本文介绍如何使用 Azure 网络观察程序的排查连接问题功能来诊断和排查连接问题。 有关连接故障排除的详细信息,请参阅连接故障排除概述。
先决条件
拥有有效订阅的 Azure 帐户。 创建试用版订阅。
在您要排除故障的虚拟机 (VM) 所在区域中启用网络监视器。 默认情况下,在区域中创建虚拟网络时,Azure 会在该区域中启用网络观察程序。 有关详细信息,请参阅启用或禁用 Azure 网络观察程序。
具有以下出站 TCP 连接的虚拟机:
- 到 169.254.169.254(通过端口 80)
- 到 168.63.129.16(通过端口 8037)
第二台虚拟机,具备从 168.63.129.16 通过正在测试的端口的入站 TCP 连接(用于端口扫描程序诊断测试)。
拥有有效订阅的 Azure 帐户。 创建试用版订阅。
在您要排除故障的虚拟机 (VM) 所在区域中启用网络监视器。 默认情况下,在区域中创建虚拟网络时,Azure 会在该区域中启用网络观察程序。 有关详细信息,请参阅启用或禁用 Azure 网络观察程序。
具有以下出站 TCP 连接的虚拟机:
- 到 169.254.169.254(通过端口 80)
- 到 168.63.129.16(通过端口 8037)
第二台虚拟机,具备从 168.63.129.16 通过正在测试的端口的入站 TCP 连接(用于端口扫描程序诊断测试)。
Azure PowerShell。
也可以在本地安装 Azure PowerShell 以运行 cmdlet。 本文需要 Az PowerShell 模块。 有关详细信息,请参阅如何安装 Azure PowerShell。 如果在本地运行 PowerShell,请使用 Connect-AzAccount -Environment AzureChinaCloud cmdlet 登录到 Azure。
拥有有效订阅的 Azure 帐户。 创建试用版订阅。
在您要排除故障的虚拟机 (VM) 所在区域中启用网络监视器。 默认情况下,在区域中创建虚拟网络时,Azure 会在该区域中启用网络观察程序。 有关详细信息,请参阅启用或禁用 Azure 网络观察程序。
具有以下出站 TCP 连接的虚拟机:
- 到 169.254.169.254(通过端口 80)
- 到 168.63.129.16(通过端口 8037)
第二台虚拟机,具备从 168.63.129.16 通过正在测试的端口的入站 TCP 连接(用于端口扫描程序诊断测试)。
Azure CLI。
还可以 在本地安装 Azure CLI 以运行命令。 如果在本地运行 Azure CLI,请使用 az login 命令登录到 Azure。
测试与虚拟机的连接
在本部分中,将测试从一台虚拟机到同一虚拟网络中的另一台虚拟机的远程桌面端口 (RDP) 连接。
登录到 Azure 门户。
在门户顶部的搜索框中,输入“网络观察程序”。 在搜索结果中,选择“网络监视器”。
在“网络诊断工具”下,选择“连接故障排除”。 输入或选择下列值:
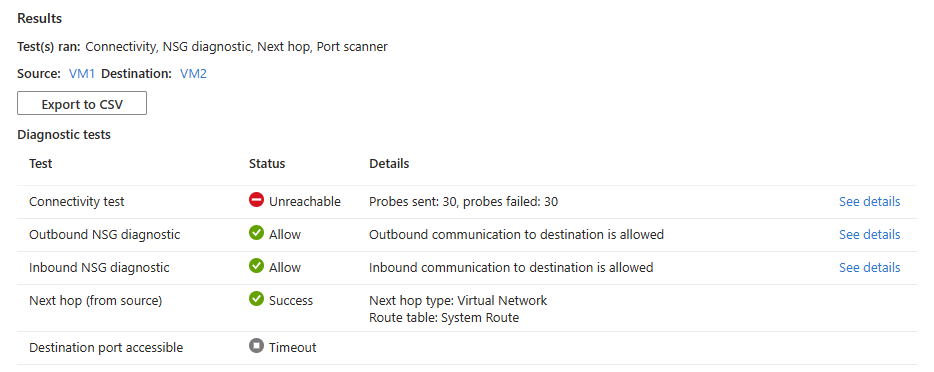
设置 价值 来源 源类型 选择“虚拟机”。 虚拟机 选择要进行连接故障排查的虚拟机。 目的地 目标类型 选择选择虚拟机。 虚拟机 选择目标虚拟机。 探测设置 首选 IP 版本 选择 IPv4。 其他可用选项包括:“两者”和“IPv6”。 协议 选择TCP。 其他可用选项包括:ICMP。 目标端口 输入“3389”。 端口 3389 是 RDP 的默认端口。 源端口 留空或输入要测试的源端口号。 连接诊断 诊断测试 选择“连接性”、“NSG 诊断”、“下一跳”和“端口扫描器”。 显示 Azure 门户中网络监视程序用于排查两台虚拟机间连接问题的屏幕截图。
