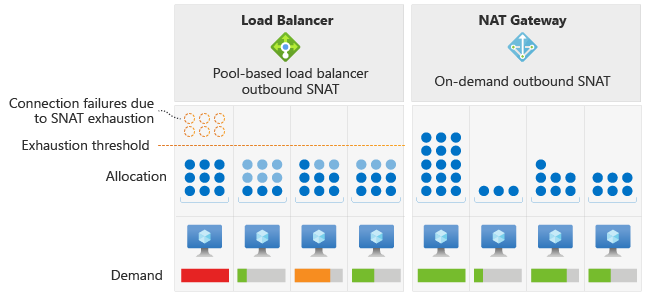
端口选择和重用行为。
NAT 网关从可用端口池中随机选择端口。 如果没有可用的端口,只要没有与同一目标公共 IP 和端口的现有连接,就会重复使用 SNAT 端口。 NAT 网关的此端口选择和重用行为使得遇到连接超时的可能性较低。
若要详细了解 SNAT 和端口使用情况如何适用于 NAT 网关,请参阅 SNAT 基础知识。 在某些情况下,无法将 NAT 网关用于出站连接。 有关 NAT 网关限制的详细信息,请参阅 NAT 网关限制。
如果无法使用 NAT 网关进行出站连接,请参阅本文中所述的其他迁移选项。
配置负载均衡器出站规则以最大化每个 VM 的 SNAT 端口
如果使用公共标准负载均衡器并遇到 SNAT 耗尽或连接故障,请确保使用包含手动端口分配的出站规则。 否则,可能依赖于负载均衡器的默认端口分配。 默认端口分配会根据后端池中的实例数,自动分配保守数量的端口。 建议不要使用默认端口分配方法来启用出站连接。 当后端池缩放时,如果需要重新分配端口,连接可能会受到影响。
若要详细了解默认端口分配,请参阅出站连接的源网络地址转换。
若要增加每个 VM 的可用 SNAT 端口数,请在负载均衡器上配置包含手动端口分配的出站规则。 例如,若已知后端池中最多有 10 个 VM,则可以为每个 VM 最多分配 6,400 个 SNAT 端口,而不是默认的 1,024 个。 如果需要更多 SNAT 端口,可以为出站连接添加多个前端 IP 地址,将可用的 SNAT 端口数倍增。 在添加更多前端 IP 地址之前,请确保了解 SNAT 端口耗尽的原因。
有关详细指导,请参阅本文后面的将应用程序设计为高效使用连接。 若要为出站连接添加更多 IP 地址,请为每个新 IP 创建前端 IP 配置。 配置出站规则后,你可以为后端池选择多个前端 IP 配置。 建议对入站和出站连接使用不同的 IP 地址。 不同的 IP 地址可隔离流量,以利于监视和故障排除。
在 VM 上配置单个公共 IP
对于较小的规模部署,可以考虑将公共 IP 分配给 VM。 如果向 VM 分配公共 IP,则公共 IP 提供的所有端口都可用于 VM。 与负载均衡器或 NAT 网关不同,端口只能访问与 IP 地址关联的单个 VM。
强烈建议考虑改用 NAT 网关,因为分配单个公共 IP 地址不是可缩放的解决方案。
注意
如果需要将 Azure 虚拟网络连接到 Azure PaaS 服务,例如 Azure 存储、Azure SQL、Azure Cosmos DB 或其他可用的 Azure 服务,则可以利用 Azure 专用链接完全避免 SNAT。 Azure 专用链接通过 Microsoft Azure 主干网络(而不是通过 Internet)将来自虚拟网络的流量发送到 Azure 服务。
关于对 Azure 托管服务的专用访问,建议首选专用链接而不是服务终结点。 有关专用链接和服务终结点之间的差异的详细信息,请参阅比较专用终结点和服务终结点。
设计高效连接的应用程序
设计应用程序时,请确保它们高效使用连接。 连接效率可以减少或消除已部署应用程序中的 SNAT 端口耗尽问题。
修改应用程序以重复使用连接
建议将应用程序配置为重复使用连接,而不是为每个请求生成单独的原子 TCP 连接。 连接重用会产生性能更高的 TCP 事务,并与 HTTP/1.1 之类的协议尤其相关,在这些协议中,默认设置是重复使用连接。 此重用适用于使用 HTTP 作为其传输的其他协议,例如 REST。
修改应用程序以使用连接池
在应用程序中使用连接池方案,其中在一组固定的连接中内部分布请求,并且在可能的情况下,重复使用这些请求。 此方案会限制正在使用的 SNAT 端口的数量,并创建更加可预测的环境。
此方案可以通过在操作答复上单个连接阻塞时允许多个同时操作,增加请求的吞吐量。
连接池可能已经存在于正在使用的框架中,以开发应用程序或应用程序的配置设置。 可将连接池与连接重复使用相结合。 多个请求使用指向相同目标 IP 地址和端口的可预测固定数量的端口。
请求可以从 TCP 事务的高效使用中受益,从而减少延迟和资源利用。 UDP 事务也可以受益。 通过管理 UDP 流的数量可以避免耗尽情况和管理 SNAT 端口利用率。
修改应用程序以使用主动性较低的重试逻辑
当 SNAT 端口耗尽或应用程序故障发生时,无衰减或回退逻辑的积极重试或暴力重试会使耗尽状况再次发生或一直持续。 使用主动性较低的重试逻辑,可以降低对 SNAT 端口的需求。
根据配置的空闲超时,如果重试过于频繁,则连接可能没有足够的时间关闭和释放 SNAT 端口以供重复使用。
使用 keepalive 重置出站空闲超时
默认情况下,负载均衡器出站规则有 4 分钟的空闲超时,该超时最多可以调整到 100 分钟。 还可以使用 TCP keepalive 刷新空闲流,并在必要时重置此空闲超时。 使用 TCP keepalive 时,在连接的一端启用它们就足够了。
例如,若要重置流的空闲计时器,在服务器端启用它们就足够了,没有必要在两端都启动 TCP keepalive。 应用程序层(包括数据库客户端-服务器配置)也存在类似的概念。 检查服务器端对于特定于应用程序的 keepalive 存在哪些选项。
后续步骤
有关 SNAT 端口耗尽、出站连接选项和默认出站访问的详细信息,请参阅: