若要提高调用 API 的安全性,可通过 Azure 门户设置 Microsoft Entra 身份验证,这样就无需更新代码。 或者,还可利用 API 代码要求并强制执行身份验证。
可以通过以下方式添加身份验证:
无需更改代码:通过 Azure 门户使用 Microsoft Entra ID 保护 API,这样就无需更新代码或重新部署 API。
注释
默认情况下,在 Azure 门户中选择的 Microsoft Entra 身份验证不提供细化的授权。 例如,此身份验证将 API 锁定到特定租户,而不是特定用户或应用。
更新 API 的代码:通过代码强制 实施证书身份验证 或 Microsoft Entra 身份验证 来保护 API。
在不更改代码的情况下,验证对 API 的调用
下面是此方法的常规步骤:
创建两个Microsoft Entra 应用程序标识(应用注册):一个用于逻辑应用资源,一个用于 Web 应用(或 API 应用)。
要验证对 API 的调用,请对与逻辑应用的 Microsoft Entra 应用程序标识相关联的服务主体使用凭据(客户端 ID 和密码)。
在逻辑应用的工作流定义中包含此应用程序 ID。
第 1 部分:为逻辑应用创建 Microsoft Entra 应用程序标识
逻辑应用资源使用此 Microsoft Entra 应用程序标识对 Microsoft Entra ID 进行身份验证。 只需为租户将此标识设置一次。 例如,可选择为所有逻辑应用使用相同标识,但也可为每个逻辑应用创建唯一标识。 可以在 Azure 门户中或者使用 PowerShell 设置这些标识。
在 Azure 门户 搜索框中,找到并选择 Microsoft Entra ID。
确认所在租户与 Web 应用或 API 应用相同。
小窍门
若要切换租户,请从 Azure 顶部标题栏中打开个人资料,然后选择“切换目录”。
在租户资源菜单上的“ 管理”下,选择 “应用注册”。
“应用注册”页显示租户中的所有应用注册。 若要仅查看自己的应用注册,请选择“拥有的应用程序”。
在工具栏上,选择新建注册。
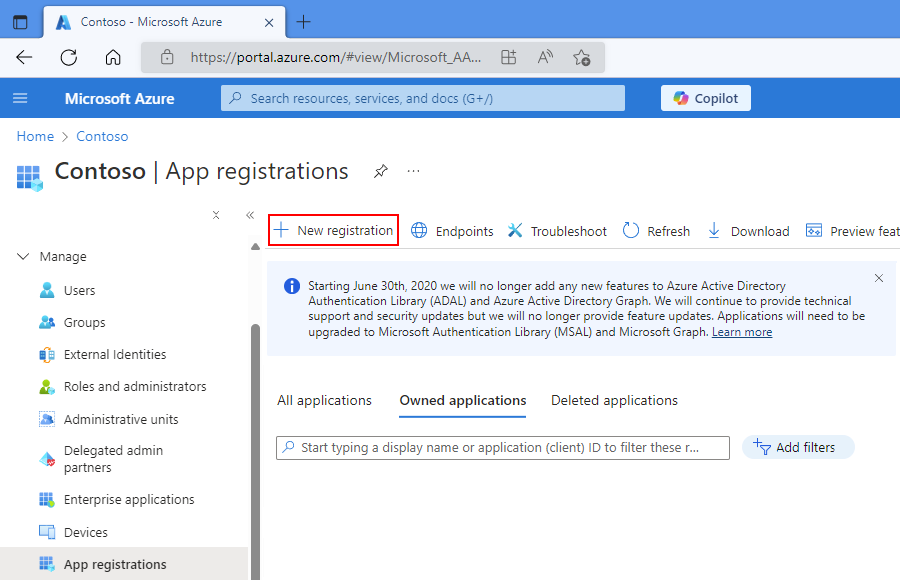
在 “注册应用程序 ”页上,执行以下步骤:
对于 Name,请为逻辑应用的应用程序标识提供一个友好的面向用户的名称。
在 “支持的帐户类型”下,选择最能描述可以使用应用程序标识或获取 API 访问权限的帐户类型的选项。
在重定向 URI 下,选择 Web 作为平台。 在此选项旁边,提供用于返回身份验证响应的位置的唯一 URL。
完成后,选择“ 注册”。
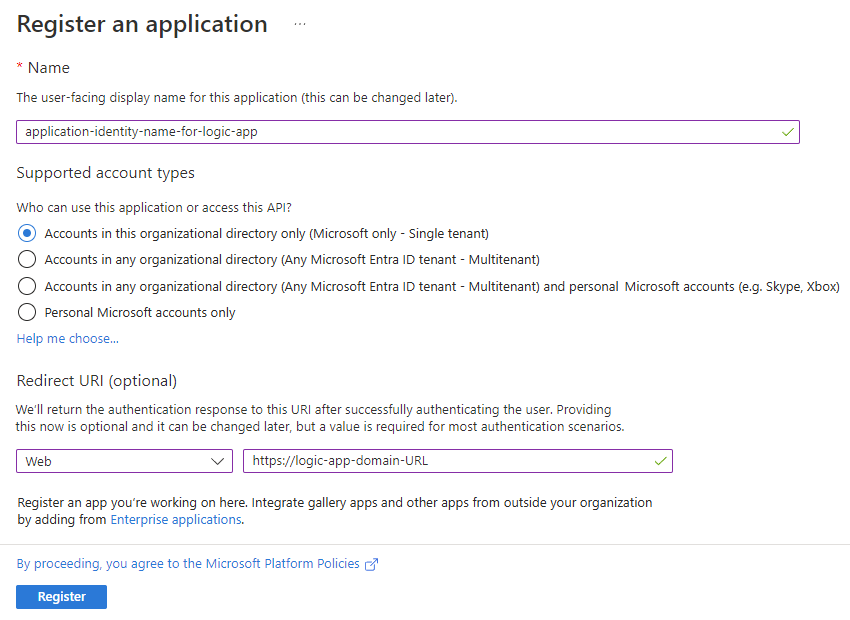
“ 拥有的应用程序 ”选项卡现在显示已创建的应用程序标识。 如果未显示此标识,请在工具栏上选择“刷新”。
从应用注册列表中,选择新的应用程序标识。
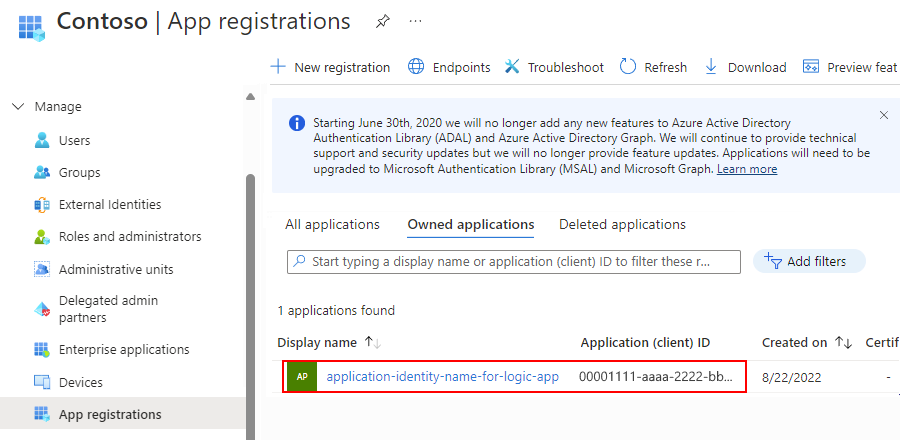
从应用程序标识导航菜单中,选择“概述”。
在 “概述 ”页上的 “概要”下,复制并保存 应用程序(客户端)ID ,以用作第 3 部分中逻辑应用的客户端 ID。
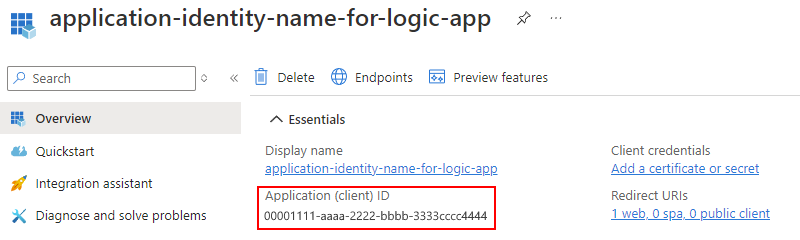
在应用程序标识菜单中的“ 管理”下,选择“ 证书和机密”。
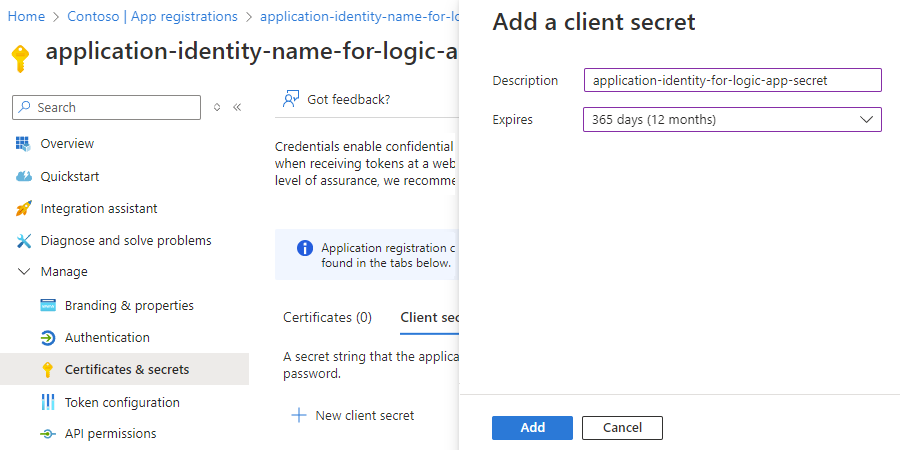
在 “客户端机密 ”页上,选择“ 新建客户端密码”。
在 “添加客户端机密 ”窗格中,对于 “说明”,提供机密的名称。 对于“过期”,请为机密选择持续时间。 完成后,选择“添加”。
创建的机密将充当逻辑应用的应用程序标识的“机密”或密码。
在 “证书和机密 ”页上的 “客户端机密 ”选项卡上,你的机密现在随机密值和机密 ID 一起显示。
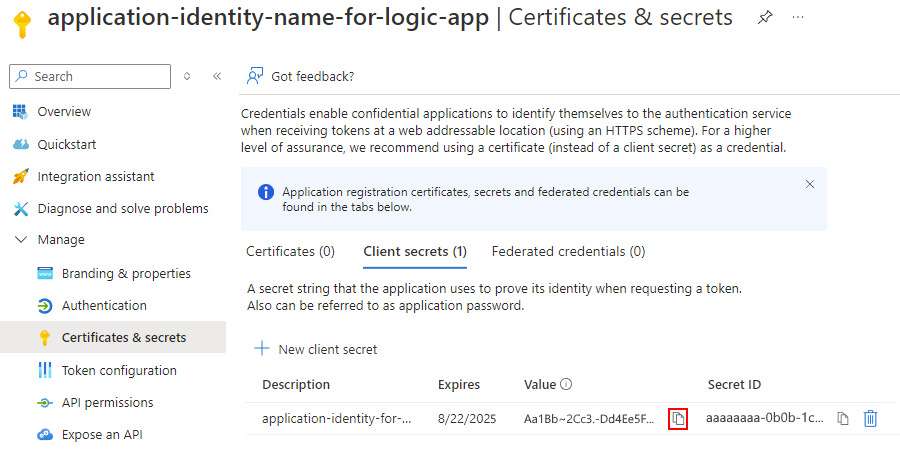
复制机密值以备后用。 在第 3 部分配置逻辑应用时,请指定该值作为“密钥”或密码。
第 2 部分:为 Web 应用或 API 应用创建 Microsoft Entra 应用程序标识
如果已部署 Web 应用或 API 应用,则可在 Azure 门户中开启身份验证并创建应用程序标识。 否则,可以在使用 Azure 资源管理器模板部署时开启身份验证。
在 Azure 门户中为已部署的 Web 应用或 API 应用创建应用程序标识
在 Azure 门户中,找到并选择 Web 应用或 API 应用。
在“设置”下,选择“身份验证”“添加标识提供者”。
“添加标识提供者”窗格打开后,在“基本信息”选项卡上,从“标识提供者”列表中,选择“Microsoft”以使用 Microsoft Entra 标识,然后选择“添加”。
现在为 Web 应用或 API 应用创建应用程序标识,如下所示:
对于“应用注册类型”,请选择“新建应用注册”。
对于“名称”,请为应用程序标识提供一个名称。
对于“支持的帐户类型”,请选择适合方案的帐户类型。
对于“限制访问”,请选择“需要身份验证”。
对于“未经身份验证的请求”,请根据方案选择选项。
完成后,选择“添加”。
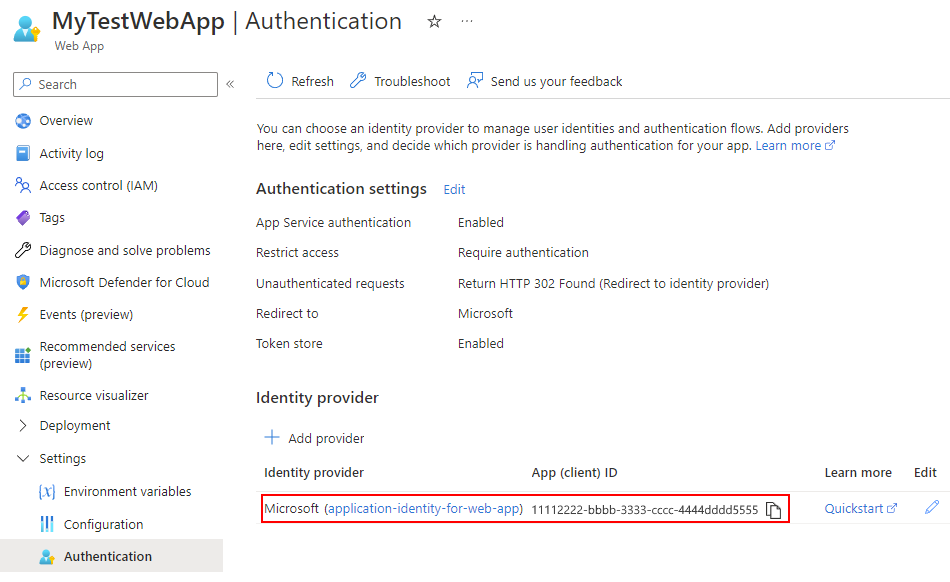
在 “标识提供者 ”部分中,将显示 Web 应用或 API 应用的新应用程序标识:
小窍门
如果未显示此应用程序标识,请在工具栏上选择“刷新”。
现在,必须找到刚刚为 Web 应用或 API 应用创建的应用程序标识的应用程序(客户端)ID 和租户 ID。 第 3 部分需使用这些 ID。 因此,请对 Azure 门户继续执行以下步骤。
在 Azure 门户中查找 Web 应用或 API 应用的应用程序标识的客户端 ID 和租户 ID
在 Web 应用菜单上的“ 管理”下,选择“ 身份验证”。
在 “标识提供者 ”部分中,找到以前创建的应用程序标识。 选择应用程序标识名称。
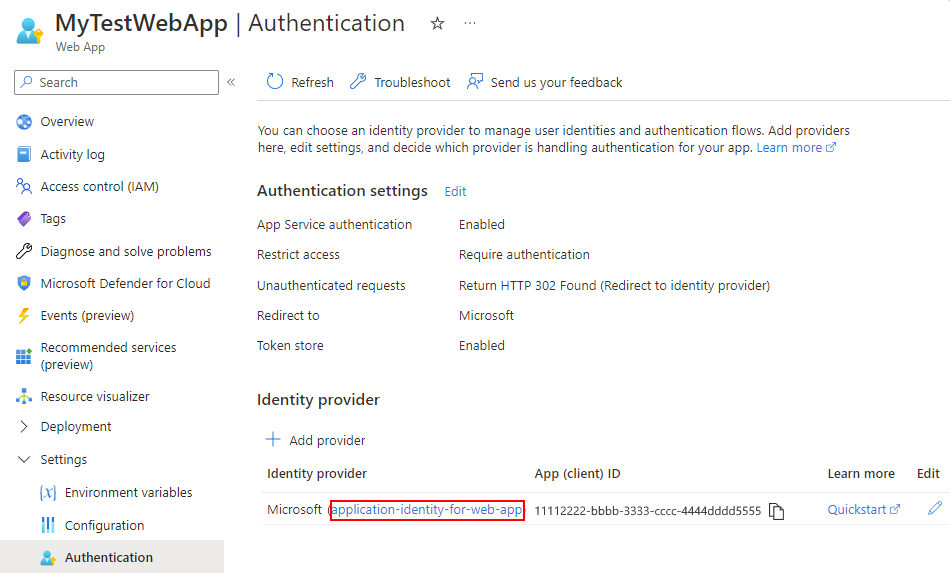
在 “概述 ”页上,查找 应用程序(客户端)ID 和 目录(租户)ID 的值。 复制并保存该值,以便在第 3 部分使用。
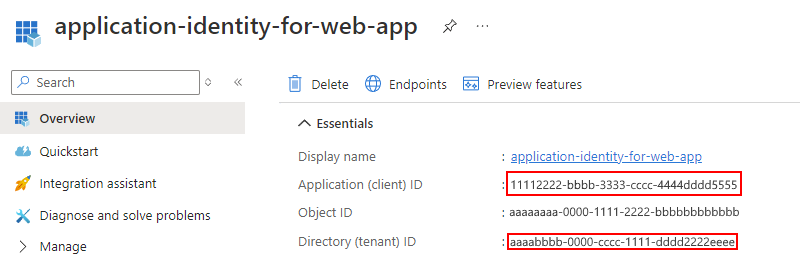
如有必要,还可在 Web 应用或 API 应用的部署模板中使用租户 ID GUID。 此 GUID 是你的特定租户的 GUID(“租户 ID”),应显示在此 URL 中:
https://sts.chinacloudapi.cn/<tenant-GUID>
使用 Azure 资源管理器模板部署时设置身份验证
如果使用的是 Azure 资源管理器模板(ARM 模板),仍需为 Web 应用或 API 应用创建 Microsoft Entra 应用程序标识,该标识与逻辑应用的应用标识不同。 若要创建应用程序标识,然后查找客户端 ID 和租户 ID,请对 Azure 门户执行前面第 2 部分中的步骤。 你将在应用的部署模板以及第 3 部分中同时使用客户端 ID 和租户 ID。
重要
为 Web 应用或 API 应用创建 Microsoft Entra 应用程序标识时,必须使用 Azure 门户,而不是 PowerShell。 PowerShell commandlet 没有设置可让用户登录到网站的必需权限。
获得客户端 ID 和租户 ID 后,将这些 ID 作为 Web 应用或 API 应用的子资源包含在部署模板中:
"resources": [
{
"apiVersion": "2015-08-01",
"name": "web",
"type": "config",
"dependsOn": ["[concat('Microsoft.Web/sites/','parameters('webAppName'))]"],
"properties": {
"siteAuthEnabled": true,
"siteAuthSettings": {
"clientId": "<client-ID>",
"issuer": "https://sts.chinacloudapi.cn/<tenant-ID>/"
}
}
}
]
若要使用 Microsoft Entra 身份验证自动同时部署空白 Web 应用和逻辑应用,请在此处查看完整模板或选择以下“部署到 Azure”按钮:
第 3 部分:填充逻辑应用中的授权部分
上面的模板已设置了此授权部分,但如果要直接对逻辑应用定义进行授权,则必须包括完整的授权部分。
在代码视图中打开逻辑应用定义。
转到“HTTP”操作定义,找到“授权”部分,将以下属性包含在其中:
{
"tenant": "<tenant-ID>",
"audience": "<client-ID-from-Part-2-web-app-or-API app>",
"clientId": "<client-ID-from-Part-1-logic-app>",
"secret": "<secret-from-Part-1-logic-app>",
"type": "ActiveDirectoryOAuth"
}
| 资产 | 必选 | DESCRIPTION |
|---|---|---|
tenant |
是的 | Microsoft Entra 租户的 GUID。 |
audience |
是的 | 要访问的目标资源的 GUID,它是 Web 应用或 API 应用的应用程序标识中的客户端 ID。 |
clientId |
是的 | 请求访问权限的客户端的 GUID - 逻辑应用的应用程序标识中的客户端 ID。 |
secret |
是的 | 请求访问令牌的客户端的应用程序标识中的机密或密码。 |
type |
是的 | 身份验证类型。 对于 ActiveDirectoryOAuth 身份验证,该值为 ActiveDirectoryOAuth。 |
例如:
{
"actions": {
"HTTP": {
"inputs": {
"method": "POST",
"uri": "https://your-api-chinacloudsites.cn/api/your-method",
"authentication": {
"tenant": "tenant-ID",
"audience": "client-ID-from-azure-ad-app-for-web-app-or-api-app",
"clientId": "client-ID-from-azure-ad-app-for-logic-app",
"secret": "key-from-azure-ad-app-for-logic-app",
"type": "ActiveDirectoryOAuth"
}
}
}
}
}
通过代码保护 API 调用
证书身份验证
若要验证从逻辑应用工作流传入 Web 应用或 API 应用的请求,可以使用客户端证书。 若要设置代码,请了解如何配置 TLS 相互身份验证。
重要
始终保护和保护敏感数据,例如凭据、机密、访问密钥、连接字符串、证书、指纹以及具有最高可用或受支持的安全级别的类似信息。
确保使用 Microsoft Entra ID 和 Azure 密钥保管库安全存储此类信息。 不要硬编码此信息、与其他用户共享或保存在其他人可以访问的任何位置的纯文本中。 设置计划以轮换或撤销机密,以防机密被盗用。 有关详细信息,请参阅以下资源:
在“授权”部分中包含以下属性:
{
"type": "ClientCertificate",
"password": "<password>",
"pfx": "<long-pfx-key>"
}
| 资产 | 必选 | DESCRIPTION |
|---|---|---|
type |
是的 | 身份验证类型。 对于 TLS/SSL 客户端证书,该值必须为 ClientCertificate。 |
password |
否 | 用于访问客户端证书的密码(PFX 文件)。 |
pfx |
是的 | 客户端证书(PFX 文件)的 base64 编码内容。 |
基本身份验证
若要验证从逻辑应用传入 Web 应用或 API 应用的请求,可以使用基本身份验证,如用户名和密码。 尽管基本身份验证是一种常见的模式,但你可以使用任何语言使用此身份验证来生成 Web 应用或 API 应用,但始终使用可用的或受支持的最佳身份验证级别。
警告
Microsoft 建议不要使用以下流程进行身份验证和授权:
OAuth 2.0 的资源所有者密码凭据 (ROPC)
此流允许使用密码登录到应用程序。 该流与多重身份验证(MFA)不兼容,需要在应用程序中高度信任,并且存在其他流中不存在的风险。 仅当其他更安全的流不受支持或可用时,才使用此流。
有关详细信息,请参阅 Oauth 2.0 资源所有者密码凭据。
OAuth 2.0 的隐式授权流
此基于令牌的流适用于传统 Web 应用,其中服务器对处理
POST数据具有更安全的控制,并且通常用于 授权代码流。 由于此流处理和返回 ID 令牌或访问令牌的方式,流要求在应用程序中高度信任,并具有其他流中不存在的风险。 仅当其他更安全的流不受支持或不可用时,才使用此流。有关详细信息,请参阅 OAuth 2.0 隐式授权流。
在“授权”部分中包含以下属性:
{
"type": "Basic",
"username": "<username>",
"password": "<password>"
}
| 资产 | 必选 | DESCRIPTION |
|---|---|---|
type |
是的 | 要使用的身份验证类型。 对于基本身份验证,该值必须为 **Basic**。 |
username |
是的 | 要用于身份验证的用户名。 |
password |
是的 | 要用于身份验证的密码。 |
通过代码进行 Microsoft Entra 身份验证
默认情况下,在 Azure 门户中启用的 Microsoft Entra 身份验证不提供细化的授权。 例如,此身份验证将 API 锁定到特定租户,而不是特定用户或应用。
若要通过代码限制 API 访问逻辑应用,请提取具有 JSON Web 令牌 (JWT) 的标头。 检查调用方的标识,并拒绝不匹配的请求。
