在本快速入门中,你要部署虚拟机并使用网络观察程序 IP 流验证来测试与不同 IP 地址的连接。 使用 IP 流验证功能得到的结果,可以确定阻止流量并导致通信失败的安全规则,并了解如何解决该问题。 你还将了解如何使用网络接口的有效安全规则来确定安全规则允许或拒绝流量的原因。
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
先决条件
- 具有活动订阅的 Azure 帐户
登录 Azure
使用 Azure 帐户登录到 Azure 门户。
创建虚拟机
在门户顶部的搜索框中,输入“虚拟机”。 在搜索结果中,选择“虚拟机”。
选择“+ 新建”。
在“创建虚拟机”中,在“基本信息”选项卡中输入或选择以下值:
设置 值 项目详细信息 订阅 选择 Azure 订阅。 资源组 选择“新建”。
在“名称”中输入“myResourceGroup” 。
选择“确定”。实例详细信息 虚拟机名称 输入myVM。 区域 选择“中国东部”。 可用性选项 选择“无需基础结构冗余”。 安全类型 保留默认值标准。 映像 选择“Ubuntu Server 20.04 LTS - x64 Gen2”。 大小 选择大小或保留默认设置。 管理员帐户 身份验证类型 选择密码。 用户名 输入用户名。 Password 输入密码。 确认密码 重新输入密码。 选择“网络”选项卡,或选择“下一步: 磁盘”,然后选择“下一步: 网络”。
在“网络”选项卡中,选择“新建”以创建新的虚拟网络。
在“创建虚拟网络”中,输入或选择以下值:
设置 值 名称 输入 myVNet。 地址空间 地址范围 输入 10.0.0.0/16。 子网 子网名称 输入 mySubnet。 地址范围 输入 10.0.0.0/24。 选择“确定”。
在“网络”选项卡中,输入或选择以下值:
设置 值 公共 IP 选择无。 NIC 网络安全组 选择基本。 公共入站端口 选择“无”。 注意
Azure 将为 myVM 虚拟机创建默认网络安全组(因为你选择了基本 NIC 网络安全组)。 在下一部分中,你将使用此默认网络安全组来测试传入和来自虚拟机的网络通信。
选择“查看 + 创建”。
检查设置,然后选择“创建”。
使用 IP 流验证测试网络通信
在本部分中,你要使用网络观察程序的 IP 流验证功能来测试传入和来自虚拟机的网络通信。
在门户顶部的搜索框中,输入“网络观察程序”。 在搜索结果中,选择“网络观察程序”。
在“网络诊断工具”下,选择“IP 流验证”。
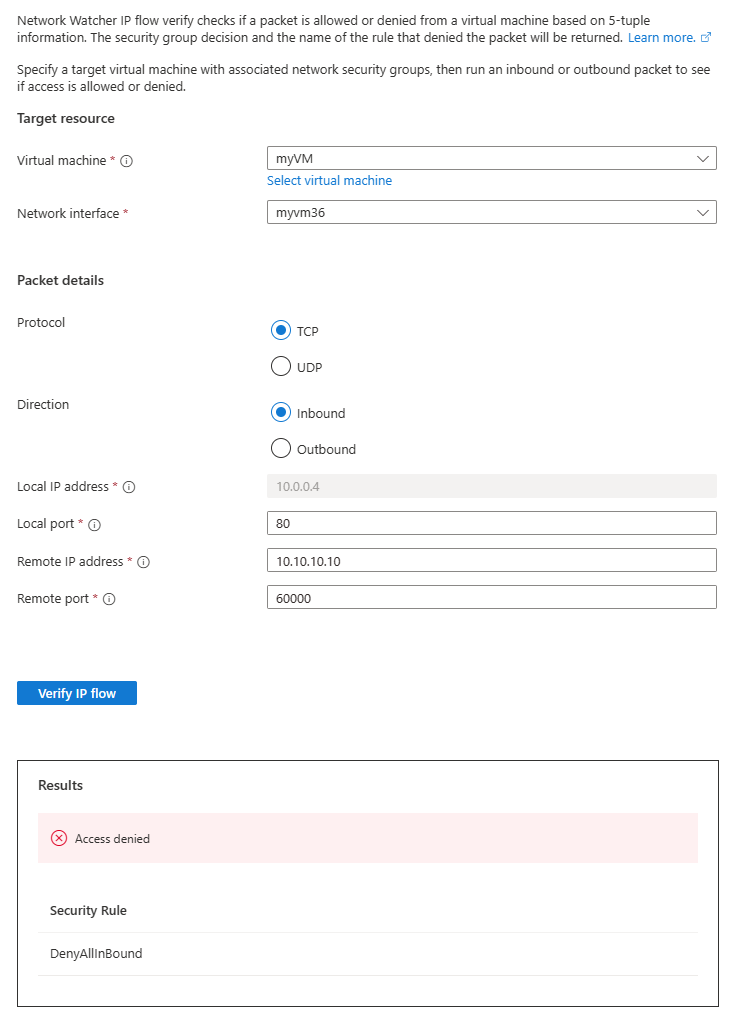
在“IP 流验证”页中,输入或选择以下值:
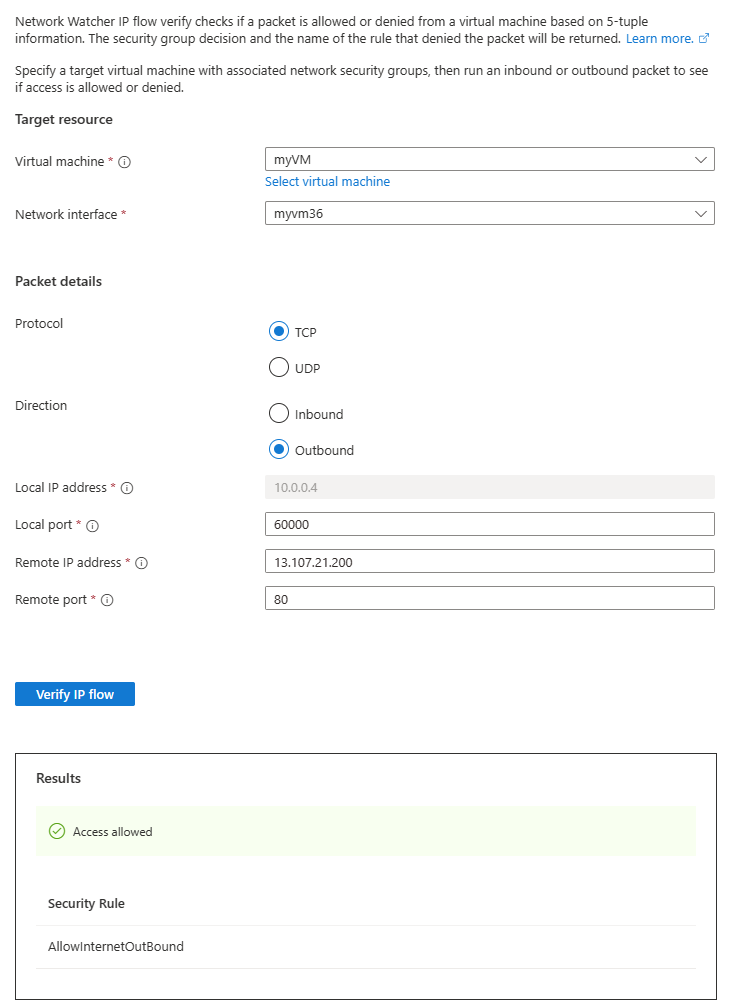
设置 值 目标资源 虚拟机 选择 myVM 虚拟机。 Linux 选择 myVM 的网络接口。 使用 Azure 门户创建虚拟机时,门户将使用虚拟机的名称和随机数命名网络接口(例如 myvm36)。 数据包详细信息 协议 选择“TCP”。 方向 选择“出站”。 本地端口 输入 60000。 从 Internet 分配号码机构 (IANA) 范围中选择任何端口号,用于动态或专用端口。 远程 IP 地址 输入 13.107.21.200。 此 IP 地址是 www.bing.com网站的一个 IP 地址。远程端口 输入 80 注意
如果在可供选择的虚拟机列表中看不到该虚拟机,请确保它正在运行。 已停止的虚拟机无法被选中进行 IP 流验证测试。
选择“验证 IP 流”按钮。
几秒钟后,可以看到测试结果,指示由于默认安全规则 AllowInternetOutBound,允许访问 13.107.21.200。
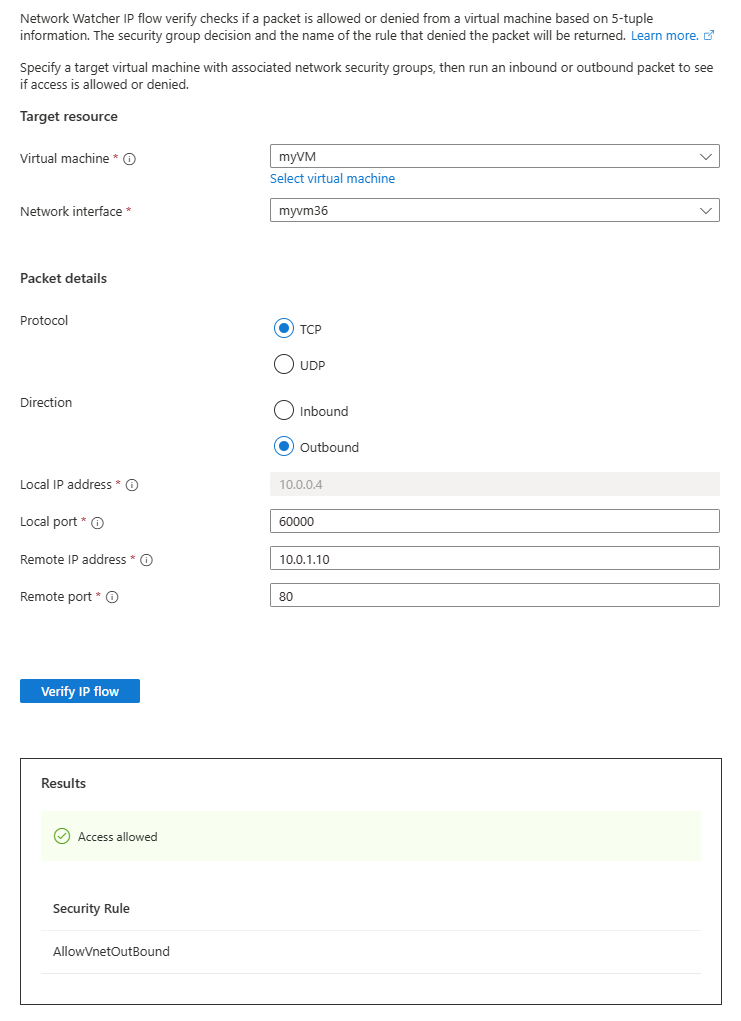
将远程 IP 地址更改为 10.0.1.10,这是 myVNet 地址空间中的专用 IP 地址。 然后选择“验证 IP 流”按钮重复测试。 第二次测试的结果指示,由于默认安全规则 AllowVnetOutBound,允许访问 10.0.1.10。
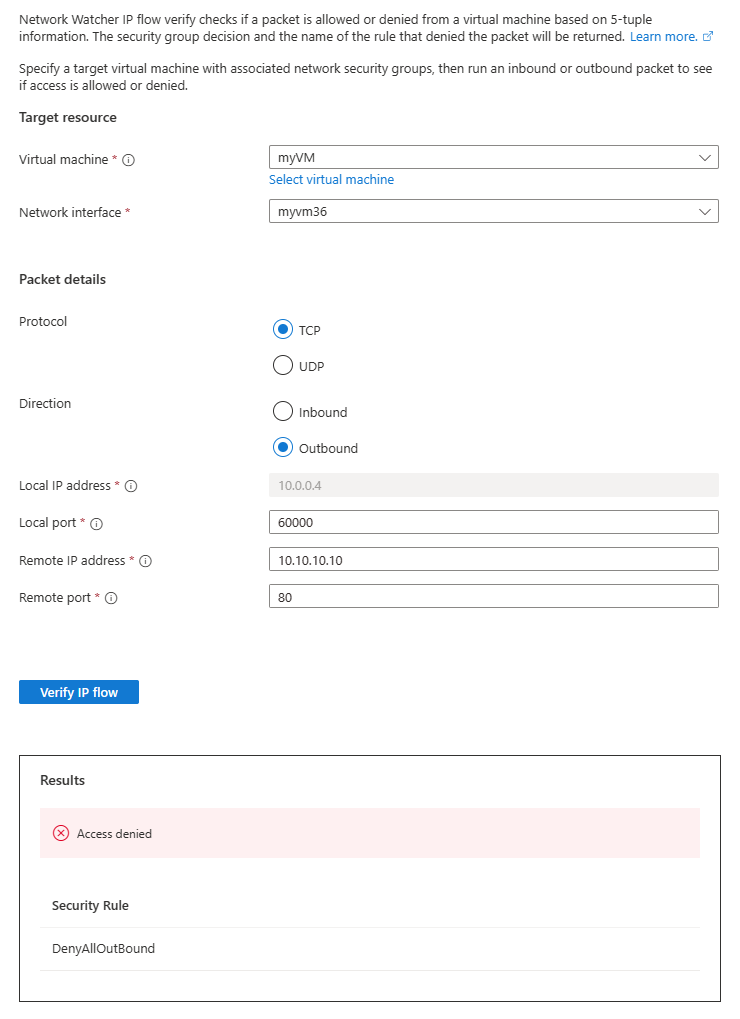
将远程 IP 地址更改为 10.10.10.10 并重复测试。 第三次测试的结果表明,由于默认安全规则 DenyAllOutBound,拒绝访问 10.10.10.10。
将“方向”更改为“入站”,将“本地端口”更改为“80”,将“远程端口”更改为“60000”,然后重复测试。 第四次测试的结果表明,由于默认安全规则 DenyAllInBound,拒绝来自 10.10.10.10 的访问。
查看安全规则的详细信息
要确定上一部分中的规则允许或拒绝通信的原因,请查看 myVM 虚拟机中网络接口的有效安全规则。