选择“运行诊断测试”。
如果这两台虚拟机正在通信,没有问题,则会看到以下结果:
- 已成功将 66 个探测发送到目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 允许来自源虚拟机的出站连接。 选择查看详细信息来查看允许源虚拟机进行出站通信的安全规则。
- 允许与目标虚拟机的入站连接。 选择查看详细信息以查看允许入站通信到目标虚拟机的安全规则。
- Azure 默认系统路由用于在这两台虚拟机之间路由流量(路由表 ID:系统路由)。
- 在目标虚拟机上可以访问端口 3389。
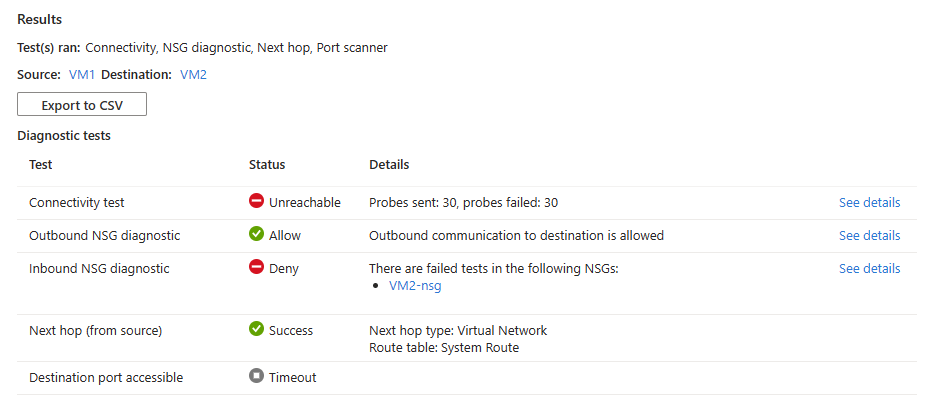
如果目标虚拟机具有拒绝传入 RDP 连接的网络安全组,则会看到以下结果:
- 已发送 30 个探测,未能到达目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 允许来自源虚拟机的出站连接。 选择查看详细信息来查看允许源虚拟机进行出站通信的安全规则。
- 拒绝与目标虚拟机的入站连接。 选择查看详细信息,以查看拒绝入站通信到目标虚拟机的安全规则。
- Azure 默认系统路由用于在这两台虚拟机之间路由流量(路由表 ID:系统路由)。
- 由于安全规则拒绝到目标端口的入站通信,无法在目标虚拟机上访问端口 3389。
解决方案:将目标虚拟机上的网络安全组更新为允许入站 RDP 流量。
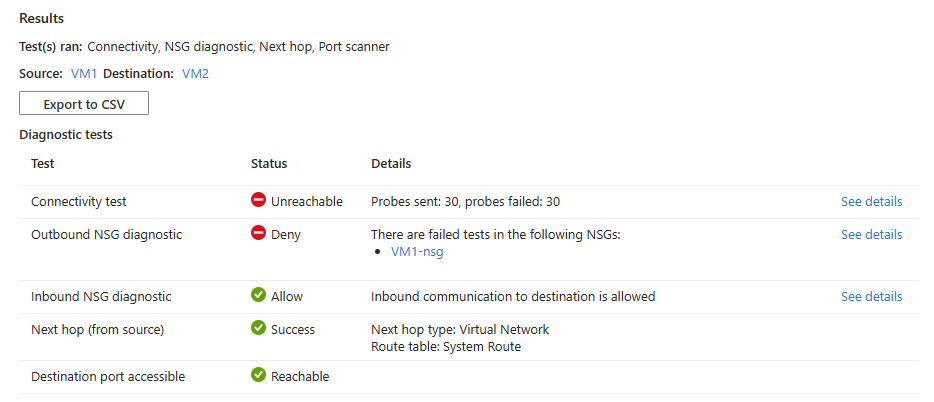
如果源虚拟机的网络安全组拒绝到目标的 RDP 连接,那么您会看到以下结果:
- 已发送 30 个探测,未能到达目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 拒绝来自源虚拟机的出站连接。 选择“查看详细信息”以查看拒绝源虚拟机出站通信的安全规则。
- 允许与目标虚拟机的入站连接。 选择查看详细信息以查看允许入站通信到目标虚拟机的安全规则。
- Azure 默认系统路由用于在这两台虚拟机之间路由流量(路由表 ID:系统路由)。
- 在目标虚拟机上可以访问端口 3389。
解决方案:更新源虚拟机上的网络安全组以允许出站 RDP 流量。
如果目标虚拟机上的操作系统不接受端口 3389 上的传入连接,则会看到以下结果:
- 已发送 30 个探测,未能到达目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 允许来自源虚拟机的出站连接。 选择查看详细信息来查看允许源虚拟机进行出站通信的安全规则。
- 允许与目标虚拟机的入站连接。 选择查看详细信息以查看允许入站通信到目标虚拟机的安全规则。
- Azure 默认系统路由用于在这两台虚拟机之间路由流量(路由表 ID:系统路由)。
- 无法在目标虚拟机上访问端口 3389(操作系统上的端口 3389 不接受传入 RDP 连接)。
解决方案:将目标虚拟机上的操作系统配置为接受入站 RDP 流量。
选择“导出到 CSV”以 CSV 格式下载测试结果。
使用 Test-AzNetworkWatcherConnectivity cmdlet 运行连接故障排除,以测试通过端口 3389 与虚拟机的连接:
# Test connectivity between two virtual machines that are in the same resource group over port 3389.
Test-AzNetworkWatcherConnectivity -Location 'chinaeast' -SourceId '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup1/providers/Microsoft.Compute/virtualMachines/VM1' -DestinationId '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup2/providers/Microsoft.Compute/virtualMachines/VM2' -DestinationPort '3389' | Format-List
如果这两台虚拟机正在通信,没有问题,则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Reachable AvgLatencyInMs : 1 MinLatencyInMs : 1 MaxLatencyInMs : 1 ProbesSent : 66 ProbesFailed : 0 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "VirtualMachine", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.0.0.5", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "NextHopIds": [], "Issues": [] } ]- 连接状态为“可访问”(可通过端口 3389 访问目标虚拟机)。
- 已成功将 66 个探测发送到目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
如果目标虚拟机具有拒绝传入 RDP 连接的网络安全组,则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "VirtualMachine", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.0.0.5", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "NextHopIds": [], "Issues": [ { "Origin": "Inbound", "Severity": "Error", "Type": "NetworkSecurityRule", "Context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM2-nsg/SecurityRules/Deny3389Inbound" } ] }, { "Origin": "Local", "Severity": "Error", "Type": "NoListenerOnDestination", "Context": [] } ] } ]- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 网络安全组
Deny3389Inbound中的安全规则VM2-nsg拒绝与目标虚拟机的入站连接。
解决方案:将目标虚拟机上的网络安全组更新为允许入站 RDP 流量。
如果源虚拟机的网络安全组拒绝到目标的 RDP 连接,那么您会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [ { "Origin": "Outbound", "Severity": "Error", "Type": "NetworkSecurityRule", "Context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM1-nsg/SecurityRules/Deny3389Outbound" } ] } ] }, { "Type": "VirtualMachine", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.0.0.5", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "NextHopIds": [], "Issues": [ { "Origin": "Local", "Severity": "Error", "Type": "NoListenerOnDestination", "Context": [] } ] } ]- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 网络安全组
Deny3389Outbound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。
解决方案:更新源虚拟机上的网络安全组以允许出站 RDP 流量。
如果目标虚拟机上的操作系统不接受端口 3389 上的传入连接,则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "VirtualMachine", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.0.0.5", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "NextHopIds": [], "Issues": [ { "Origin": "Local", "Severity": "Error", "Type": "NoListenerOnDestination", "Context": [] }, { "Origin": "Local", "Severity": "Error", "Type": "GuestFirewall", "Context": [] } ] } ]- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 无法在目标虚拟机上访问端口 3389(目标虚拟机上的输出具有
NoListenerOnDestination和GuestFirewall错误)。
解决方案:将目标虚拟机上的操作系统配置为接受入站 RDP 流量。
使用 az network watcher test-connectivity 命令运行连接故障排除诊断测试,以测试通过端口 3389 与虚拟机的连接:
# Test connectivity between two virtual machines that are in the same resource group over port 3389.
az network watcher test-connectivity --resource-group 'myResourceGroup' --source-resource 'VM1' --dest-resource 'VM2' --protocol 'TCP' --dest-port '3389'
注释
如果虚拟机不在同一资源组中,请使用其资源 ID 而不是其名称。 例如,使用以下命令测试位于两个不同资源组中的两个虚拟机之间的连接:
# Test connectivity between two virtual machines that are in two different resource groups over port 3389.
az network watcher test-connectivity --source-resource '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup1/providers/Microsoft.Compute/virtualMachines/VM1' --dest-resource '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup2/providers/Microsoft.Compute/virtualMachines/VM2' --protocol 'TCP' --dest-port '3389'
如果这两台虚拟机正在通信,没有问题,则会看到以下结果:
{ "avgLatencyInMs": 1, "connectionStatus": "Reachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "", "roundTripTimeAvg": 1, "roundTripTimeMax": 1, "roundTripTimeMin": 1 } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.0.0.5", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "type": "VirtualMachine" } ], "maxLatencyInMs": 1, "minLatencyInMs": 1, "probesFailed": 0, "probesSent": 66 }- 连接状态为“可访问”(可通过端口 3389 访问目标虚拟机)。
- 已成功将 66 个探测发送到目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
如果目标虚拟机具有拒绝传入 RDP 连接的网络安全组,则会看到以下结果:
{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.0.0.5", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [ { "context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM2-nsg/SecurityRules/Deny3389Inbound" } ], "origin": "Inbound", "severity": "Error", "type": "NetworkSecurityRule" }, { "context": [], "origin": "Local", "severity": "Error", "type": "NoListenerOnDestination" } ], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "type": "VirtualMachine" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 网络安全组
Deny3389Inbound中的安全规则VM2-nsg拒绝与目标虚拟机的入站连接。
解决方案:将目标虚拟机上的网络安全组更新为允许入站 RDP 流量。
如果源虚拟机的网络安全组拒绝到目标的 RDP 连接,那么您会看到以下结果:
{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [ { "context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM1-nsg/SecurityRules/Deny3389Outbound" } ], "origin": "Outbound", "severity": "Error", "type": "NetworkSecurityRule" } ], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.0.0.5", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [ { "context": [], "origin": "Local", "severity": "Error", "type": "NoListenerOnDestination" } ], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "type": "VirtualMachine" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 网络安全组
Deny3389Outbound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。
解决方案:更新源虚拟机上的网络安全组以允许出站 RDP 流量。
如果目标虚拟机上的操作系统不接受端口 3389 上的传入连接,则会看到以下结果:
{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.0.0.5", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [ { "context": [], "origin": "Local", "severity": "Error", "type": "NoListenerOnDestination" }, { "context": [], "origin": "Local", "severity": "Error", "type": "GuestFirewall" } ], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM2", "type": "VirtualMachine" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可通过端口 3389 访问目标虚拟机)。
- 已发送 30 个探测,未能到达目标虚拟机。
- 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 无法在目标虚拟机上访问端口 3389(目标虚拟机上的输出具有
NoListenerOnDestination和GuestFirewall错误)。
解决方案:将目标虚拟机上的操作系统配置为接受入站 RDP 流量。
测试与 Web 地址的连接
本部分将测试虚拟机与 web 地址之间的连接。
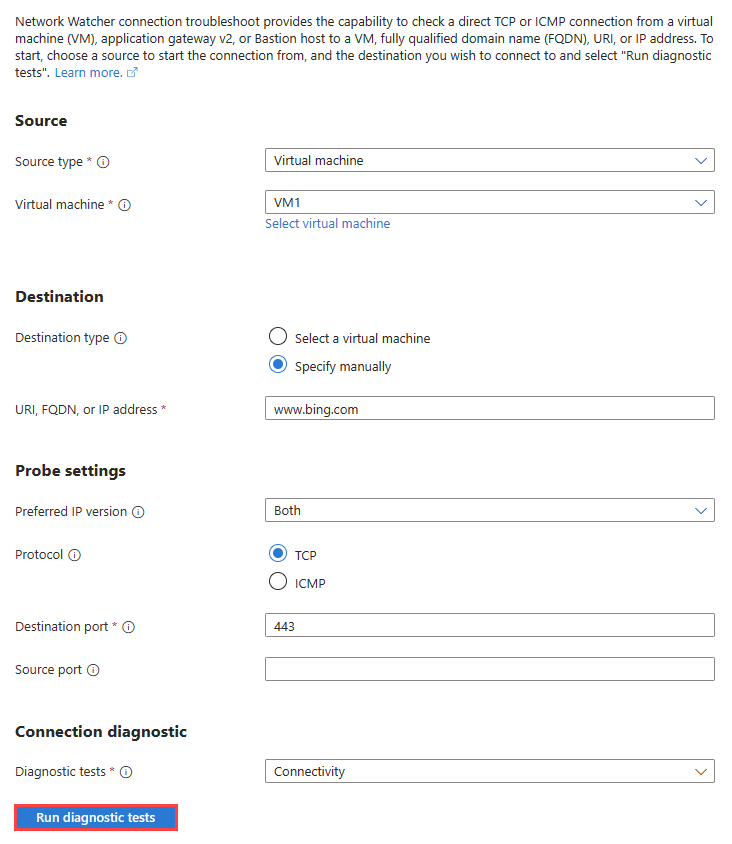
在“连接故障排除”页上。 输入或选择以下信息:
设置 价值 来源 源类型 选择“虚拟机”。 虚拟机 选择要进行连接故障排查的虚拟机。 目的地 目标类型 选择手动指定。 URI、FQDN 或 IP 地址 输入要测试其连接的 Web 地址。 在此示例中,使用 www.bing.com。探测设置 首选 IP 版本 选择同时。 其他可用选项包括:IPv4和IPv6。 协议 选择TCP。 其他可用选项包括:ICMP。 目标端口 输入 443。 对于 HTTPS,使用端口 443。 源端口 留空或输入要测试的源端口号。 连接诊断 诊断测试 选择“连接”。 选择“运行诊断测试”。
选择“导出到 CSV”以 CSV 格式下载测试结果。
使用 Test-AzNetworkWatcherConnectivity cmdlet 运行连接故障排除,以测试与 www.bing.com以下设备的连接:
# Test connectivity from a virtual machine to www.bing.com.
Test-AzNetworkWatcherConnectivity -Location 'chinaeast' -SourceId '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1' -DestinationAddress 'www.bing.com' -DestinationPort '443' | Format-List
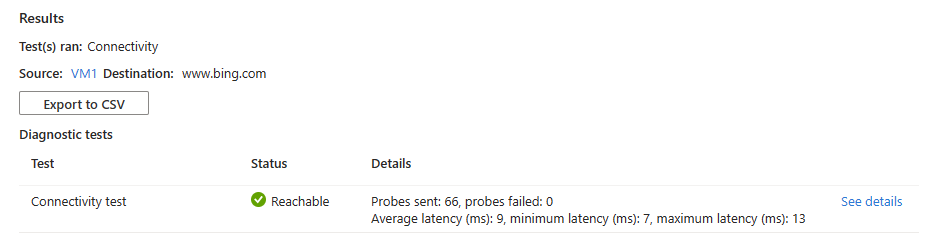
如果
www.bing.com从源虚拟机可达,则会看到以下结果:Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Reachable AvgLatencyInMs : 1 MinLatencyInMs : 1 MaxLatencyInMs : 6 ProbesSent : 66 ProbesFailed : 0 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "Internet", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "150.171.30.10", "NextHopIds": [], "Issues": [] } ]- 连接状态为“可访问”(可从 VM1 访问 )
www.bing.com。 - 已向
www.bing.com成功发送 66 个探测,平均延迟为 9 毫秒。 - 下一个跃点类型为
Internet。
- 连接状态为“可访问”(可从 VM1 访问 )
如果由于安全规则而导致源虚拟机无法连接到
www.bing.com,则会看到以下结果:Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [ { "Origin": "Outbound", "Severity": "Error", "Type": "NetworkSecurityRule", "Context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM1-nsg/SecurityRules/DenyInternetOutbound" } ] } ] }, { "Type": "Internet", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "203.0.113.184", "NextHopIds": [], "Issues": [] } ]- 连接状态为“不可访问”(不可从 VM1 访问 )
www.bing.com。 - 已发送 30 个探测,未能到达
www.bing.com。 - 网络安全组
DenyInternetOutbound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。 - 下一个跃点类型为
Internet。
解决方案:更新源虚拟机上的网络安全组,以允许到
www.bing.com的出站流量。- 连接状态为“不可访问”(不可从 VM1 访问 )
使用 az network watcher test-connectivity 命令进行连接故障排除,以测试与 www.bing.com 的连接。
# Test connectivity from a virtual machine to www.bing.com.
az network watcher test-connectivity --resource-group 'myResourceGroup' --source-resource 'VM1' --dest-address 'www.bing.com' --protocol 'TCP' --dest-port '443'
如果
www.bing.com从源虚拟机可达,则会看到以下结果:{ "avgLatencyInMs": 9, "connectionStatus": "Reachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "Internet", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "", "roundTripTimeAvg": 9, "roundTripTimeMax": 9, "roundTripTimeMin": 9 } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "104.117.244.81", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "Internet", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "type": "Internet" } ], "maxLatencyInMs": 13, "minLatencyInMs": 7, "probesFailed": 0, "probesSent": 66 }- 连接状态为“可访问”(可从 VM1 访问 )
www.bing.com。 - 已向
www.bing.com成功发送 66 个探测,平均延迟为 9 毫秒。 - 下一个跃点类型为
Internet。
- 连接状态为“可访问”(可从 VM1 访问 )
如果由于安全规则而导致源虚拟机无法连接到
www.bing.com,则会看到以下结果:{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [ { "context": [ { "key": "RuleName", "value": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkSecurityGroups/VM1-nsg/SecurityRules/DenyInternetOutbound" } ], "origin": "Outbound", "severity": "Error", "type": "NetworkSecurityRule" } ], "links": [ { "context": {}, "issues": [], "linkType": "Internet", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "203.0.113.184", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "Internet", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "type": "Internet" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可从 VM1 访问 )
www.bing.com。 - 已发送 30 个探测,未能到达
www.bing.com。 - 网络安全组
DenyInternetOutbound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。 - 下一个跃点类型为
Internet。
解决方案:更新源虚拟机上的网络安全组,以允许到
www.bing.com的出站流量。- 连接状态为“不可访问”(不可从 VM1 访问 )
测试与 IP 地址的连接
本部分将测试虚拟机与另一台虚拟机的 IP 地址之间的连接。
在“连接故障排除”页上。 输入或选择以下信息:
设置 价值 来源 源类型 选择“虚拟机”。 虚拟机 选择要进行连接故障排查的虚拟机。 目的地 目标类型 选择手动指定。 URI、FQDN 或 IP 地址 输入要测试其连接的 IP 地址。 在此示例中,使用 10.10.10.10。探测设置 首选 IP 版本 选择 IPv4。 其他可用选项包括:“两者”和“IPv6”。 协议 选择TCP。 其他可用选项包括:ICMP。 目标端口 输入“3389”。 源端口 留空或输入要测试的源端口号。 连接诊断 诊断测试 选择“连接”、“NSG 诊断”和“下一个跃点”。 选择“运行诊断测试”。
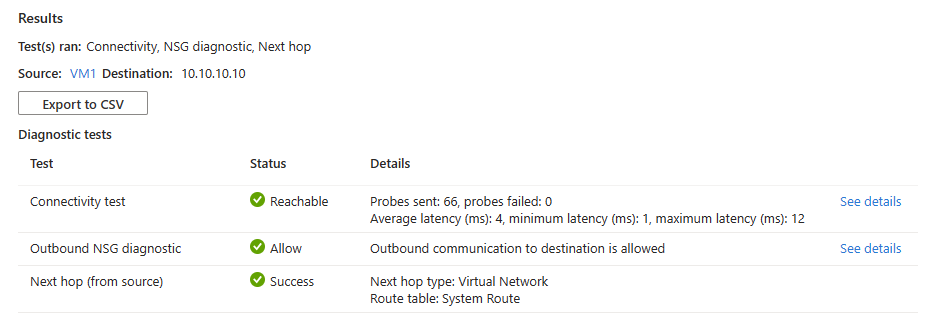
如果 IP 地址可访问,则会看到以下结果:
- 已成功发送 66 个探测,平均延迟为 4 毫秒。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 允许来自源虚拟机的出站连接。 选择查看详细信息来查看允许源虚拟机进行出站通信的安全规则。
- Azure 默认系统路由用于将流量路由到同一虚拟网络或对等互连虚拟网络中的 IP 地址。 (路由表 ID:系统路由和下一个跃点类型:虚拟网络)。
如果 IP 地址由于目标虚拟机未运行而无法访问,则会看到以下结果:
- 已发送 30 个探测,未能到达目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 允许来自源虚拟机的出站连接。 选择查看详细信息来查看允许源虚拟机进行出站通信的安全规则。
- Azure 默认系统路由用于将流量路由到同一虚拟网络或对等互连虚拟网络中的 IP 地址。 (路由表 ID:系统路由和下一个跃点类型:虚拟网络)。
解决方案:启动目标虚拟机。
如果源虚拟机的路由表中没有 IP 地址的路由(例如,IP 地址不在 VM 虚拟网络或其对等互连虚拟网络的地址空间中),则会看到以下结果:
- 已发送 30 个探测,未能到达目标虚拟机。 选择“查看详细信息”以查看下一个跳转点的详细信息。
- 拒绝来自源虚拟机的出站连接。 选择“查看详细信息”以查看拒绝源虚拟机出站通信的安全规则。
- 下一跃点类型为“无”,因为没有到该 IP 地址的路由。
解决方案:将路由表与源虚拟机子网的正确路由相关联。
选择“导出到 CSV”以 CSV 格式下载测试结果。
使用 Test-AzNetworkWatcherConnectivity cmdlet 运行连接故障排除,以测试 RDP 与 10.10.10.10以下设备的连接:
# Test connectivity from a virtual machine to 10.10.10.10 over port 3389.
Test-AzNetworkWatcherConnectivity -Location 'chinaeast' -SourceId '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1' -DestinationAddress '10.10.10.10' -DestinationPort '3389' | Format-List
如果 IP 地址可访问,则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Reachable AvgLatencyInMs : 1 MinLatencyInMs : 1 MaxLatencyInMs : 3 ProbesSent : 66 ProbesFailed : 8 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "VirtualNetwork", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.10.10.10", "NextHopIds": [], "Issues": [] } ]- 连接状态为“可访问”(可通过端口 3389 访问 )
10.10.10.10。 - 已向
10.10.10.10成功发送 66 个探测,平均延迟为 2 毫秒。 - 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 连接状态为“可访问”(可通过端口 3389 访问 )
如果 IP 地址由于目标虚拟机未运行而无法访问,则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [] }, { "Type": "VirtualNetwork", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.10.10.10", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup1/providers/Microsoft.Network/networkInterfaces/vm2375/ipConfigurations/ipconfig1", "NextHopIds": [], "Issues": [] } ]- 连接状态为“不可访问”(不可通过端口 3389 访问 )
10.10.10.10。 - 已发送 30 个探测,未能到达
10.10.10.10。 - 源虚拟机中无任何问题。
-
10.10.10.10无任何问题。
解决方案:启动目标虚拟机。
- 连接状态为“不可访问”(不可通过端口 3389 访问 )
如果源虚拟机的路由表中没有 IP 地址的路由(例如,IP 地址不在 VM 虚拟网络或其对等互连虚拟网络的地址空间中),则会看到以下结果:
Hops : {aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb, bbbbbbbb-1111-2222-3333-cccccccccccc} ConnectionStatus : Unreachable AvgLatencyInMs : MinLatencyInMs : MaxLatencyInMs : ProbesSent : 30 ProbesFailed : 30 HopsText : [ { "Type": "Source", "Id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "Address": "10.0.0.4", "ResourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "NextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "Issues": [ { "Origin": "Local", "Severity": "Error", "Type": "RouteMissing", "Context": [] }, { "Origin": "Outbound", "Severity": "Error", "Type": "UserDefinedRoute", "Context": [ { "key": "ErrorMessage", "value": "NextHop Type None, NextHop IP " } ] }, { "Origin": "Outbound", "Severity": "Error", "Type": "NetworkSecurityRule", "Context": [ { "key": "RuleName", "value": "DefaultRule_DenyAllOutBound" } ] } ] }, { "Type": "Destination", "Id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "Address": "10.10.10.10", "NextHopIds": [], "Issues": [] } ]- 连接状态为“不可访问”(不可通过端口 3389 访问 )
10.10.10.10。 - 已发送 30 个探测,未能到达
10.10.10.10。 - 源虚拟机的路由表中没有到
10.10.10.10的路由(源虚拟机上的输出具有RouteMissing错误)。 - 下一跃点类型为“无”,因为没有到 的路由
10.10.10.10。 - 网络安全组
DefaultRule_DenyAllOutBound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。
解决方案:将路由表与源虚拟机子网的正确路由相关联。
- 连接状态为“不可访问”(不可通过端口 3389 访问 )
使用 az network watcher test-connectivity 命令运行连接故障排除,以测试到 10.10.10.10 的 RDP 连接。
# Test connectivity from a virtual machine to 10.10.10.10 over port 3389.
az network watcher test-connectivity --resource-group 'myResourceGroup' --source-resource 'VM1' --dest-address '10.10.10.10' --protocol 'TCP' --dest-port '3389'