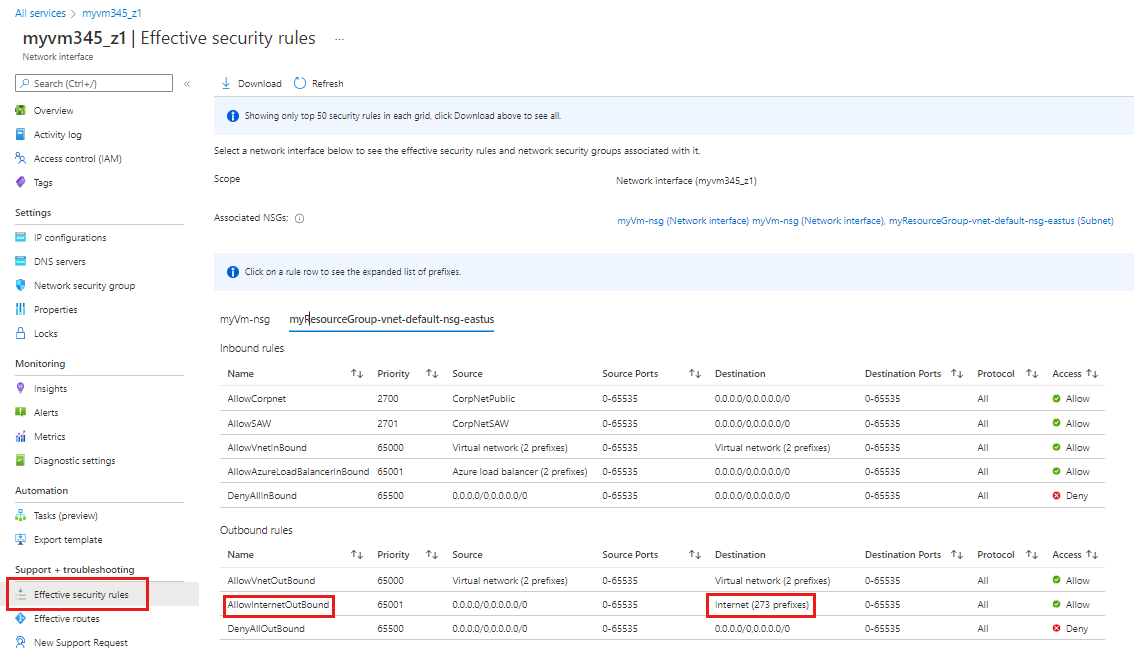
在“网络观察程序”中的“网络诊断工具”下,选择“有效安全规则”。
选择以下信息:
设置 值 订阅 选择 Azure 订阅。 资源组 选择“myResourceGroup”。 虚拟机 选择“myVM”。 注意
myVM 虚拟机具有一个网络接口,选择 myVM 后,将会选择该接口。 如果虚拟机有多个网络接口,请选择要查看其有效安全规则的网络接口。
在“出站规则”下,选择“AllowInternetOutBound”,查看此安全规则下允许的目标 IP 地址前缀。
可以看到地址前缀 13.104.0.0/13 是 AllowInternetOutBound 规则的地址前缀之一。 此前缀包含你在上一部分的步骤 4 中测试的 IP 地址 13.107.21.200。
同样,可以检查其他规则来查看每个规则下的源和目标 IP 地址前缀。
IP 流验证会检查 Azure 默认和配置的安全规则。 如果检查返回预期的结果,而网络问题仍然存在,请确保在虚拟机和要与之通信的终结点之间没有防火墙,且虚拟机中的操作系统没有会拒绝通信的防火墙。
清理资源
不再需要资源组时,可将资源组及其包含的所有资源一并删除:
在门户顶部的搜索框中输入 myResourceGroup。 从搜索结果中选择“myResourceGroup”。
选择“删除资源组” 。
在“删除资源组”中,输入 myResourceGroup,然后选择“删除”。
选择“删除”以确认删除资源组及其所有资源。