如果 IP 地址可访问,则会看到以下结果:
{ "avgLatencyInMs": 2, "connectionStatus": "Reachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "", "roundTripTimeAvg": 2, "roundTripTimeMax": 2, "roundTripTimeMin": 2 } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.10.10.10", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkInterfaces/vm2375/ipConfigurations/ipconfig1", "type": "VirtualNetwork" } ], "maxLatencyInMs": 7, "minLatencyInMs": 1, "probesFailed": 0, "probesSent": 66 }- 连接状态为“可访问”(可通过端口 3389 访问 )
10.10.10.10。 - 已向
10.10.10.10成功发送 66 个探测,平均延迟为 2 毫秒。 - 两个虚拟机之间的路径有两种跃点(两个 VM 之间的路径中没有设备或其他资源)。
- 连接状态为“可访问”(可通过端口 3389 访问 )
如果 IP 地址由于目标虚拟机未运行而无法访问,则会看到以下结果:
{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.10.10.10", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkInterfaces/vm2375/ipConfigurations/ipconfig1", "type": "VirtualNetwork" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可通过端口 3389 访问 )
10.10.10.10。 - 已发送 30 个探测,未能到达
10.10.10.10。 - 源虚拟机中无任何问题。
-
10.10.10.10无任何问题。
解决方案:启动目标虚拟机。
- 连接状态为“不可访问”(不可通过端口 3389 访问 )
如果源虚拟机的路由表中没有 IP 地址的路由(例如,IP 地址不在 VM 虚拟网络或其对等互连虚拟网络的地址空间中),则会看到以下结果:
{ "connectionStatus": "Unreachable", "hops": [ { "address": "10.0.0.4", "id": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "issues": [ { "context": [], "origin": "Local", "severity": "Error", "type": "RouteMissing" }, { "context": [ { "key": "ErrorMessage", "value": "NextHop Type None, NextHop IP " } ], "origin": "Outbound", "severity": "Error", "type": "UserDefinedRoute" }, { "context": [ { "key": "RuleName", "value": "DefaultRule_DenyAllOutBound" } ], "origin": "Outbound", "severity": "Error", "type": "NetworkSecurityRule" } ], "links": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "bbbbbbbb-1111-2222-3333-cccccccccccc", "resourceId": "" } ], "nextHopIds": [ "bbbbbbbb-1111-2222-3333-cccccccccccc" ], "previousHopIds": [], "previousLinks": [], "resourceId": "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachines/VM1", "type": "Source" }, { "address": "10.10.10.10", "id": "bbbbbbbb-1111-2222-3333-cccccccccccc", "issues": [], "links": [], "nextHopIds": [], "previousHopIds": [ "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb" ], "previousLinks": [ { "context": {}, "issues": [], "linkType": "VirtualNetwork", "nextHopId": "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb", "resourceId": "" } ], "type": "Destination" } ], "probesFailed": 30, "probesSent": 30 }- 连接状态为“不可访问”(不可通过端口 3389 访问 )
10.10.10.10。 - 已发送 30 个探测,未能到达
10.10.10.10。 - 源虚拟机的路由表中没有到
10.10.10.10的路由(源虚拟机上的输出具有RouteMissing错误)。 - 下一跃点类型为“无”,因为没有到 的路由
10.10.10.10。 - 网络安全组
DefaultRule_DenyAllOutBound中的安全规则VM1-nsg拒绝来自源虚拟机的出站连接。
解决方案:将路由表与源虚拟机子网的正确路由相关联。
- 连接状态为“不可访问”(不可通过端口 3389 访问 )
相关内容
其他资源
-
Last updated on
2025-11-27
 显示在 Azure 门户中如何搜索 “网络观察程序” 的屏幕截图。
显示在 Azure 门户中如何搜索 “网络观察程序” 的屏幕截图。

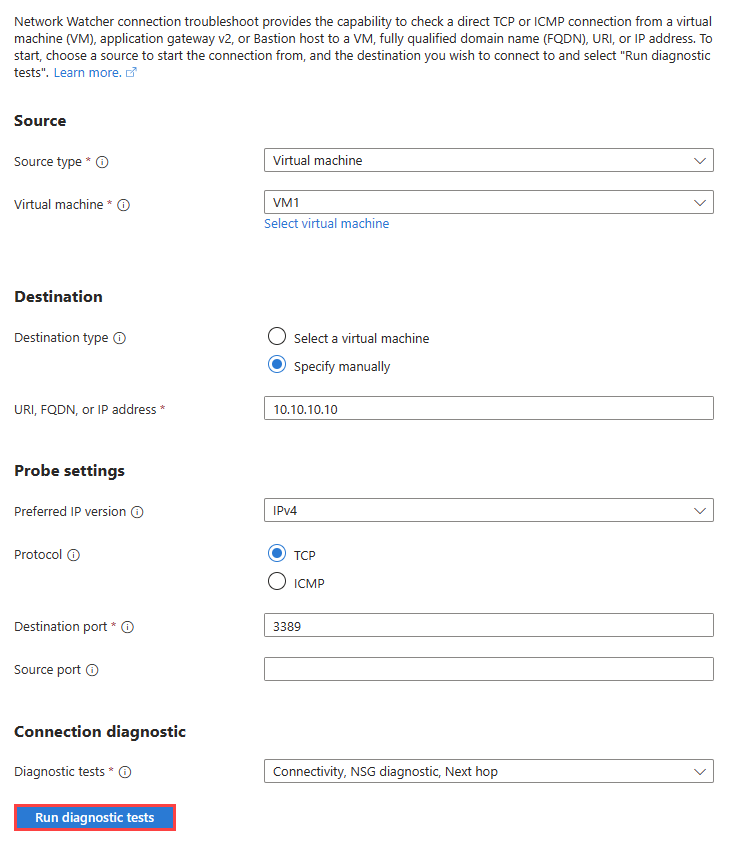 显示 Azure 门户中的排查连接问题(用于测试虚拟机与 IP 地址之间的连接)的屏幕截图。
显示 Azure 门户中的排查连接问题(用于测试虚拟机与 IP 地址之间的连接)的屏幕截图。